On Day 18 of Cybersecurity Awareness Month, learn how to enhance security by configuring idle session timeout for Entra portal. Stay tuned for upcoming blogs in our M365 Cybersecurity blog series.
The Microsoft Entra portal is essential for managing Azure AD identities, objects, and apps. Securing access to it is critical to protect your Azure AD tenant from threats like session hijacking and unauthorized access. Without properly configuring the session timeout for Entra portal, it could become vulnerable, putting your organization at risk.
Therefore, this blog will explain how to set up Entra portal’s session lifetime to enhance Microsoft 365 security. Let’s get started.
Why Configuring Session Timeout for Entra Portal is Crucial?
Session timeouts may seem like a minor setting in Entra’s security features, but they are critical for securing your Microsoft Entra. Consider the following scenario to understand this more clearly.
For instance, if one of your organization’s admins or users leaves their Entra portal session active on an unsecured network, it can lead to unauthorized access. In such cases, if the session timeout is configured, it will automatically terminate the idle sessions. This termination prevents the exposure of privileged accounts that could lead to the compromise of your organization’s identity infrastructure.
Configure Session Timeouts for Entra Portal
Microsoft allows Global Administrators to configure the Entra idle session timeout limit at the directory level. It also enables users or other admins to override the settings configured at the directory level.
Points to Note:
- By default, the Microsoft Entra ID session lifetime is set to never sign-out in a tenant.
- As the Entra portal is a dedicated platform for handling Azure AD identity-related tasks (previously part of the Azure portal), configuring the session timeouts applies to both portals, wherever applicable.
How to Configure Session Timeouts in Entra Portal for Directory-wide Use?
To enforce the Azure portal session timeout for all users in your organization, follow these steps:
Prerequisite: Global Administrator access.
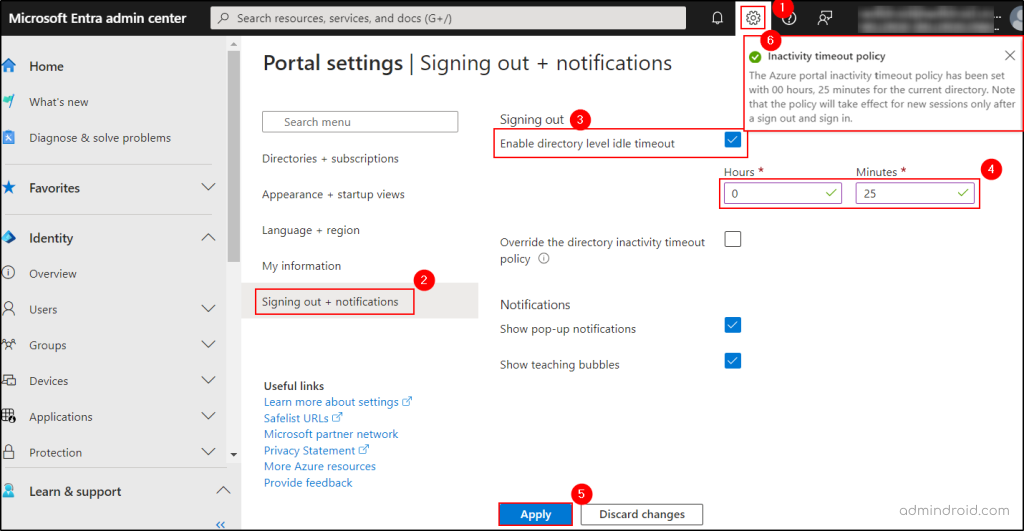
- In the Microsoft Entra admin center, click on the settings icon (⚙) available at the top right corner and head to the Signing out + notifications tab.
- Turn on the Enable directory level idle timeout check box.
- Next, enter the Hours and Minutes for the maximum period a user can be inactive before their session is automatically signed out.
- Click Apply to configure the setting for all users in the directory.
- Finally, verify that the policy was applied correctly by checking for a success notification.
Once set, all future portal sessions will adhere to this timeout setting. The change will take effect for currently signed-in users after their next sign-in.
How Can Users Override the Session Timeouts for the Entra Portal?
Microsoft doesn’t offer a feature for the Global Administrators to configure different session timeouts for individual users in the tenant. But other admins or the end users can set a shorter timeout interval for themselves. However, they can’t make their individual session timeout to a longer interval than the current option set by a Global Administrator.
Note: Global Administrators can also follow the same configuration discussed here to override directory-wide session timeout settings.
To override the directory-wide settings for the session timeout, follow the steps described here:
- Log in to the Entra admin center.
- Click on the settings icon (⚙) available at the top right corner and go to the Signing out + notifications tab.
- Enable the Override the directory inactivity timeout policy checkbox, and then enter the desired Override value.
- Finally, click Apply.

What Happens When the Inactive Session Timeout Expires?
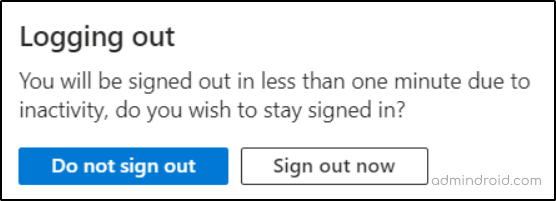
When a user leaves after signing in, they will see the following prompt after their session expired on Azure portal:
“You will be signed out in less than one minute due to inactivity. Do you wish to stay signed in?”
- If the user selects Do not sign out, the session will be extended for a new timeout period.
- If they choose Sign out now, the session will immediately end.
- If no action is taken, the session will automatically sign out within a few seconds.
Key Considerations for Setting Entra Portal Session Timeouts
Configuring session timeouts is vital, but finding the right balance between security and user experience is also necessary. Here are some best practices and important points to consider:
Choose the Right Timeout Duration: Setting session timeouts too short can frustrate users by requiring frequent re-authentication. On the other hand, a duration that is too long may expose the system to security risks. Aim for a balance that suits both security and user experience.
Adjust Timeout Settings: Global Administrators can modify a previously selected timeout by repeating the configuration steps. If the ‘Enable directory level idle timeout’ option is unchecked, the previous timeout setting remains unchanged. However, individual users can adjust their personal session timeouts for Microsoft Entra.
Implement Multi-Factor Authentication (MFA): In addition to configuring session timeout, enforce multifactor authentication for users to add an extra layer of security. Even if users have saved their passwords in their browsers, MFA ensures that only authorized users can re-authenticate after a timeout.
Understand ‘Stay Signed In’ Behavior: Even if users select “Yes” on the “Keep me signed in” prompt, they will still be signed out when the Entra portal session timeout is enforced. This ensures that session timeout policies are consistently applied, requiring users to re-authenticate during their next sign-in.
Difference Between Entra Portal & Microsoft 365 Idle Session Timeout: While the Entra portal session timeout targets inactivity within the portal, the idle session timeout for Microsoft 365 apps works separately. Administrators should configure both timeouts to maintain security across environments where users access multiple services.
Conclusion
Overall, I hope this blog will help you prevent unauthorized access or session hijacking when an attacker takes over an active session. By enforcing session timeout for Entra portal, you limit the window of opportunity for attackers to exploit idle sessions. If you have any queries regarding Azure AD session timeout settings, kindly leave them in the comment section below.