On Day 1 of Cybersecurity awareness month, learn to conceal your organization from cyber threats today. Stay tuned for upcoming blogs in the Cybersecurity blog series
In this digital era, everything gets digitized and widely used by everyone. Likewise, tricky hackers are evolving more, and their techniques get multiplied periodically. Although Microsoft comes up with advanced security solutions over time, hackers try to bypass them through a tiny loophole that we might not know about in our security checklist. Most hackers target small and medium businesses, as they might not upgrade to advanced security solutions like large enterprises. They trickily target the least privileged users like interns or vendors to get as much information as they need from your Microsoft 365 environment. They steal the organizational user details, privileges, used devices, device details like OS, device type, and other personal information. Then they hack the user account and steal the organization’s data.
Insider threats are not viewed as seriously as external threats, like a cyber-attack
– Larry Ponemon
So, we need to have a sharp eye on users’ access rights in the organization and ensure whether they have access to sensitive resources in any way. One of the loopholes is the Microsoft Azure Portal. As the Azure portal contains all the information about users, groups, devices, admin roles, configuration details, and more, hackers can smartly gain the required info.
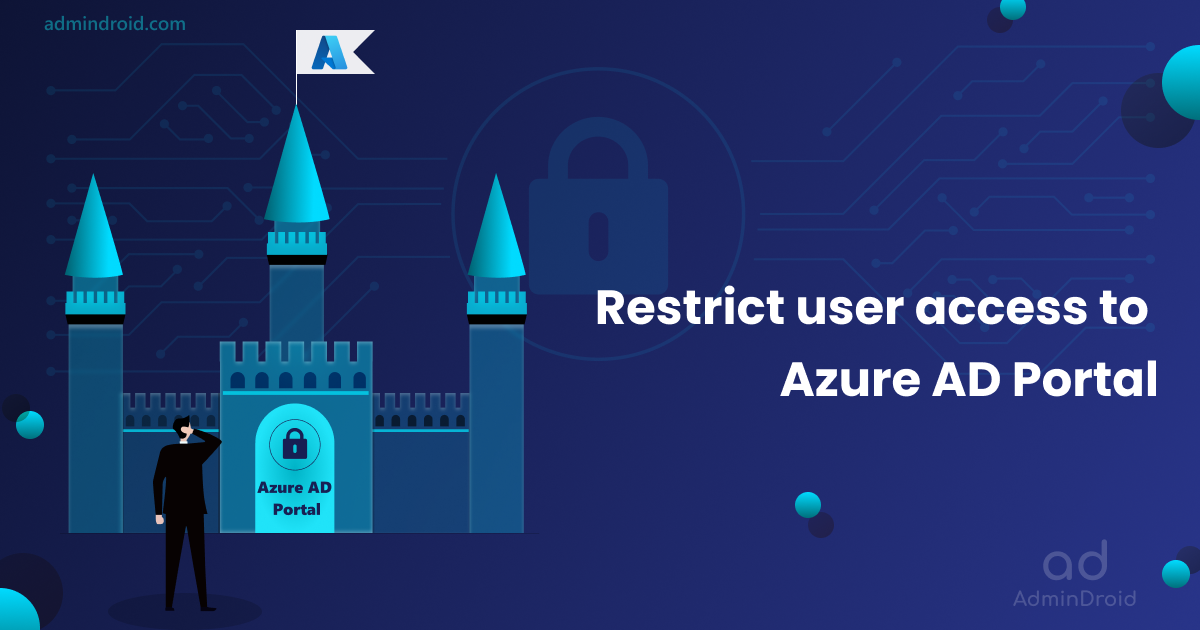
Is Azure AD Portal Open to All?
Yes! We may think only users with adequate privileges can access the portal and modify any settings. Do you know that a non-admin can access the Azure portal? Though they can’t change any settings, they can view the user info, group info, device details, user privileges, etc., by navigating portal.azure.com. Thus, hackers can gain all these details through any unprivileged user in the organization without much effort. Isn’t it hazardous?
How To Restrict User Access to Azure AD Portal?
You can restrict users without administrative privileges from accessing the Azure AD portal using the steps given below.
- Sign
- Select Users –> User Settings
- Move the toggle to ‘Yes’ under the Administration Portal.
- Select ‘Save’ in the top.
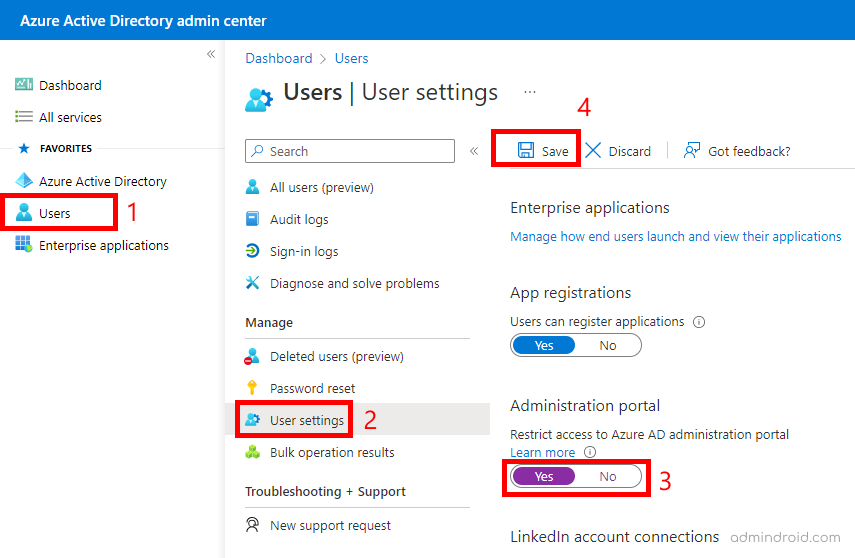
Now, the non-administrators can’t access Azure AD portal by navigating portal.azure.com.
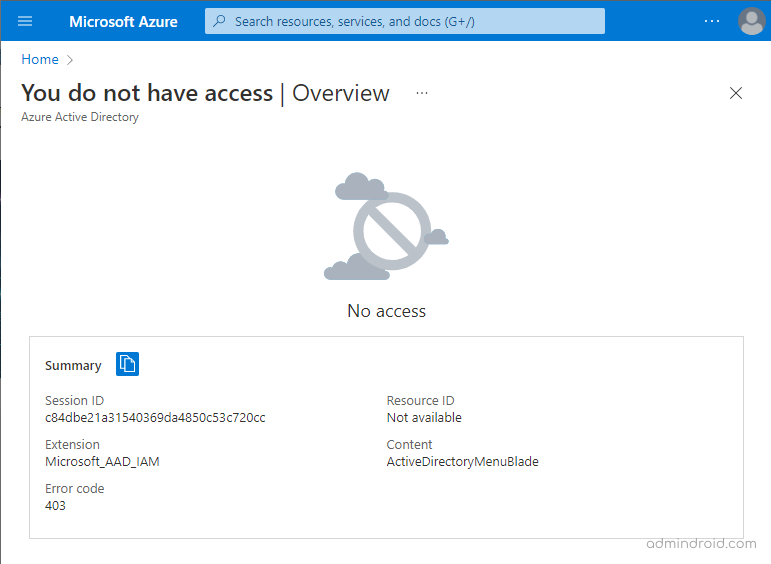
Wait! Do you think it’s all done? Has the user restricted completely? As an admin, we should always think out-of-the box while securing data against cyberattacks. Just think, is there any other way in which users get in?
Yes, it is! Another prominent thing we should consider is Microsoft Entra. It was introduced by Microsoft recently through which users can also access Azure portal.
Has Microsoft Entra Holds Azure Active Directory?
Microsoft developed Entra to manage all the Microsoft identity and access efficiently across hybrid and multi-cloud environments. It extends its hands broader to Azure Active Directory, GCP, and AWS. Thus, users can access Azure Active Directory by navigating entra.microsoft.com and access the necessary info.
Why should we consider Entra after blocking Azure Portal access in Azure AD?
Previously, Microsoft Entra had no concern on Azure portal settings. Even if we restrict access in Azure AD admin center, users can still access the portal through Entra admin center. After contacting Microsoft Support, we found that the only way we could do is to restrict the Entra portal access in the local firewall. Don’t worry! Now, Microsoft addressed the severity and adds value to the Azure AD settings. Now, users can’t access the Azure portal through the Entra admin center too.
Are we done securing Azure AD data?
No, this doesn’t stop here.. A hacker don’t use GUI!
The above works well for end users who don’t use tech tools. However, if a hacker gains access to one such account, then they can use the readily available PowerShell modules such as MSOnline, AzureAD, etc. to get what they want! 😮Don’t worry, we don’t leave you here with this.
How to Restrict access to MSOnline PowerShell?
Though MSOnline is a pretty old PowerShell module to use, due to the introduction of AzureAD and Microsoft.Graph modules, it still gives data. That is enough for a someone who needs something, Right? A hacker would say yes.
So let’s jump in and see how we can restrict users from viewing others’ data from MSOnline. Just three lines of PowerShelling, and you’ll be done.
Install-Module MSOnline
Connect-MsolService
Set-MsolCompanySettings -UsersPermissionToReadOtherUsersEnabled $false Now, that we have successfully defended our company from MSOnline module attack, let’s enter the AzureAD battle zone.
How to restrict users from using AzureAD PowerShell module?
Let’s play with Apps now. It’s great that Microsoft has designed it as an application, we simply have to set who can access this application. Tada, others are restricted from accessing. 👏
Microsoft has backed me up by preparing a PowerShell script to do this!
Finally, are we done securing Azure AD data at least now?
Not yet; there is still more. We’ll come up with a few more blog posts to address as much as possible. Stay tuned!
Apart from restricting users from accessing Azure AD, it is prominent for admins to monitor users’ sign-ins into the Azure portal and identify suspicious sign-ins & sudden hikes. Though the native sign-ins report provides sign-in details, it is inadequate for monitoring sudden hikes, valuable insights, etc. By utilizing the AdminDroid Azure AD auditing tool, get all the sign-in info with greater insights at your fingertips.
Now, look at
How AdminDroid Helps You Identify Azure Portal Sign-ins?
AdminDroid never leaves admins in a hitch when it comes to monitoring their Microsoft 365 environment. It provides the user’s sign-in analysis with in-depth details and appealing insights to visualize every sign-in from all possible aspects.
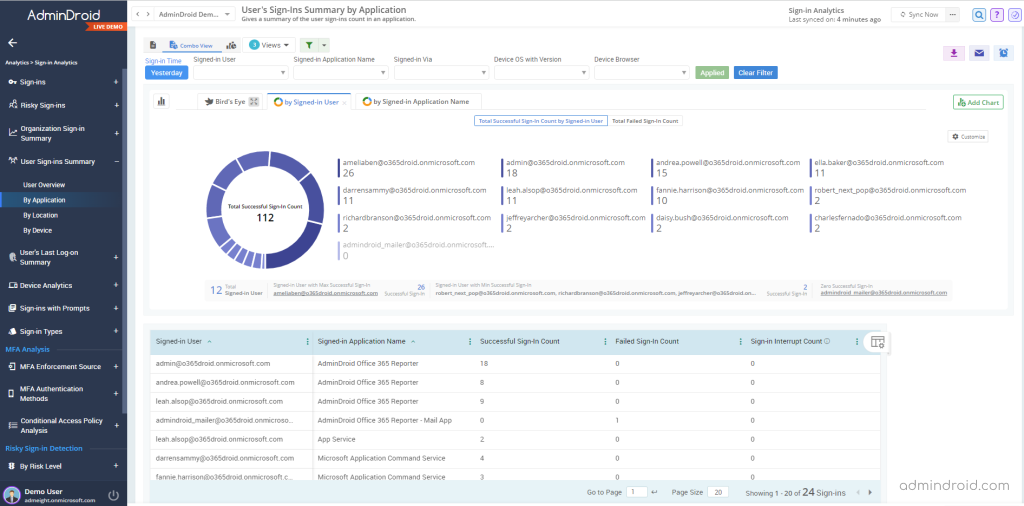
User’s Sign-in Summary by Application
You will get each user’s sign-ins in every application separately, from which you can filter ‘Azure Portal’ to get your desired results. Additionally, you can monitor the user’s sign-in count, failed count, and sign-in interrupt count in the Azure portal to help you find sudden hikes in failures.
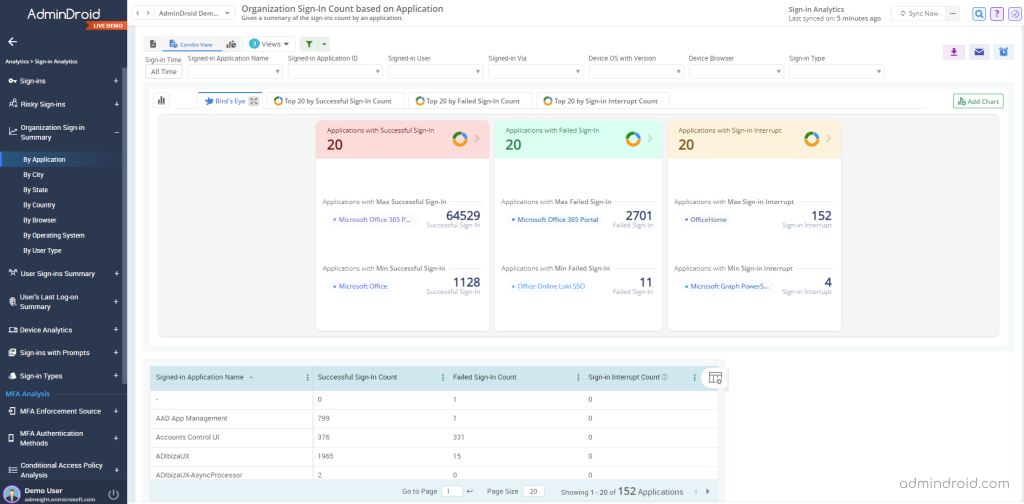
Organization’s Sign-in Summary by Application
Get an overview of successful & failed sign-in count, and sign-in interrupt count for each application from this report. It will give you a bird’s eye view of your organization’s application sign-ins.
Furthermore, AdminDroid provides more sign-in reports, including failed sign-ins, device sign-ins, risky sign-ins, last logon details, MFA analysis, and so on. Thus, you can monitor Azure AD sign-in logs in your organization without missing any aspects.
How Will You Benefit from Using AdminDroid Free Azure AD Reporting Tool?
- Gain every aspect of the organization’s sign-ins with crystal clear details and valuable insights.
- Get your desired results by filtering the report data and saving it as a View for future reference.
- Schedule any report to monitor risky sign-ins at your preferred time.
- Create customized alerts to get instant notifications of suspicious sign-ins.
Besides Microsoft 365 sign-in details, AdminDroid provides 190+ free Azure AD reports to visualize users, licenses, subscriptions, groups, applications, directory details, MFA, CA policies, and more in the organization. Elevate your Azure AD management more than ever with AdminDroid. Check it out now!
I hope we’ve made you aware of possible unwanted exposure of Azure AD data, and also the steps to secure from all those weak links. Share your thoughts or ideas in our social media pages. Mission on!