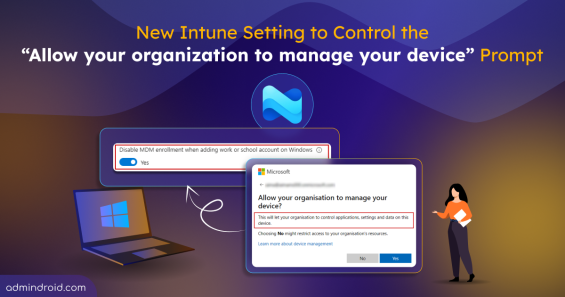
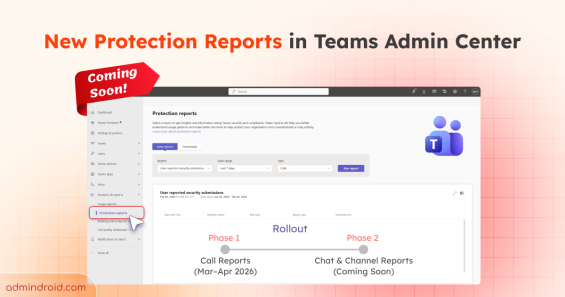
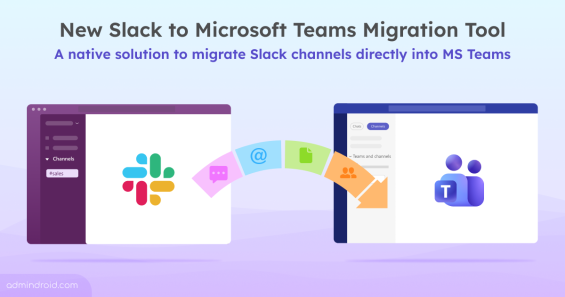
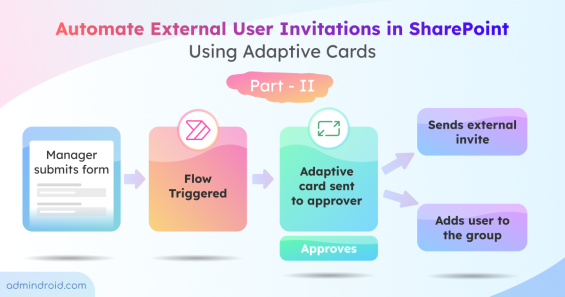
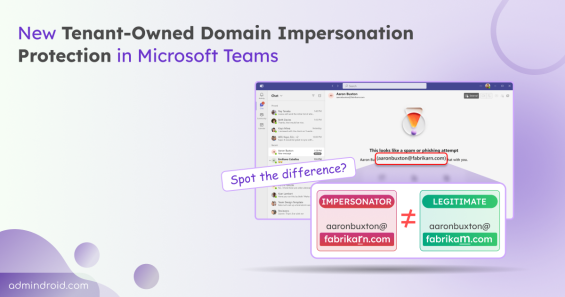
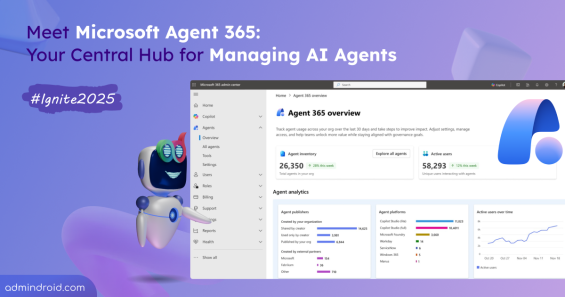
Quick M365 Updates
New SharePoint Experience in Microsoft 365: Smarter, Faster, AI-Ready
Discover how the new SharePoint experience in Microsoft 365 makes collaboration smarter with AI tools, modern layouts, and task-focused design.
6 min read