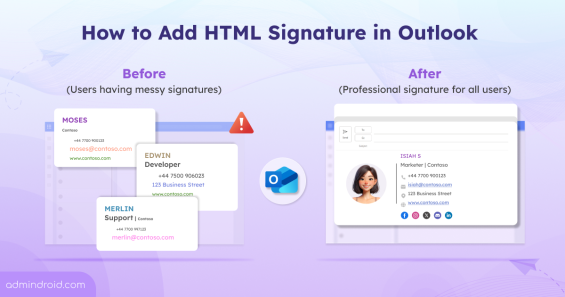
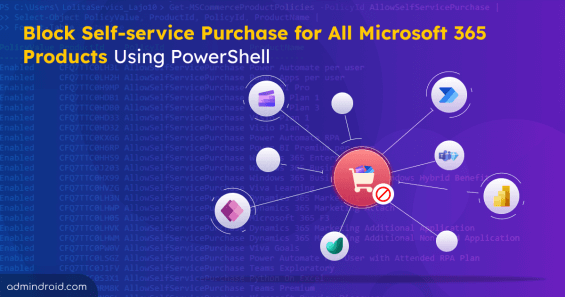
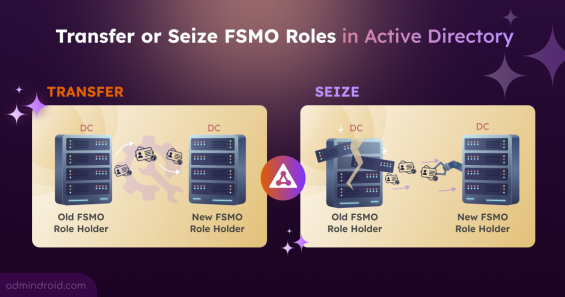
We ❤️ to Serve the Microsoft 365 Community
With the
Latest Updates, Free Scripts, and Tools!
something new to learn.