
Create Scope Tags in Microsoft Intune
Learn how to create and assign scope tags in Microsoft Intune to control visibility and streamline Intune resources management.
10 min read
SharePoint Online environments often grew without control, with sites staying active long after projects ended, members never being cleaned up, and sharing left open. This led to oversharing and content sprawl, with many sites lacking clear ownership and proper governance. Without automation, managing site lifecycles across hundreds or thousands of sites became a manual, unscalable…
For years, private channels were the “quiet corners” of Microsoft Teams, excellent for security. However, they were frustratingly limited when it came to the apps and bots that drive daily workflows. Only a limited set of tabs was supported, forcing admins to move from private channels to standard channels to access Teams app functionality. That limitation…
Have you ever managed a Microsoft 365 tenant-to-tenant migration during a merger, acquisition, or organizational split? If so, you know how complex it can be—separate tools for Exchange and OneDrive, multiple scripts to track progress, and limited visibility into what’s moving and what’s not. For admins, cross-tenant migrations have often…
Imagine you’re in a Microsoft Teams meeting. Someone shares a link, another asks for a file, and a new name appears in the chat. You respond without hesitation. But do you really know who’s on the other side? Is that person an internal colleague? A trusted external partner? Or a guest with limited access? That’s where Microsoft Teams Trust…
When responding to suspicious MFA sessions, compromised accounts, or device loss, most admins instinctively go for revoking MFA sessions. However, what’s often misunderstood is how this action actually works. The “Revoke MFA sessions” option only clears per-user MFA sessions created through per-user MFA. It does not revoke MFA claims issued…
SharePoint Online is a go-to platform for collaboration, where users upload audio files for teamwork and share large videos for training. The catch? Even small updates to these media files generate massive new versions. These media formats typically generate much larger versions than standard documents, causing storage to balloon quickly in…
Struggling to automate secure monitor manage M365?
Try AdminDroid for Free!The ultimate Microsoft 365 resource hub for beginner to pro.

Learn how to create and assign scope tags in Microsoft Intune to control visibility and streamline Intune resources management.
10 min read
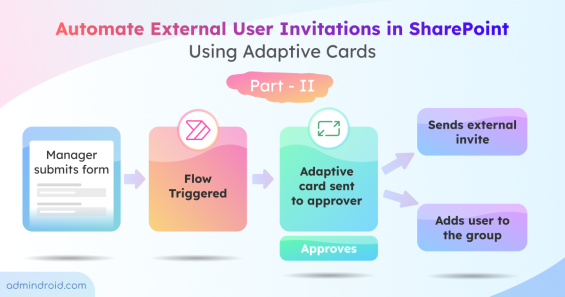
Learn how to automate external user invitations using Power Automate and Adaptive Cards in Teams with this step-by-step guide.
16 min read

Explore how the Shared tab in MS Teams Channels that makes it easier to access files and links shared in posts and document libraries for good collaboration.
3 min read

Explore the crucial Microsoft Teams governance strategies to improve collaboration and ensure compliant use of Teams across the organization.
11 min read
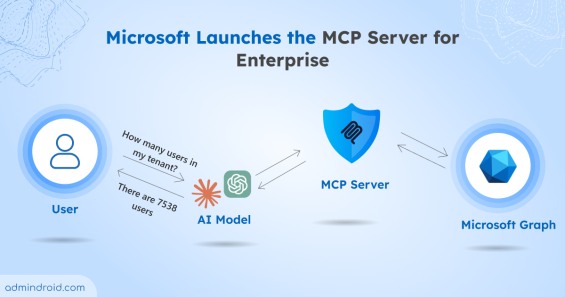
Learn how the Microsoft MCP Server for Enterprise lets AI agents query Microsoft 365 and Entra ID data through natural language.
6 min read
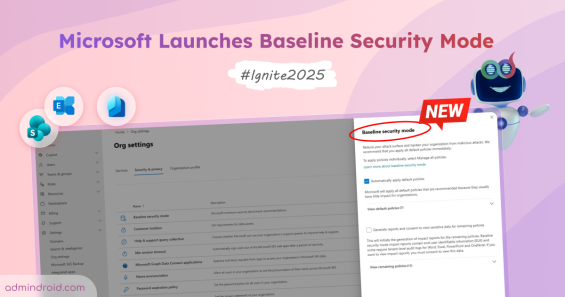
Baseline Security Mode (BSM) is a centralized Microsoft 365 security framework that enforces essential identity, access, and authentication protections.
9 min read

Learn how to collect files in the document library using Microsoft Forms and streamline document collection in SharePoint.
5 min read

Learn how to create, configure, & monitor device compliance policies in Intune to enforce security standards and protect corporate data.
9 min read

Learn how to automate SharePoint guest access approvals using Power Automate and Adaptive Cards in Teams with this step-by-step guide.
11 min read

Cybersecurity Month wrap-up: Strengthen IT environments and secure Microsoft 365, Active Directory, hybrid, and AI platforms.
11 min read

Explore key strategies to safeguard employee personal data across apps, devices, and cloud services in modern hybrid workplaces.
8 min read
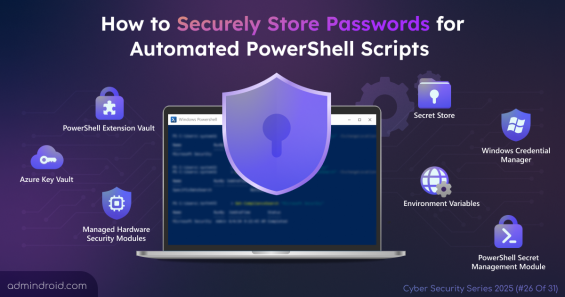
Explore methods to securely store passwords for PowerShell script to avoid unauthorized access, credential leaks, and ensure safe automation.
9 min read