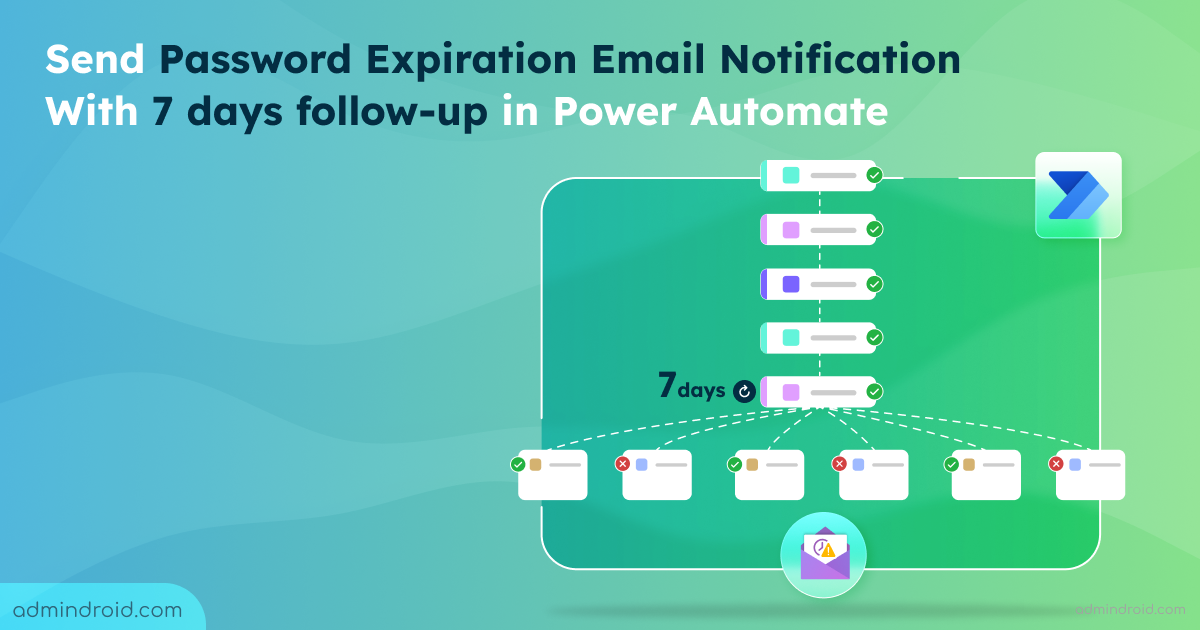
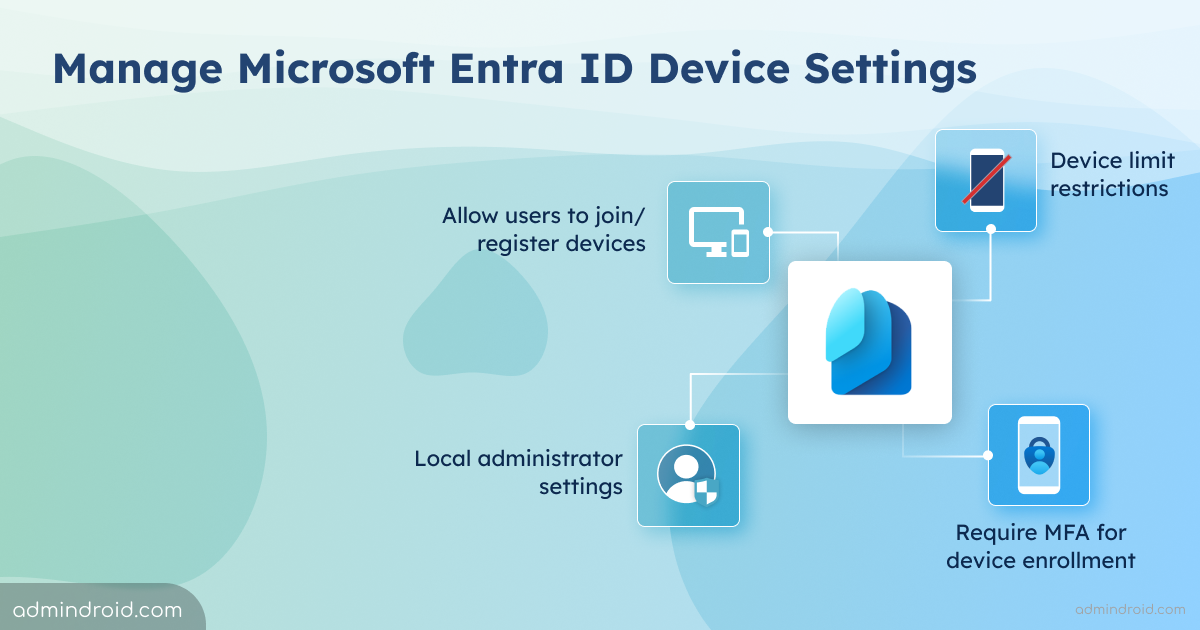
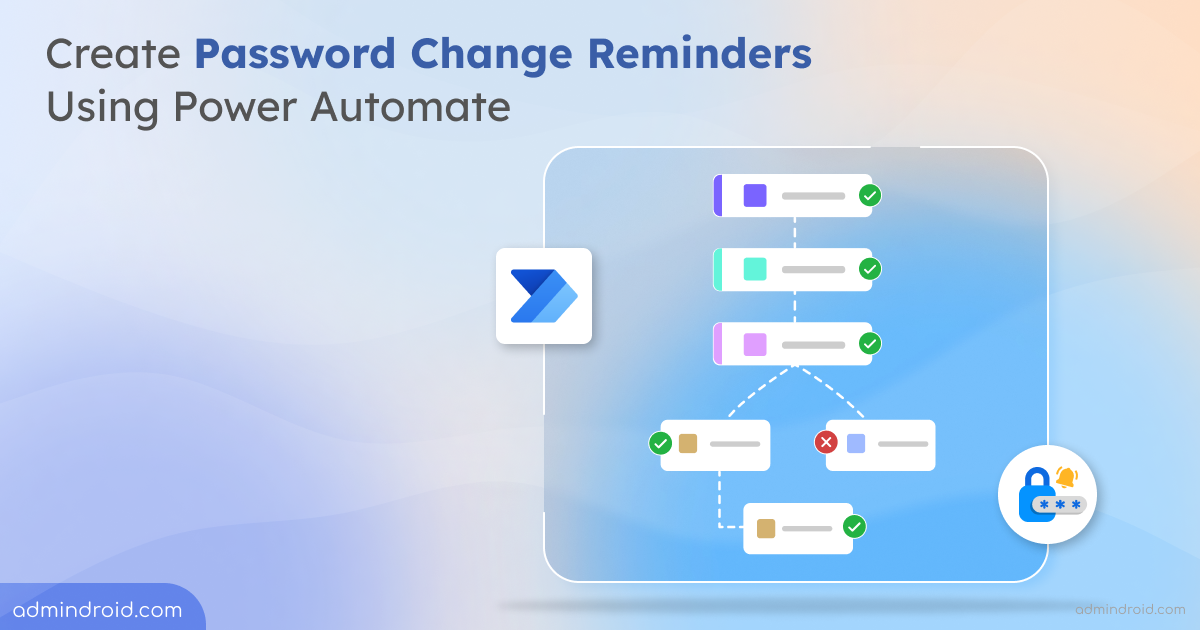
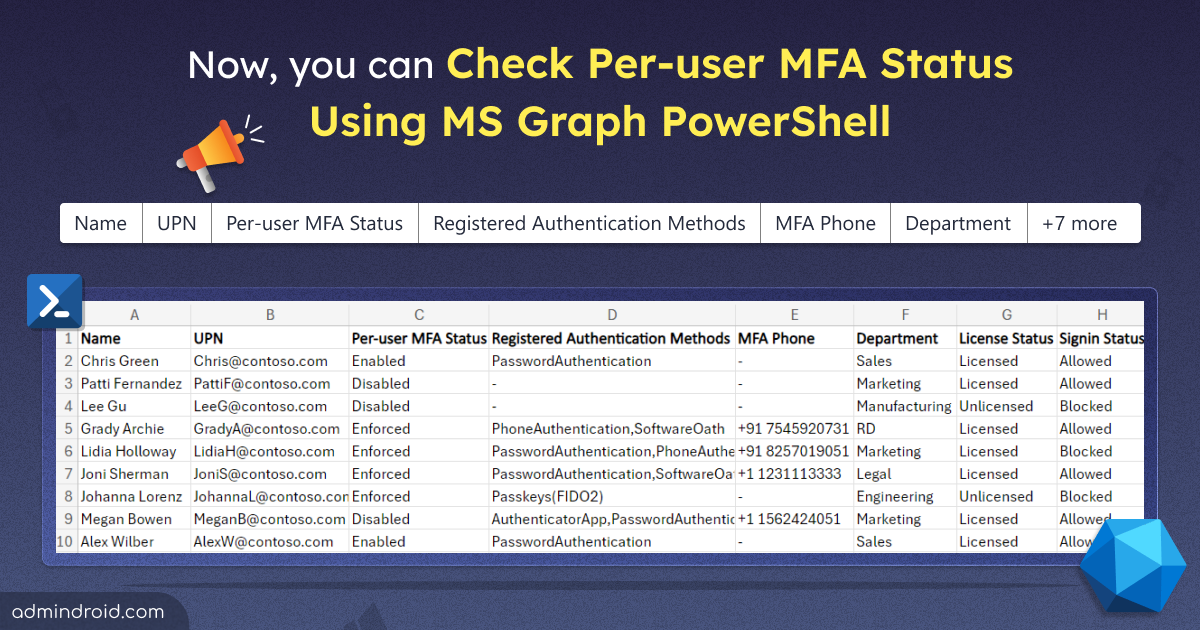
Statistics show that password-related issues are among the most common helpdesk calls💻📞. Implementing an automated process can reduce helpdesk call volume and associated costs. In our previous blog, we discussed how to create password change reminders using Power Automate . One of the most requested Power Automate flows for password expiry is follow-up emails✉. In this…