Dear Sysadmins, Microsoft 365 reporting & auditing is an inevitable necessity in this fast-paced digital world! Considering your arduous situation, we came up with a solution called Microsoft 365 Built-in Reports – Blog Series.
This series will provide deeper insights into the reporting capabilities that are already available in your hand in the name of Microsoft 365 admin center reports. Following is the list of services explained in this blog series.
- Built-in Azure AD Reports
- Native Exchange Online Reports
- Inbuilt Teams Usage and Activity Reports
- SharePoint Usage & External Sharing Reports
- OneDrive Activity Reports
- Yammer (Viva Engage) Analytics Reports
The answer to all your reporting queries is served here! Next, Microsoft 365 Defender becomes part of this series. A dedicated security solution provided by Microsoft for business enterprises to protect against sophisticated attacks. So, let’s dig deeper into this blog to gain knowledge about the built-in Microsoft 365 Defender reports and its advanced capabilities.
Microsoft 365 Defender Reporting
Microsoft brought Microsoft 365 Defender to provide all security solutions under a single roof for uplifting the burden of admins pondering over many places.
Microsoft 365 Defender is a defense suite deployed to provide a high level of protection against severe cyber security threats by detecting, investigating, preventing, and responding to the changes that occur in Microsoft 365 space.
The native Microsoft 365 Defender reports offer a comprehensive summary of an organization’s security posture within the Microsoft 365 environment, covering aspects such as threat intelligence, incident response, advanced hunting, and secure score. It helps security teams monitor, respond to, and investigate security incidents while aiding in trend analysis, compliance, and auditing.
Let’s get into exploring the 20+ different M365 Defender reports in this section. These reports are exclusive to the Microsoft 365 Defender and require specific licenses, excluding Microsoft Defender Plans 1 and 2.
- Microsoft 365 Audit Logs in Defender
- General Microsoft 365 Security Reports
- Email & Collaboration Reports
- Microsoft 365 Mail flow Status Summary
- Threat protection Status in Microsoft 365
- Post-Delivery Activities Report in Microsoft 365
- Microsoft 365 URL Protection Report
- Top Malware in Microsoft 365
- Spoof Detections Report in Microsoft 365 Defender
- Compromised Microsoft 365 Users
- Mail Latency Report
- Microsoft 365 Defender User Reported Messages Report
- Submissions Report in Microsoft 365 Defender
- Top Senders & Recipients
- Microsoft 365 Defender Incidents & alerts
- Advanced Hunting in Microsoft 365 Defender
- Microsoft 365 Security Threat analytics
- Microsoft 365 Defender Identities
- Advanced Email Monitoring Reports in Microsoft 365 Defender
- Microsoft Defender for Cloud Apps
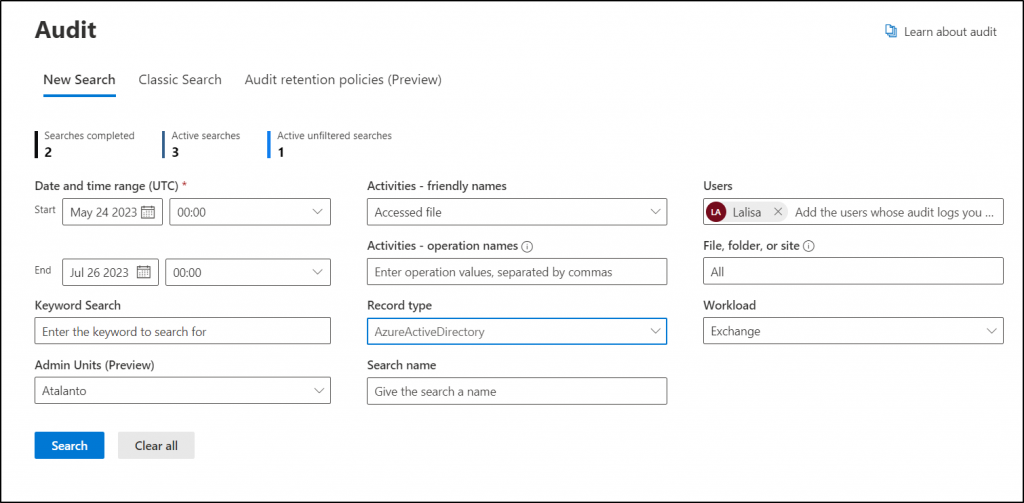
How to Get Microsoft 365 Audit Logs?
Want to know who did a specific activity in your organization or identify any system configuration changes? Here comes your all-in-one solution, Microsoft 365 Defender audit logs! It answers your every query & satisfies your every need related to Microsoft 365 defense mechanisms.
This Microsoft 365 audit logs in Defender provide a detailed record of events that occur within an organization’s Microsoft 365 environment, used for monitoring and investigating security incidents, monitoring user behavior, etc.
From your Office 365 user activity to system events, these audit logs provide clear visibility and help the security teams quickly identify & respond to potential security threats!
More info- https://learn.microsoft.com/en-us/microsoft-365/security/defender/auditing
Link to report – https://security.microsoft.com/auditlogsearch
General Microsoft 365 Security Reports
1. Does Microsoft 365 have Malware Detection Reports?
Malware Detection reports under Microsoft 365 Defender provide a 360-degree view of security-related events based on identities, data, devices, apps, and infrastructure. There are multiple dashboards provided under this security report which are listed below for better clarity.
Get Reports on Risky Users & Global Admins
- Risky users – Identify all the Microsoft 365 risky users with this report.
- Global admins – This report gives the overall count of global admins in your Microsoft 365 environment.
Get Reports on Malware Affected Devices & Users
- Device compliance – Microsoft Intune device compliance status is clearly stated under this report.
- Devices with active malware – Monitor security events and configure compliance policies through Intune device management.
- Type of malware on devices – Malware types detected on Intune-managed devices are recorded here.
- Devices with malware detections – Malware found on Intune-managed devices and their details are shown under this report.
- Users with malware detections – This report showcases the users with the most malware detections on Microsoft Intune-enrolled devices.
- Threat analytics – A executive summary of active and resolved alerts is shown here.
This multiple comprehensive dashboards on various reports provides a wealth of intelligence that can be used to strengthen an organization’s cybersecurity posture.
Link to report- https://security.microsoft.com/reports
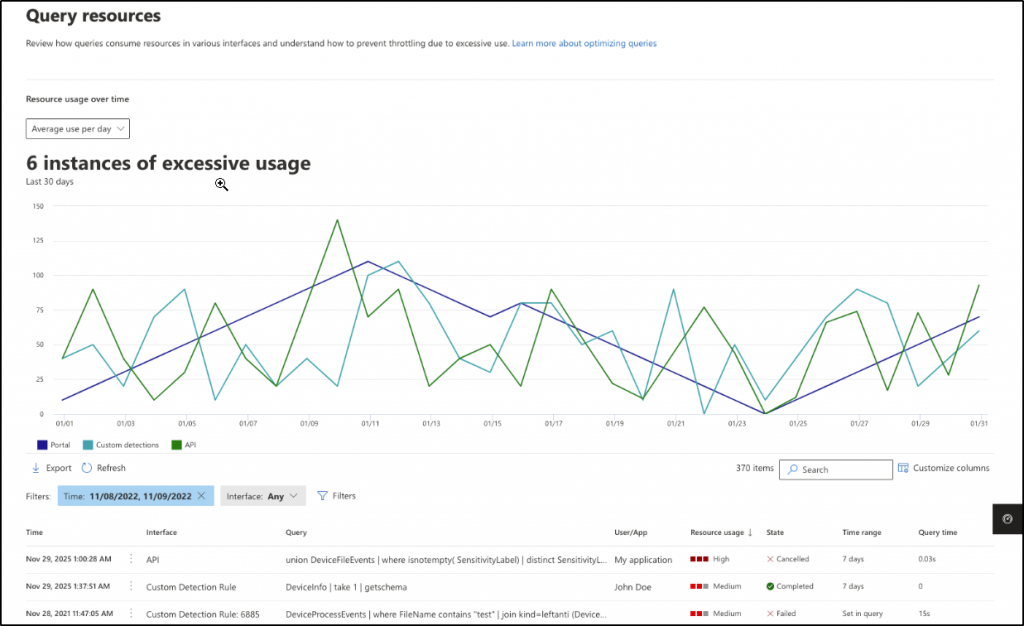
2. What is Query Resource Report?
Admins can check the query resource report to identify the queries that consumed more resources and take necessary remediate actions to prevent throttling because of excess usage. The report shows the queries that ran on the last day and the CPU resources consumed. Also, it displays details like time, interface, user/app, resource usage, etc., to identify resource-intensive queries and follow advanced hunting query best practices.
Link to report- https://security.microsoft.com/advanced-hunting/quotareport
Email & Collaboration Reports
- How to get a mail flow status report in Microsoft 365?
- What is the threat protection status?
- How to track post-delivery activities report?
Don’t let challenging questions bother you; Microsoft 365 Defender reports are here to be your guiding light! Microsoft 365 Defender offers over 10 detailed reports on your organization email & collaboration activities. No need to search elsewhere! trust Microsoft 365 Defender for all your email security reports. 😌
These email and collaboration reports offer key information such as mail flow status, threat protection, malware detections, spoof detections, compromised user lists, etc., to provide vital insights for building a robust email defense system. Admins can use these reports to build your email defense system without any loopholes and enhance email security. You can find these below reports in the “Reports” section on Email & collaboration page.
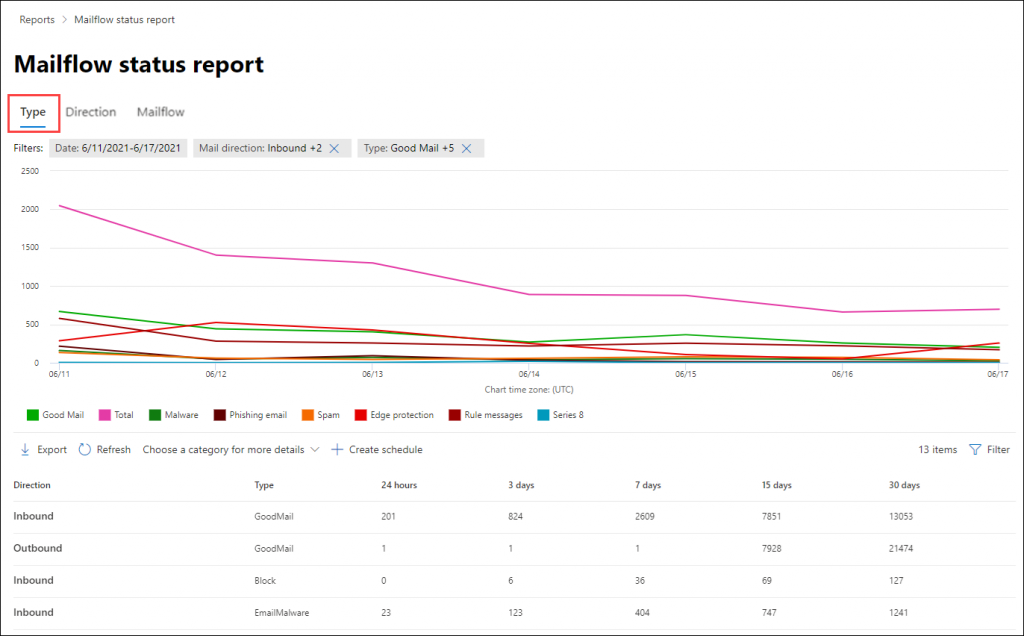
1. What is the Mail Flow Status Report in Microsoft 365?
Mail flow status report provides information on every in & out email activity happening in your Microsoft 365 environment.
This report categorizes your organization’s mail into good, spam, phishing, and malware based on detections and investigation. There are numerous mail flow reports in the new Exchange admin center, showcasing the various email activities of Microsoft 365. But most importantly, this is the only mail flow report that provides edge protection information.
So, admins must monitor this report not only knowing the good, spam, and malware detections in mail flow but also for emails blocked or allowed in the edge.
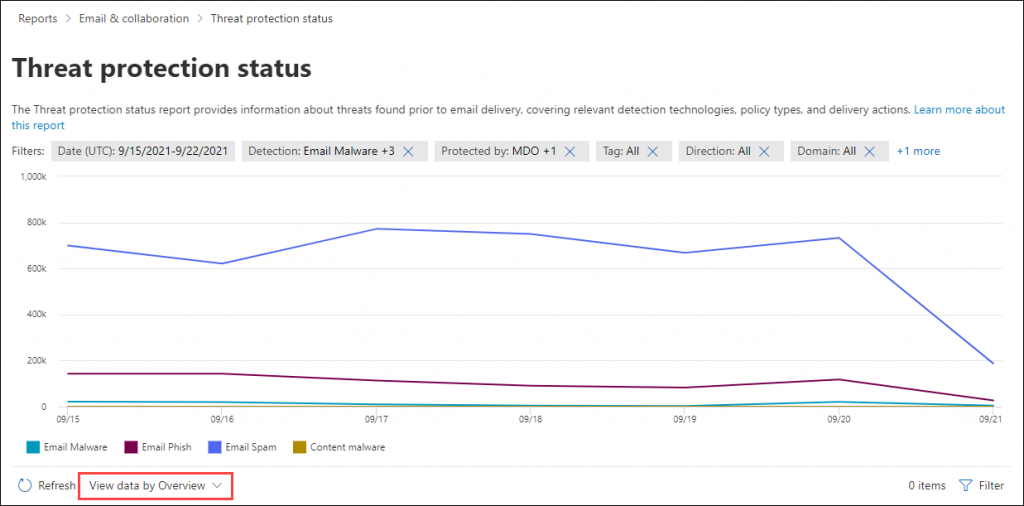
2. How to Get Threat Protection Status Report?
It provides information about the threats that were detected prior to email delivery, covering detection methods, security policies, and delivery actions.
Admins can gain insights into affected files or websites by various anti-malware policies, zero-hour auto purge (ZAP), safe links, safe attachments, and anti-phishing policies. Therefore, admins must proactively monitor these reports and identify trends to optimize security policies efficiently!
3. What is Post-Delivery Activities Report?
Microsoft 365 Defender provides post-delivery activities report to record and display all the email messages filtered by zero-hour auto purge in Exchange Online. This report shows the messages removed from users’ mailboxes after delivery by the zero-hour auto-purge feature in real-time.
With this report, admins can identify the number of messages removed from mailboxes for spam, malware, and phishing by ZAP with this report.
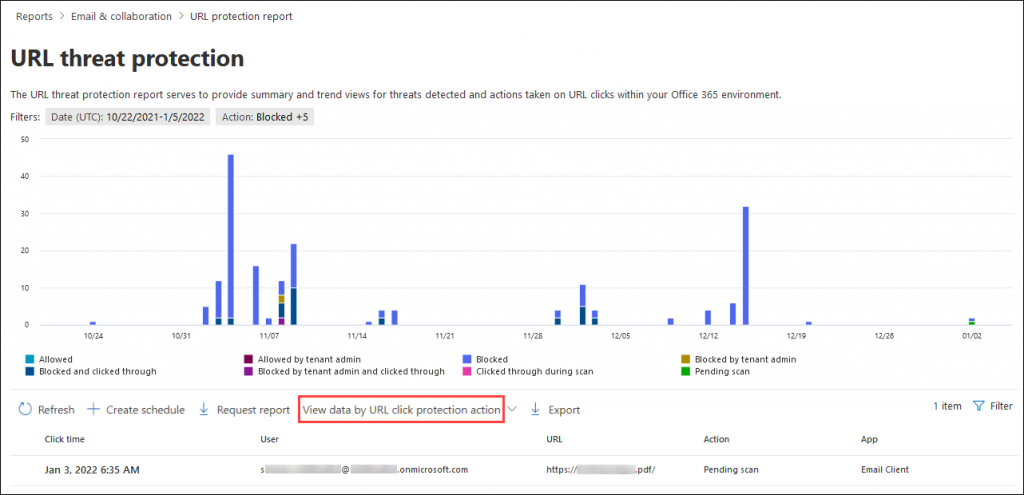
4. How to View URL Protection Report?
Without proper awareness, users easily click malicious URL links, for instance, when they are drawn towards offers and prizes in emails! 🎁 Such malicious links and URL clicks must be proactively monitored to secure the organization from data breaches. Thus, to monitor these URL clicks, Microsoft 365 Defender provides an exclusive URL protection report based on the safe links adopted in your organization.
This report provides details on allowed and blocked links, both by tenant admins and users. It covers blocked and clicked-through links during the scan, giving admins an overview of detected threats and the actions taken on Microsoft 365 users’ URL clicks.
5. Does Microsoft 365 Include Top Malware Report?
Yes, Microsoft 365 includes top malware reports! This report enables admins to discern malware trends & patterns targeting their organization. Empowered with this knowledge, they can frame effective transport policies & rules to restrict the movement of malware messages.
6. How to Track Spoof Mail Report in Microsoft 365?
The spoof detections report in Microsoft 365 Defender provides vital knowledge about the messages blocked or allowed due to spoofing. This Microsoft 365 Defender spoof intelligence prevents the organization from spoofing attacks and reassures the domain’s reputation.
- Organizations must know how to enable DKIM, DMARC, and SPF – the basic email authentication methods. Since this Microsoft 365 spoof detection report compiles the spoof messages detected by these email verification methods and other anti-spoofing protection in Exchange Online (EOP).
- Admins must closely monitor and analyze this report to safeguard their domain reputation, gaining insights into spoofed users, attack types, results, and other crucial details.
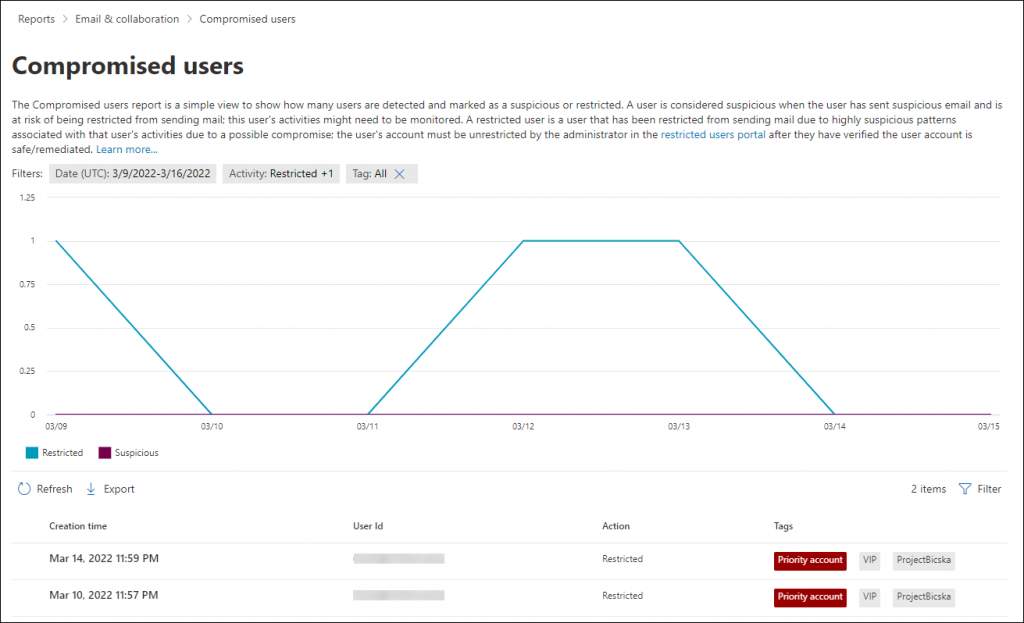
7. How to Find the Compromised Users List in Microsoft 365?
Monitoring the compromised user list is crucial in Microsoft 365. They are just like the doors opened for an uninvited guest! 👨💻So, admins can find all the compromised users of your organization from Microsoft 365 Defender Compromised Users Report.
This report highlights suspicious and restricted users of Microsoft 365. Suspicious users are on the edge of restriction, while restricted users cannot send emails due to highly suspicious behavior. With this report, admins can analyze spikes and patterns to secure compromised accounts effectively.
8. How to Get Mail Latency Report?
This Microsoft 365 Defender mail latency report compiles and stores an overview of your email’s journey, shedding light on its delivery speed and efficiency. But wait, there’s more! Unlike your usual reports, this one focus solely on mail latency, leaving client and network latency out of the picture. It’s all about the email here!
Thus, administrators can grasp the detonation latency of email messages within their organization and optimize their email delivery for peak performance.
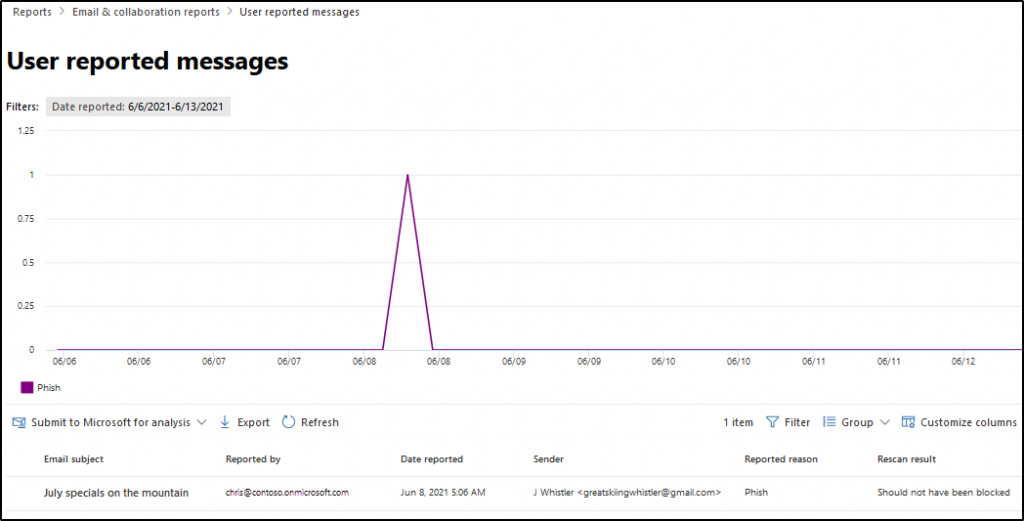
9. Microsoft 365 Defender User Reported Messages Report
Microsoft equips various methods for reporting suspicious email messages in your organization, ensuring you stay highly protected. Users can report junk emails using the provided options if they come across any.
- Built-in Report button in Outlook on the Web
- Microsoft Report Message
- Report Phishing Add-ins
When they report messages, it gets recorded here as suspicious email reports (spam, phishing, junk). Thus, admins can track reported messages to gauge filter effectiveness. Strengthen policies to restrict malicious emails and take action against offending users promptly.
10. Submissions Report in Microsoft 365 Defender
Beyond user-reported messages, Microsoft also provides a separate space for admins to report spam, phishing, malware URL, files, and messages for analysis. A distinguished report to view the status of messages, URLs, and attachments reported by admins is the Microsoft 365 Defender submissions report.
- In this report, all admin-originated submissions and admin submissions of user-reported messages are recorded and displayed for an overall idea.
- The report shows the submission date, ID, network message ID, sender, recipient, submitted by, the reason for submitting, etc., to understand the investigations and corresponding actions taken to ensure your Microsoft 365 email security.
11. Top Senders and Recipients Report in Microsoft 365
Monitoring top email collaborators is critical as they often become targets of spam, phishing, and malware attacks! Therefore, admins can use this report to discover the top 20 email senders and recipients of your Microsoft 365 space. And also, the top spam recipients, top malware recipients, and top phishing recipients of your organization.
Note that results may vary based on the safety features available, such as visualizing malware detected by Safe attachments in Defender for Microsoft 365, but Exchange Online Protection (EOP) lacks this capability.
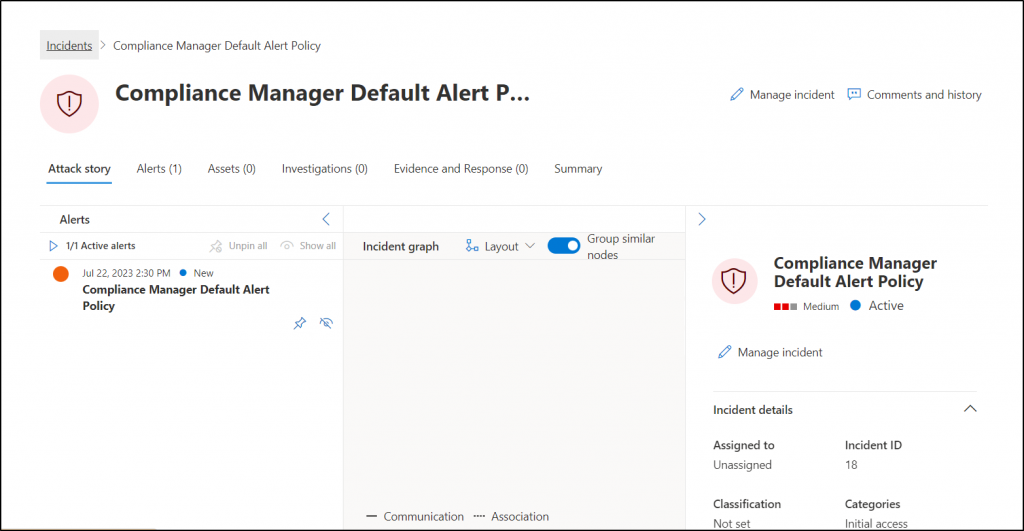
Microsoft 365 Defender Incidents & Alerts
If Microsoft detects any suspicious or malicious activity, it creates alerts to investigate and take immediate action against it. But usually, a cyber-attack targets different entities such as devices, users, or mailboxes simultaneously! Therefore, Microsoft creates different alerts for a particular attack.
Keeping a step ahead, Microsoft 365 Defender aggregates similar or correlated alerts into incidents. Such that, it can provide valuable insight into the attack that happened against your organization for better Microsoft 365 incident response.
Thus, admins should monitor the Microsoft 365 incidents and Microsoft 365 Defender alerts page to know
- where the attack started,
- the impact of the attack and
- organization’s data associated with it.
More info- https://learn.microsoft.com/en-us/microsoft-365/security/defender/incidents-overview
Link to report- https://security.microsoft.com/incidents
Advanced Hunting in Microsoft 365 Defender
Microsoft 365 Defender advanced hunting is a KQL query-based hunting tool. Administrators can proactively hunt for known and potential threats with flexible data access in advanced hunting.
This tool provides two types of modes namely advanced and guided mode for admins. You can run queries from scratch in the advanced mode. But if you are an amateur in using KQL, then you can take advantage of the guided mode!
- Above all, it gives some sample queries like high-confidence phishing emails delivered to the inbox, file activity by name, etc., and allows you to explore 30-day raw data. Thus, admins can widen incident investigations, carry out data analytics, focus on specific threats, and locate threat indicators & entities within their network.
More info- https://learn.microsoft.com/en-us/microsoft-365/security/defender/advanced-hunting-overview
Link to report- https://security.microsoft.com/v2/advanced-hunting
Microsoft 365 Security Threat Analytics
Threat analytics in Defender is a valuable resource for insights into existing and emerging security threats within Microsoft 365 infrastructure. It is designed specifically to assist the security team, providing classified & updated threat information for ease of understanding.
- The threat analytics report includes a threat overview, analyst report, related incidents, and affected assets, along with recommended actions for incident response.
- The threat analytics dashboard highlights key metrics to gauge threat exposure.
- The recommended actions tab is also available on the threat analytics dashboard, guiding you in responding to any related threat incidents in your organization and helping you understand the threat exposure metrics.
Also, this page classifies the threats into 3 different categories such as latest threats, high-impact threats, and threats with highest exposure. Using this threat intelligence solution by Microsoft can greatly help organizations to understand threats better and assist their security team effectively.
More info- https://learn.microsoft.com/en-us/microsoft-365/security/defender/threat-analytics
Link to report-https://security.microsoft.com/threatanalytics3
Microsoft 365 Defender Identities
Simplify your security workflow with Microsoft Defender for Identity integrated into Microsoft 365 Defender. No more juggling multiple tabs!
- The Microsoft 365 Defender Identities Report offers a unified view of all your monitored entities, including internal & external users, investigations, groups, and applications.
- Admins can gain insights into each user’s activity, incidents, owned files, and more, enabling them to detect, investigate, and respond to identity-related incidents and alerts for enhanced protection. A centralized hub for monitoring Microsoft identities, data, devices, and applications – all at your fingertips!
More info- https://learn.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-security-center-mdi?view=o365-worldwide
Link to report- https://security.microsoft.com/cloudapps/users-and-accounts
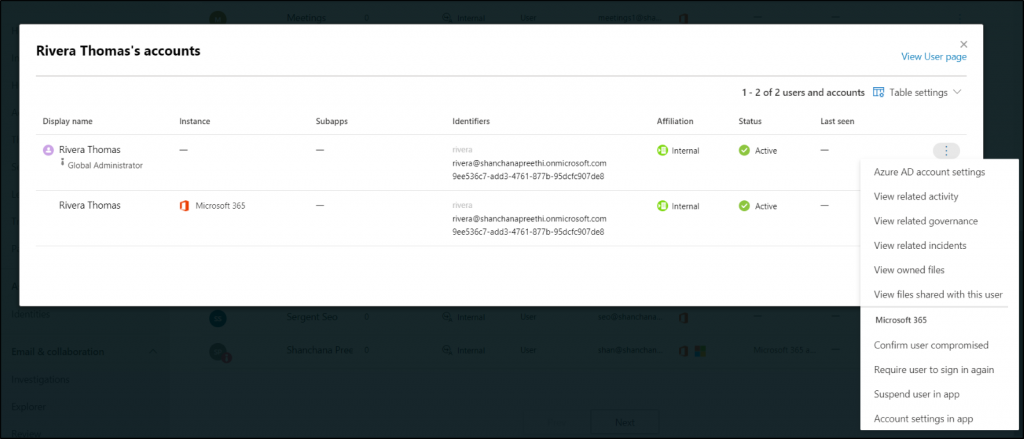
Microsoft 365 Defender Identities
💡 Tip: For deeper visibility into identity threats, use the Identity Threat Detection & Response dashboard in Microsoft Defender. It centralizes identity threat signals and helps prioritize actions across your environment.
Advanced Email Monitoring Reports in Microsoft 365 Defender
1. Automated Investigations and Response (AIR)
It’s definitely not possible only for the security team to perform all the required actions when an enormous number of alerts are triggered. Thus, here comes the automated investigations and response (AIR) to lend them a hand! 🤝
- This AIR capability efficiently handles well-known threats through automated investigation process. For example, when a user-reports a message, it triggers a system-based alert, launching an automatic investigation playbook.
- And here, the AIR process identifies threat types, message senders, and related infrastructure across different stages. You can conveniently review these investigations and responses in Microsoft 365 Defender, ensuring seamless flow and continuous protection for your organization.
More info- https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/air-about-office
Link to report- https://security.microsoft.com/airinvestigation
2. Microsoft Threat Explorer
Microsoft Threat Explorer is a dedicated space for the messages detected containing malware & phishing on the email entity page of Microsoft 365 Defender.
- The Threat Explorer page offers comprehensive malware details, including top families, targeted users, and email origins. It also covers phishing insights like URL links, clicks, and allowed/blocked URLs.
- Therefore, admins can effortlessly review malware & phishing messages and report false positives in Explorer, ensuring smooth flow and continuous protection.
More info- https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/email-security-in-microsoft-defender
Link to report- https://security.microsoft.com/threatexplorer
3. Microsoft 365 Defender Quarantined Messages
Usually it’s natural to feel uncertain about what needs to be reviewed and how the process works! 😩 Here, the Microsoft 365 Defender review page offers a unified interface for admins to conveniently handle multiple reviewing capabilities.
- Action Center– Empowers admins to take decisive actions against malware and phishing campaigns by redirecting them to the unified Action Center.
- Quarantine– Microsoft 365’s quarantine feature securely holds spam, phishing, and malware messages, including Teams messages and files.
- A message containing spam, phishing, and malware is quarantined by the email filters (anti-malware policies, safe attachment policies, anti-spam policies, etc.) available in Microsoft 365.
- This allows admins to efficiently review, respond, and enhance quarantine management in Microsoft 365.
- Restricted Entities– Admins can unblock restricted users from sending emails due to potential compromise from the review section.
- Malware trends– Finally, this shows a quick overview of malware trends in your organization.
More info- https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/quarantine-about?view=o365-worldwide
Link to report- https://security.microsoft.com/threatreview
Microsoft Defender for Cloud Apps
1. Get OneDrive Files Report in Microsoft 365 Defender for Cloud Apps
Microsoft 365 Defender for cloud apps continuously skims & scans files in OneDrive and Salesforce, whenever the files are stored, or their content is modified.
- Here, admins can use the “Files” section in Microsoft 365 Defender to inspect all files in connected apps and review stored data in cloud apps.
More info- https://learn.microsoft.com/en-us/defender-cloud-apps/file-filters
Link to report- https://security.microsoft.com/cloudapps/files
2. How to View Activity log in Microsoft 365 Defender for Cloud Apps?
Admins can analyze all the activities from their connected apps through Microsoft 365 Defender Activity logs for Cloud Apps. Thus, admins can monitor all connected app activities via the Cloud Apps activity log with facile.
For instance, admins can use this activity log to monitor users using outdated operating systems or browsers.
More info- https://learn.microsoft.com/en-us/defender-cloud-apps/activity-filters
Link to report- https://security.microsoft.com/cloudapps/activity-log
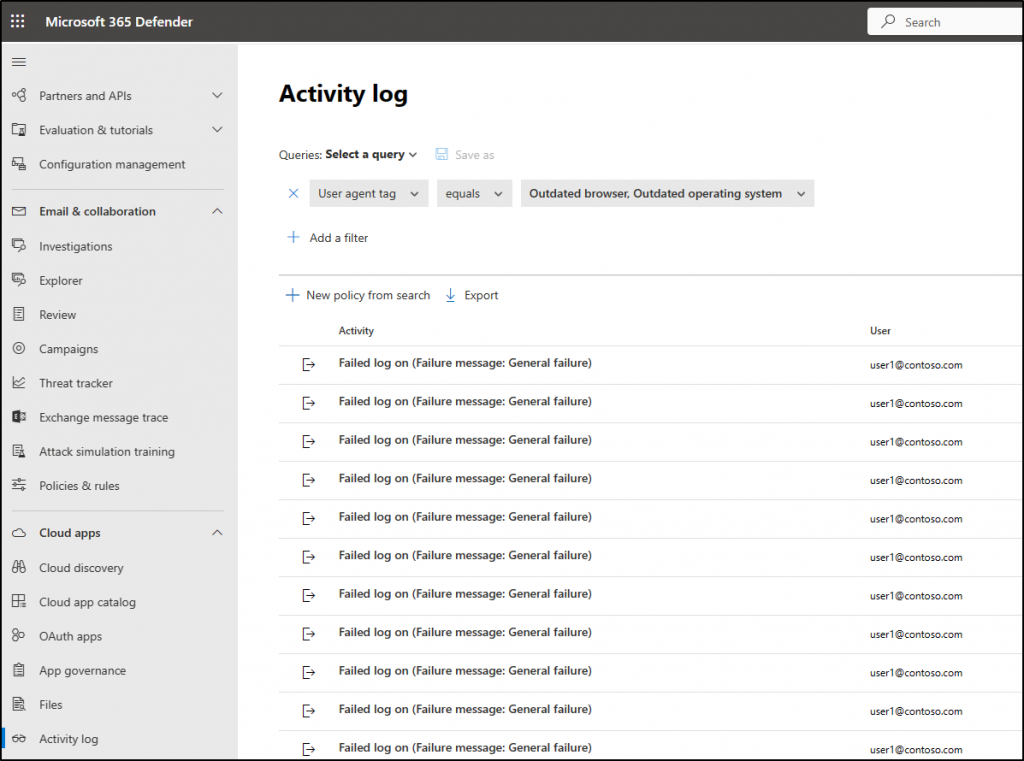
3. What is the Governance log in Defender for Cloud Apps?
The Governance log maintains a status history for every task configured in Defender for Cloud Apps, covering both manual and automatic tasks. These tasks include policy settings, governance actions applied to files and users, as well as any other actions designated within Defender for Cloud Apps.
- It also offers information on the success or failure of these events. Thereby, app governance in Microsoft 365 Defender is made easy by monitoring this governance log.
More info- https://learn.microsoft.com/en-us/defender-cloud-apps/governance-actions#governance-log
Link to report- – https://security.microsoft.com/cloudapps/governance-log
Are you tired of auditing manually in Microsoft 365 Defender? Feeling exhausted shifting multiple tabs and consistently filtering for desired reports? Then let go of your worries! Here comes AdminDroid Microsoft 365 auditing tool to uplift your burden in Microsoft 365 auditing.
Hassle-freely Audit Microsoft 365 with AdminDroid!
AdminDroid is an elite tool that offers a vast collection of reports for the purpose of Microsoft 365 auditing. It downsizes all challenges while auditing multiple Microsoft 365 services under a single tab. With AdminDroid in your hands, you can efficiently track user activities, identify suspicious behavior, detect security threats, and do more in your Microsoft 365 auditing world. In addition, AdminDroid provides distinguished reports to audit each Microsoft 365 service separately rather than auditing altogether around the clock.
- Azure AD Auditing – Use AdminDroid to become a prodigy in Azure AD auditing! Unveil 75+ auditing reports, 45+ statistics reports, and 10+ insightful dashboards to magnify your Azure AD (Entra ID) auditing with AdminDroid. From monitoring user activities, directory events, and app additions to administrative actions, track everything with the AdminDroid Azure AD auditing tool.
- Exchange Online Auditing – Grab the AdminDroid Exchange Online auditing tool to skim & scan every mailbox of your organization! It grants 65+ explicit auditing reports to be aware of the mailbox access permissions, threat protection status, and various other aspects crucial for effective Exchange Online management.
- Microsoft Teams Auditing – As organizations expand communication to external users, auditing MS Teams is crucial to prevent data leakages in this digital world. So now, harness the power of the AdminDroid Microsoft Teams auditing tool to find a solution to all your auditing queries! It brings all critical Teams activities, such as membership changes, external user login, and file-sharing events, to your notice in stride.
- SharePoint Online Auditing – In today’s interconnected and collaborative world, sharing is an inevitable demand, which must be balanced with strong data security measures. Therefore, get started and audit your SharePoint Online with AdminDroid! It is a place where you can audit site collections, SharePoint sharing & access requests, DLP activities, external file activities, SPO group memberships, etc.
- OneDrive Auditing – Continuous and rigorous monitoring of OneDrive, Microsoft 365’s personal cloud storage, is essential to ascertain an individual’s access level to confidential files/folders in the work environment. AdminDroid OneDrive auditing tool serves as your lens to keep an eye on all anonymous link creations, file access history, shared files & folders, and a way more to explain.
- Yammer Auditing – Visualize all Yammer (Viva Engage) activities in detail with AdminDroid. Analyze all Yammer analytics like user activities, device usage, group activities, and inactive users by auditing Yammer with AdminDroid.
Not only for auditing but also for Microsoft 365 reporting AdminDroid is the best choice! Because it ultimately provides 1800+ granular reports and 30+ AI-powered dashboards on various Microsoft services like Azure AD, Exchange Online, Microsoft Teams, SharePoint Online, OneDrive, and Yammer.
Moreover, it holds various advanced features that will take your Microsoft 365 administration to the next level!
- Delegate and distribute tasks with granular access delegation.
- Schedule and stay behind through AdminDroid scheduling.
- Deploy alerts with AdminDroid alerting to be aware of security incidents.
- Refine and report in the company of Advanced customization filters.
- Fascinating amenities such as a user-friendly interface.
So, download AdminDroid now with a 15-day trial to witness the enormous dimensions of Microsoft 365 reporting!
It’s time to ensure that all the security gates are closed in a world where cyber threats are increasingly sophisticated. Therefore, make use of the Microsoft 365 Defender reports, a place to monitor your accurate security!
We hope this blog will deepen your understanding of Microsoft 365 Defender reports and guide you in the right direction. Feel free to reach us for any queries through the comments section.