Being a Microsoft 365 admin, I’m sure you’ve noticed that one of your M365 tenants gets targeted by cyberattacks a lot – while other stays safe, right?😥 So, you decide to identify and rectify any misconfigured security settings in the vulnerable tenant. 💡
The initial thought would be to manually note down all the settings and check them with your victim Microsoft 365 tenant, wouldn’t it? If you do this, you’ll definitely regret it later since it consumes time and has multiple tabs switches! 💯
Boom! Fortunately, there’s a free config compare tool: Microsoft365DSC. With this M365DSC tool, admins can generate a discrepancy report, pinpoint the changes, and take corrective action to ensure both tenants are properly secured.
Let’s delve into the blog about the config compare tool and how it helps you to compare the Microsoft 365 tenant configurations. 👇
What is Microsoft365DSC Tool?
Microsoft365DSC is a free tool that helps you configure and manage your Microsoft 365 tenant in a configuration as a code style. This innovative tool uses the PowerShell Desired State Configuration (DSC) framework, enabling you to precisely define how your tenant should be configured.
Delving deeper into the capabilities of the open-source Microsoft365DSC tool, it resolves various challenges you may encounter. For instance, it allows you to,
✅ Automate the configuration of Microsoft 365 tenant settings.
✅ Export Microsoft 365 configurations.
✅ Synchronize configurations across different Microsoft 365 tenants.
✅ Monitor Microsoft 365 Tenant settings changes.
Furthermore, Microsoft365DSC aligns with our goal of easily assessing M365 tenant settings. Let’s delve into the advantages of utilizing this tool for evaluating Microsoft 365 tenant settings.
Advantages of Using Microsoft365DSC to Compare Microsoft 365 Settings
Here are some of the benefits you can achieve by comparing tenant configurations with Microsoft365DSC.
- Easily Track Tenant Settings Changes: Microsoft365DSC facilitates efficient monitoring of your Microsoft 365 settings by swiftly identifying tweaks to your tenant’s configurations. This helps ensure that your crucial Microsoft 365 security policies and settings remain unchanged.
- Smooth Microsoft 365 Tenant-to-Tenant Migration: Amid cross-tenant migration problems? No worries! With M365DSC, you can ensure that your new M365 tenant’s settings align perfectly with the old ones. Simply deploy the settings, then use M365DSC to double-check that everything matches up.
- Determine Microsoft 365 Security Best Practices: When managing multiple Microsoft 365 tenants, thoroughly compare each one using M365DSC to scrutinize their security settings and pinpoint the best practices. Once you’ve uncovered the Microsoft 365 security best practices, seamlessly apply them across all your tenants for unified protection.
Now, let’s delve into the steps to get a Microsoft 365 tenant discrepancy report with M365DSC. Before getting into that, make sure you install the Microsoft365DSC module.
Use New-M365DSCDeltaReport to Compare M365 Tenant Settings
You can utilize the “New-M365DSCDeltaReport” cmdlet to generate a discrepancy report for two scenarios:
- Compare configurations of a two Microsoft 365 tenant
- Compare previous Microsoft 365 settings with existing settings of a M365 tenant
1. Microsoft365DSC – Comparing Configurations of a Two M365 Tenant
Let’s say there are two tenants: Tenant A and Tenant B.
To assess the Microsoft 365 settings of these two different tenants and analyze their configuration differences, you’ll need to rely on the “Export-M365DSCConfiguration” cmdlet first. So, export the Microsoft 365 settings of both Tenant A and Tenant B using the M365DSC export cmdlet.
After completing the export process, make sure to take note of the file paths of each configuration. Then, you can proceed to use the following cmdlet with the correct paths for the “Source” and “Destination” parameters.
Cmdlet:
|
1 |
New-M365DSCDeltaReport –Source <Path of configuration file of Tenant A> -Destination <Path of configuration file of Tenant B> -OutputPath <Specify the path of the output HTML file> |
Example:
|
1 |
New-M365DSCDeltaReport –Source D:\M365DSC\TenantAconfig.ps1 -Destination D:\M365DSC\TenantBconfig.ps1 -OutputPath D:\M365DSC\DiscrepancyReport.html |
Below is a sample HTML report illustrating a comparison of Conditional Access policy settings between two tenants (Tenant A and Tenant B).
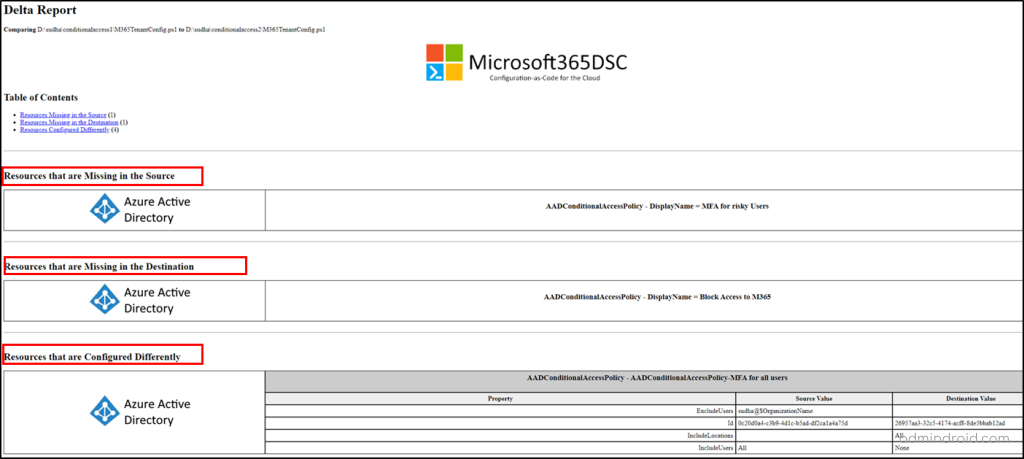
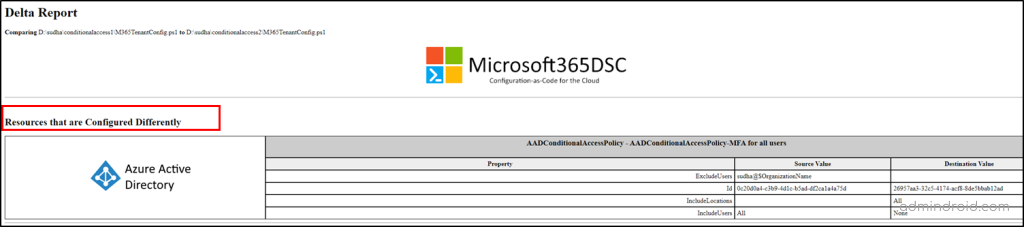
The report will showcase both the missed configurations and the settings that differ between the Microsoft 365 tenants. If you prefer to focus solely on identifying the differently configured settings, you can employ the “–DriftsOnly” parameter when generating the report.
Cmdlet:
|
1 |
New-M365DSCDeltaReport –Source <Specify the configuration file of Tenant A> -Destination <Specify the configuration file of Tenant B> -OutputPath <Specify the path of the output HTML file> -DriftsOnly $true |
Example:
|
1 |
New-M365DSCDeltaReport –Source D:\M365DSC\TenantAconfig.ps1 -Destination D:\M365DSC\TenantBconfig.ps1 -OutputPath D:\M365DSC\Report.html -DriftsOnly $true |
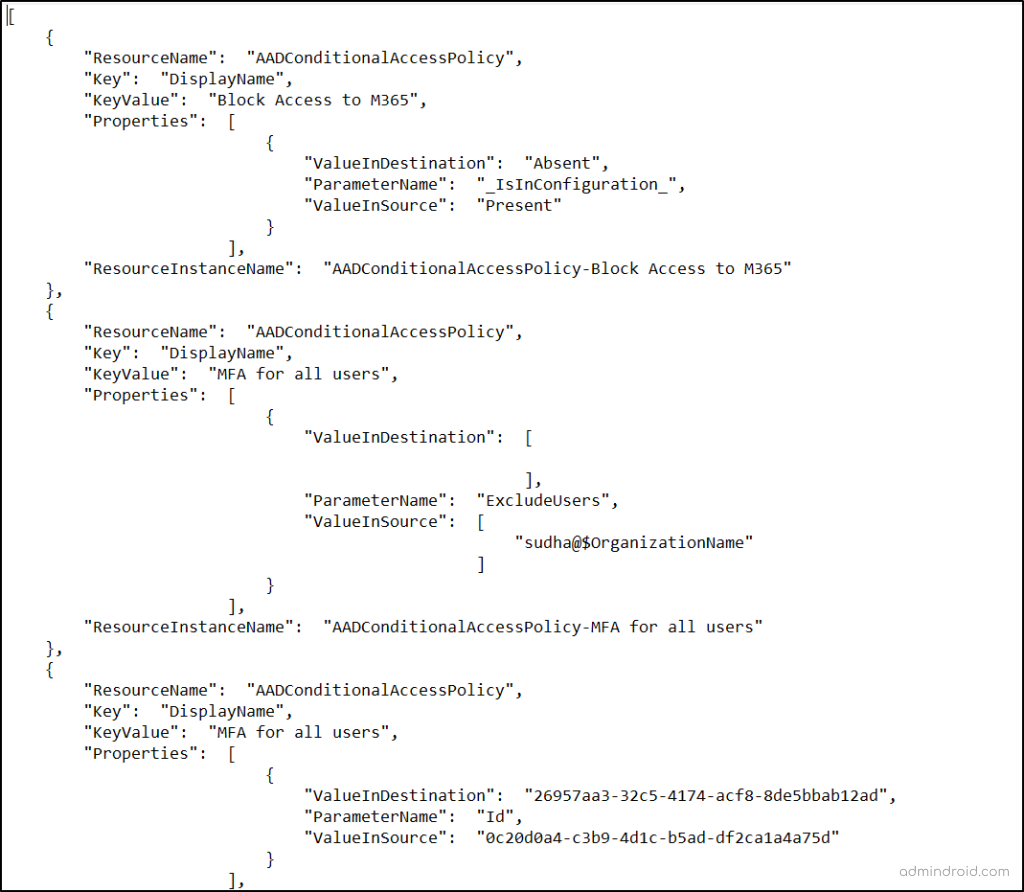
Not only in HTML format, but you can also get the report as a JSON file. To get a readable JSON discrepancy file, you need to use “
|
1 |
New-M365DSCDeltaReport –Source D:\M365DSC\TenantAconfig.ps1 -Destination D:\M365DSC\TenantBconfig.ps1 -OutputPath D:\M365DSC\Report.json -Type JSON |
2. Use Microsoft365DSC to Compare Microsoft 365 Settings Over Time
Now that we’ve explored the process of comparing various Microsoft 365 tenants, let’s delve into evaluating configurations of a single tenant.
You can compare previous Microsoft 365 settings with existing settings of a M365 Tenant.
For example, you can compare the current settings of your M365 environment with a configuration file exported six months earlier. For that, ensure you have retained the previously exported file for time-based comparisons.
To conduct this comparison, you just need to replace the respective file paths in the appropriate parameters of the previously mentioned cmdlet. This straightforward process allows you to assess any changes or updates in your tenant’s configuration over time with ease.
Cmdlet:
|
1 |
New-M365DSCDeltaReport –Source <Specify the recently exported configuration file> -Destination <Path of the file exported earlier> -OutputPath <Specify the path of the output HTML file> |
Example:
|
1 |
New-M365DSCDeltaReport –Source D:\M365DSC\TenantConfig1.ps1 -Destination D:\M365DSC\TenantConfig2.ps1 -OutputPath D:\DiscrepancyReport.html |
Here are some of the discrepancy reports you must generate periodically to ensure you Microsoft 365 security.
📢 Entra ID Settings and Policies
- Get Microsoft 365 Conditional Access changes report
- Export Cross-tenant access settings assessment report
- Get Authentication Methods policy misconfiguration report
📢 Exchange Online Essential Configurations
- Get Microsoft 365 mailbox permissions disparity report
- Export EXO automatic reply configuration discrepancy report
- View OWA mailbox policy changes report
📢 Microsoft Teams Crucial Settings
- Retrieve Teams channel policy drifts report
- Get MS Teams guest meeting settings discrepancy report
- Retrieve Microsoft Teams files policy assessment report
📢 SharePoint Online Security Settings
- Export SPO Online access request setting changes report
- Get External sharing settings drift report
- Retrieve SPO storage entity setting configuration report
📢 Microsoft OneDrive Fundamental Settings
- Export OneDrive settings misconfiguration report
📢 Office 365 and Intune Settings and Policy
- Export Office 365 admin audit log settings discrepancy report
- Get Intune account protection policy changes report
📢 Security and Compliance Policies
- Export misconfigured auto sensitivity label rule report
- Get DLP policy misconfiguration report
Assert-M365DSCBlueprint: Compare a Microsoft 365 Tenant Setting with Blueprint
Up to this point, we’ve compared the settings of two Microsoft 365 tenants and generated a report highlighting any discrepancies. However, we can’t always guarantee the accuracy of our reports!
So, it’s essential to assess your Microsoft 365 tenant settings against industry best practices using a blueprint💡. This serves as a benchmark security configuration file reviewed or approved by either your organization or Microsoft blueprints.
Thus, Microsoft365DSC blueprint streamlines this process by allowing organizations to validate their existing Microsoft 365 tenant configuration with just a single cmdlet😎. Before delving into the command, let’s first explore how to create a blueprint.
How to Create a Blueprint with Microsoft 365 Baseline Configurations?
Creating a blueprint is pretty straightforward! You’ll need to write some DSC (Desired State Configuration) code in .ps1 format with baseline settings, just like how we usually do for auto-deploy settings scenarios.
Now, you might think that we can then use the “New-M365DSCDeltaReport” cmdlet to assess the settings with the created Microsoft365DSC blueprint. It’s a valid thought!
But blueprints stand one step tall ahead with its out of the box capability! The great thing about blueprints is their ability to include metadata, offering contextual information within the discrepancy report. Take this code snippet, for instance.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
Node localhost { AADConditionalAccessPolicy "AADConditionalAccessPolicy-Block Access to M365" { AuthenticationContexts = @(); BuiltInControls = @("mfa");### L1|We recommend to require MFA for all users ClientAppTypes = @("all"); CloudAppSecurityType = ""; Credential = $Credscredential; CustomAuthenticationFactors = @(); DeviceFilterRule = ""; DisplayName = "Block Access to M365"; Ensure = "Present"; ExcludeApplications = @(); ExcludeExternalTenantsMembers = @(); ExcludeExternalTenantsMembershipKind = ""; ExcludeGroups = @(); ExcludeLocations = @(); ExcludePlatforms = @(); ExcludeRoles = @(); ExcludeUsers = @("Diego chris"); ### L2|We recommend to exclude global admin to avoid locking out! GrantControlOperator = "OR"; Id = "57b051fe-61b7-40ab-9d00-4c2d3b454850"; IncludeApplications = @("All"); IncludeExternalTenantsMembers = @(); IncludeExternalTenantsMembershipKind = ""; IncludeGroups = @(); IncludeLocations = @("AllTrusted"); IncludePlatforms = @(); IncludeRoles = @(); IncludeUserActions = @(); IncludeUsers = @("None"); PersistentBrowserMode = ""; SignInFrequencyType = ""; SignInRiskLevels = @(); State = "enabled"; ### L3|We recommend to turn on the policy to enforce it in the tenant UserRiskLevels = @(); } |
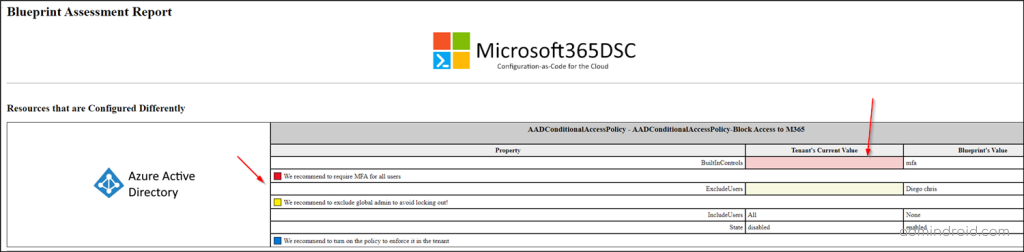
In this example, the metadata entries are indicated by the ### syntax. The text following the three-pound signs indicates the level of severity and contextual information. Currently, you can use the three levels of severities,
- L1: Critical (will appear in red in the discrepancy report)
- L2: Warning (will appear in yellow in the discrepancy report)
- L3: Information (will appear in white in the discrepancy report)
That’s all! Once you’ve created a blueprint, you can use the Assert-M365DSCBlueprint cmdlet to compare your Microsoft 365 tenant against a good configuration. You can also make use of Microsoft blueprints to validate your tenant configuration.
|
1 2 |
Assert-M365DSCBlueprint -BluePrintUrl <Blueprint file Path> -OutputReportPath <Full path to where to save the HTML report> -Credentials (Get-Credential) |
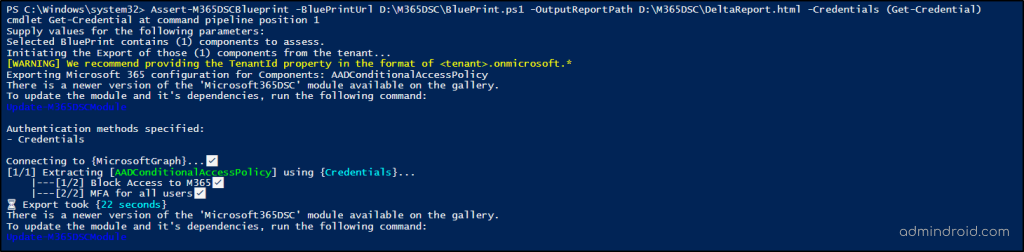
- It’s crucial to note that even if a drifted property doesn’t have associated metadata in the blueprint, it will still show up in the discrepancy report. However, it won’t include any contextual information.
Here’s the sample HTML file with metadata comparing the existing CA policies of a tenant and a blueprint.
Effectively Use Microsoft365DSC to Compare Microsoft 365 Settings!
That’s it! With Microsoft365DSC, spotting and fixing missed or misconfigured settings is a breeze. Its handy discrepancy report highlights exactly what needs attention and helps you to make necessary changes with ease!
So, why wait? Start using the configuration comparison tool “Microsoft365DSC” today and let it be your trusty assistant in keeping your configurations in check.
I hope this blog brings you more information about how to use Microsoft365DSC to compare Microsoft 365 settings. Furthermore, get back to us for queries and we are happy to assist you!