
Custom Security Attributes in Microsoft Entra ID
Custom security attributes in Entra ID help extend user and app profiles with business-specific data. Learn how to configure them.
6 min read
Struggling to automate secure monitor manage M365?
Try AdminDroid for Free!Explore the global trends and tributes we cherish.

Custom security attributes in Entra ID help extend user and app profiles with business-specific data. Learn how to configure them.
6 min read
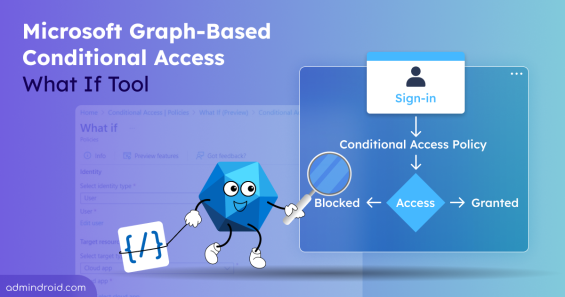
Explore the new Graph-based Conditional Access What If tool to evaluate policies with accurate sign-in context using Graph API.
6 min read

Ensure all users can complete multifactor authentication in Microsoft 365 to safeguard against account compromise.
5 min read

Learn the key differences between Microsoft 365 features to choose the right tools and avoid common pitfalls in security and management.
12 min read
Sysadmin Day is celebrated on the last Friday of July to honor sysadmins worldwide. AdminDroid thanks all sysadmins who resolved the CrowdStrike BSOD outage.
3 min read

Discover AdminDroid, your ultimate tool for Office 365 reporting, available on Azure Marketplace - Gain insights and manage your M365 environment efficiently.
2 min read
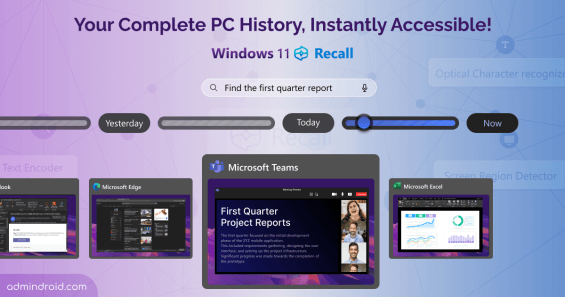
Windows 11 Recall is a feature of Copilot+PCs, which records everything you do, working in apps, browsers, live meetings and creates a photographic memory of PC
5 min read
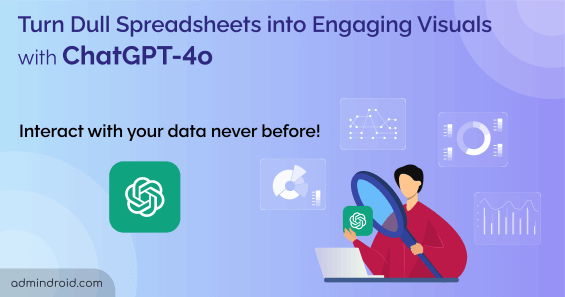
Generate insightful reports and create stunning visualizations from your spreadsheet data. Transform your data into visual insights with GPT-4o!
3 min read

Ensure a swift, ransom-free recovery for SharePoint, OneDrive, and Exchange with Microsoft 365 Backup feature!
6 min read

Microsoft enables you to set custom domain email notifications instead of "no-reply" system-based product address, making it as a internal communication.
3 min read

Get 10+ built-in Azure AD reports to understand your user's login activities and protect your Microsoft from evolving risks
13 min read

Enable DKIM in Microsoft 365 to retain your domain reputation and protect it from being phished or spoofed by impersonating hackers.
8 min read