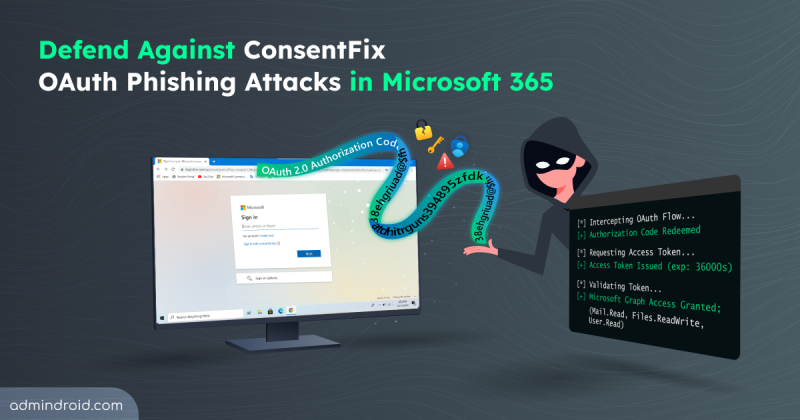
What is ConsentFix Attack and How to Mitigate it in Microsoft 365
Explore how ConsentFix attack abuses trusted Microsoft 365 first-party app access and learn mitigations to prevent OAuth token misuse.
15 min read
Microsoft now allows admins to enforce a default expiration period for “People in your organization” sharing links in SharePoint Online and OneDrive. By configuring maximum and recommended expiration values, admins can prevent internal links from staying active indefinitely. This update helps reduce stale access while maintaining flexible and secure collaboration.
Starting March 3, 2026, Microsoft is introducing a completely reimagined SharePoint experience in Microsoft 365, designed to make collaboration smarter, faster, and more intuitive. The new experience features a redesigned app bar categorized into three core jobs - Discover, Publish, and Build along with AI-powered tools and a neutral theme.
Microsoft Entra Kerberos provides a simpler way to set up hybrid-joined devices by reducing the need for Microsoft Entra Connect or Active Directory Federation Services. By using cloud-based authentication with Microsoft Entra ID, organizations can streamline device onboarding and simplify hybrid deployments.
Tracking Microsoft 365 licenses can be challenging for many organizations. To simplify this, Microsoft introduced the Cloud Licensing beta API in Microsoft Graph (preview), giving admins and developers granular control. Instead of just showing a flat license count, it supports batch tracking, queuing users when licenses run out, and quickly identifying assignment errors.
Starting in late February 2026, Microsoft Teams Mobile (Android & iOS) will prompt users to choose between Edge and the default browser when opening non-Office and PDF links. While Microsoft presents this as a usability update, the flow clearly promotes Edge within the decision screen. It’s less forceful than before, but still a built-in nudge toward Microsoft’s browser. The feature is enabled by default for all tenants but can be disabled by admins via PowerShell.
Microsoft now introduces the Security Dashboard for AI in public preview to help organizations strengthen AI security. This dashboard centralizes AI inventory, risks, and recommendations in one place for easier security management.
Struggling to automate secure monitor manage M365?
Try AdminDroid for Free!The ultimate Microsoft 365 resource hub for beginner to pro.

Explore how ConsentFix attack abuses trusted Microsoft 365 first-party app access and learn mitigations to prevent OAuth token misuse.
15 min read
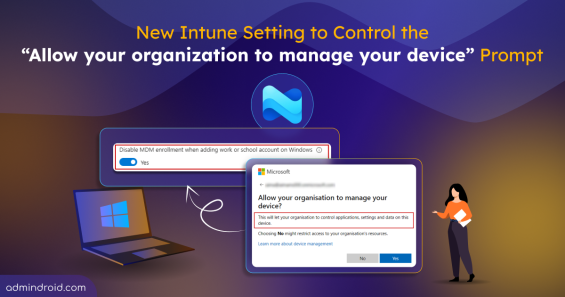
Learn how to disable automatic MDM enrollment during work or school account sign-in on Windows.
8 min read

Learn different ways to clean up file version history in SharePoint Online to optimize storage and maintain a healthy M365 environment.
13 min read

Microsoft is retiring Standalone SharePoint and OneDrive Plans (Plan 1 & 2). Explore Business & Enterprise suite & storage alternatives now.
4 min read
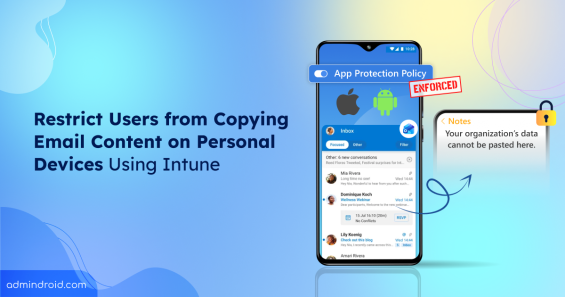
Learn how to protect email data on unmanaged devices using app protection policy in Microsoft Intune.
12 min read
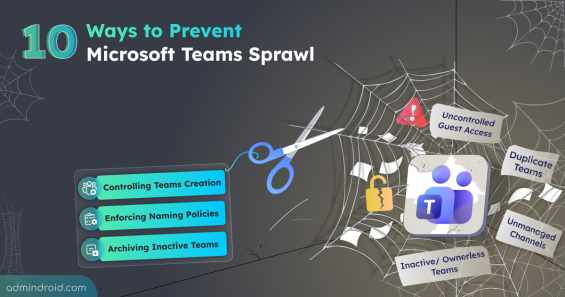
Learn how to prevent Teams sprawl with 10 proven strategies to improve governance and reduce security risks.
12 min read
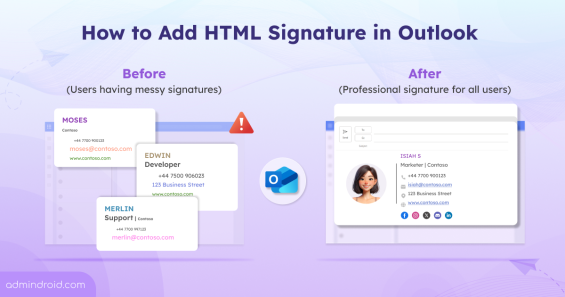
Admins can create and add html signatures in Microsoft 365 to have consistent style and formatting in the organization.
9 min read

Learn which Microsoft 365 services and technologies are reaching end-of-support milestone in 2026 and how admins can plan ahead.
10 min read

Discover the top Microsoft 365 admin blogs of 2025, featuring the latest tips and best practices to help you manage your M365 environment.
15 min read

Discover the key Microsoft 365 security settings added in 2025 and learn which features to enable or disable to strengthen security posture.
12 min read

Learn how to create and assign scope tags in Microsoft Intune to control visibility and streamline Intune resources management.
10 min read
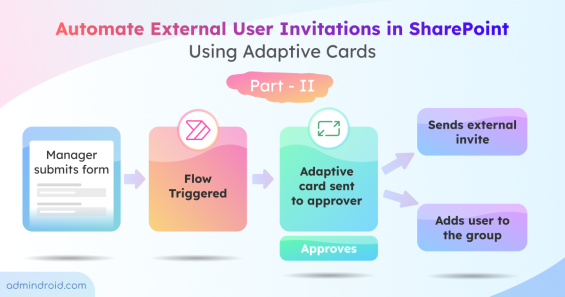
Learn how to automate external user invitations using Power Automate and Adaptive Cards in Teams with this step-by-step guide.
16 min read