On Day 19 of Cybersecurity Awareness Month, learn how to reset the KRBTGT account password in Window Active Directory to protect against Kerberos authentication attacks. Stay tuned for upcoming blogs in our ongoing Cybersecurity blog series.
What if a single compromised account could quietly unlock access to your entire organization? This is exactly what happens when attackers target the KRBTGT account, which plays a central role in Kerberos authentication within Active Directory. Using tools like Mimikatz, they can forge its tickets, which act like master keys, giving them unrestricted access across your domain. These forged credentials often go unnoticed, allowing attackers to move laterally, steal data, and maintain persistent access.
The real danger lies in the longevity of these tickets. Once created, they remain valid until the KRBTGT password is changed. That’s why regularly resetting this account’s password is essential to invalidate existing tickets and protect your environment.
In this blog, we walk you through the steps to safely reset the KRBTGT account password in Active Directory, helping you safeguard your domain against ticket-based attacks.
What is the KRBTGT Account in Active Directory
In Active Directory, KRBTGT refers to the Kerberos Ticket Granting Ticket account. Kerberos is the main authentication protocol used to verify any security principal, including user accounts, computer accounts, service identities, and Managed Service Accounts (MSAs). The Key Distribution Center (KDC) is a trusted service that issues and manages Kerberos authentication tickets within the domain.
The KRBTGT account is a built-in service account automatically created when a new domain is set up. It serves as the service account for the KDC, providing the encryption key used to sign and validate Kerberos tickets. By default, its Security Identifier (SID) is S-1-5-<domain>-502, and it resides in the Users container. Microsoft advises against moving this account to another organizational unit (OU).
The account cannot be deleted, renamed, or enabled, and it is not intended for interactive sign-ins. It also functions as the security principal name (SPN) used by the KDC, as defined in RFC 4120. Kerberos uses the KRBTGT password to encrypt Ticket Granting Tickets, which allow users to access network resources without re-entering credentials.
The KRBTGT account keeps its two most recent passwords based on its default password history value, which is important during password resets.
The Importance of KRBTGT Account Password Reset
Regular KRBTGT password resets strengthen your domain’s resilience by limiting the lifespan of potentially compromised credentials.
Mitigate Golden Ticket Attacks
A compromised KRBTGT password hash allows attackers to create Golden Tickets (forged Kerberos Ticket-Granting Tickets). With these, an attacker can impersonate any user (even domain admins) and maintain persistent, undetected access to your domain.
Maintain Security Hygiene
Like changing any important password, regularly resetting the KRBTGT password helps maintain good security hygiene. This proactive measure prevents undetected attacks and ensures cryptographic keys are kept current. For this reason, Microsoft recommends performing a KRBTGT password reset at least every 180 days, even if no compromise has been detected in your domain.
Invalidate Forged or Stolen Tickets
Resetting the KRBTGT account password invalidates existing Kerberos tickets that were encrypted with the old password hash, so any stolen (forged) tickets become unusable. It’s an immediate, effective way to cut off attacker access and stop ongoing Ticket misuse.
How to Check KRBTGT Account Password Last Set Date
Prior to resetting the KRBTGT account password, it’s essential to verify the last password set date. This ensures that a reset is necessary and helps maintain stable authentication across the domain. Additionally, checking the time since the previous reset allows administrators to determine for making a second reset and prevent potential disruptions in domain connectivity.
You can use the following steps to check the KRBTGT account’s last password set date.
- Open Server Manager, go to Tools, and select Active Directory Users and Computers.
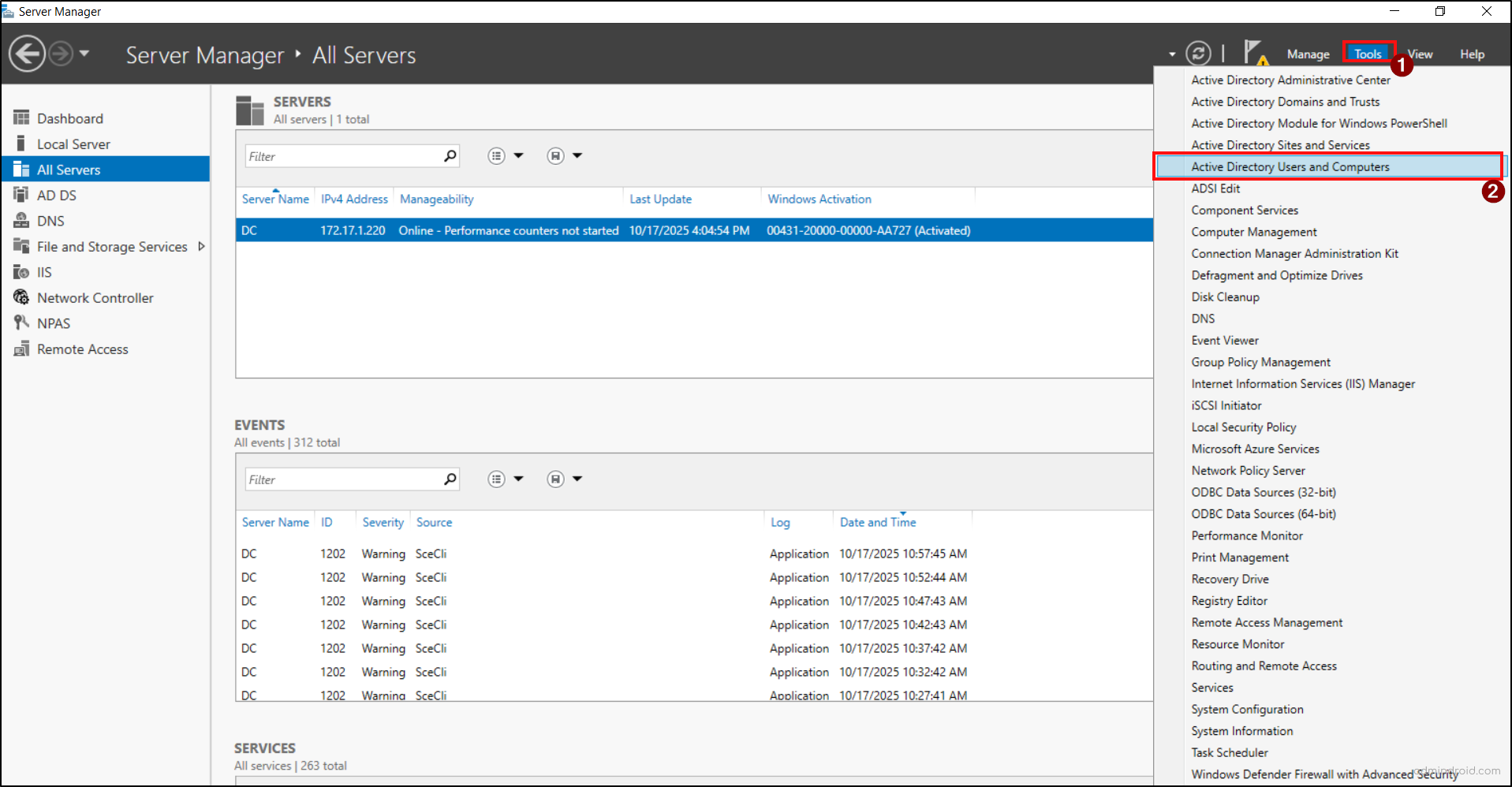
- In the ADUC console, enable Advanced Features from the view tab to ensure the krbtgt account is visible.
- Then, expand your domain and navigate to the Users container.
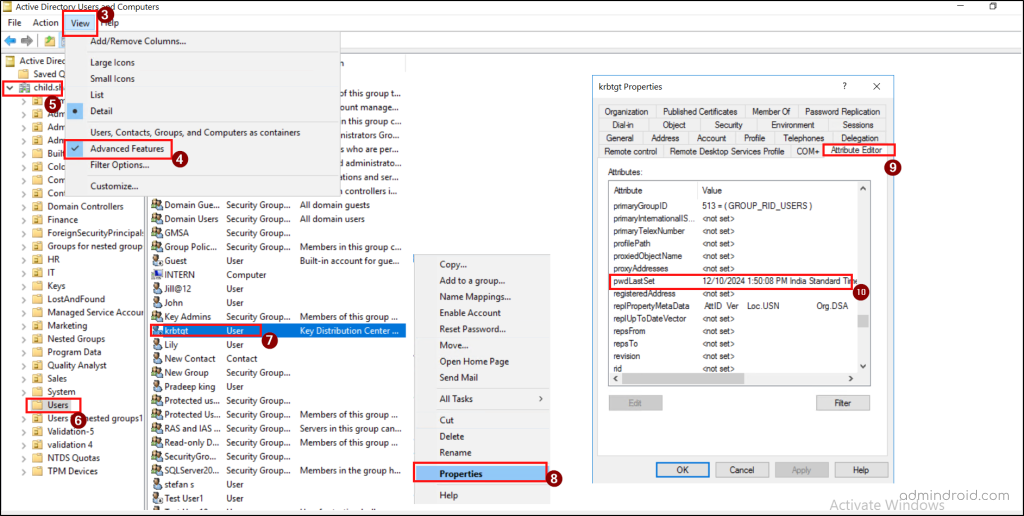
- Find the krbtgt account, right-click on it, and choose properties.
- Navigate to the Attribute Editor tab and scroll down to find the PwdLastSet attribute value.
Alternatively, you can use PowerShell to find the KRBTGT account’s last password set date using the steps below.
Make sure that the Active Directory PowerShell module is installed on your computer using the cmdlet below.
|
1 |
Get-Module -ListAvailable ActiveDirectory |
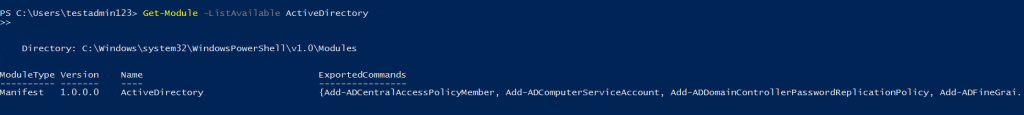
If you notice that the Active Directory PowerShell module isn’t installed or imported on your computer, you can use the following cmdlet to install and import Active Directory PowerShell module.
|
1 2 |
Install-WindowsFeature RSAT-AD-PowerShell Import-Module ActiveDirectory |
Next, run the following cmdlet to get the last password set for the krbtgt account.
|
1 |
Get-ADUser "krbtgt" -Property Created, PasswordLastSet |
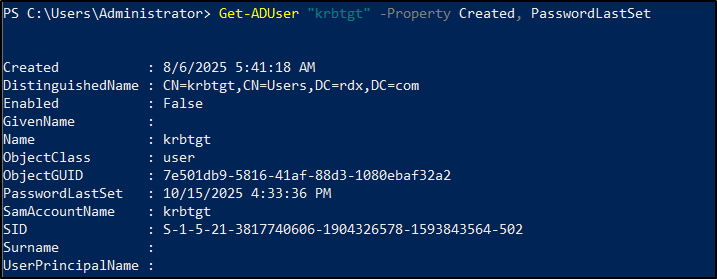
Here, review the last password set date to ensure it hasn’t been updated recently to perform KRBTGT account password reset.
How to Reset the KRBTGT Account Password
Resetting the KRBTGT password is different from changing a regular user password. This change updates authentication across your entire domain and plays an important role in Active Directory Forest recovery.
Since the KRBTGT account keeps its last two passwords, resetting it twice is required to eliminate old hashes and fully invalidate existing Kerberos tickets.
Ensure you have Domain Admin rights and that all Domain Controllers replicate correctly to perform the reset operation without issues. You can use any one of the following methods to reset the KRBTGT account password.
1. Reset the KRBTGT Account Password Using Active Directory Users and Computers Console
To change the krbtgt account password in ADUC, follow the steps below.
- Right-click the krbtgt account in the ‘Users’ container and select Reset password from the list.
- In the Reset Password dialog box, enter a strong new password, confirm it, and click OK.
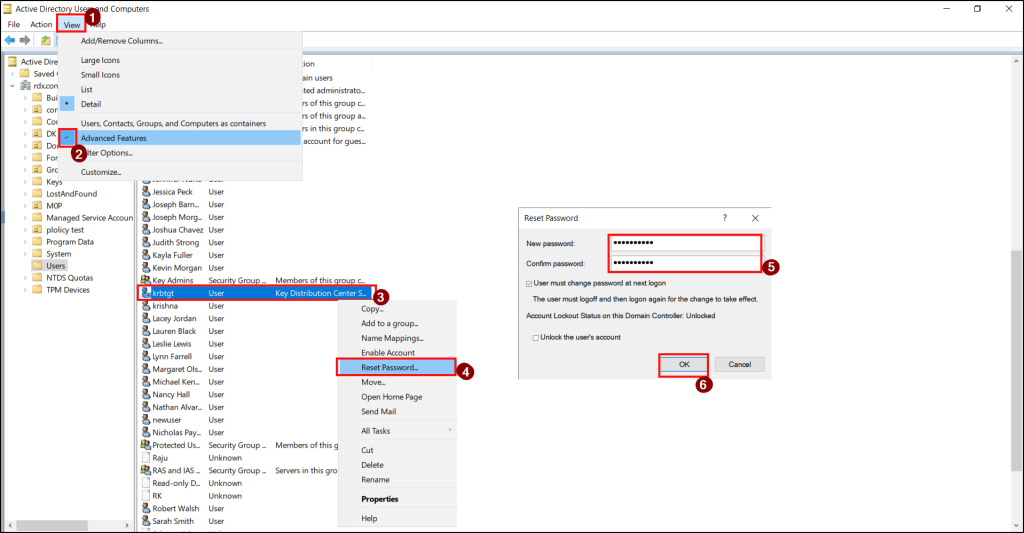
- By default, it takes about 10 to 12 hours for a KRBTGT password change to replicate across all domain controllers. However, this duration can vary depending on your organization’s configured Ticket-Granting Ticket (TGT) lifetime.
- After the replication of the password change, you should reset the password again to completely remove the old password, as the KRBTGT account stores the last 2 passwords.
2. Update the KRBTGT Account Password Using PowerShell
You can execute the following cmdlet to reset the KRBTGT account password after replacing the “<NewStrongPassword>” with the actual password that you want to enter for resetting.
|
1 |
Set-ADAccountPassword -Identity krbtgt -Reset -NewPassword (ConvertTo-SecureString "<NewStrongPassword>" -AsPlainText -Force) |
To ensure that the password has been successfully updated, you can execute the PowerShell cmdlet provided below. Running this command will allow you to verify the status of the password and confirm whether the update has been applied as intended.
|
1 |
Get-ADUser -Identity "krbtgt" -Properties PasswordLastSet | Select-Object Name, PasswordLastSet |
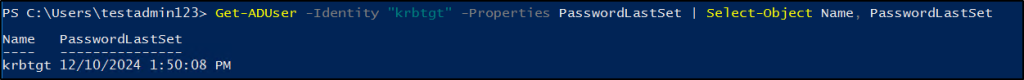
Using the same method, you need to reset the KRBTGT password again after 10 to 12 hours, depending on the Kerberos ticket’s lifetime. This ensures proper replication and removes access for old password history or any compromised tickets across all domain controllers.
Common Mistakes to Avoid for Resetting the KRBTGT Account Password
While the KRBTGT password reset process is straightforward, overlooking key steps can lead to authentication issues or incomplete resets. Here are some common pitfalls to watch for and avoid.
- Resetting Only Once: Since the KRBTGT account retains two password hashes, performing only one reset leaves the old hash active, allowing forged tickets to remain valid. To fully invalidate them, always perform two resets with an appropriate time gap between them.
- Not Allowing Enough Time for Replication: After the first KRBTGT password reset, it’s important to allow sufficient time for the change to replicate across all Domain Controllers (DCs). Performing the second reset too soon can lead to inconsistent authentication data and Kerberos ticket validation issues. To ensure replication has completed successfully, verify the status of all DCs using the following command.
|
1 |
repadmin /replsummary |
- Performing the Reset During Business Hours: Resetting the KRBTGT password during peak usage can interrupt authentication sessions and cause temporary access issues for users and services. Always schedule the reset during a planned maintenance window to minimize disruption.
- Skipping Verification After Reset: Some administrators assume the reset process is complete once the commands are executed. However, verifying that new Kerberos tickets are being issued and that replication is healthy is essential.
By avoiding these common mistakes, administrators can ensure a seamless KRBTGT password rotation that strengthens domain security without causing operational impact.
In short, the KRBTGT account is not just a ticket issuer; it protects the integrity of your domain’s authentication system. Keeping its password regularly updated is simple yet one of the most essential Active Directory security best practices.
We’re only on Day 19 of Cybersecurity Awareness Month, and there are still more insights to come! Stay tuned for upcoming cybersecurity blogs, and feel free to share your comments or questions below.