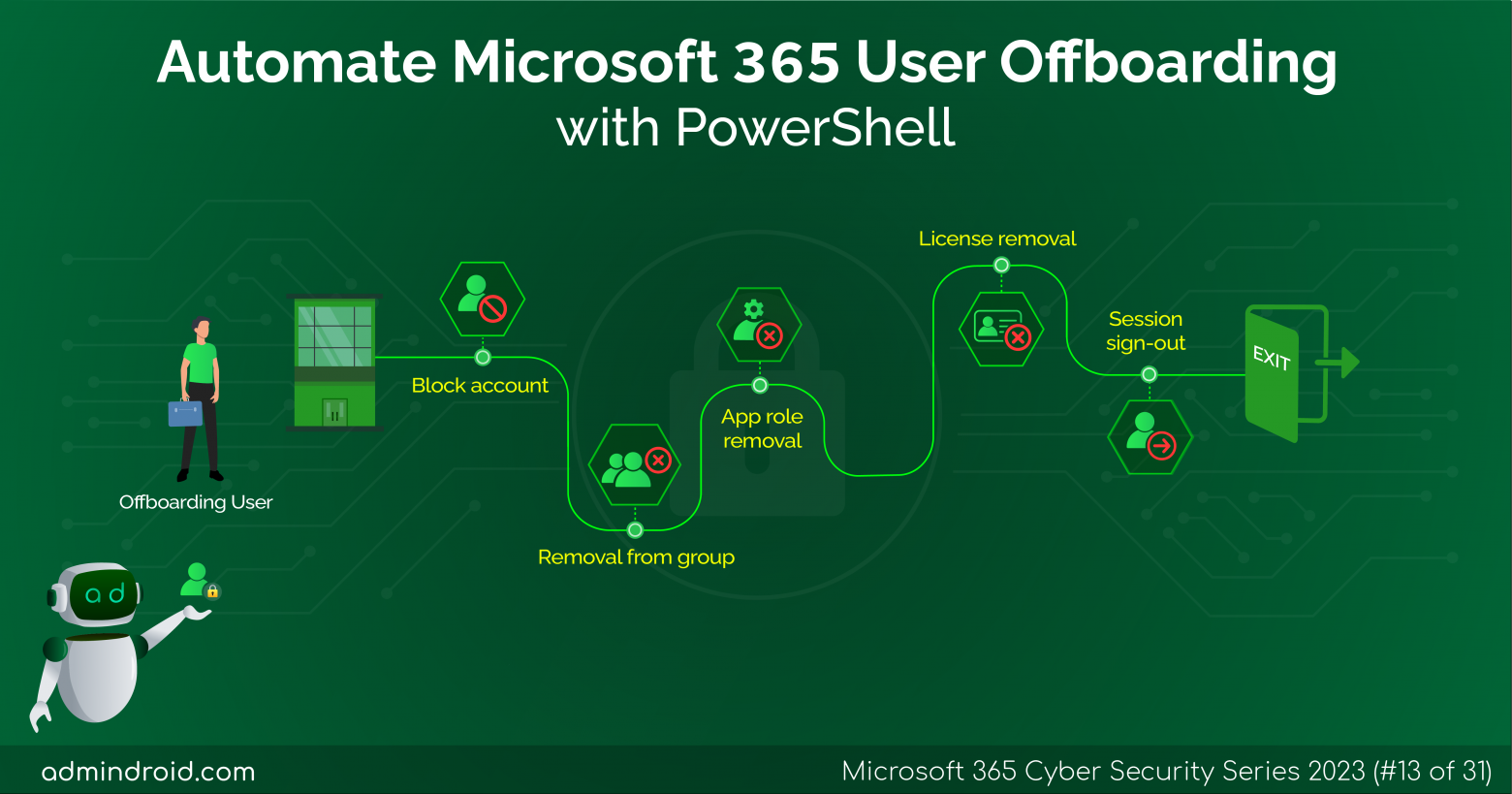
On Day 13 of the Cybersecurity Awareness month, we present to you a Microsoft 365 user off-boarding script that incorporates the best practices suggested by sysadmins the world over. Easen your workload in a safe and secure manner. Stay tuned for more in the M365 cybersecurity blog series The process of removing or ‘offboarding’ a former employee is…