It’s the season! Did I say about the fall? Or did I say about the Halloween season? Nah, it’s time for Cybersecurity Awareness Month!
As work becomes increasingly digital, so are cyber-attacks. Researchers estimate that social engineering and phishing attacks account for 75% of cyber-security threats. Moreover, we’ve noticed a crucial vulnerability called the MFA fatigue attack ruining MFA purposes, so we dug up the hidden MFA security features that empower security standards. Therefore, it is essential to consider cyber security seriously today.
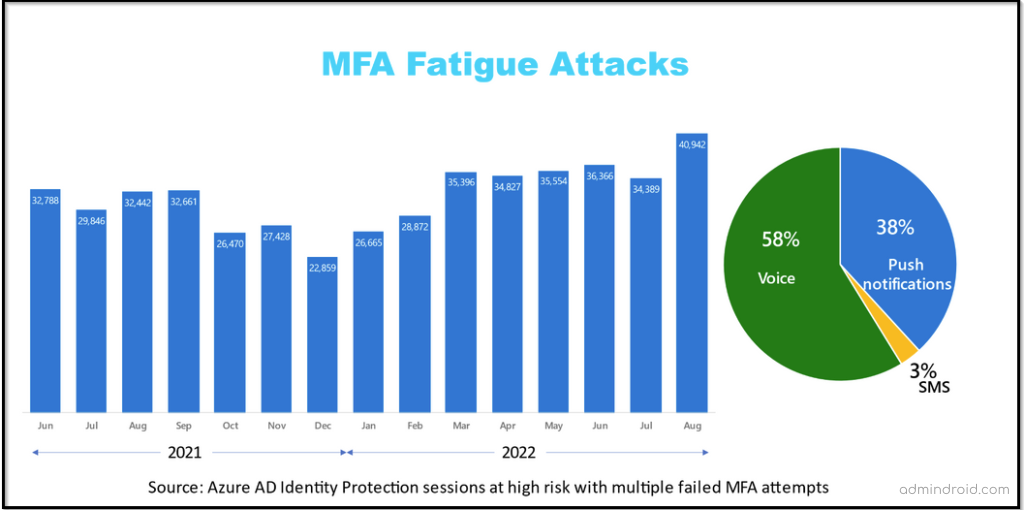
On top of that, two similar events take place in the same month. A double shot! So, this makes it a perfect time to implement the best security practices. Cybersecurity is spookier than ever, so let’s get started.
This October, Cybersecurity Awareness Month, we encourage everyone to share information about digital security and engage people around them with safety practices. Even though bypassing accounts, attempting data breaches, or tampering with our devices becomes harder now, it might feel like you have no power! Don’t panic, though. Because it’s not what you think of. It’s easy to stay safe online!!
Yes, you heard it right! By taking simple steps against cybercrimes in your daily routine, your organization can get protected massively. Understanding the importance of cyber security is good, but taking steps and implementing safety practices upfront is even better.
There are only two types of companies:
Those that have been hacked,
And those that will be.
–Robert Mueller
Don’t be among those two types, try to stand out of the line! So, we’ve mapped out a perfect way to bring awareness about cyber security and put constant effort into staying safe and secure online.
To make Cybersecurity Awareness Month more effective, we DROIDIANS will assist you with several key steps for safeguarding your Office 365 environment from hackers💢.
It’s going to be 31 DAYS, 31 BLOGS about security measures to be taken for Office 365 environment🎗️
What Recommendations Are We Going to Provide?
Thinking about what’s in the load? Here are some of the things you can expect from this series:
- With this series, you’ll gain more ideas on unknown and hidden security settings in Office 365 rather than stressing the most used and known features, such as using strong passwords, enabling MFA, staying updated, etc.
- Moreover, Microsoft 365 Defender and Security & Compliance Center cover every security measure your organization should take. However, most of the tenants don’t use the enterprise packs. So, keeping this in mind, this series will cover the security settings under the Business suite and extend it further to enterprise licenses.
- We will be focusing primarily on Office 365 security and its solutions, so you probably won’t see much brand-promotional content.
Our goal is to identify the top M365 security threats to your business and put forth the simplest to stay secure. So, we encourage you to GET INVOLVED with us for this entire Cyber Security Awareness Month and implement the steps we guide to prevent the emergence of suspicious attacks.
Ready to join us? Almost, it’s time to ruin the suspicious attacks of cyber criminals!
Essential Toolkits for Better Office 365 Security:
Day 1: Restrict user access to Azure AD portal.
As the Azure AD portal contains all the organization information, being viewable to users is one of the weakest security links. So, we should restrict the non-admins from accessing the Azure AD in the organization.
Day 2: Block email auto-forwarding to external domains.
When an account is compromised, a forwarding rule may be created for a particular mailbox, despite the fact that the user isn’t aware of the forwarding. It is therefore essential for admins to allow automatic forwarding only for those users who really need it, while blocking others.
Day 3: Ban custom passwords using Azure AD password protection.
Often Office 365 users are instructed not to use weak or easily-hackable passwords. But still, simple and insecure passwords are used, which increases password-related attacks. To avoid such attacks, administrators can ban custom passwords for their organization using Azure AD Password Protection.
Day 4: Break Glass Account for Office 365 Login During Emergency Situations.
Office 365 admin accounts can become stuck due to an MFA outage or incorrectly assigned conditional access policies. In this case, what will you do? Do we have any way out? Yes, it’s possible! You can have a break glass account in your organization- “An account with MFA Disabled and set up with a strong password.”
Day 5: Manage user consent to applications in Microsoft 365.
In Office 365, user consent to apps is allowed by default. This default setting will pose severe security threats if the admin hasn’t checked and managed this setting. Thus, secure your O365 organization from consent phishing attacks by managing user consent to malicious apps.
Day 6: Possible Ways to Limit External Sharing in SharePoint Online.
When considering Office 365, the average organization shares documents with external domains, which include business partners and personal email addresses. So, we should always keep an eye on external sharing configurations in SharePoint Online and OneDrive.
Day 7: Use Phishing-Resistant MFA to Implement Stronger MFA Authentication.
Have you checked out this new update? Microsoft has released a new grant control called “require multifactor strength” in Microsoft conditional access policies. Hereafter, you can opt to allow SMS for base-level workers and implement stronger phishing-resistant MFA for admin & executive accounts. As of October 2022, this MFA setting is in “preview” mode.
Day 8: Easy, Yet Efficient Solution to Avoid Data Leakages: Idle Session Timeout.
Since hybrid initiatives have grown in enterprise businesses over the past few years, admins have been shocked to learn that employees often forget to sign out after checking their emails on Outlook on the web or accessing a document from SharePoint, which results in data leaks. Configure Idle Session Timeout policy to automatically sign out users on unmanaged/personal devices if they are inactive over a configured period.
Day 9: Securely Connecting through Microsoft Teams Meetings.
When things change into the virtual mode, data protection methods must also be changed. Microsoft Teams Meetings are the place where we discuss important information about the organization. Thus, the data related to a meeting must be protected. Thus, Microsoft Teams meetings can be safeguarded by configuring meeting policies and settings. You can define and control these policies via the Microsoft Teams Admin Center or by using PowerShell.
Day 10: Protect Your Organization from Outlook Phishing Attack using External Email Tagging.
In phishing attacks, attackers send emails pretending to be trusted persons or organizations. By adding an external email warning tag in Outlook, admins can prevent users from clicking malicious links and attachments sent by external users.
Day 11: A Guide to SPF, DKIM, and DMARC to Prevent Spoofing.
Without strong email authentication policies, domains may get a high chance of being spoofed by attackers. To retain our domain reputation and trust, and to safeguard our domain, we need to configure SPF, DKIM, and DMARC based on the organization’s requirements.
Day 12: Tag and Protect Priority Accounts in Microsoft 365.
Priority accounts are users in an organization who manage sensitive information such as financial data, product development information, etc. More precisely, these users are C-level or D-level executives other than regular employees. Applying Priority account tags to these users helps to target your most important data reports.
Day 13: An Admin’s Guide to Review App Permissions & Consents in Microsoft 365.
A single malicious application in your Office 365 organization will exploit all resources and sensitive data. Thus, Admins should be aware of those consent phishing attacks and review permissions granted to the application. They should delete the malicious app as soon as identified with illicit permissions.
Day 14: Make Sure Your Confidential Teams Calls Are End-to-End Encrypted.
In the past decade, businesses worldwide have lost billions in revenue as a result of high-profile hacks and phishing attacks. These attacks are done by targeting mostly employee emails, texts, and phone calls. As we know, many users rely on Microsoft Teams every day, trusting the platform implicitly. To avoid such undesired attacks, enabling end-to-end encryption is a key step in protecting organizations from hackers. It works by encrypting messages at both ends, the sender and receiver, so one in the middle can read your messages.
Day 15: Prohibit Unmanaged Devices Accessing SharePoint and OneDrive to Prevent Data Exposure.
Unmanaged devices in Microsoft 365 can pose a security risk as it is not compliant. So, admins need to block unmanaged devices from accessing SharePoint and OneDrive to protect the data securely.
Day 16: Unified Audit Log: A Guide to Track Office 365 Activities.
We must track the activities happening in our organization to prevent security flaws. You can use a unified audit log to track these activities. Unified Audit logs are an added layer of surveillance that provides deeper insight into activities happening in the office 365 organization. It provides details about all the activities, with who performed them and when.
Day 17: Empower Your Microsoft 365 Security with Least Privilege Access.
Researchers estimate that improper access control leads to the loss of millions of dollars each year. So with the rise of cyber threats, organizations must change their cybersecurity strategies and implement security measures such as least privilege access. Having less access privilege reduces security risks and business disruptions. Moreover, the zero-trust strategy relies heavily on least privilege access to achieve its objectives.
Day 18: Use Free Office 365 Test Tenant to Test New Features and Scripts.
Through Microsoft 365 Developer Program, admins can get a free Office 365 tenant. It will help to simulate a small corporate environment to test scripts, install apps, and explore the new configurations without affecting the production environment.
Day 19: SharePoint and OneDrive Integration with Azure AD B2B.
By integrating SharePoint and OneDrive with Azure AD B2B, the external sharing experience can be upgraded to automatically enforce conditional access policies such as MFA on recipients that act as an additional layer of security for shared items.
Day 20: Monitoring Azure AD Sign-in Logs and Risky Sign-In Activities.
Unusual sign-ins, frequent login failures, and sign-ins from different locations may pose severe security threats to your Office 365. Thus, it is crucial to review the Azure AD Sign-in logs and identify the risky sign-ins to safeguard your O365 organization.
Day 21: A Complete Guide to Secure a Compromised Microsoft 365 Account.
Recently, remediating compromised accounts is the most commonly raised security support request among Microsoft 365 users. Since corporate accounts compromised by credential theft are vulnerable to malicious attacks, it is important to know how to spot the warning signs and how to prevent them from being compromised.
Day 22: Microsoft 365 Alerting – Detect and React to Threats Instantly
Microsoft provides default alert policies and has a provision to create custom alert policies to meet your security needs. Ensure that you utilize them effectively and stay updated on suspicious events, anomalies, unusual activities, and risky happenings in the organization.
Day 23: Guide to Setup Office 365 Password Policy in Azure AD Password Protection.
Most organizations don’t take passwords seriously, and users probably use easy-to-remember passwords. So, there happens the rise of numerous brute-force attacks, password spraying, etc. Therefore, it is of utmost importance to implement a strong Office 365 password policy and prevent your organization from suspicious attacks.
Day 24: A Quick Checklist to Make Mailbox Auditing More Efficient in Office 365.
We all know that Exchange mailbox auditing is enabled by default. But it doesn’t mean that all the activities are recorded by default. There are a few considerations that require admins’ attention for effective mailbox auditing. Admins need to check and configure settings to lessen or eliminate threats and identify security breaches.
Day 25: Microsoft 365 Company Branding – An Easy Way to Avoid Phishing Attacks.
Attackers often try multiple suspicious phishing strategies to compromise your Office 365 login credentials and may access your sensitive data. They recreate fake login pages like a default O365 login page and cleverly steal your login info without your knowledge. Beware of these types of fake login pages and configure Microsoft 365 company branding to reduce credential phishing.
Day 26: Boost up Your Security Posture with Microsoft Secure Score.
Security and integrity of data are paramount when your organization uses a cloud platform. Since more organizations are migrating to cloud solutions, it is raising concerns about data security, especially when ransomware attacks are on the rise. As a result, Microsoft came up with a simplified analytics tool to ensure that security is optimal. With all these new threats evolving, now it’s time to review your security posture with the Microsoft Secure Score!
Day 27: Mailflow Status Reports to Secure Microsoft 365 Emailing Process.
It is highly essential to track the mail flow in order to enhance the email security of your M365 users and your organization. Keeping track of the mail flow reports in the Microsoft 365 Defender portal and Exchange admin center would help us to be aware of the organization’s email collaboration.
Day 28: Office 365 Offboarding Best Practices.
When an employee leaves Office 365 organization, the IT admin must follow the proper offboarding procedure to avoid losing critical business data. An effective offboarding process involves blocking former employees from accessing company files, preserving the documents they created, and performing several other admin tasks associated with removing a user. It also helps you meet your business and legal requirements.
Day 29: Azure AD Continuous Access Evaluation – Why is it important?
Azure Active Directory offers a variety of security features to ensure security in organizations. One such feature is Continuous Access Evaluation.
Continuous access evaluation is the mechanism of a two-way conversation between the token issuer (Azure AD) and the relying party (client app). This setting is enabled by default and we can use conditional access policies to disable it. Currently, CAE is available for Exchange, Teams, and SharePoint Online which are referred to as CAE-capable clients.
Day 30: Enable Passwordless Authentication with Temporary Access Pass.
Passwordless authentication streamlines user interactions while enhancing security posture. With the start of passwordless authentication, Temporary Access Pass (TAP) has also rapidly come into existence. Temporary access pass (TAP) aids in onboarding passwordless authentication methods and aid in recovering access to accounts when a device is lost or stolen without requiring the authentic password login method.
Day 31: A Guide to Microsoft 365 Forensic Investigation.
Microsoft DART team makes use of various forensic artifacts in Microsoft 365 during a forensic investigation. Figure out where to find the forensic artifacts and what are the challenges in Microsoft 365 environment.
We’ll keep updating the list every day, so subscribe now to get notified! 🔔
Reddit: reddit.com/r/AdminDroid/
LinkedIn: linkedin.com/company/admindroid
Twitter: twitter.com/admiindroid
Facebook: facebook.com/admindroid