Privileged Identity Management (PIM) for groups plays a crucial role in safeguarding your organization’s critical assets with its just-in-time access and continuous monitoring. However, challenges arise when resources and sensitive data are at risk due to non-compliant devices, users from unknown locations, etc. So, how can PIM be configured to better address these vulnerabilities?
That’s where the Conditional Access Policies in Privileged Identity Management for groups become your security stronghold. Let’s explore the concept in detail.
Conditional Access in Privileged Identity Management
The integration of Conditional Access authentication context with PIM empowers you to implement precise policies for sensitive data and actions, extending beyond app-level regulations. You can apply CA policies to three components of PIM, including Microsoft Entra roles, Azure resources, and PIM for groups. By combining PIM and CA policies, you can set specific requirements for activating PIM roles, such as,
- Enforcing strong authentication methods.
- Requiring compliant devices for PIM role activations.
- Validation of user locations through GPS-based named locations.
- Blocking role activations for risky users via Microsoft Entra ID Protection.
PIM role activation can also use external authentication methods to meet MFA requirements. Now, let’s explore the steps involved in the integration of Conditional Access with PIM for groups.
How to Apply Conditional Access in Privileged Identity Management for Groups?
To integrate a Conditional Access policy with Privileged Identity Management, follow the three simple steps given below.
- Configure authentication context for Privileged Identity Management
- Configure CA policy for PIM activation in Microsoft Entra
- Integration of Conditional Access with Privileged Identity Management
Configure Authentication Context for Privileged Identity Management
Organizations can effectively label specific resources requiring protection using Conditional Access authentication context. Access to these labeled resources is then granted or restricted based on predefined conditions, providing a robust and adaptable security framework.
Let’s see how to configure the authentication context for Privileged Identity Management.
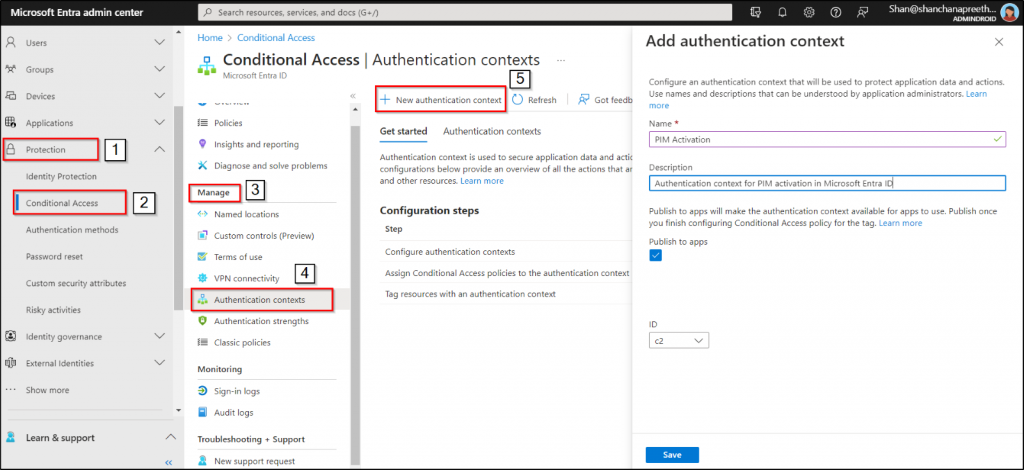
- Navigate to the Microsoft Entra admin center and select “Identity.”
- Under “Protection”, choose “Conditional Access.”
- Within the “Manage” section, locate and click on the “Authentication contexts.”
- Click on “New authentication context.”
- Enter a suitable name and description for your authentication context.
- Tick the “Publish to apps” checkbox.
- Click “Save.”
Create a CA Policy for PIM Activation in Microsoft Entra
After setting up the authentication context, the next step is to create a Conditional Access policy for Privileged Identity Management in groups. Let’s now explore the process of creating a Conditional Access policy to target the authentication context created in the previous step.
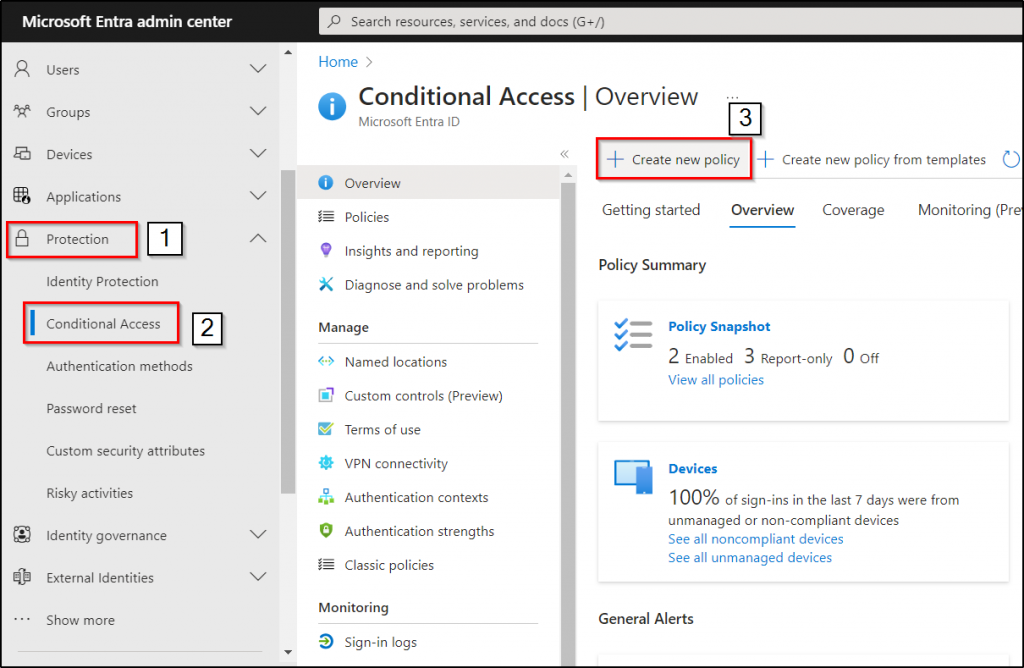
- Navigate to the Microsoft Entra admin center and select ‘Identity’.
- From the “Protection” dropdown, choose “Conditional Access.”
- Select “+Create new policy” and provide an identifiable name for your policy.
- In the Assignments section, choose “Users.”
- Under the “Include” category, select users based on your organizational setup.
- For the “Exclude” option, choose “Users and groups” and specify your organization’s emergency access or break glass accounts.
- Navigate to “Target resources.”
- Choose Authentication context with the ‘Select what this policy applies to’ section. Here, we have chosen the ‘PIM Activation authentication context’ that we created earlier.
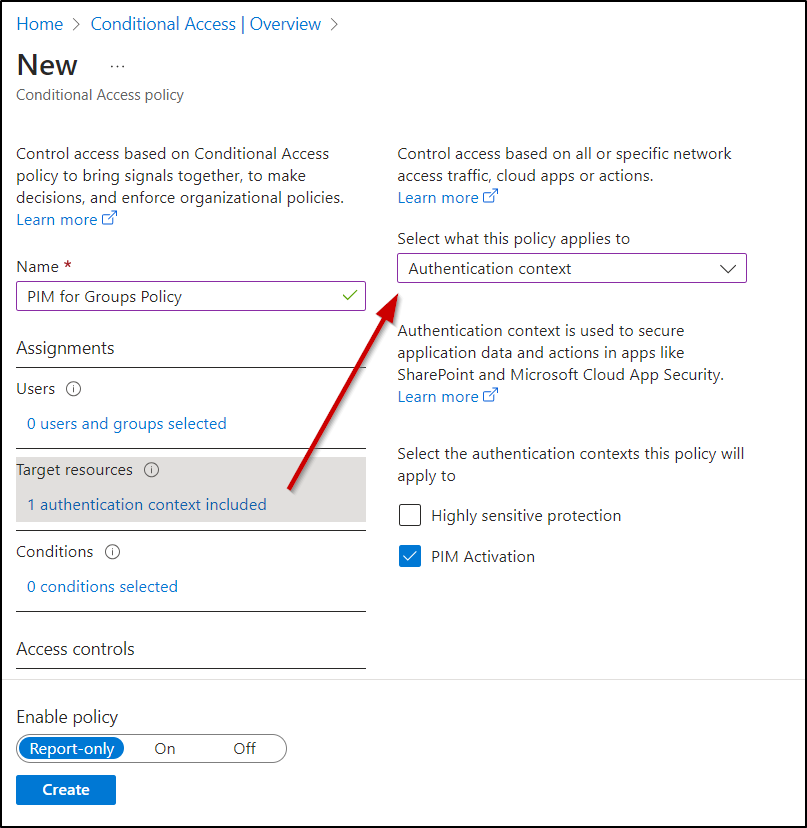
- In the “Access controls” section, choose your desired conditions under the “Grant” option. In our case, we have chosen ‘Require authentication strength.’
Requiring authentication strength to obtain PIM group membership enables the use of robust methods such as phishing-resistant MFA and Passwordless MFA, which offer greater security compared to basic MFA methods like SMS.

- Enable the “Report-only” mode under the Enable policy option.
- Click “Save” to apply the policy.
Integration of Authentication Context within PIM
The next step is to integrate the created Microsoft Entra Conditional Access authentication context with PIM for groups. To target the security controls within the authentication context through CA policy, simply assign the authentication context to the PIM.
- Navigate to the Microsoft Entra admin center and select “Identity Governance.”
- Click on “Privileged Identity Management” and under “Manage,” select Groups.
- Choose the group you want to include in the Microsoft Entra Conditional Access authentication context.
- From the group page, select “Settings” under “Manage.”
- After selecting a member or owner role, click on “Edit” to edit the role settings.
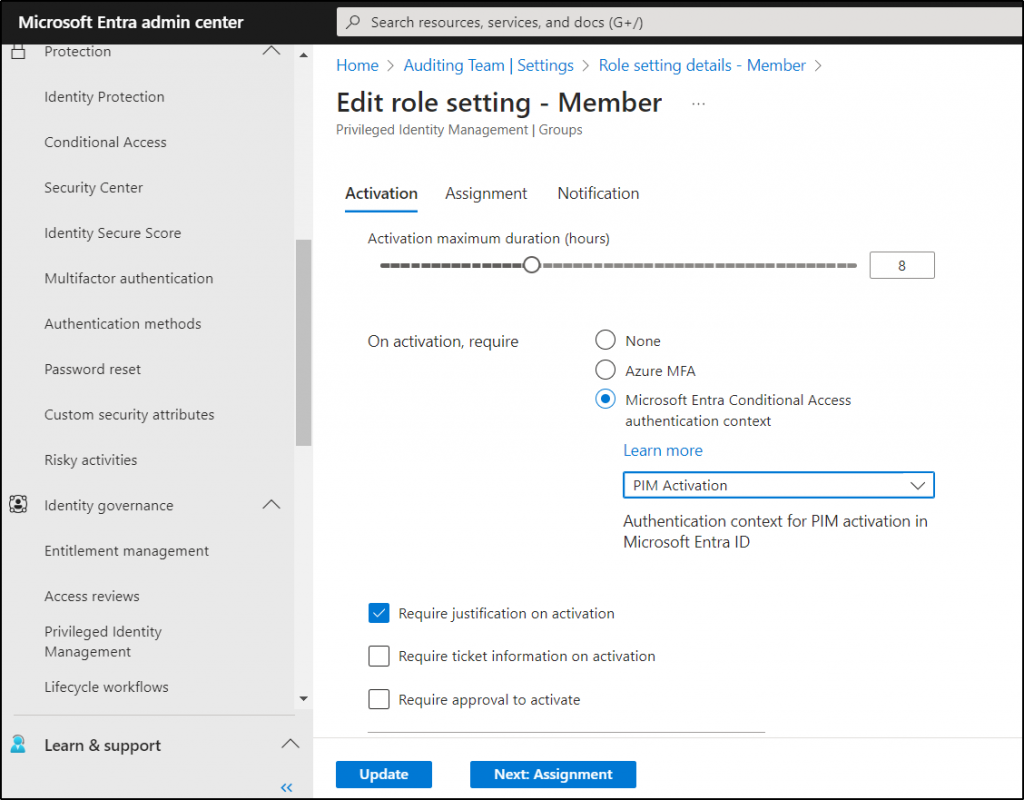
- Under the Activation tab, locate “On activation, require Microsoft Entra Conditional Access authentication context.”
- Choose the authentication context you just created from the drop-down.
- Finally, click “Update” to apply the settings in PIM for groups.
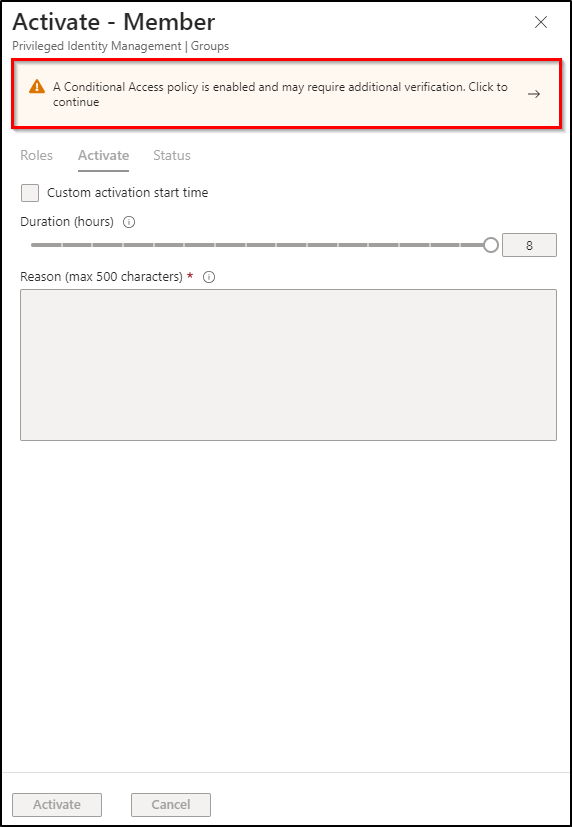
Real-Time Testing of Conditional Access in Privileged Identity Management for Groups
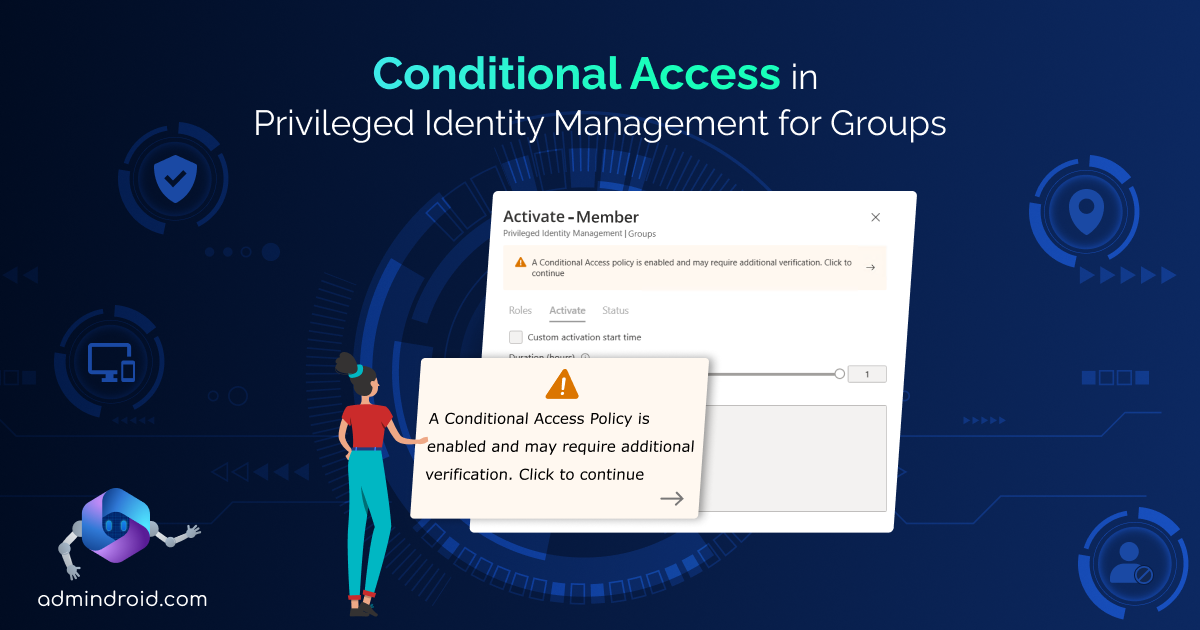
Testing the implementation of a Conditional Access policy in PIM for Groups can be done during the activation of PIM roles. If a Conditional Access policy is enabled, you may encounter the following error message indicating the need for additional verifications.
“A Conditional Access policy is enabled and may require additional verification.”
Benefits of Combining Conditional Access with PIM
Implementing CA policies in PIM for groups offers several key benefits:
- Robust Security Framework: The combination of Microsoft Entra PIM with authentication context creates a robust security framework for privileged identities within organizations.
- User Access Evaluation: You can use Conditional Access authentication context when a user seeks access to a privileged role or resource. It assesses whether the user fulfills the security requirements for that role and grants just-in-time access.
- Enhanced Monitoring and Tracking: Authentication context enables organizations to monitor and track user access to privileged roles or resources. This heightened visibility provides valuable insights into potential security threats and ensures compliance.
Conclusion:
In summary, Conditional Access policies for PIM offer a robust Microsoft 365 security framework for groups. You can also customize the CA policies as per your needs to enhance the PIM group security. In addition, you can create access reviews for PIM groups to ensure that only authorized users maintain ongoing access and promptly eliminate unauthorized ones.
We hope this blog has simplified the process of integrating Conditional Access policies in Privileged Identity Management for groups. Feel free to share your thoughts and questions in the comments section.