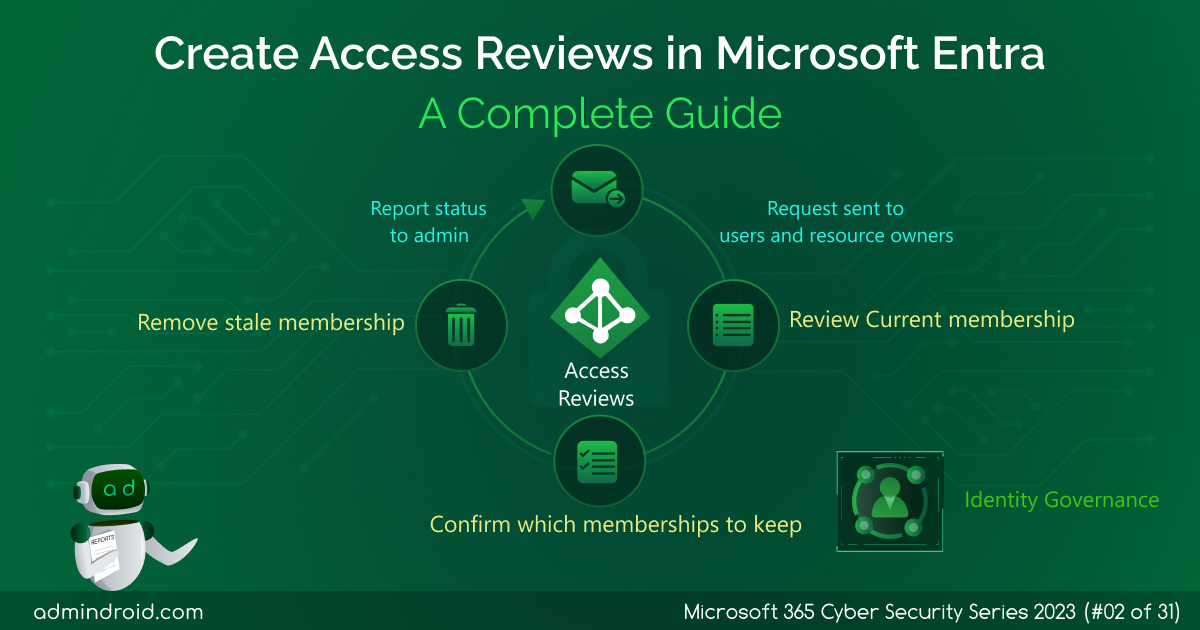
On Day 2 of the cybersecurity awareness month, learn how to create access reviews in Microsoft Entra ID. Stay tuned for more blogs in the M365 Cybersecurity blog series. Access management in modern organizations has become a complex task, especially with the rise of remote work, collaboration tools, and the need to ensure data security. This…