As a pioneer of Microsoft 365, admins always have a never-ending list of questions for efficient Office 365 administration and management. Also, there will always be a restless mind-boggling for crystal-clear reports & deeper insights into your Microsoft environment! 😕 Don’t worry, the Microsoft 365 admin center reports have got you covered, enclosing every service report!
But unfortunately, enumerating reports for all Microsoft services under one hood will be much more arduous to understand and implement. 😩 So for your convenience and clarity, we have come up with the Microsoft 365 Built-in Reports – Blog Series setting the path in steps for the pathfinders.
With this series, find answers to all your questions on Office 365! From user activity reports to security and compliance, discover any information related to Microsoft 365 service reports under this series. Every service report and its significance will be recorded under these blogs.
🤝 Join us in this blog series, where we explore Microsoft’s in-built reports of various services within Microsoft 365. Each blog will focus on a specific service, providing valuable information and analysis of the built-in reports to optimize your Office 365 usage. Without further ado, let us get started with our very first service, Azure Active Directory (Azure AD).
Azure AD Reporting and Monitoring
Azure AD is Microsoft’s cloud-based identity and access management service, providing centralized control over user identities, controlling access, and more. Moreover, Azure AD acts as the backbone for authentication and authorization in the Azure environment. Therefore, monitoring Azure AD reports is crucial as it enables organizations to track user activities, identify suspicious behavior, detect security threats, and ensure compliance with regulations.
The multiple built-in reports in Azure AD provide a wide range of information regarding your Office 365 tenant, which is categorized below to ease your burden in monitoring.
- Track Microsoft 365 User Activities in Azure AD
- Monitor Risky Sign-ins in Azure Active Directory
- Check User Login Status with Azure AD Sign-in Logs
- Self-Service Password Reset Reports in Azure AD
- MFA Registration and Reset Event Reports
- Monitor Conditional Access Policy Changes
- Office 365 Group Reports in Azure AD
- Get Azure AD Devices Report in Azure AD
- Get Usage & Insights Reports in Azure AD
- Analyzing Azure AD Logs with Log Analytics
- Using Azure Monitor Workbooks in Azure AD
1. Track Microsoft 365 User Activities in Azure AD
- How to check user activity in Azure AD?
- How to check the user sign-in pattern, sign-in location, and number of sign-in attempts in Microsoft 365?
- How to see the login history on Office 365?
No worries if you can’t find the answer! Microsoft Entra admin center lends you a hand in this case! By monitoring user activity reports in Azure AD, you can solve all problems and questions regarding user actions, such as log-in patterns, sign-in locations, user creations, password changes, etc.
How to Track Office 365 User Activities in Azure AD?
Effortlessly track Office 365 user activities of your organization in Azure AD audit logs. Monitoring these reports makes you aware of the user creations, deleted users, updates applied to users, and many more.
More info- https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-audit-logs
Link to report- https://portal.azure.com/#view/Microsoft_AAD_UsersAndTenants/UserManagementMenuBlade/~/Audit
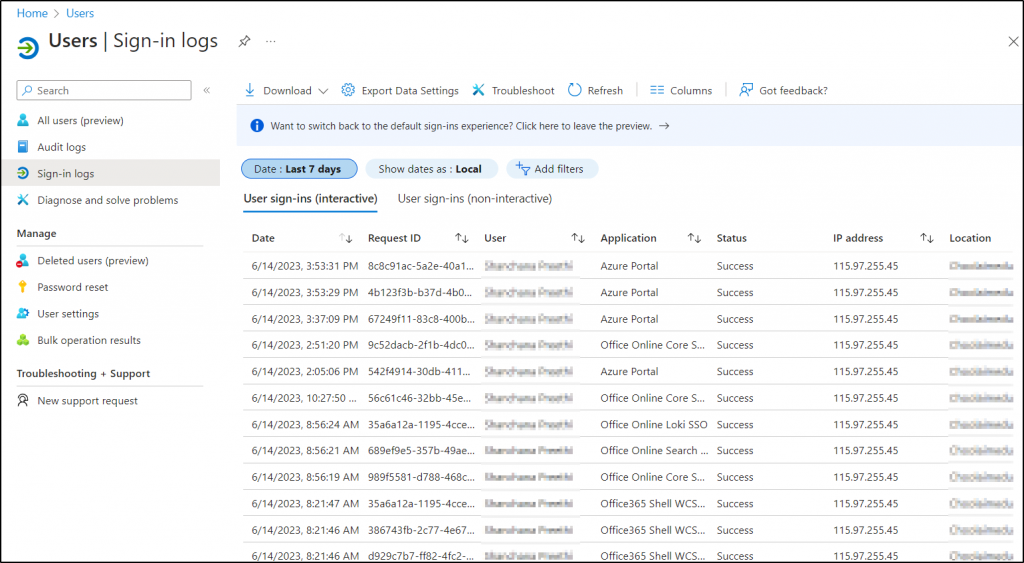
How to View Office 365 User’s Interactive and Non-Interactive Sign-ins?
All user interactive and non-interactive sign-ins can be viewed in Azure AD Sign-in logs under the Users page. With this report, you can analyze the sign-in pattern, user sign-in location, sign-in passes MFA challenges, etc.,
More info- https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-all-sign-ins
Link to report- https://portal.azure.com/#view/Microsoft_AAD_UsersAndTenants/UserManagementMenuBlade/~/SignIns
2. Monitor Risky Sign-ins in Azure Active Directory
Risky sign-ins present the highest level of risk, demanding immediate action to identify appropriate solutions. But if you’re stuck on questions like,
- How to view risky users report?
- How to check risky sign-ins in Azure?
- How to identify risky workload identities?
Then, here is the answer! Microsoft provides multiple reports in the Azure AD security dashboard to clear up all your doubts related to high-level risky sign-ins and audit users’ risky log-in attempts in Office 365. Yes, get clarified and continuously monitor them to circumvent any threat actor from barging into your Office 365 environment!
How to View Office 365 Risky Users Report?
1. The Microsoft 365 risky sign-ins report in Azure AD helps to find all risky sign-ins and the risk level of each sign-in attempt based on various factors such as user behavior, location, device, etc.
2. Monitor the Office 365 risky users report to identify users exhibiting high-risk behavior and understand the reasons behind it. This report provides comprehensive data on risk users, risk-remediated users, and risk-dismissed users. Therefore, by regularly reviewing these reports, admins can take proactive measures like
✅Resetting user passwords
✅ Blocking user sign-ins, or
✅ Dismissing users from the risk state
Link to report–https://entra.microsoft.com/Microsoft_AAD/SecurityMenuBlade/~/RiskyUsers/menuId/SecurityCenter?Microsoft_AAD_IAM_legacyAADRedirect=true
How to Get Reports on Risky Workload Identities?
Get the exclusive risky workload identities reports in Azure to detect major problems like leaked credentials, anomalous service principal sign-in activity, suspicious & malicious applications, and many more.
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/SecurityMenuBlade/~/RiskyServicePrincipals
How to Get Office 365 Risk Detection Reports?
Now get Office 365 risk detection reports in Azure AD that detect and display every risk with information like detection type, detection time, risk state, risk level, etc., to find the loopholes of the organization.
Apart from each risk detail, admins can also find risks triggered simultaneously and the sign-in attempt location to guard against the invading cyber-security risks.
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/SecurityMenuBlade/~/RiskDetections
3. Check User Login Status with Azure AD Sign-in Logs
Meticulously monitoring user login status is significant for eliminating potential threats and safeguarding organizational resources. In case if you are struggling with these queries,
- How to view the sign-in logs in Azure Active Directory?
- What are provisioning logs?
- How to check audit logs in Azure AD?
All your surfing and struggle for an answer is over now! Azure AD provides various reports to ease your burden in searching for answers to user login status queries. Admins can effectively monitor user sign-in patterns and sign-in activities, enhance security measures, and ensure that the organization has a proper baseline defense against sign-in risks by using these reports.
How to View Azure AD Sign-in Logs?
To enhance system security and keep track of various sign-ins in Azure AD, you can access the “Monitoring” section of the Azure AD page. Here you can monitor various sign-in types, including interactive sign-ins, non-interactive sign-ins, service principal sign-ins, and more.
- Therefore, regularly review the sign-in logs to identify any suspicious activities or potential security threats and stay vigilant.
More info- https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-sign-ins
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/SignIns
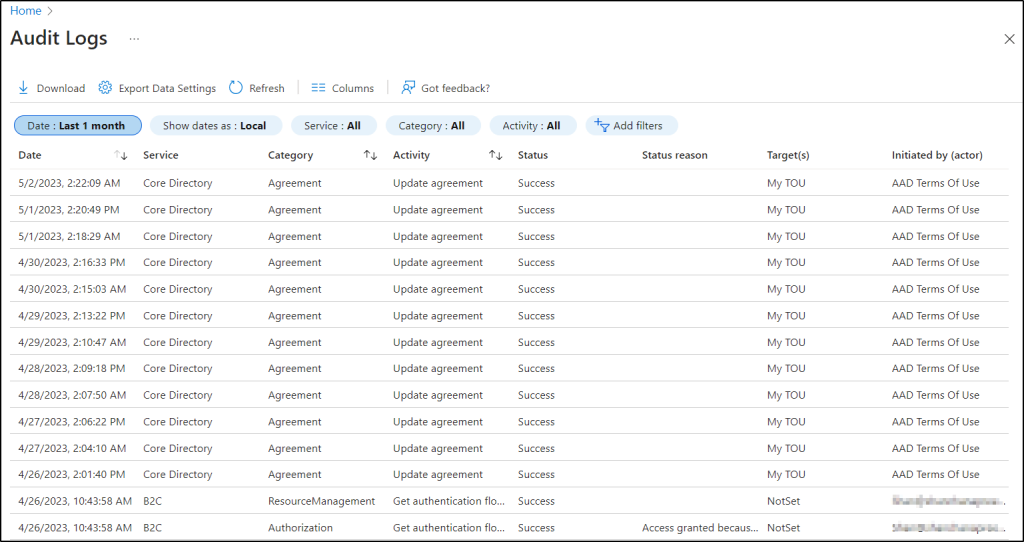
What are Audit logs in Azure Active Directory – Microsoft Entra?
The audit logs in Azure AD serve as a magnifier, enhancing your understanding of Azure AD activities! 🔍
The Azure AD audit logs provide admins with a convenient way to monitor and analyze various events within Azure AD. These events include changes to user accounts, password changes, and updates to users, groups, devices, applications, etc., under a single frame with much greater resolution. 💯
More info- https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-audit-logs
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Audit
How to Check User Provisioning Status?
User provisioning in Azure AD is a process of creating and managing user identities, roles, and permissions within the Azure Active Directory environment. To streamline user management, Azure AD implements third-party tools and automated mechanisms to provision users to the tenant.
Therefore, analyze the provisioning logs in Azure AD to furnish the details like the user provisioning status, source & target identifier, and action performed for troubleshooting various errors related to provisioned users.
Link to report- https://entra.microsoft.com/#view/Microsoft_AAD_Connect_Provisioning/ProvisioningEventsBlade?Microsoft_AAD_IAM_legacyAADRedirect=true
4. Self-Service Password Reset Reports in Azure AD
- What is the self-service password reset flow activity progress?
- How to check Azure sign-ins by authentication method?
Do these questions strike your mind while thinking about password reset? You can find a solution now on the ‘Azure AD password reset page’ for all your password-related queries. Therefore, monitor these reports to strengthen Microsoft 365 password policy within your organization.
How to Find Self-Service Password Reset Reports?
Azure AD audit logs under “Password reset” give explicit details on self-service password reset occurring in your Office 365. This helps admins to identify information like users registered for a password reset, count of reset, etc., under this report for password protection.
More info-https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-sspr-reporting
Link to report-https://portal.azure.com/#view/Microsoft_AAD_IAM/PasswordResetMenuBlade/~/Audit
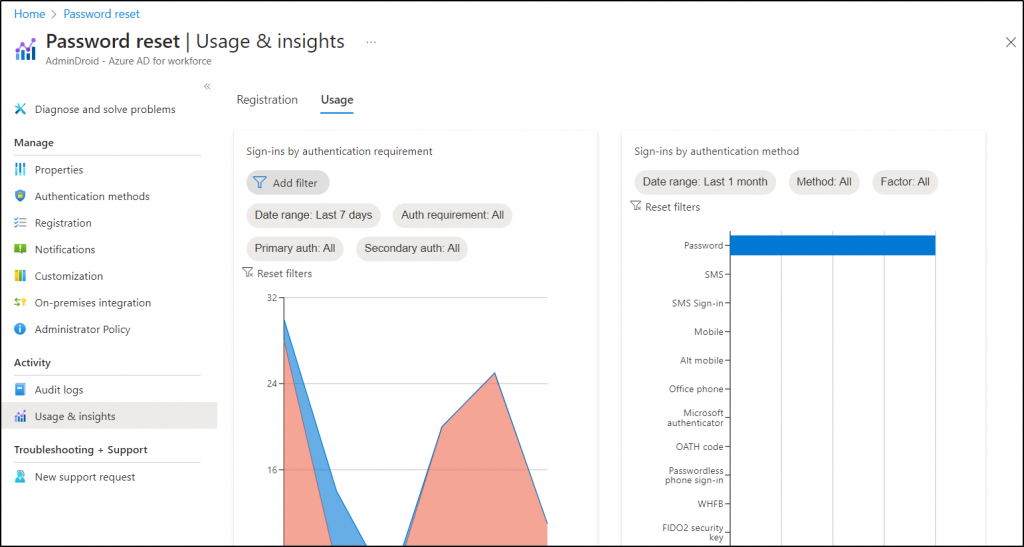
How to Track Password Changes and Reset in Office 365?
Now gain comprehensive visibility into the number of password changes and resets with “password reset reports”. Moreover, these reports offer visual charts that illustrate sign-ins and password changes by an authentication method for the last 24 hours, 7 days, or a month, enabling you to analyze trends and patterns effectively.
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/PasswordResetMenuBlade/~/UsageAndInsights
5. MFA Registration and Reset Event Reports
- How to Export Office 365 users MFA status?
- What are the authentication methods in Azure Active Directory?
- How to check the MFA registration status?
- How to audit Conditional Access policy changes?
Instead of brainstorming for answers, you can easily find all reports related to authentications, conditional access policies, and MFA registrations under Azure AD! 😌 Ultimately, monitor and analyze the reports to protect your organization from severe cyber security attacks targeted to bypass the authentication.
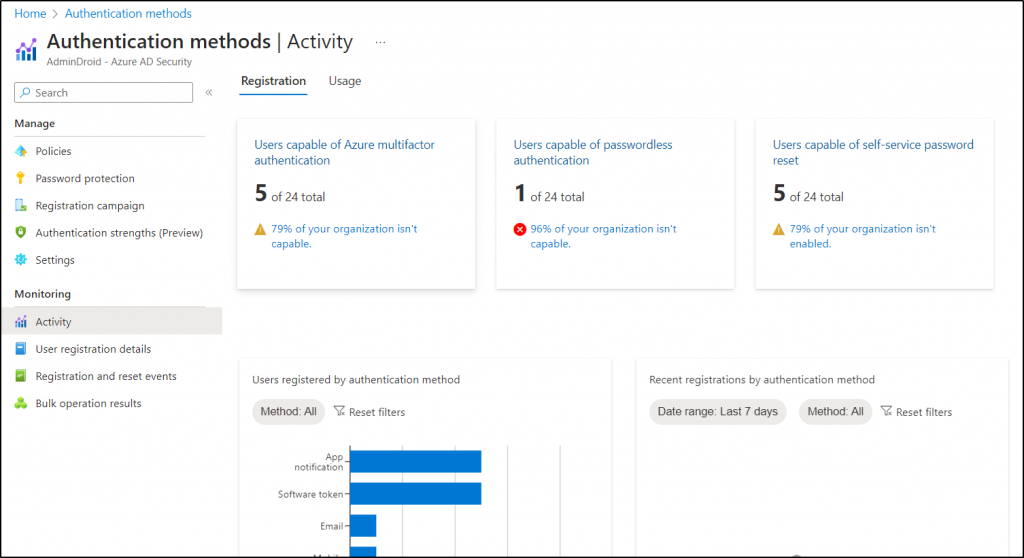
What is the Authentication Methods Activity Report?
Authentication methods activity report monitors & analyzes the usage of different auth methods, providing an overview of the auth methods used by whom and how often in the organization.
- Thus, track the registration and usage of all authentication methods with Azure AD reports on authentication methods activity. This report provides data on users capable of Azure MFA, password less, and self-service password reset. With the gathered information, admins can configure authentication methods policy for efficient auth management.
Link to report- https://portal.azure.com/Microsoft_AAD_IAM/AuthenticationMethodsMenuBlade/~/AuthMethodsActivity
How to Get MFA Activity Report?
Access the Multi-factor authentication activity report from Azure AD to monitor how your users authenticate at every single instance to access their account, applications, and resources in Office 365. Therefore, monitoring them continuously helps to safeguard your organization from rapidly evolving MFA attacks like MFA fatigue, MFA brute force attack, session hijacking, etc.
Link to report- https://portal.azure.com/Microsoft_AAD_IAM/MultifactorAuthenticationMenuBlade/~/ActivityReport
How to View the Azure MFA Registration and Reset Event Reports?
MFA registration and reset events report under the Azure AD Security section shows user registration of different auth methods. Also, it provides valuable insights into the activity related to user registration and password reset events in your organization. Admins can use this report to identify any recent registrations and resets made via compromised user accounts.
Link to report- https://portal.azure.com/Microsoft_AAD/AuthenticationMethodsMenuBlade/~/RegistrationAndResetLogs
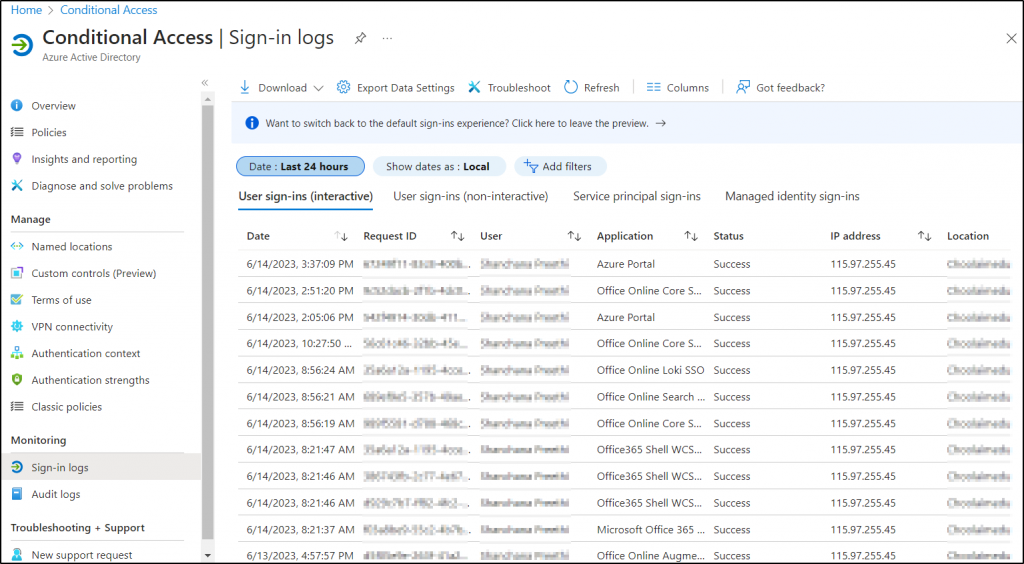
6. How to Monitor Conditional Access Policy Changes?
Keeping a close eye on those sneaky conditional access policy changes is like having a secret agent on duty, 👮♂️ protecting your organization’s security fortress! 🔐
Therefore, monitor conditional access policy changes to identify when users have passed the conditions, been blocked, or not satisfied the conditions imposed by CA, and more. With these reports, admins can spot suspicious tweaks, policy errors, or even malicious attempts to breach your defenses.
- So, grab your virtual binoculars, 🔎because monitoring conditional access policy changes to keep the bad guys out & your data safe from harm. There are different ways to spy on actions triggered by CA policies, and they are:
- Use Azure AD Sign-in logs to Analyze Sign-in behaviors due to CA policies.
- View CA policy Events using Azure AD Audit logs.
- Azure AD Conditional access insights and reporting workbook.
- Run Azure log analytics query to audit CA policies.
Link to report- https://portal.azure.com/#view/Microsoft_AAD_ConditionalAccess/ConditionalAccessBlade/~/Overview
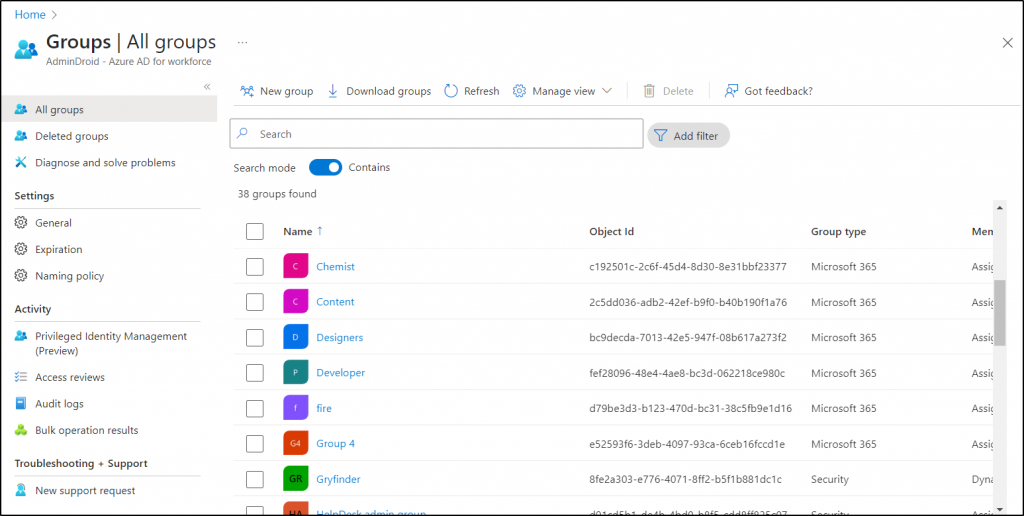
7. How to Get Office 365 Group Reports in Azure AD?
Are you puzzled about finding your way to Microsoft 365 groups? No worries, Azure AD directs you to the comprehensive Microsoft 365 group reports. With Azure AD’s granular group reports, you can find valuable information like group membership type, email, object ID, source, and many more, making group management a breeze! Whether it’s security groups, distribution lists, or dynamic groups, Azure AD reports will reveal them all! 💯
Thus, examine all group creations, deletions, modifications, membership changes, and license changes simply with this report for enhanced group management.
More info- https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/how-to-manage-groups
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/GroupsManagementMenuBlade/~/AllGroups
8. How to Get Azure AD Devices Report in Azure AD?
Find all registered Azure AD devices with drilled-down details like device name, OS version, join type, compliant devices, etc., for centralized device management and to reduce & manage stale devices.
More info- https://learn.microsoft.com/en-us/azure/active-directory/devices/device-management-azure-portal
Link to report- https://portal.azure.com/#view/Microsoft_AAD_Devices/DevicesMenuBlade/~/Devices/menuId~/null
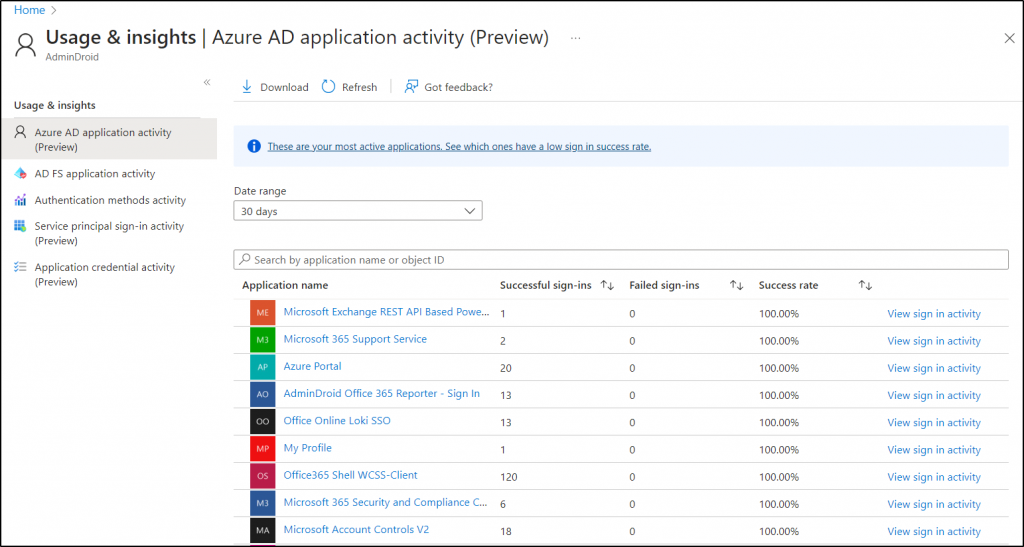
9. What is the Purpose of Azure AD Usage & Insights Reports?
🔭Azure AD Usage & Insights Reports are a powerful telescope that grants you an eagle-eyed view into the application usage within your Office 365 tenant. This report offers insights on authentication methods, service principals, and credential activities, helping you identify the most failed sign-ins and popular applications. Overall, admins can use this report to make informed decisions, optimize application usage & enhance security. It offers the following reports:
- Azure AD Application Activity Report (Preview)
- AD FS Application Activity Report
- Authentication Methods Activity Report
- Service Principal Sign-In Activity (Preview)
- Application Credential Activity Report (Preview)
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Insights
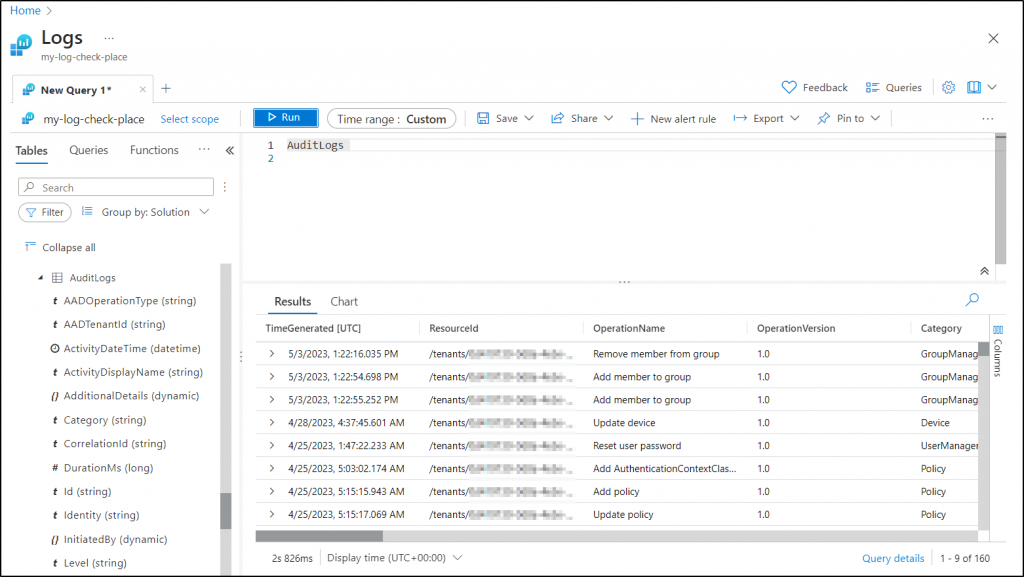
10. Analyzing Azure AD Logs with Log Analytics
- What are Azure Log Analytics used for?
- Where are Azure diagnostic settings?
Do these clueless queries hit hard on you? Drop your worries, look for the Azure Monitoring page in Azure AD to find all the answers about the diagnostic settings and log analytics workspace.
What are Diagnostic Settings in Azure AD?
Usually, diagnostic settings in Azure Monitor are used to transport Azure metrics and logs to different destinations, and a single diagnostic setting can only define a single location. These settings play a crucial role in analyzing audit logs, sign-in logs, directory logs, and password change events.
Logs and metrics can be sent to Azure Monitor Logs, Event Hubs, or Storage Accounts for analysis and visualization, aiding in issue troubleshooting and anomaly detection. This, in turn, helps monitor the health, performance, and usage of Azure AD resources.
More info- https://learn.microsoft.com/en-us/azure/azure-monitor/essentials/diagnostic-settings?tabs=portal
Link to report – https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/DiagnosticSettings
What does Azure Log Analytics workspace do?
The Log Analytics workspace allows you to run and edit KQL queries based on Azure Monitor logs. It provides valuable insights into user activities, security events, and compliance-related information within their Azure AD environment.
More info- https://learn.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-tutorial
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Logs
11. What is an Azure Monitor Workbooks?
Azure Monitor Workbooks is a feature in Microsoft Azure that allows you to create & customize interactive reports and dashboards to visualize data collected by Azure Monitor. With Azure Monitor Workbooks, you can track user behaviors, identify security issues, and generate Azure AD reports that meet your specific needs, all within a centralized monitoring an reporting framework.
More info- https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/overview-workbooks
Link to report- https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Workbooks
To sum up, leveraging built-in Azure AD reports not only aids in detecting and addressing security issues but also empowers informed business decisions through valuable insights.
Become an Expert in Azure AD Reporting with AdminDroid!
You might be tired of shifting through multiple tabs to track user login activities. Would you rather have separate reports on multiple login activities rather than having to filter them under a single tab? 👀 Then here comes the AdminDroid Microsoft 365 reporter to help you out with Azure AD reporting.
AdminDroid now breaks down all the Microsoft Entra insights into crystal-clear reports. And in the case of Microsoft 365 user login reporting, it provides complete history like user login history, login IP address, login status, etc., to monitor all your user entries completely, without leaving a trace! In general, the Free Azure AD reporting tool by AdminDroid gives 190+ reports to have a 360-degree view of your Azure environment for enhanced Azure AD management.
Overall, AdminDroid is a dedicated tool solving IT admins’ challenges with 1800+ comprehensive reports 📊 and 30+ visually appealing dashboards on various services like Azure AD, Exchange Online, Microsoft Teams, OneDrive, SharePoint Online, and Yammer.
- Moreover, AdminDroid offers unique features which will leave you amazed! Set up custom alerts on risky sign-ins, log-ins from unknown locations, unauthorized device access, and many more suspicious activities with the AdminDroid alerting feature. Identify and mitigate Microsoft 365 issues instantly with this alerting feature! ⚠️
- Then, advanced customization filters are available in AdminDroid to make your filtering process a breeze! Now generate crystal-clear reports as per your requirements with this filtering feature.
- With granular access delegation, admins can now split their workload and set their focus on more important tasks. Above all, they can automate report generation and effortlessly access them from anywhere with AdminDroid scheduling.
Start exploring AdminDroid now with a 15-day trial to have an amazing hands-on experience in Office 365 reporting. Envision your entire Microsoft 365 reports with AdminDroid!
I hope this blog helped you to dive deeper into Azure AD built-in reports and their ultimate purposes. Drop your thoughts in the comments section.
Stay tuned for the exciting reports of the next Microsoft 365 service!






