
Microsoft 365 News
2026 End-of-Support Milestone in Microsoft 365
Learn which Microsoft 365 services and technologies are reaching end-of-support milestone in 2026 and how admins can plan ahead.
10 min read
Summary:Microsoft Entra Kerberos provides a simpler way to set up hybrid-joined devices by reducing the need for Microsoft Entra Connect or Active Directory Federation Services. By using cloud-based authentication with Microsoft Entra ID, organizations can streamline device onboarding and simplify hybrid deployments. Hybrid identity has always been a balancing act.…
Summary: Microsoft introduces the new Cloud Licensing API in Microsoft Graph (beta) to improve license management. Some of this functionality was released back in 2024. Currently in preview, this update introduces “Allotments,” “Waiting Members,” and more, giving Microsoft 365 developers and admins granular control over how licenses are managed in your organizations. While existing endpoints like subscribedSkus and licenseDetails provide high-level visibility, they lack the precision to map…
Summary Starting in late February 2026, Microsoft Teams Mobile (Android & iOS) will prompt users to choose between Edge and the default browser when opening non-Office and PDF links. While Microsoft presents this as a usability update, the flow clearly promotes Edge within the decision screen. It’s less forceful than before, but still a built-in nudge toward Microsoft’s browser. The feature is enabled by default…
Summary Microsoft now introduces the Security Dashboard for AI in public preview to help organizations strengthen AI security. This dashboard centralizes AI inventory, risks, and recommendations in one place for easier security management. While AI apps and agents are rapidly sprawling across Microsoft 365 organizations, many security teams still lack clear visibility into…
Summary: Microsoft is retiring the Credential parameter in Exchange Online PowerShell as part of its move toward a stronger, MFA-backed sign-in experience. Support will be removed from module versions released after June 2026. Admins and automation workflows should migrate to supported alternatives, like interactive sign-ins, app-only authentication, and managed identity…
Summary: Microsoft is officially retiring the standalone SharePoint Online and OneDrive for Business plans (Plan 1 and Plan 2).Instead, customers will need to move to Microsoft 365 suite licenses as Microsoft consolidates its services into a more integrated cloud experience. If you’ve been relying on the handy standalone SharePoint Online and OneDrive for…
Struggling to automate secure monitor manage M365?
Try AdminDroid for Free!
Learn which Microsoft 365 services and technologies are reaching end-of-support milestone in 2026 and how admins can plan ahead.
10 min read
Learn to build a unified identity and network foundation for Entra Suite by automating provisioning, compliance checking, VPN replacements.
12 min read
Learn to detect shadow AI Usage and protect internet access with Entra Suite features like web content filtering, threat intelligence filtering.
6 min read
Learn how Microsoft Entra Suite modernize the security on on-premises application with the help of Microsoft Entra Private Access
4 min read
Learn how to ensure least privilege access with access packages, lifecycle workflows in Microsoft Entra Suite
4 min read
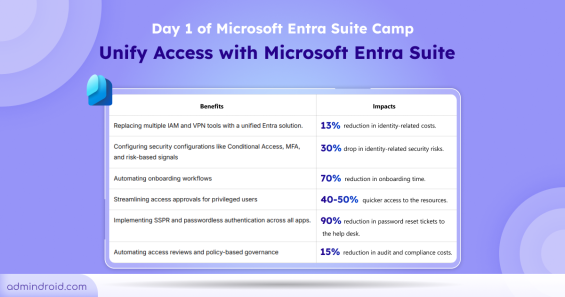
Learn the importance of Microsoft Entra Suite for secure Zero trust Access to your environment
3 min read
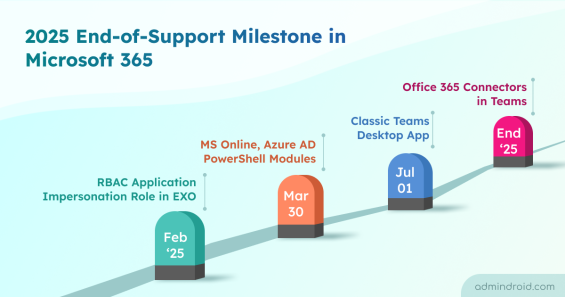
This blog highlights the Microsoft 365 services, products, and technologies set to be deprecated in 2025. Admins can plan for necessary steps.
6 min read

Learn to delete phone authentication for Microsoft 365 users via Entra admin center, MS Graph PowerShell, and a all-in-one PowerShell script
7 min read

Learn to allow external sharing for specific SharePoint sites in Microsoft 365 using a all-in-one PnP PowerShell script
6 min read
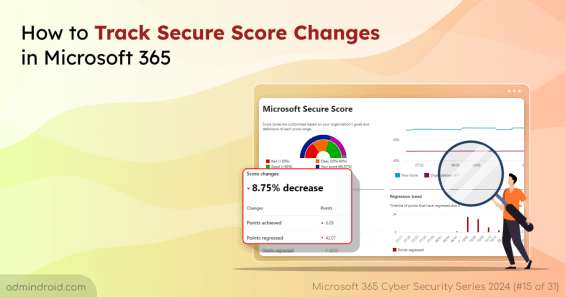
Learn to track secure score changes in Microsoft 365 to avoid accidental misconfigurations and secure your Microsoft 365 environment.
5 min read
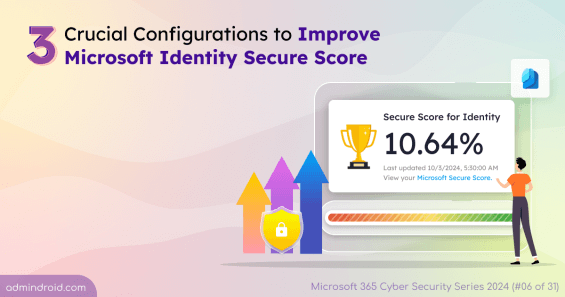
Learn to improve Microsoft identity secure score with three crucial Microsoft settings and safeguard your organization's identity.
6 min read
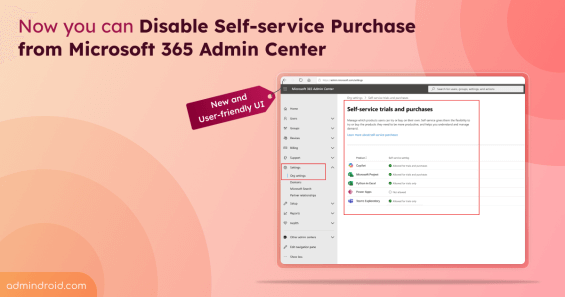
Admins can block self-service purchases from an user-friendly UI found in Microsoft 365 admin center.
3 min read