On Day 15 of Cybersecurity awareness month, learn to protect your organizations’ data from unmanaged devices today. Stay tuned for more blogs in the Cybersecurity blog series.
Every organization wants to protect its data securely from cyber criminals. For securing data, the organization implements various security measures, enforces policies, and more. Coming to Microsoft 365, SharePoint and OneDrive for Business top the list in handling organization data, and they need to be secured.
As the world is increasingly interconnected, everyone shares the responsibility of securing cyber space
– Newton Lee
Like the quote says, users use their own devices to connect and work with the organization’s data from anywhere they want to. If the device is unmanaged or not compliant, it might be a way through which cybercriminals can steal data easily. So, administrators must restrict unmanaged devices from accessing SharePoint and OneDrive to prevent data loss during cyber threat or credential theft. Let’s see how to block unmanaged devices in your organization in detail.
What are Unmanaged Devices in Azure AD?
Devices that are not hybrid AD joined or compliant in Intune are considered unmanaged devices. These devices might have more chances of losing their organization’s data when used in insecure networks. Thus, you should protect your user’s BYOD devices properly.
How to Restrict Unmanaged Devices in SharePoint and OneDrive?
Azure AD joined devices are considered unmanaged devices as it is not compliant in Intune and not hybrid AD joined. To restrict these devices, you can use the Conditional Access policy to block unmanaged devices from SharePoint and OneDrive.
Before configuring the CA policy, we recommend enabling it in the ‘Report-only’ mode for a week and analyze the impact on your organization
- Navigate to the Conditional Access policy page in Azure AD Admin Center.
- Select ‘New Policy’ to create a new policy.
- Name your policy.
- Select ‘Users or workload identities’ and select users or groups based on your needs.
- Then, select ‘Cloud apps or actions’ and check the ‘Select apps’ under ‘Include’. Search and select ‘Office 365 SharePoint Online’ and press ‘Select’.
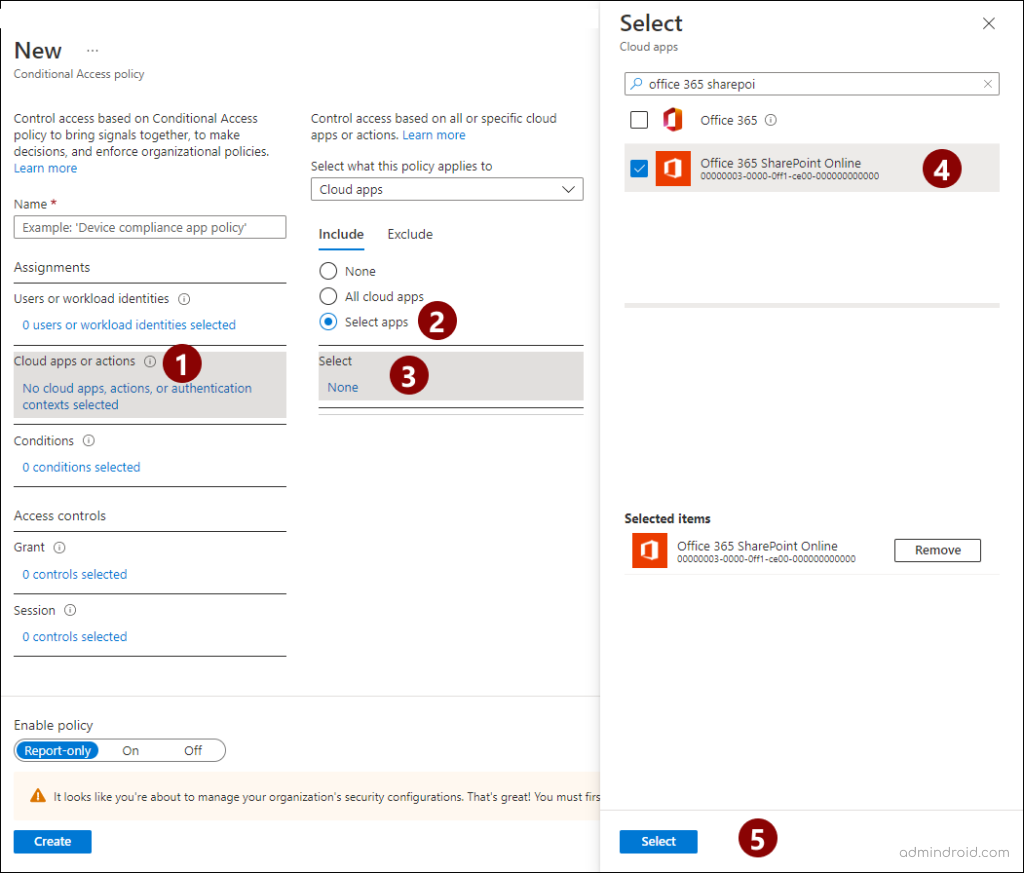
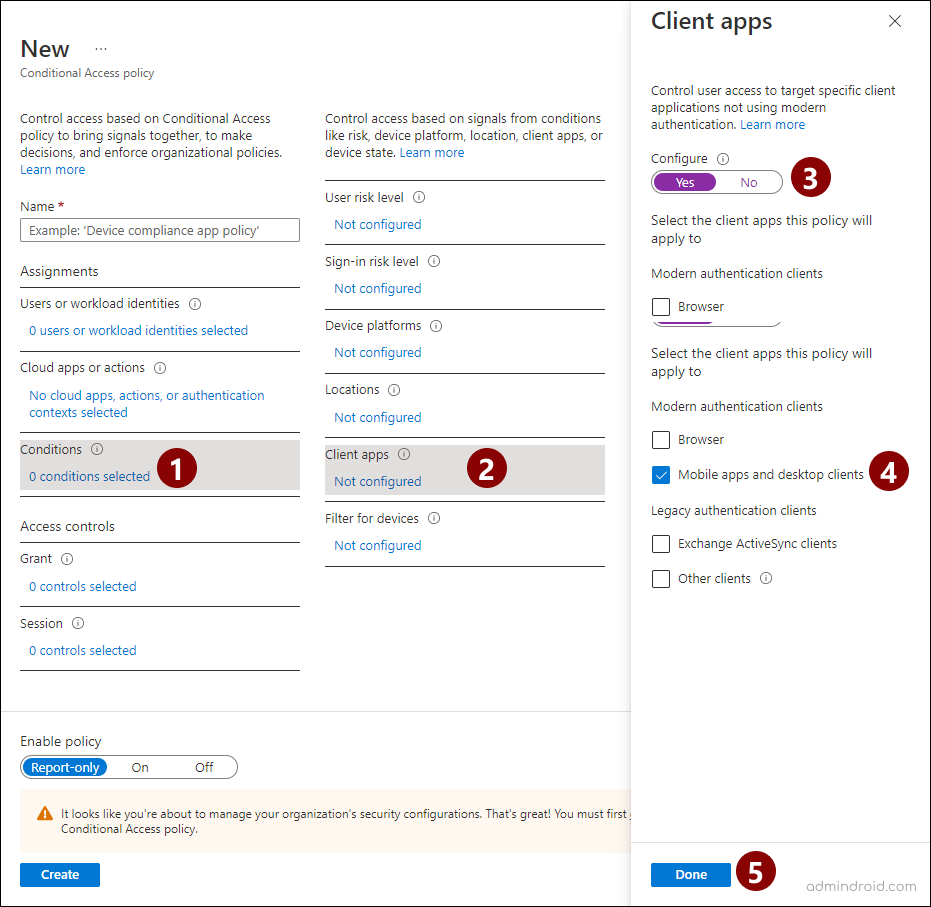
- Click ‘Conditions’ and select ‘Client apps’ and move the configure toggle to ‘yes’. Then, uncheck the ‘Legacy authentication clients’ and ‘browser’ under the modern auth clients. Click ‘Done’.
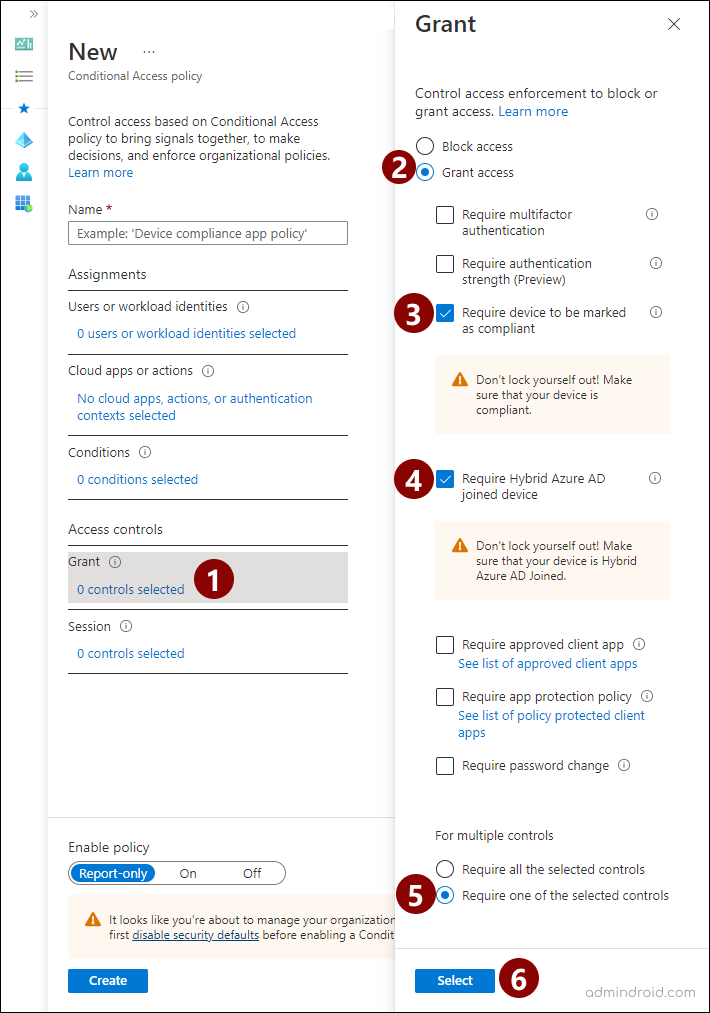
- Select ‘Grant’ access control. In the pop-up page, choose ‘Grant access’ and check the ‘Require device to be marked as compliant’ and ‘Require Hybrid Azure AD joined device’ checkboxes. Then, choose ‘Require one of the selected controls’ under ‘For multiple controls’. Click ‘Select’
- Move the ‘Enable policy’ toggle to ‘On’ and click ‘Create’.
After enabling the policy, the unmanaged devices can’t access the SharePoint and OneDrive apps. Apart from CA policies, admins can also block unmanaged device registration in Entra ID device settings.
Points to Remember:
- While including users in the CA policy, you can exclude break glass accounts to avoid locking out in emergency situations.
- Note that blocking SharePoint and OneDrive access will also impact Microsoft Teams, Delve, and Analytics. So, Teams mobile and the desktop client will also be blocked for the respective users.
- Before enabling this policy, you can enforce users to ‘Sign out of all sessions’ using Admin Center. Because, the policy will not affect the existing connected sessions and will reflect only when a new session is initiated.
- You can also block the ‘unmanaged devices’ by navigating to SharePoint Admin Center–> policies–> Access control–> unmanaged devices. It will create a respective CA policy, but the policy customization didn’t reflect in the tenant when I tested it.
How to Allow specific domains to Sync OneDrive and SharePoint Data?
For configuring CA policies, your organization must have an Azure AD P1 or P2 license. If you don’t have these licenses and your device is AD joined, you can allow only specific domains to sync SharePoint and OneDrive data. Thus, devices joined to the allowed AD domain can only be able to sync data, thereby preventing unnecessary data loss.
To allow specific domains, you must know the GUID of the respective domains. You can get your domain GUID using the Get-ADDomain PowerShell cmdlet.
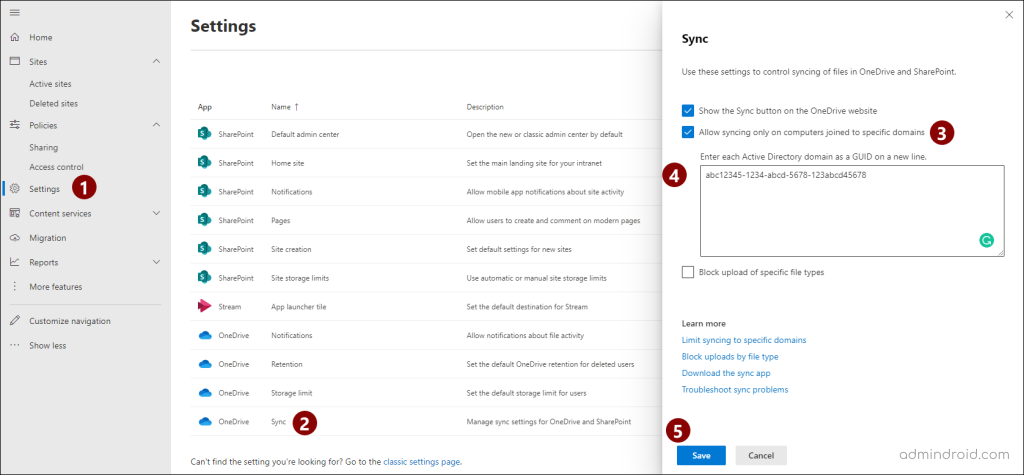
- Navigate to SharePoint Admin Center.
- Select ‘Settings’ –> OneDrive (sync).
- In the pop-up, select the ‘Allow syncing only on computers joined to specific domains’ checkbox and enter the domain GUIDs you want to allow.
- Click ‘Save’.
Note: This setting will be applicable only for AD joined devices not for Azure AD joined. For Azure AD joined, you can go with the CA policy steps explained above.
Not simply unmanaged devices, there are many factors you need to consider when preventing data exposure in your organization. Day-by-day threats are becoming more, and we can’t conclude the loopholes the organization might have. What we can do is to try defending and protecting data in every possible way. For that, periodically monitoring and identifying suspicious actions is foremost of all. AdminDroid comes into play here. Let’s see,
How AdminDroid Opens the Door for Securing Your Organization’s Data?
In Microsoft 365, securing data in SharePoint & OneDrive involves many factors to consider. On top of that, admins need to monitor anonymous access, external user activities, file activities, sharing links, etc., to secure the data. To simplify the process, AdminDroid SharePoint Online auditing tool provides a dashboard with an overview of all details and reports with in-depth info.
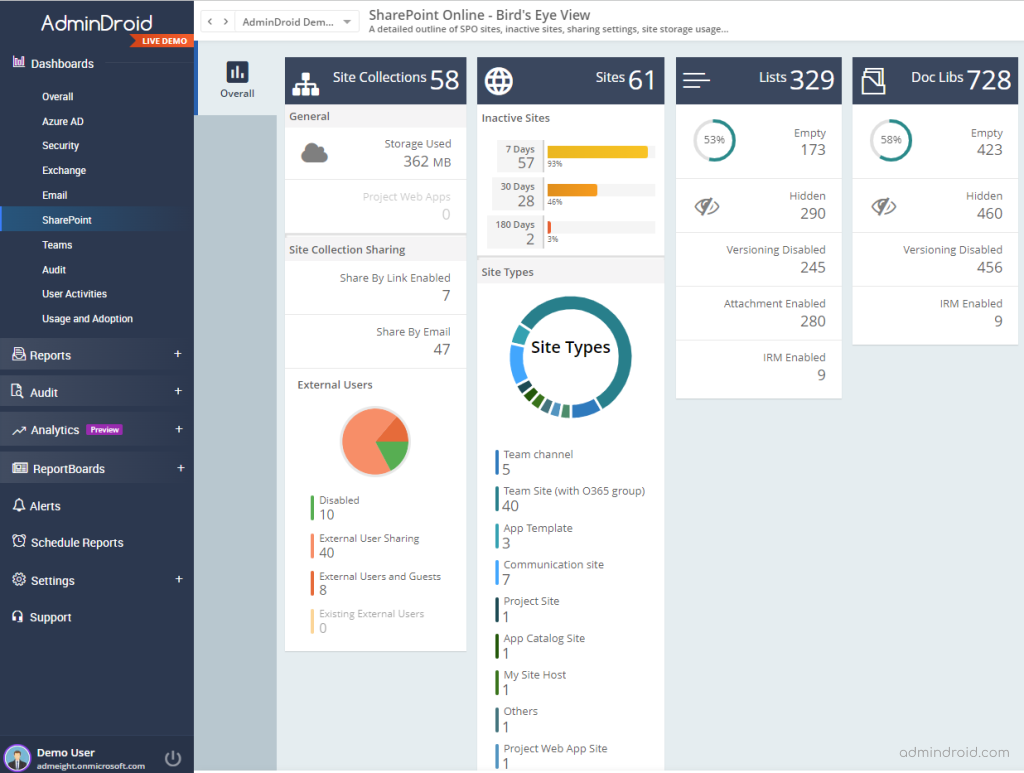
SharePoint Online Dashboard
It gives you a bird’s eye view of site collection sharing, storage, site types, external users, lists, and document libraries. Let’s visualize the overview of your SharePoint Online and manage them efficiently.
All-around SharePoint Online & OneDrive Reports
From AdminDroid’s comprehensive reports, you will gain details on sharing invites, file activities, site collections, lists & document libraries, and more. Monitoring these reports helps you to identify unwanted file changes, deletions, downloads, and unauthorized access to sensitive content. Also, with the external sharing reports, you can avoid unnecessary external sharing and prevent confidential files from anonymous users.
File Activities
- SharePoint & OneDrive file accesses
- SharePoint & OneDrive file downloads
- SharePoint & OneDrive file modification
- SharePoint & OneDrive file deletion
Sharing Invitations
- Site invite creations
- Accepted site invites
- Guest user expiration changed
- External user invites
Likewise, you will get details on OneDrive sharing invitations from AdminDroid OneDrive auditing tool.
Anonymous Link Activities
- Anonymous link creation
- Anonymous link modification
- Anonymous link removals
- Anonymous link accesses
Similarly, you can also view anonymous link activities for OneDrive files.
Boost up your SharePoint Online management by taking full control of SharePoint data and preventing unwanted access to organization files. Similarly, handle your user’s files and secure users’ individual files from malicious threats and prevent data exposure with the AdminDroid OneDrive management tool.
Undoubtedly, AdminDroid becomes a whip hand for monitoring and securing your organization’s data. Want to test it? Go ahead and explore it today!
We have covered unmanaged devices in Azure AD and how to block these devices to protect your organization’s data from various cyber threats. Also, for AD-joined devices, you can go with allowing sync for specific domains to block access from other domains. I hope this blog will help you to manage unmanaged devices effectively. Happy securing!








