Day 4 of the Entra Suite Camp highlighted how Entra Suite helps administrators gain visibility and control over web activity within the organization. It also featured demo sessions introducing new capabilities to manage access to GenAI tools, detect shadow AI usage and defend against web-based threats.
If you missed any sessions, here’s a quick recap:
Day 1: Unify access with Microsoft Entra Suite
Day 2: Ensure least privilege access with Entra Suite
Day 3: Secure access to on-premises apps with Entra Suite
Now let’s dive into what was covered in Day 4.
What fuels your workforce can also compromise it — the internet! It is now the most used, yet least protected part of your stack. According to the Microsoft 2024 trend index, 75% of users are using GenAI tools and web-based services in their work. That’s not surprising anymore, we’ve all started using them in one way or another. But the actual problem lies in the lack of visibility and control over how users interact with the internet.
Here is where the Microsoft Entra Internet Access comes in to fill the gap.
Microsoft Entra Internet Access – Securely Access Anything, Anywhere
To start with the basics, Global Secure Access is Microsoft’s Secure Service Edge (SSE) solution designed to enforce secure access across your network, identities, and endpoints. It includes two key products: Microsoft Entra Internet Access and Microsoft Entra Private Access.
In this, Microsoft Entra Internet Access is your go-to solution for secure access to Saas and GenAI tools.
Microsoft Entra Internet Access is a secure web gateway that ensures safe access to public internet resources. It helps organizations simplify access decisions by combining identity-based controls with network-level security.
Let’s see the innovative Entra Internet features that help you monitor and control internet access.
Block Usage of Unauthorized GenAI Tools with Web Content Filtering
Web content filtering in Entra Internet Access lets you apply granular access control based on web categories and FQDNs (Fully Qualified Domain Names).
Let’s say the Marketing team in your organization shouldn’t be allowed to access Deepseek.com, but they can use approved tools like ChatGPT, only for a limited duration. Here’s how to implement it:
Step 1: Create web content filtering to block unauthorized GenAI
Let’s first set the web content filtering policy to block Deepseek.com. You can refer to the create web content filtering policies blog to set the configurations below.
- Configure FQDN as deepseek.com in the web content filtering policy.
- Set the action to “Block.”
- Link this policy to a security profile created for the Marketing Team.
Step 2: Allow approved GenAI tools with time-based access
Now, let’s allow the Marketing team to use ChatGPT, but only for a limited time. Just-in-Time access to GenAI apps can be done using a combination of web content filtering and access packages.
Here’s the process:
- Create a web content filtering policy that allows chatGPT.
- Link this policy to the same security profile used for the Marketing team.
- Next step is to create an access package. You can refer to the create access packages blog to set the following configurations:
- Grants access to a group (e.g., AllowForChatGpt) for a specific duration (e.g., 6 hours).
- Set “Marketing team” members as eligible to request access.
- Requires approval before granting access.
Once approved, members will be added to the AllowForChatGpt group, giving them temporary access to ChatGPT.
Step 3: Combine the Security Profile with the Conditional Access
To make the policy context-aware, use Conditional Access:
- Target the policy to AllowforChatGpt group and marketing team.
- Apply the associated security profile within the Conditional Access rule.
End-user experience:
- When Clara from the marketing team tries to access Deepseek.com, she sees a block message based on the policy.
- To use ChatGPT instead, she can request an access package.
- Once approved, she gets access for 6 hours only, as defined in the policy.
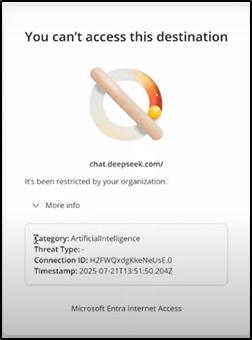
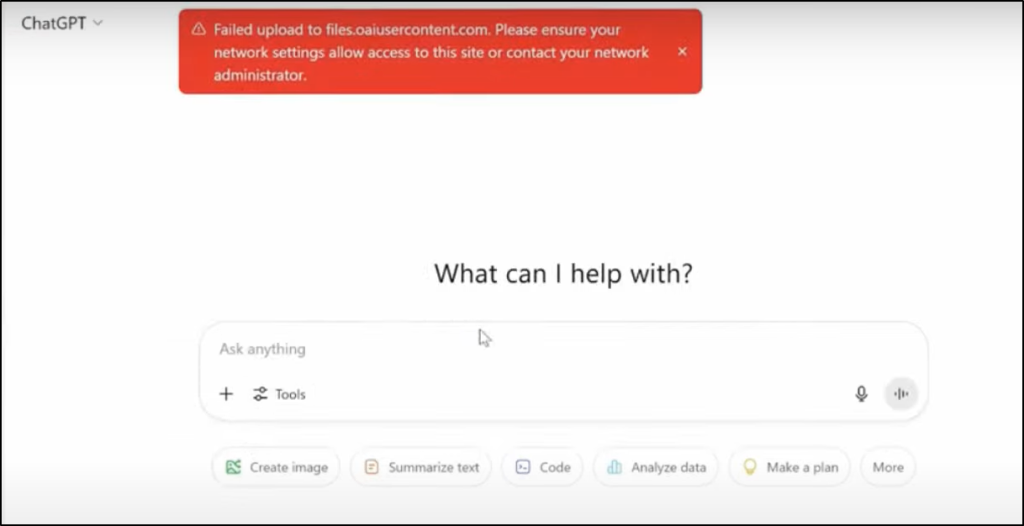
Now, let’s take it a step further. Clara has access to ChatGPT. But what if she tries to upload a sensitive file into it? How do you prevent that? This is exactly where the new feature comes in – Netskope One Advanced SSE.
Prevent Uploading Sensitive Data to GenAI with Netskope One Advanced SSE
GenAI tools are widely used now, but the risk is that users might unknowingly upload sensitive data or access unsanctioned sites. These tools can also be misused to generate phishing emails or create polymorphic malware. The challenge is that admins often don’t have enough visibility or control over these actions.
To address this, Netskope One Advanced SSE is now integrated with Microsoft Entra Internet Access. This integration brings inline Data Loss Prevention (DLP) and Advanced Threat Protection across all web sessions.
With this setup, admins can:
- Use custom DLP policies created in the Entra admin center. For example, you can define a policy to detect when someone uploads files patterns like credit card numbers and block the action instantly.
- You can combine DLP policies with Conditional Access to enforce them on specific users or groups, providing greater granularity.
😎So even if Clara is allowed to use ChatGPT, these controls make sure she can’t upload sensitive information like financial data, preventing data exfiltration. We are working on a detailed blog that will guide you how to prevent users from uploading sensitive content to ChatGPT. Stay tuned!
Update: We’ve published a step-by-step guide on preventing sensitive file uploads to ChatGPT, feel free to explore it for more practical insights!
Block Malicious Destinations with Threat Intelligence Filtering
We’re seeing a rise in malicious domains nowadays—many of them host phishing links, malware downloads, or are used for crypto mining. These domains don’t stay up for long, but even a short window is enough to cause serious damage. That’s where Threat Intelligence Filtering comes in.
This feature uses Microsoft’s vast threat intelligence, combining both first-party data (collected by Microsoft’s global security teams) and trusted third-party threat feeds. This layered approach gives broader and more up-to-date coverage of known threats. It can evaluate up to 1 million indicators in real time.
- As users try to access websites, Threat Intelligence Filtering checks the URLs against this threat data. If anything malicious is detected, access is blocked instantly, stopping the threat before it reaches the user.
You can also refer to this Microsoft documentation to learn more about Threat Intelligence Filtering.
In addition to the above features, admins can also make use of the TLS inspection feature within Microsoft Entra Internet Access. Transport Layer Security inspection allows Entra Internet Access to decrypt and inspect HTTPS (TLS-encrypted) traffic. This process helps identify malicious content, enforce compliance, and apply access controls even to encrypted traffic.
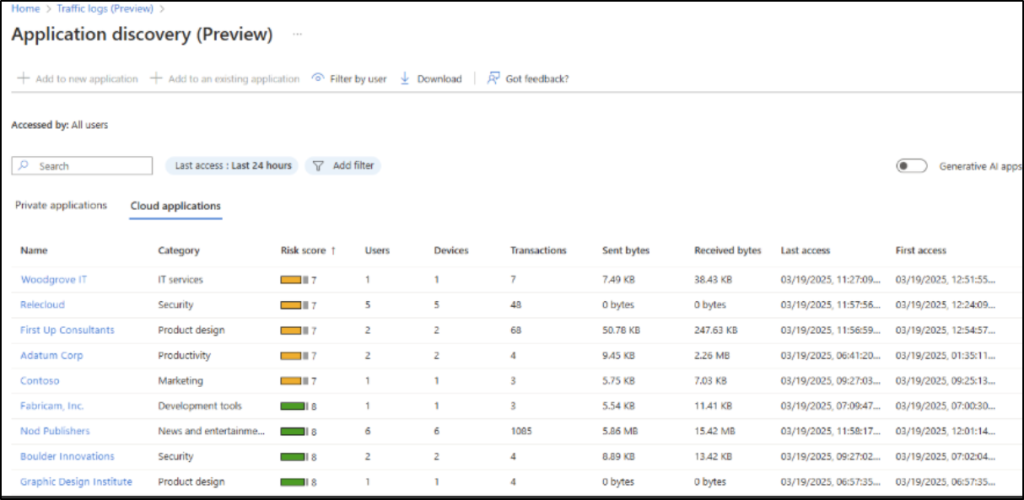
Analyse the Usage of GenAI Apps Using Application Discovery
Many users are already using GenAI tools without any IT approval. This opens up security risks, compliance gaps, and even chances of data exfiltration. To address this, Microsoft Internet Access now includes the “Application Insights and Analytics” dashboard. This gives you visibility into how GenAI tools and other cloud apps are being used across your organization.
With these application insights and risk scores, you can take immediate action, like allowing or blocking specific Gen AI apps, or configuring just-in-time access to provide secure access to applications.
That’s a wrap on the final day of the Entra Suite Camp! We hope you’ve learned a lot throughout the sessions, from key features to how Entra Suite enhances security, governance, and identity management. Thanks for reading!