On Day 8 of Cybersecurity awareness month, learn to avoid data leakages by configuring Idle Session Timeout. Stay tuned for more blogs in the Cybersecurity blog series.
As we have entered the hybrid work environment, accessing an organization’s resources from web apps on unmanaged devices or shared devices is on the rise. Unmanaged devices offer a huge opportunity for attackers to compromise those devices and lead to data breaches. To protect the company’s sensitive information, idle session timeout in Microsoft 365 was introduced as an additional layer of security. Let’s see how idle session timeout balances user productivity and meets the organization’s security and compliance requirements.
“Security is not a product, but a process!”
-Bruce Schneier
What is Idle Session Timeout in Microsoft 365?
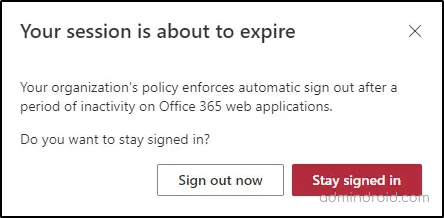
Idle session timeout is a feature that automatically signs out users from Microsoft 365 web apps if they are inactive. It prevents data disclosure when users forget to sign out of web applications. It is a tenant-wide feature and will apply to all users in the organization. Also, you should be aware that idle session timeout will not affect Microsoft 365 desktop or mobile apps. The below prompt will be shown while the user has been inactive in the M365 webapps for the timeout period configured.
Firstly, the idle session timeout settings were available only for Outlook web app and SharePoint Online. By analyzing its perks and customer requests, Microsoft later implemented an efficient solution for most of the Microsoft 365 web apps.
The Microsoft 365 web apps include,
- Outlook Web App
- OneDrive for Business
- SharePoint Online
- Word, Excel, PowerPoint on the web
- Microsoft 365 Admin Center
- Office.com, and other start pages
Who can Enable Idle Session Timeout in Microsoft 365?
To enable idle session timeout, you must be assigned with any one of the following roles.
- Global admin
- Security admin
- Application admin
- Cloud Application admin
How to Enable Idle Session Timeout in Microsoft Admin Center?
Follow the steps below to turn on idle session time out in Microsoft admin center:
Set Up Idle Session Timeout for All Devices in Microsoft 365:
- Open Microsoft 365 admin center.
- Navigate to Settings –> Org settings –> Security & privacy.
- Select Idle session timeout.
- Check in the box to set the period of inactivity for users to be signed off from Office web apps.
- Choose a Timeout Value from the dropdown menu.
- Select Save to configure the idle session timeout setting.
Note – If you pick custom (in minutes) as a time interval, it must be between 5 and 1440 minutes.
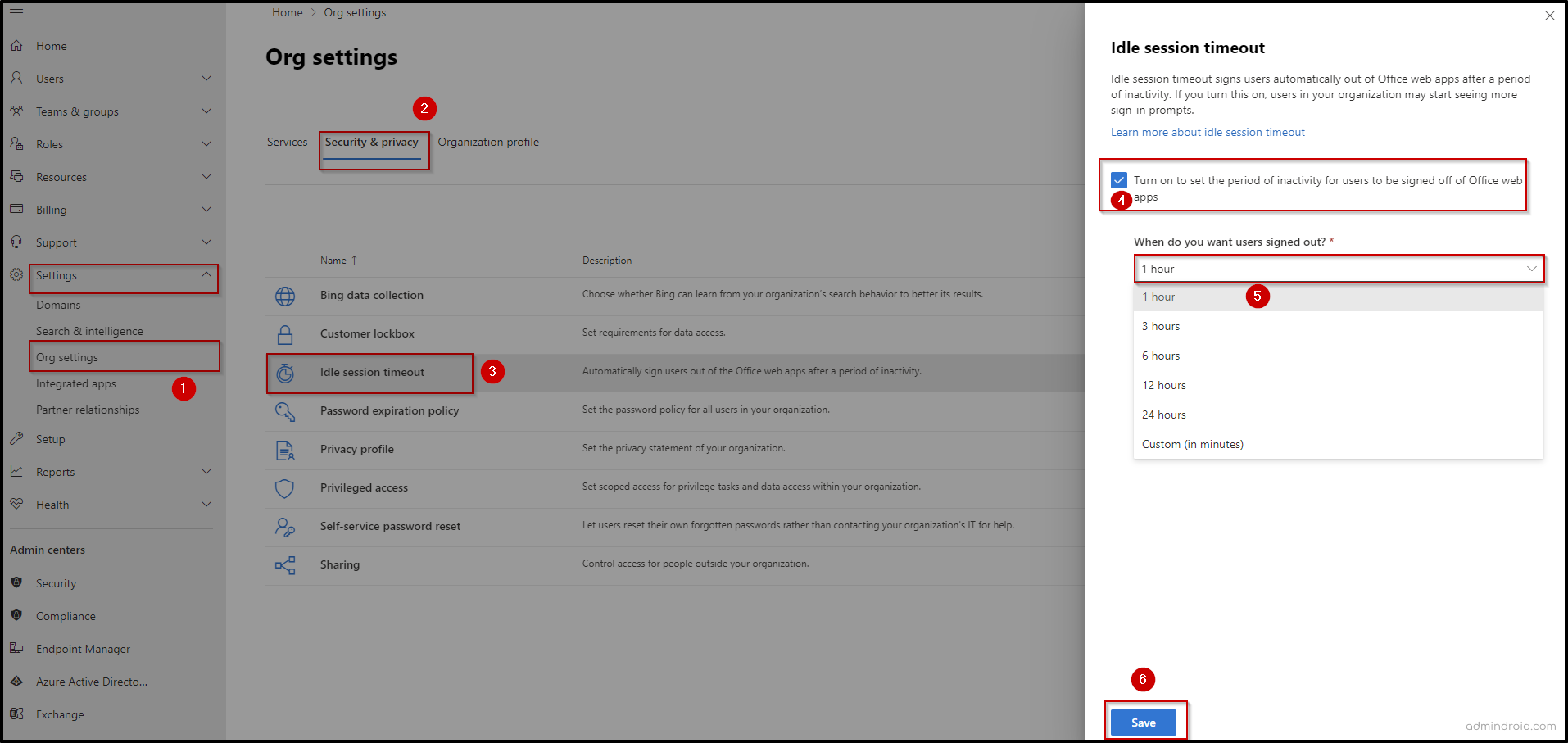
If you want to delete idle session time policy, you can Uncheck Turn on to set the period of inactivity for users to be signed off of Microsoft 365 web apps and select Save.
Trigger Idle Session Time on Unmanaged Devices Using Condition Access Policy:
Instead of turning on idle session timeout on all devices, you can turn it only on unmanaged devices. To enable idle session timeout setting in an unmanaged device, adding a conditional access policy in the Microsoft Entra admin center is necessary.
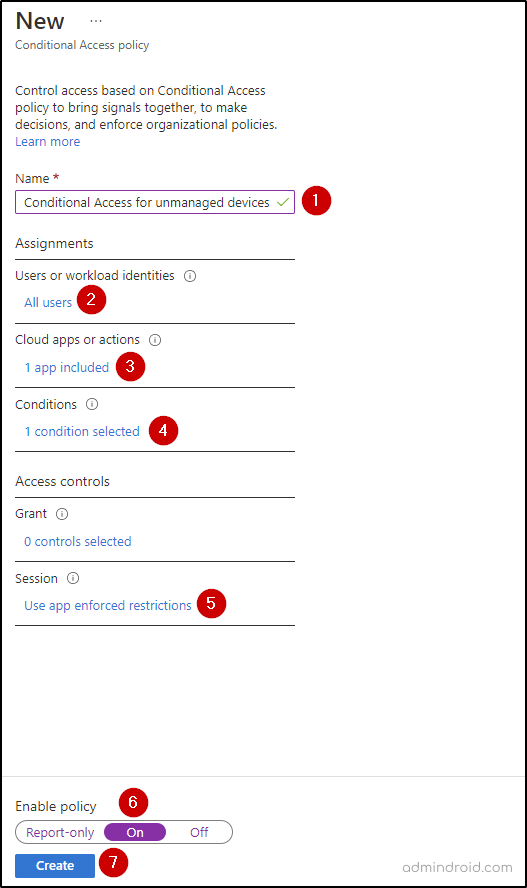
Follow the steps below to turn on idle session time using CA policy in MS Entra:
- Open Microsoft Entra admin center.
- Navigate to Conditional Access –> Policies
- Select New Policy and give a name.
- Choose All Users under Users or workload identities.
- Go to Cloud apps or actions and choose Select apps. Specify Office 365, and then Select.
- Go to Conditions –> Client apps –> Configure to Yes, and then select Done.
- Click Session under Access controls, and pick Use app enforced restrictions, and then Select.
- Enable the policy to On and click Create.
Note – Implementing Idle session timeout on unmanaged devices using CA policy requires Azure AD Premium P1 and P2 subscription.
How to Enable Idle Session Timeout Using PowerShell?
To enable idle-session timeout, firstly you need to connect to SharePoint Online PowerShell.
|
1 |
Connect-SPOService -Url https://<Tenant>-admin.sharepoint.com/ |
To configure idle-session timeout in Microsoft 365 run the following command,
|
1 |
Set-SPOBrowserIdleSignOut -Enabled $true -WarnAfter (New-TimeSpan -Seconds 2700) -SignOutAfter (New-TimeSpan -Seconds 3600) |
By running this cmdlet, you can enable the idle session timeout that warn users after 45 minutes of inactivity, and automatically sign them out if there’s no activity within the subsequent 15 minutes.
Here, the ‘-WarnAfter (New-TimeSpan –Seconds 2700)’ parameter specifies the duration of inactivity (idle time) after which a warning should be displayed to the user.
Whereas the ‘-SignOutAfter (New-TimeSpan –Seconds 3600)’ parameter specifies the duration of inactivity after which the user will be automatically signed out.
The durations can be adjusted based on the organization’s security and user requirements.
Other Things to Keep in Mind About Microsoft 365 Idle Session Timeout
- The idle session timeout setting configured in Microsoft 365 admin center overrides the existing Outlook web app and SharePoint Online policies.
- When third-party cookies are disabled in the browser, idle session timeout is not supported.
- Users will get signed out only if they are inactive in all Microsoft 365 web apps for the configured duration.
- Idle session timeout can’t be scoped to specific users, groups, or organization units.
- The idle session timeout setting is not yet available for Microsoft 365 operated by 21Vianet or Microsoft Germany.
- While the above approach helps configure idle session timeout for M365 services, you must separately set up session timeout for the Entra portal to secure access.
As seen earlier, implementing an idle session timeout feature exclusively for unmanaged devices requires a conditional access policy. CA policies allow organizations to define specific access rules and controls based on various conditions, such as users, groups, device type, location, etc. Speaking of CA policies, it reminds AdminDroid, which offers a comprehensive suite of reports dedicated to valuable insights and empowers organizations with unparalleled visibility & control of CA policies. 🕒📈
Get Access to a Robust Suite of CA Policies Reports by AdminDroid
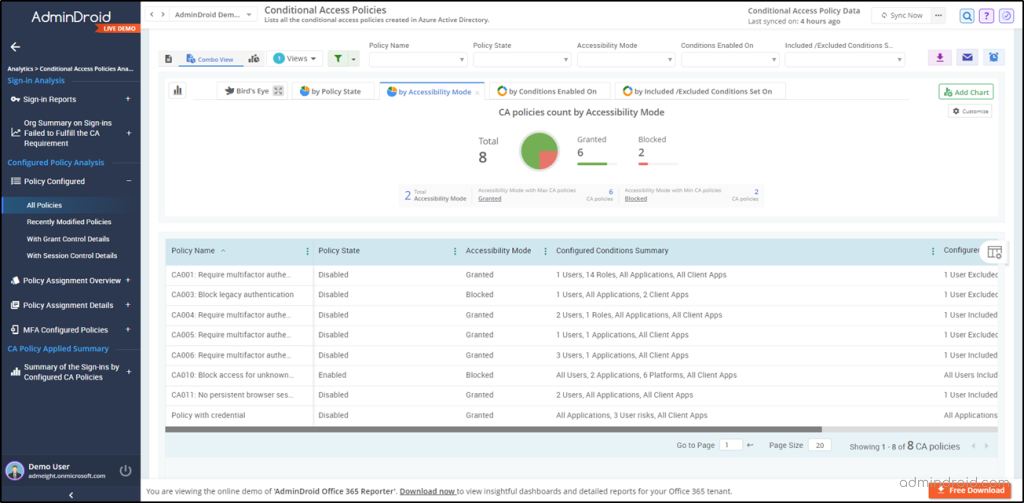
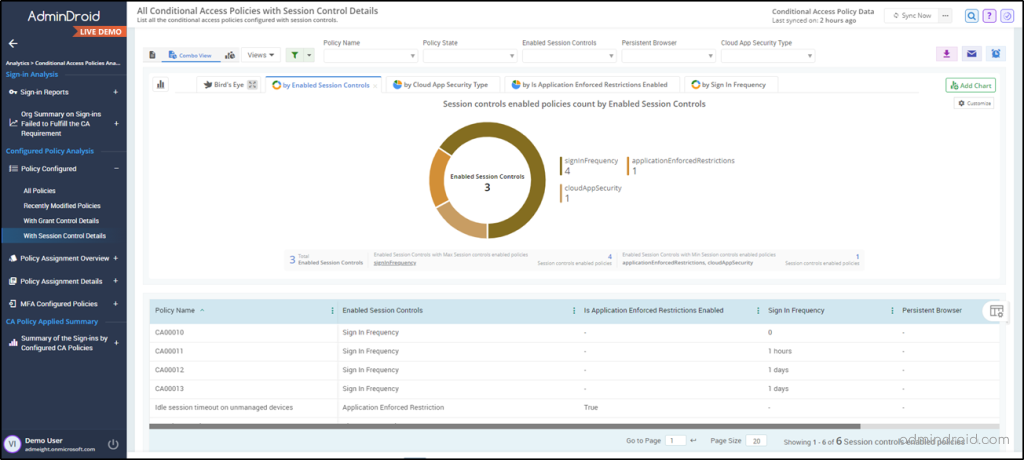
Here’s a list of a few reports offered by AdminDroid on Conditional Access policies.
- All CA policy configurations
- CA policies with grant/session control details
- Overall sign-ins by configured CA policies
- Successful sign-in summary that passed CA policy
- Sign-ins blocked through Conditional Access
- Org-wide summary on CA based sign-in failures
- Guest/External user conditions on CA policies
- CA policies with MFA grant controls
- MFA enabled CA policies – condition details
- MFA excluded users based on CA policies
Simplify Your Administrative Tasks with AdminDroid
AdminDroid goes beyond traditional reporting tools by offering Microsoft 365 alerting, scheduling reports, customizing with advanced filters, Microsoft 365 delegation, exporting data, and allowing admins to delve deep to extract valuable insights. In addition to this, admins will be amazed by 30+ visually appealing Microsoft 365 dashboards. It will provide a holistic view of the organization’s ecosystem and actionable insights that will leave you amazed.
AdminDroid offers admins the ability to seize control and effortlessly manage every facet of the Microsoft 365 services, from Azure AD to Power BI and beyond. Discover a vast collection of meticulously crafted 1800+ reports to provide unparalleled depth and precision, addressing every management need.
I hope this blog has covered everything you want to know about the ‘Idle Session Timeout’ setting. If there are any queries, feel free to reach us through social media. We would be glad to assist you!