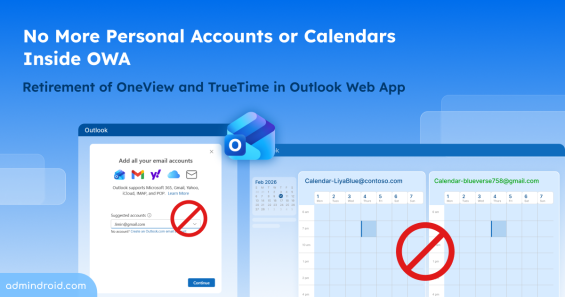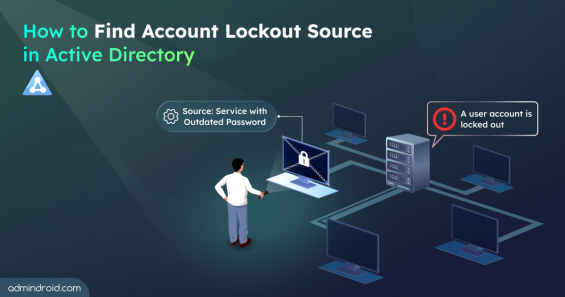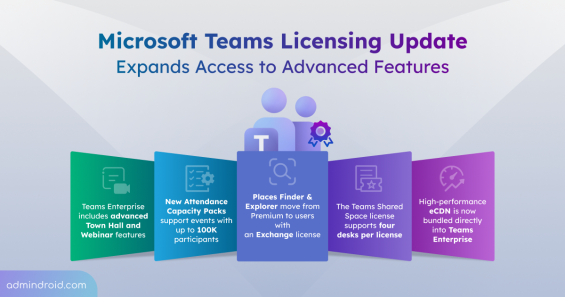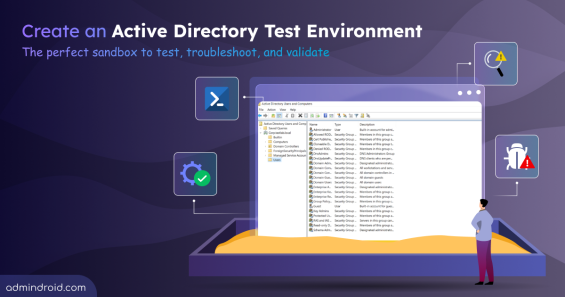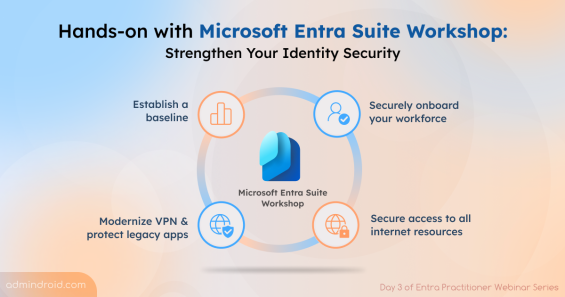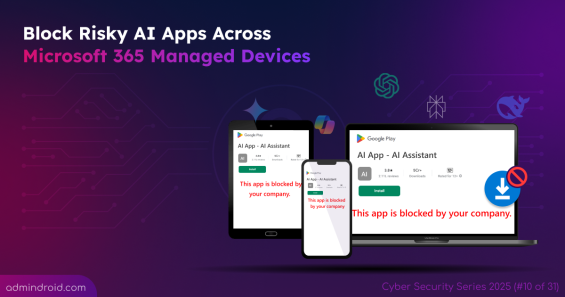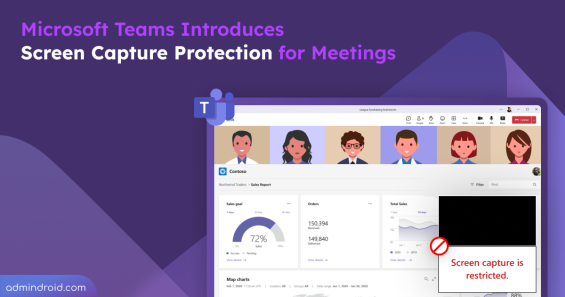
Quick M365 Updates
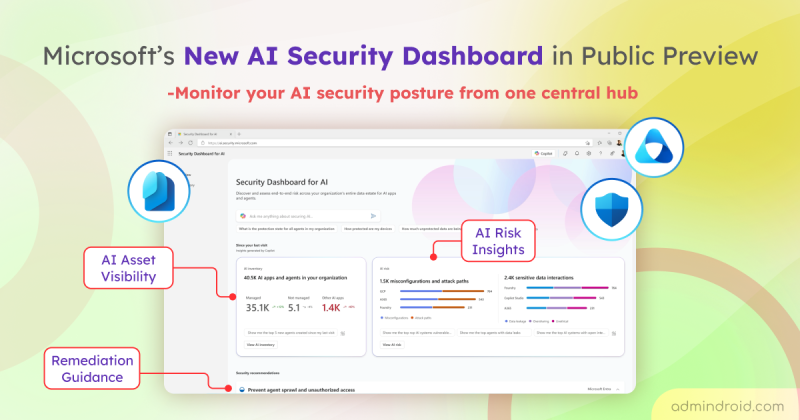
New AI Security Dashboard to Identify and Manage AI Risks in Microsoft 365
Explore Microsoft’s new Security Dashboard for AI in public preview to monitor AI assets, risks, and security posture in one place.
6 min read