Managing multi-factor authentication (MFA) for Microsoft 365 is already a frustrating, mind-boggling task. To make matters worse, the legacy MFA and SSPR policies are incredibly tedious to manage. You have to manage MFA in one place and password resets in another, constantly switching tabs! 😫
- 2022: That’s when Microsoft announced Authentication method policies in Entra ID, bringing everything under one roof for user MFA management.
- 2023: Microsoft urged a transition from MFA and SSPR policies to Authentication method policies, citing that legacy settings would be deprecated on September 30, 2024.
- 2023 – Second Half: Microsoft extended this retirement date by a year. So, legacy MFA & SSPR settings will be retired on September 30, 2025.
Given this looming deadline and the need for flexibility, many Microsoft 365 admins began migrating to the new authentication method policies.
But here is where the problem arose! 🚨Manual migration was so challenging & time-consuming, leading to numerous complications. Fortunately, Microsoft has recently brought the capability to automate the legacy MFA migration process. Let us take a closer look at what this entails.
Why Migrate to Authentication Method Policies?
- Managing authentication methods in legacy MFA and SSPR policies was a fragmented process. MFA required digging into per-user MFA service settings, while SSPR had its own configuration tucked away in the ‘User Properties’ page.
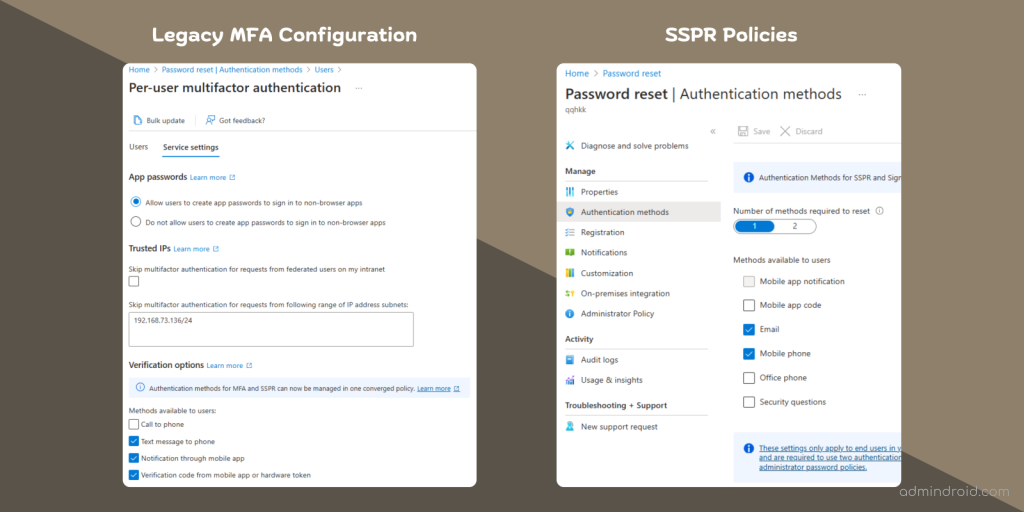
Dealing with two different policies is already challenging, but the other biggest drawback is its rigid nature.
- The two services operate at the tenant level, so you can’t customize MFA methods for different users. This lack of flexibility hindered organizations from tailoring their security policies to specific users or groups.
So, with all these complications, migrating from legacy MFA to Authentication methods policies can tighten your Microsoft 365 security and streamline your work.
What are Authentication Method Policies in Entra ID?
Authentication method policies in Entra ID centralize Authentication management under one umbrella by providing a consistent and streamlined framework.
- These policies allow administrators to configure and scope authentication methods specifically for different users and groups.
- Additionally, most methods come with configurable parameters, which allows for precise control over their usage.
For example, when you enable passwordless authentication with Microsoft Authenticator, you can add settings that show the geographic location or the app name they are logging into. These contextual details reduce the chances of accidentally approving an MFA request.
Overall, Authentication method policies promise greater flexibility and security, especially for admins balancing multiple policies. 💯
Manual vs. Automated Migration: What’s the Difference?
While manually configuring settings gives you the assurance that everything is set up by you, it can negatively impact various factors! So, why choose manual when you can go automated? Here’s a quick side-by-side comparison:
| Aspect | Manual Migration | Automated Migration |
| Process | Step-by-step for each setting. Admins must manually note down MFA and SSPR settings and align them with the new Authentication method policies. | Wizard-driven, bulk migration. This wizard scans your current setup and replicates settings under the new framework in just a few clicks. |
| Time Required | Longer, depends on user volume | Fast, regardless of environment size. |
| Error Potential | Higher risk of missing configurations | Lower, as the wizard catches all existing settings. |
| Best For | Small or highly customized setups. | Large environments or standard configurations. |
Overall, automated migration offers significant advantages in speed, accuracy, and ease of use.
How to Automatically Migrate from Legacy MFA & SSPR to Authentication Method Policies?
Now that we’ve seen the benefits of automated migration over manual processes, it’s clear that transitioning your policies automatically is both efficient and user-friendly! Here’s how to kick off your automatic migration:
- Open the Microsoft Entra admin center and select the Authentication methods from the ‘Protection’ dropdown.
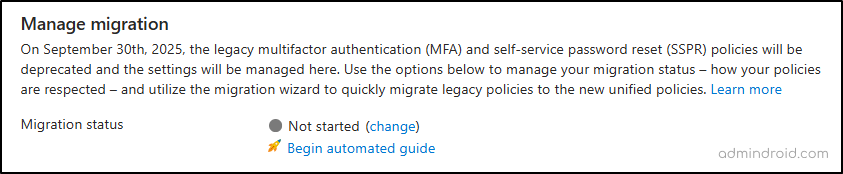
- Look for the Manage migration section, which displays your current migration status and provides an authentication methods migration guide for your reference.
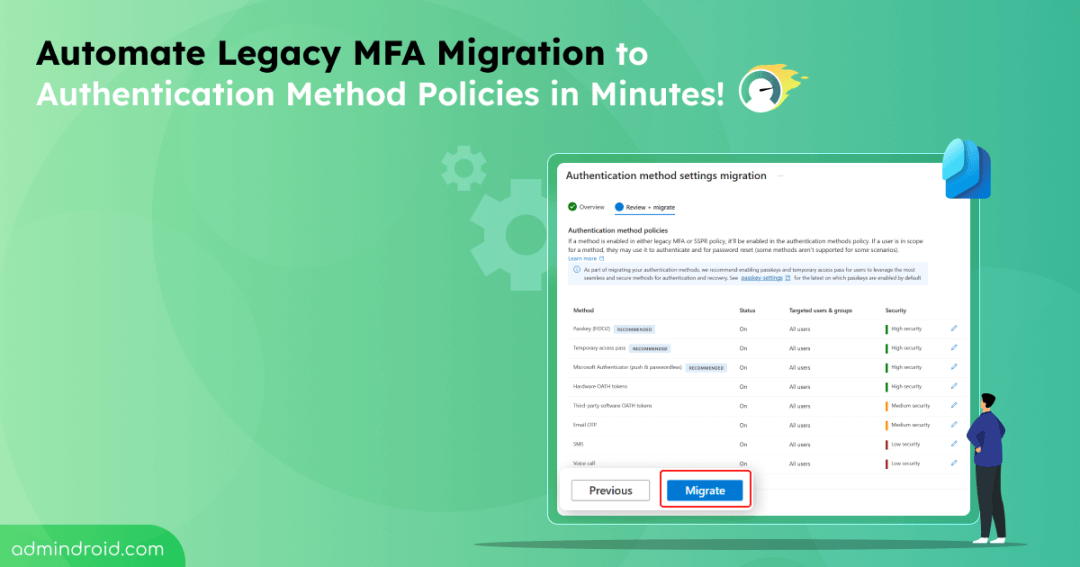
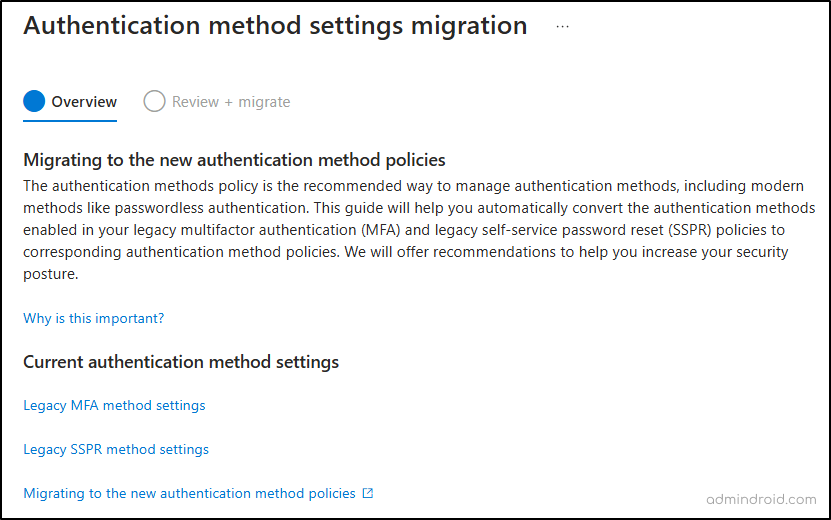
3. Click on the Begin automated guide. A new page will appear, explaining the migration process and showing the current status of your Legacy MFA and SSPR settings. Review it once!
4. Click ‘Next’ to proceed. Here, your legacy settings are automatically mapped to the appropriate Authentication method policy. You can review and modify these mappings as needed.
Tip: If you were using manual migration, you would need to manually audit your current policy settings for MFA and SSPR. So, to rightly map the legacy settings, refer to the provided documentation on the three different cases in the MFA update process.
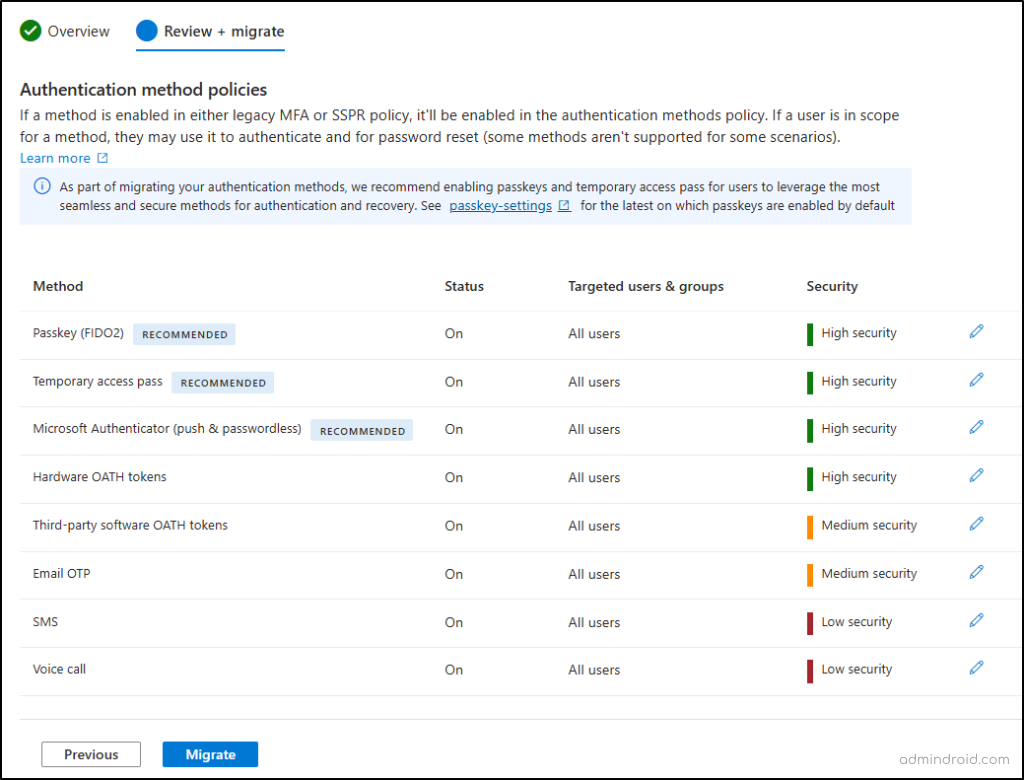
5. Before confirming, review the migration summary. If you wish to modify any mapped configurations, click ‘Edit’ (pencil icon) next to each method to make your updates.
6. Once everything looks good, select the ‘Migration’ button. The wizard will manage the process in the background and the status will update to ‘Migration complete’.
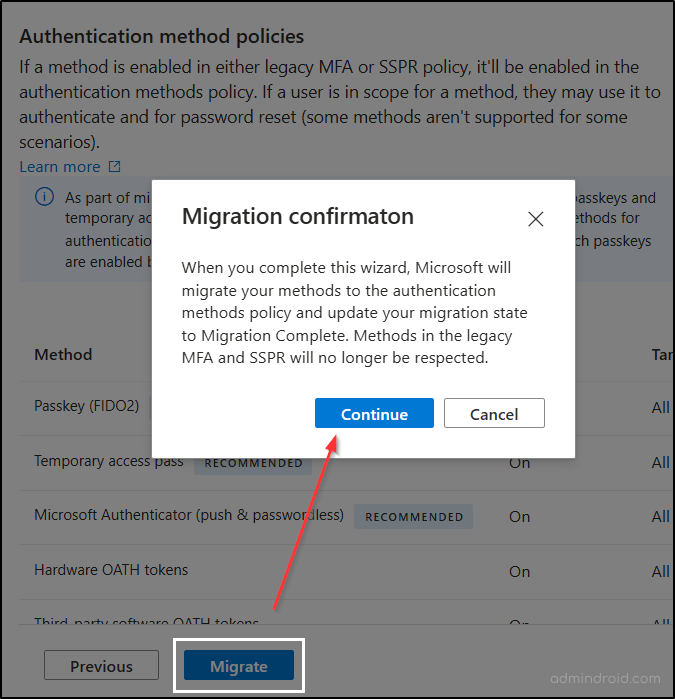
And that’s it! Once the migration is finished, your organization is up to the modern standard, secure, and ready to go! 💯
You’ve Got This!
Migrating to Authentication method policies in Entra ID is the way forward that makes MFA management more cohesive and secure. If you have not tried automatic migration yet, now is the perfect time to explore how it can simplify your work.
P.S. For those who prefer a hands-on approach, manual migration is still an option. But what’s a better way to discover the power of automation than to give it a try? 😉
If you have any questions, comment below, and we will be glad to sort it out for you.