Office 365 accounts are frequently compromised by phishing and spam attacks. Regardless, we have multiple phishing and spam detectors to detect any risky log-in attempts harming your Office 365 accounts. However, third parties and external collaborations are not the only factors posing such risks; there are other factors as well.
Little confused? Let’s have a look at the below scenarios:
- Are you aware that frequent MFA failures pose severe risks?
- How will you identify users who are still using basic authentication?
- What if your Office 365 users sign-in from any suspicious device?
- What if the highly privileged admin accounts are compromised?
The above cases depict the possible risky logins attempted by users within the organization. To prevent such login attempts, you should audit users’ risky log-in attempts in Office 365.
Detect Suspicious Log-in Attempts Using Azure Active Directory:
Microsoft Azure AD logs provide information about user sign-ins and how Office 365 resources are used by users. For compliance purposes, it logs all sign-ins that happen in each Office 365 service. Azure Active Directory sign-in reports offer three types of reports to check risky sign-ins in your organization.
To check the Office 365 risky sign-ins reports,
- Open the Azure Active Directory.
- In the left pane, select Security under the Manage section.
- To find the risky sign-in reports, navigate to the Reports section from the left pane.
- Under the Reports section, you can discover the following Office 365 risky sign-ins reports:
- Risky users report
- Risky sign-ins report and
- Risk detection report.
Using these reports, admins can discover
- History of all risky sign-ins.
- Risk History.
- Users who are at risk.
- Risks that have been remediated, dismissed, and compromised.
- Risk detection details.
Downfalls with the Native Azure AD Risky Sign-in reports:
- You have to dig deeper to find each result – no clear reports.
- Additionally, determining which log-in attempts are risky is difficult based on user and guest log-in reports.
- You can’t easily discover the risks associated with the most highly privileged administrative accounts.
To overcome the downfalls of native auditing tools, you can rely on AdminDroid Office 365 Reporting and Auditing Tool. With its advanced features, Office 365 auditing has become a piece of cake for admins. It provides detailed insights and comprehensive reports on Office 365 user sign-ins, Azure AD sign-in events, risky sign-ins, and more to keep track of user activities.
Detect all the Risky Log-in Attempts in Detail with AdminDroid:
AdminDroid analyzes and provides more detailed log-in reports and advanced features than Azure AD.
AdminDroid offers much more exhaustive reports for every risky sign-ins happening around your organization. For instance, expired log-in attempts, MFA failures, MFA fatigue attacks, basic authentication login attempts, etc.
For risky log-in attempts, AdminDroid fulfills the following queries and more:
- Did any login attempts fail to fulfill MFA authentication?
- Do any users use basic authentication?
- Can we get notified on logins failed of expired passwords in Azure AD?
- Have any disabled accounts attempted to log into Office 365?
- How do you find the admin and guest user login attempts?
- Can we detect admin login failures in Office 365?
- How do you monitor risky sign-ins across your organization?
AdminDroid sign-in audit reports come with a sleek comprehensive security-related report dashboard covering all the users, admins, and guest actions that occur across your Office 365 environment.
Discover all the Log-ins that Failed to Fulfill MFA Authentication:
Configuring MFA reduces threats to Office 365 accounts by 90%, thereby protecting them from cyber-attacks. Admins should monitor the MFA failure rate because the rise in the range may open the door for hackers to come up with severe attacks on your organization.
As a result, if you’re already using MFA with Office 365, ensure that the Office 365 accounts are safe and not experiencing any issues. But how will you locate those users who failed in the MFA challenge?
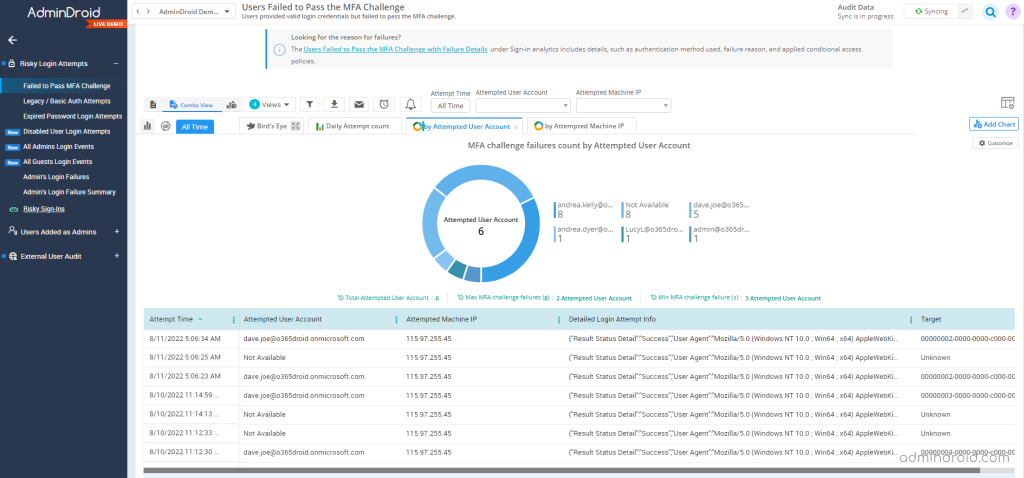
To check users who failed to pass the MFA challenge in AdminDroid, navigate to AdminDroid portal –> Audit –> Security –> Risky Login Attempts –> Failed to Pass MFA Challenge.
It provides the list of the users who failed in the MFA challenge despite providing valid credentials. Also, it lists the attempted user account, time, IP address, etc. You can filter the data to attain your requirements. Further, you can check the failure details of the users who failed to pass the MFA Challenge under the Sign-in analytics tab.
Explore the report: Users Failed to Pass the MFA Challenge with Failure Details
Find Users Who Are Using Basic Authentication in Office 365:
Basic authentication is the foremost cause of risks to user accounts as it doesn’t require any additional authentication method rather than the password. Thus, Microsoft deprecated basic authentication in Office 365 and rolled out Multi-factor Authentication (MFA) providing more security to user accounts.
So, if any of the Office 365 users still use the deprecated basic auth for login, you can check the overall Office 365 basic authentication report in AdminDroid. This report provides details on the users’ login failures using basic authentication or legacy protocols such as IMAP and POP.
Explore the report: Failed login via basic authentication report.
Get Notified on Logins Failed Due to Expired Password in Azure AD:
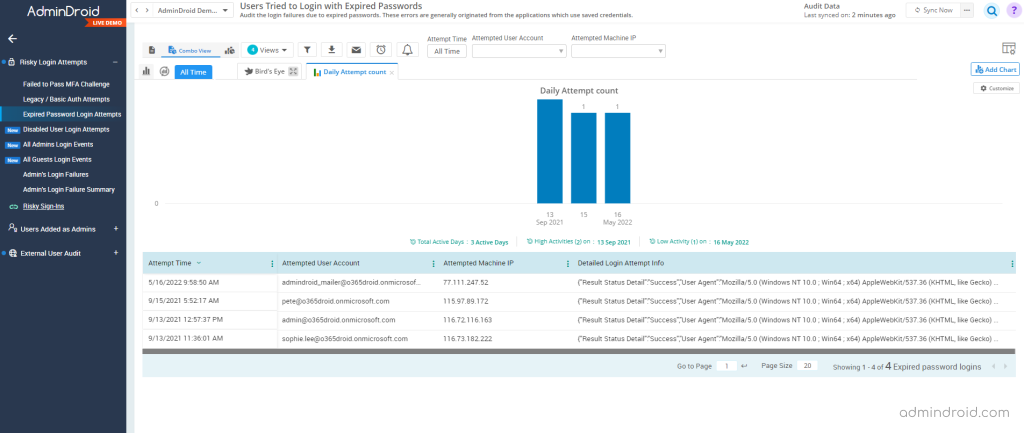
Setting a password expiration policy is the best practice to protect Office 365 from attackers. What if the user’s login with expired passwords? How to check log-ins with expired passwords?
Cool! AdminDroid offers a report that discovers the admins’ login failures due to expired passwords. (Mostly, these errors are generally originated from the applications which use saved credentials)
Explore the report: Logins Failed Due to Expired Password Report.
Find If Any Disabled Accounts are Attempted to Logins in Office 365:
If any disabled users tried to log into their Microsoft 365 account, you can easily keep track of them using the disabled account logon attempt reports in AdminDroid. This report provides the failed user logins due to the user account being disabled.
Explore the Report: Disabled accounts attempted to login report
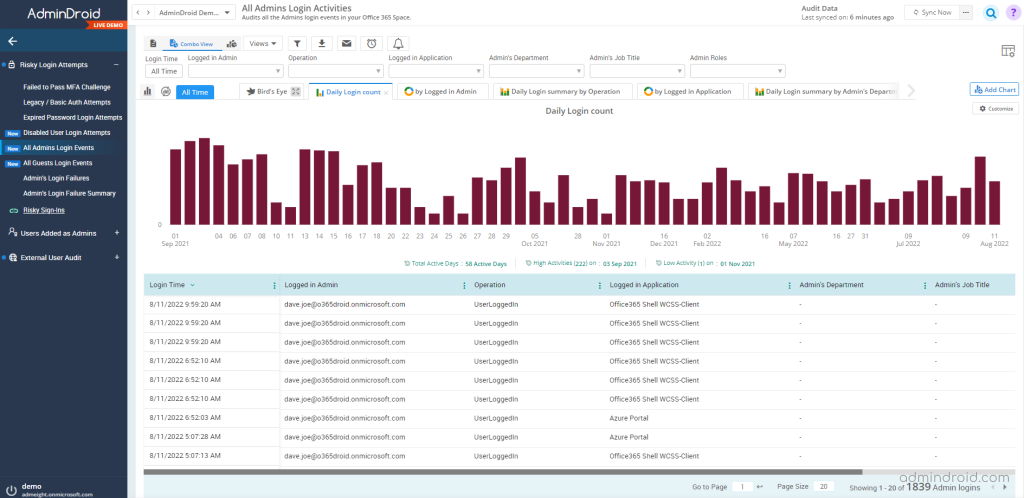
Find Admins and Guest User Login Attempts in Office 365:
AdminDroid prioritizes highly privileged admin accounts and partially risky guest accounts. It is vital to monitor admins’ login events properly to prevent any misuse of their accounts. Therefore, you must be aware of where the admin accounts get logged in.
Explore the report: Admin login activities report.
It’s important to know that guest users can also pose a threat to your Office 365 environment. Therefore, you should keep an eye on the guest login events, such as where they log in from, when they log in, and so forth. AdminDroid risky sign-in reports audit the external and internal guest user’s logins using user credentials.
Explore the Report: External and Internal Guest User Login Report.
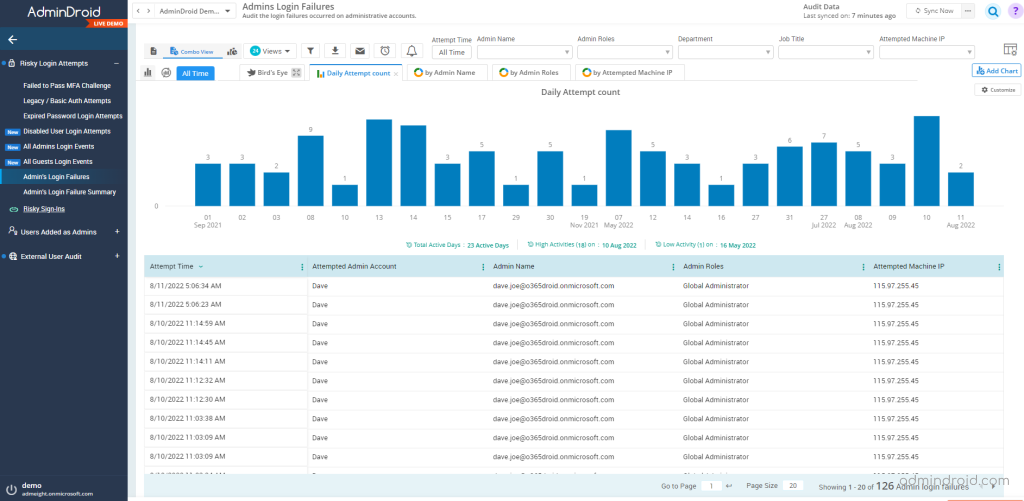
Detect the Admin Login Failures in Office 365:
Admin accounts in Office 365 require more protection since they have a high privilege and have access to confidential data. Therefore, suspicious login attempts from admin accounts need to be monitored instantly.
Here, AdminDroid assists admins to verify the failed login activities from their accounts and fellow admins with details about where the login was attempted, daily login failure count, etc. Also, it provides the admin daily login failures summary report that shows the daily login failure count of administrators.
Explore the report: Admin login failure report.
Monitor Risky Sign-ins Across Your Organization:
Hackers often target Office 365 user accounts to compromise business-critical data. So, it’s better to monitor these flagged risky sign-ins. With AdminDroid, you can discover all the Office 365 risky sign-ins that happened along with the risk level of each threat.
From the risk-based user sign-in protection reports, you can
- Investigate the risks.
- Classify the risk level based on the risk event types.
- Automatically detect and protect users according to the risks.
Classify the Risky Sign-ins Based on Various Risk Levels:
Detecting risk attempts in your organization is imperative, but it is also crucial to assess each risk’s severity. Analyzing the severity of attacks can help you determine how to respond to the risk and future exploits.
AdminDroid categorizes risky log-in attempts into low risky sign-ins, high-level risky sign-ins, and medium risky sign-ins to determine the severity range of the log-in attempts.
Explore the Report: Risky Sign-ins Based on Risk Level Report
Discover Detailed Detection Timing Reports Based on Detection Types:
Admins will likely be more aware of risks if they know how the risk has originated. There are two types of detection: offline and real-time, with users and sign-in levels typically assessed for risk.
Real-time risks are posed by anonymous IP addresses, malware-linked IP addresses, unfamiliar sign-in properties, etc. On the other hand, risks caused by abnormal travel, password spraying, or setting suspicious inbox forwarding rules are covered under offline detection.
AdminDroid provides reports based on detection timing which helps admins to identify the rate of each detection type and to mitigate against the risk event.
Explore the report: Discover the Risk Detection Time Report
Determine the Risk Status of Each Office 365 Risky Sign-ins:
Consider a scenario where multiple administrators are managing your Office 365 tenant. Whenever a suspicious risk was detected, one of the admins managed to resolve it. But how do we identify how the risk has been resolved? What is the current risk status? Has anyone marked severe risks as safe?
Check the risk status of each risky sign-in in the AdminDroid risk status dashboard that gives an aerial view of risky sign-ins with the risk status in one place. You can check on the risk status reports like,
- Confirm User Compromised Report
- Dismissed User Risks
- Risky User Sign-Ins Marked as Safe
- Risk Marked as Remediated
Explore the report: Risk Status of each Risky sign-in.
Discover the Root Cause of Each Risky Log-ins:
Your Office 365 account may be subject to suspicious activity for various reasons. But how will you discover what’s the root of each risky log-in attempt?
With AdminDroid, you can get reports with precise details on each risky event, thereby saving your time. Have a look at the risky event reports.
- AnonymizedIPAddress – Risk events are flagged as anonymized when a user logs in from an anonymous IP address in Office 365. (Like anonymous VPN).
- UnlikelyTravel – Detects Office 365 impossible travel i.e., When a user logs in from geographically distant locations compared with their past sign-in location.
- MaliciousIPAddress – Office 365 Sign-ins from a malicious IP address have been detected. High failure rates due to invalid credentials or other IP reputation sources are indicative of a malicious IP address.
- UnfamiliarFeatures – This risk is detected when a sign-in occurs from a different and unfamiliar sign-in property in azure ad compared to the previously saved sign-in history. (Usually, the system stores the IP address, location, and browser type of every user, but if it detects any suspicious IP address, location, or logging from a different browser, this risk is flagged)
- MalwareInfectedIPAddress – Indicates sign-ins from malware-linked IP addresses that are infected with malware
- SuspiciousIPAddresss – Detects sign-in from IP addresses with suspicious activity.
- LeakedCredentials – A leaked credential detection has been found in the user’s account.
- InvestigationsThreatIntelligence – In this type of risk detection, abnormal or known attack patterns are detected from user activity. It is based on Microsoft’s internal and external threat intelligence sources.
- Generic Events – This indicates that identity protection was not enabled for the user.
- GenericAdminConfirmedUserCompromised – The admin has selected “Confirm user compromised” whose identity protection is not active.
- PasswordSpray – Password spray attacks in Office 365 are flagged. (In password spray attacks, an attacker attempts to guess a user’s password multiple times in a short period of time)
- McasImpossibleTravel – Logging in from geographically distant locations within a short period, which is impossible to travel. This risk indicates that another user is using the same credentials.
- McasSuspiciousInboxManipulationRules – Any suspicious inbox manipulation rule in Office 365 that deletes or moves messages to any folder is considered this type of risk.
- InvestigationsThreatIntelligenceSigninLinked – Assesses activity that is unusual in comparison to known attack patterns
- MaliciousIPAddressValidCredentialsBlockedIP – Indicates that a sign-in attempt from a malicious IP address was made with valid credentials.
- AdminConfirmedUserCompromised – This will be displayed when an admin selects ‘Confirm user compromised’ in the Risky users UI.
- UnknownFutureValue – This risk is detected when an unknown future value in Azure (I.e., evolvable numeration sentinel value) is found
Sentinel Value – The term denotes a value that serves as an endpoint for looping algorithms rather than a ‘real value’. This is necessary because it allows the addition of future values without breaking existing applications.
Explore the report: Risky Sign-in Detection Based on Risk Event Types
Find the Risk Remediation Methods of Each Risky Sign-ins:
Administrators can take the necessary action for future exploitation by identifying what remediation methods are being used for each risk case. Hence, risk resolution records play a major role in reducing risk and saving time.
Now that you’ve got AdminDroid, you can access the risk-resolved methods and take the necessary action to remediate the risk and unblock users.
Admin Generated Temporary Password – Provides a list of risky user sign-ins that were resolved by the admin generating temporary passwords for risky users.
User Performed Secured Password Change – Lists the risky user sign-ins resolved when the user performs a secured password change.
User Performed Secured Password Reset – Lists the risky user sign-ins resolved when the user performs a secured password reset.
Admin Confirmed Sign-in Safe – Lists the risky user sign-ins resolved when the admin confirms sign-in as safe.
AI ConfirmedSign-in Safe – Lists the risky user sign-ins resolved when AI confirms the sign-in as safe.
User Passed MFA Driven by Risk Based Policy – Lists the risky user sign-ins resolved when the user passes the MFA Driven by Risk Based Policy.
Admin Dismissed All Risk for User – The report includes information on to whom the admins dismiss the user risk in Office 365.
Admin Confirmed Sign-in Compromised – Lists the risky user sign-ins resolved when the admin confirms the sign-in as compromised.
Explore the Report: Risk Remediation Method Reports
Finally, I hope this blog will help you to know how to monitor and resolve the risky log-in activities that happened in your organization. Discover the complete details of risky sign-in attempts in just a few clicks with AdminDroid. Get started now and explore it!