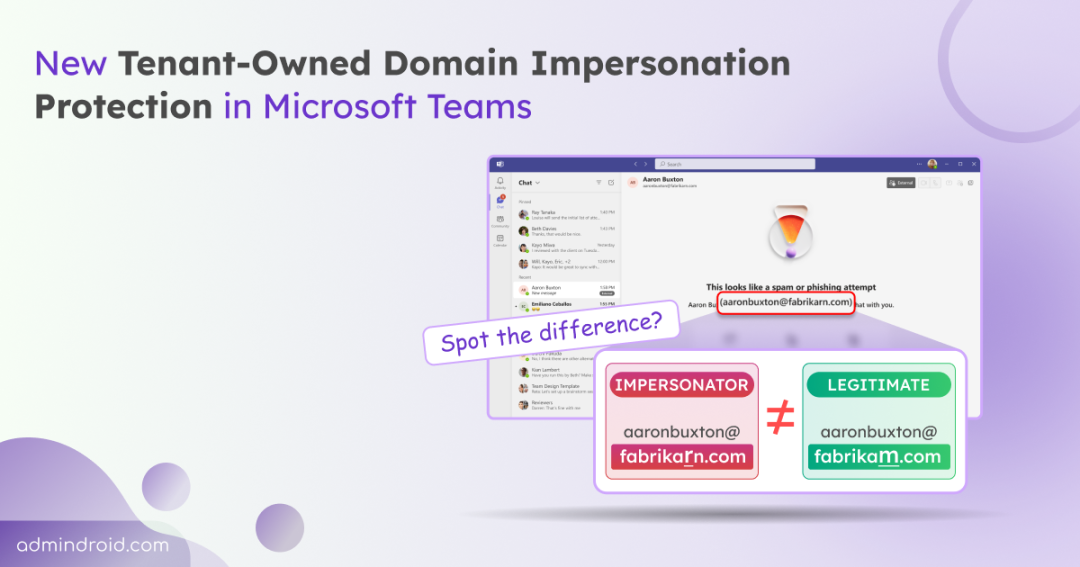
Imagine receiving a Teams chat from “support@fabrikarn.com” instead of “support@fabrikam.com” (where rn is cleverly used to look like m). At a quick glance, it can appear legitimate. One misplaced letter, and suddenly your employees are sharing sensitive information with an attacker posing as a colleague.
This type of domain impersonation has become increasingly sophisticated. Cybercriminals know that Teams conversations often bypass the same scrutiny applied to emails.
That’s why Microsoft is introducing a powerful new security feature — domain impersonation protection.
It’s designed to detect and warn internal users when external contacts attempt to impersonate your organization’s domain. Rolling out in December 2025, this automatic domain impersonation protection enhances your overall Teams security posture without requiring any action from IT administrators.
What is Domain Impersonation?
In collaboration platforms like Microsoft Teams, attackers use two closely related impersonation methods: domain impersonation and brand impersonation.
- Brand impersonation — attackers pose as well-known companies or services.
- Domain impersonation — attackers mimic your organization’s own domain to appear like internal users.
While both methods exploit user trust, domain impersonation is especially dangerous because it targets your organization’s identity directly. This technique — often called domain spoofing involves registering lookalike domains that closely resemble real ones, tricking employees into believing the messages are from trusted internal sources.
Common examples include:
- Replacing letters with similar-looking characters (fabrikarn.com vs fabrikam.com)
- Adding or removing hyphens (acme-corp.com vs acmecorp.com)
- Using different top-level domains (company.co vs company.com)
- Subtle misspellings (mircosoft.com vs microsoft.com)
These attacks are particularly dangerous because they bypass traditional email security filters and target users directly through collaboration platforms like Microsoft Teams. Once attackers blend into Teams as an employee, they can easily request sensitive information or share malicious links — all while appearing completely legitimate.
New Domain Impersonation Protection for Microsoft Teams
Following the introduction of brand impersonation protection update last year, Microsoft just introduced a major update! Microsoft Teams will now support domain impersonation protection by default, which is a huge security boost for the Teams platform!
By automatically detecting and warning users about suspicious lookalike domains, this feature adds a critical layer of defense against increasingly sophisticated social engineering attacks.
The feature will be ON by default for all tenants that allow external access in Teams. It works seamlessly across all platforms -Desktop, Web, iOS, Android, and Mac.
Rollout Timeline
General Availability: Begins in early December 2025 and expected to complete by mid-December 2025.
- Before the Rollout: Teams only scanned for brand impersonation risks. It focused on detecting attempts to mimic well-known companies like Microsoft, Google, or major banks.
- After the Rollout: Teams will check for both brand impersonation AND attempts to impersonate your organization’s specific domains. The system compares external sender domains against your tenant’s registered domains, looking for suspicious similarities that could indicate an impersonation attempt.
How Real-Time Detection Works: The Three-Layer Impersonation Protection Experience
The detection happens in real-time, meaning there’s no delay between when an attacker sends a message and when your users are protected. When Teams detects a potential domain impersonation attempt, users go through a carefully designed three-step process that balances security with usability:
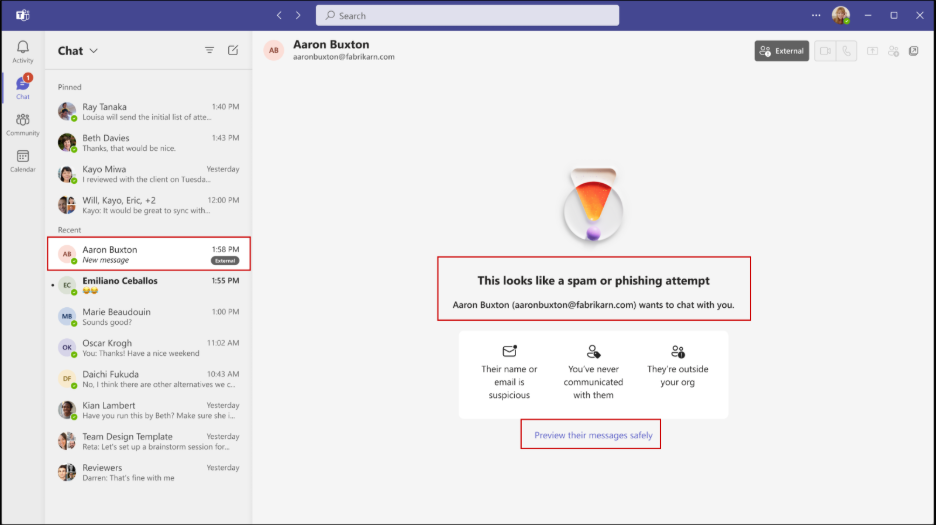
1. Initial High-Risk Warning
When domain impersonation is detected, users immediately see a prominent warning:
“This looks like a spam or phishing attempt.”
The interface clearly displays:
- The sender’s name and suspicious email address (e.g., aaronbuxton@fabrikarn.com). It doesn’t reveal the exact issue with the domain — it simply flags the message as risky to alert the user.
- An “External” badge to reinforce that this is an outside contact
- Three warning indicators explaining why the contact is flagged:
- Their name or email is suspicious
- You’ve never communicated with them
- They’re outside your organization
- A clear call-to-action: “Preview their messages safely”
At this stage, users cannot immediately accept the chat. They must consciously choose to preview the content first, preventing accidental engagement with potential threats.
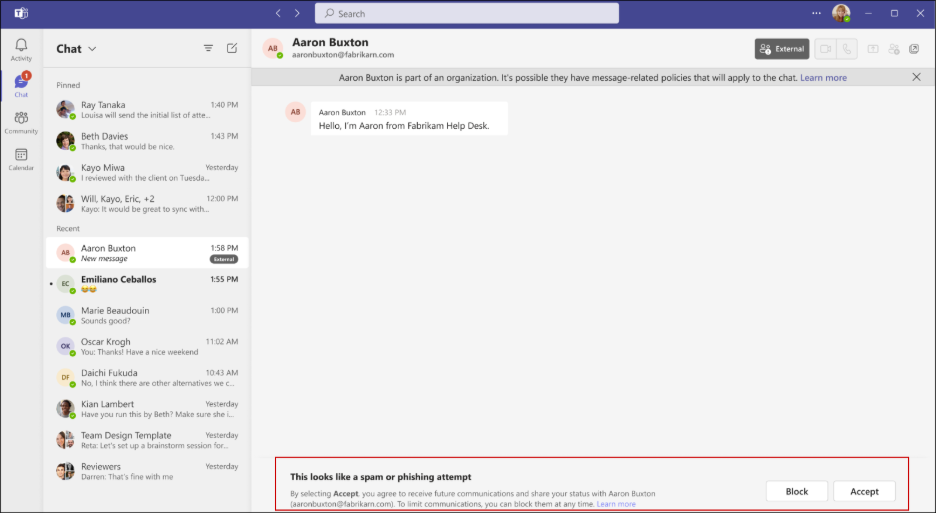
2. Safe Message Preview
When the user clicks “Preview their messages safely,” they enter a protected viewing mode where they can:
- Read the sender’s message without the sender knowing it’s been viewed.
- Evaluate the legitimacy of the request based on the content.
- Make an informed decision with two clear options:
- “Accept” – Proceed with the conversation despite the warning.
- “Block” – Reject and block the sender permanently.
This preview layer is crucial because it allows users to see if the message contains legitimate business context (like a mutual connection or specific project reference) or suspicious requests (urgent demands for credentials, money transfers, or sensitive data).
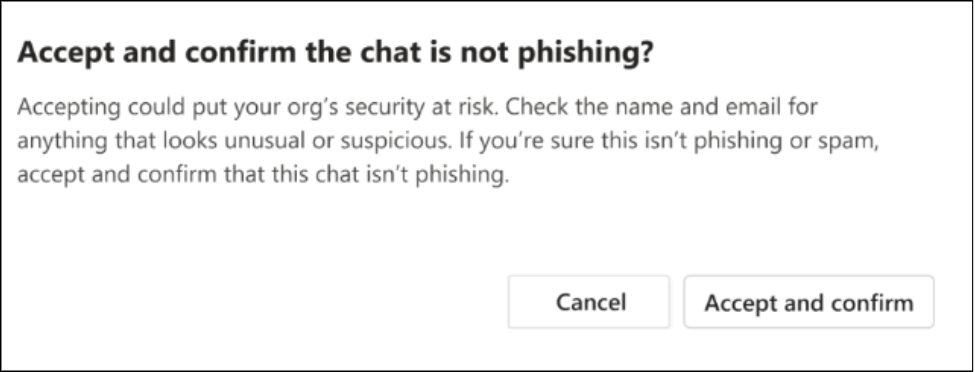
3. Final Confirmation Check
If the user decides to accept the chat despite the warning, Teams doesn’t simply proceed—it adds one final safeguard. Users are prompted again with a confirmation dialog that:
- Reminds them to verify the sender’s legitimacy.
- Explicitly asks them to confirm the sender is not attempting phishing.
- Requires deliberate action to proceed with accepting the chat.
This double-confirmation step ensures that users are making a conscious, informed decision rather than clicking through warnings without full consideration. It’s the last line of defense before establishing a potentially risky external connection.
With this three-layered protection, the feature strikes a careful balance: it doesn’t block all external communication (which would hinder legitimate collaboration), but it does force users to slow down and think critically before engaging with potentially dangerous contacts.
By closing this critical security gap, Teams now actively protects tenant-owned domains, significantly reducing the risk posed by even the most sophisticated lookalike domain attacks. As external threats continue to evolve, this update ensures that Teams users benefit from a powerful, built-in defense that safeguards sensitive information without slowing down collaboration.
Domain impersonation doesn’t stand a chance. Teams has your back! 🛡️