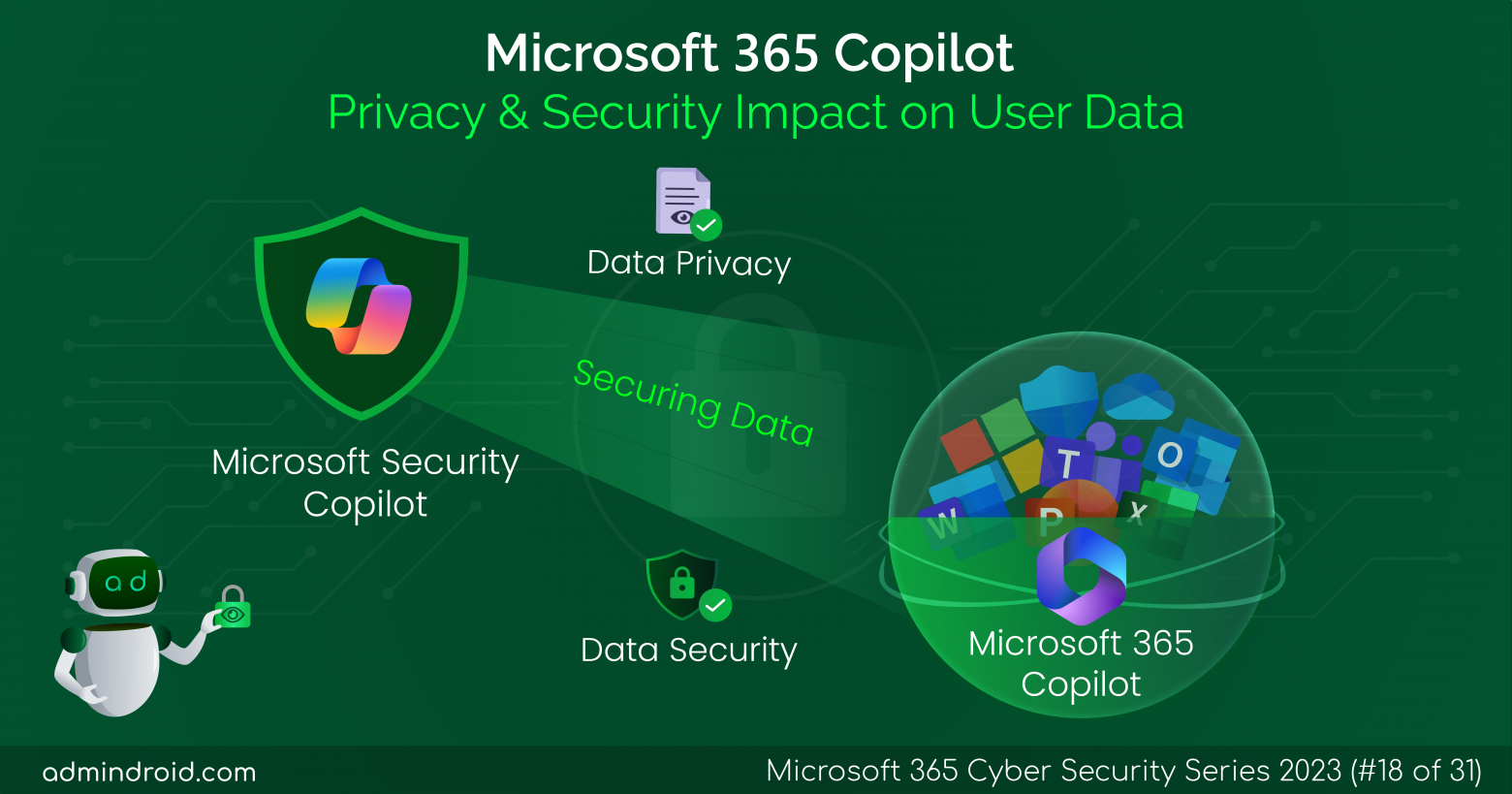
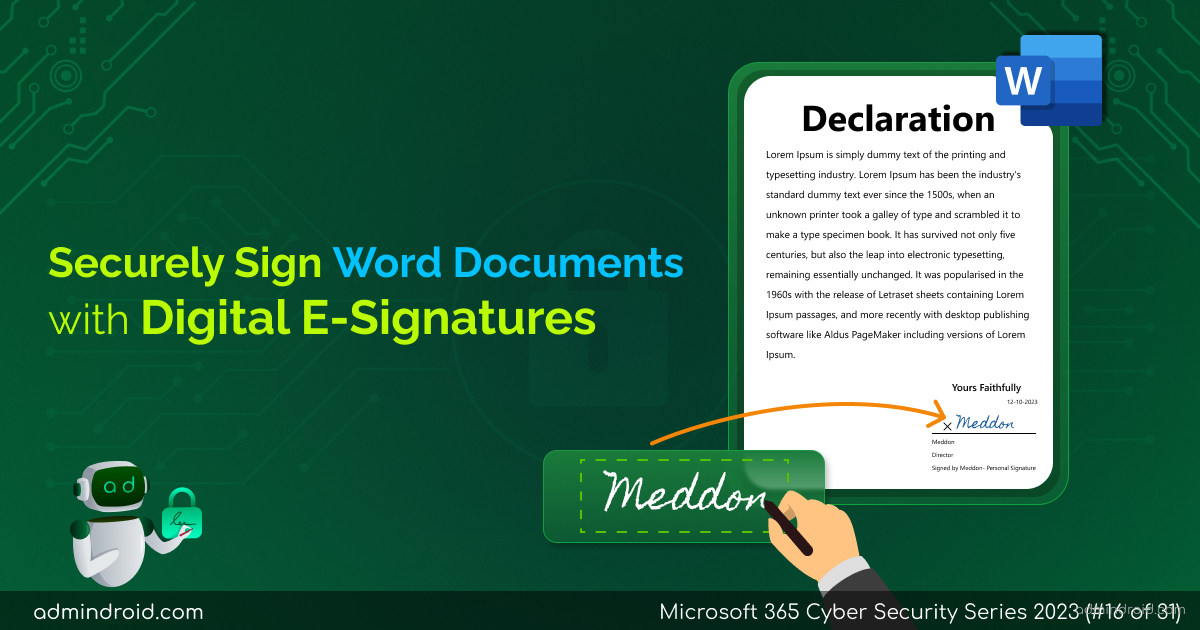
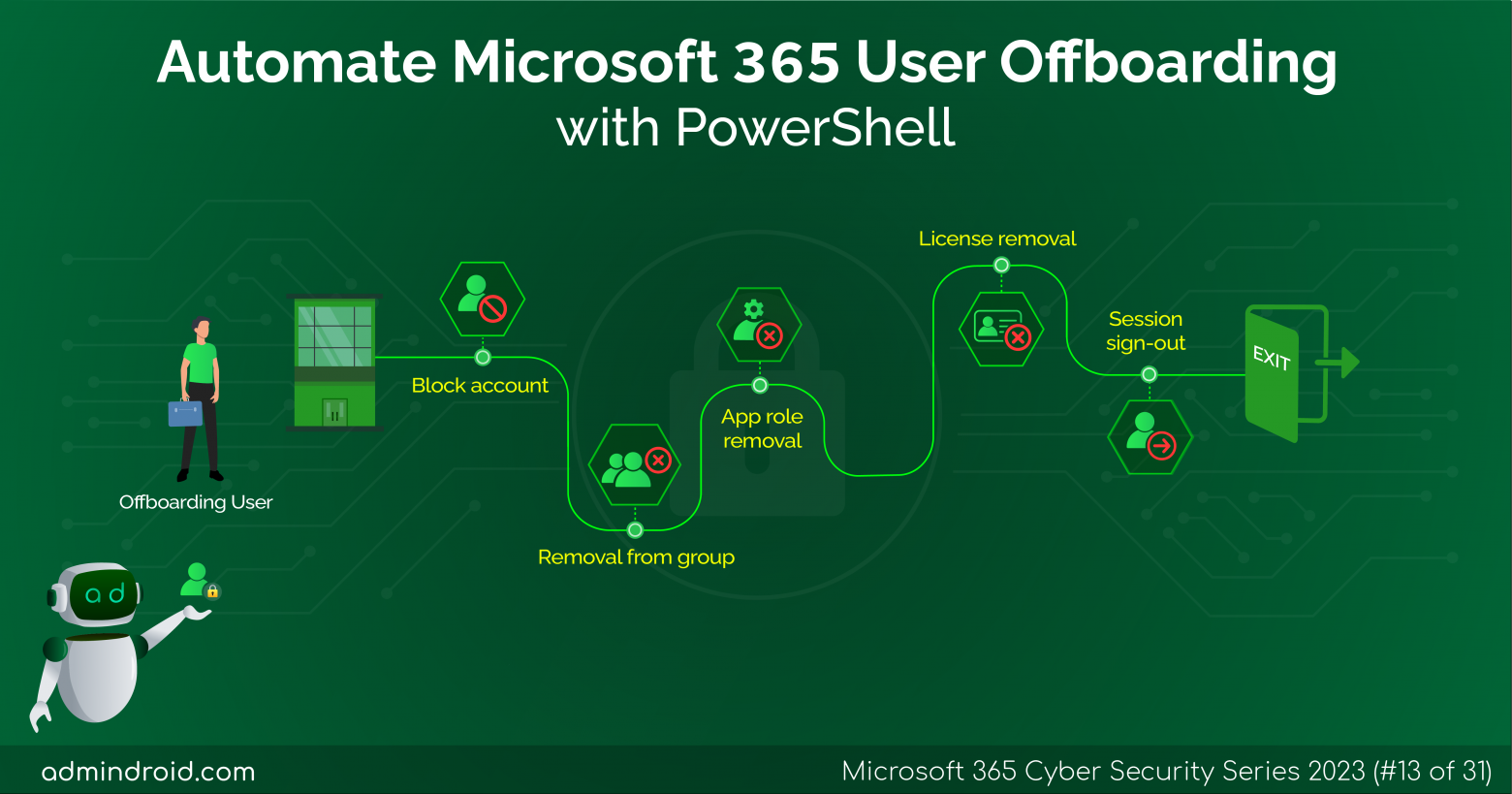
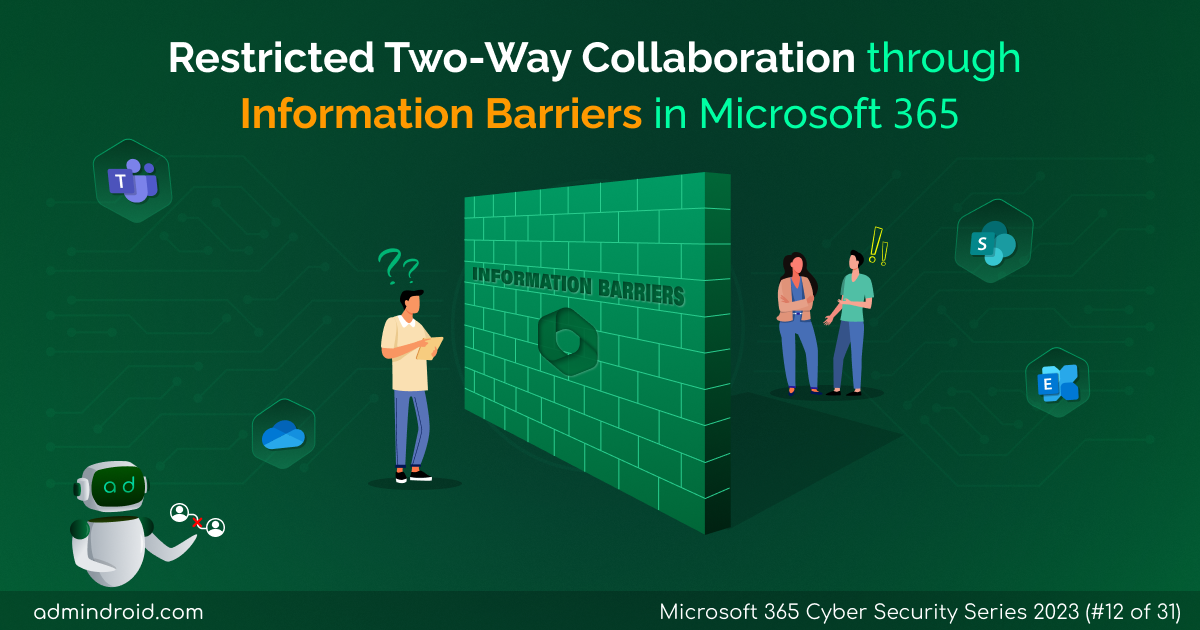
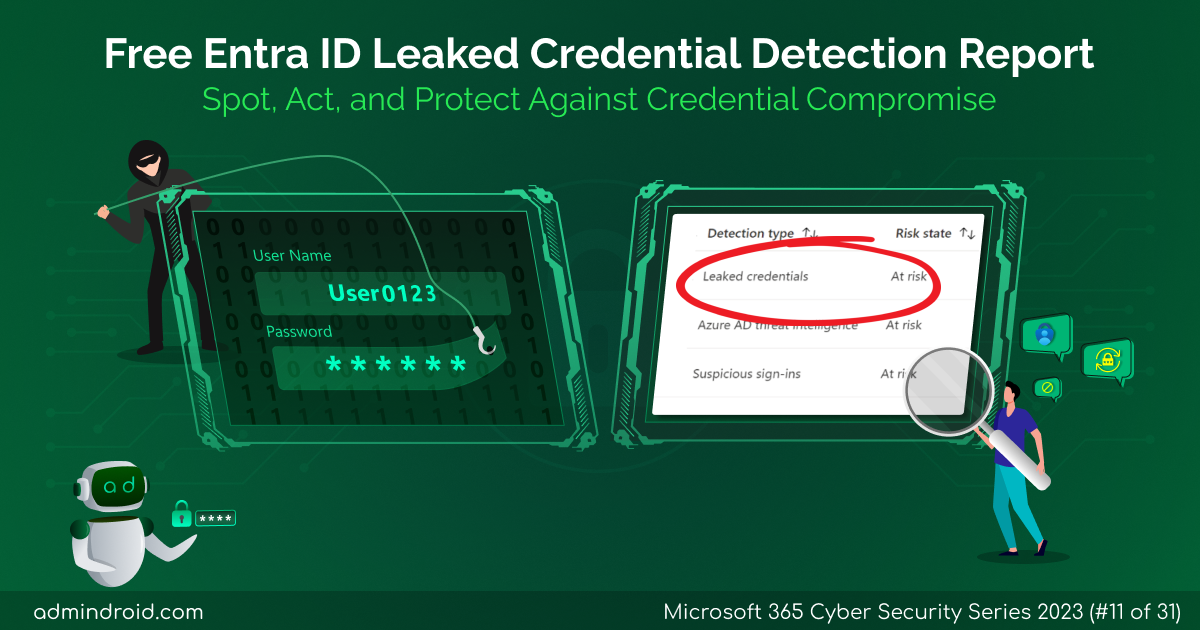
On Day 19 of the cybersecurity awareness month, learn about the Microsoft Entra ID Protection dashboard to analyze the security exposure of organizations better. Stay tuned for more blogs in the M365 Cybersecurity blog series. In the rapidly changing digital environment of today, standard security measures are not enough to protect an organization’s identity. It…