On Day 4 of Cybersecurity awareness month, learn to conceal your organization from cyber threats today. Stay tuned for more blogs in the Cybersecurity blog series.
A sudden hindrance during work affects our productivity! Think of a past incident caused by the MFA outage that caused Microsoft 365 users to face logging-in issues. Admins were most affected during the incident. What if the same happens in the future? And that’s why an emergency account with a different MFA authentication method is required!
“We are never more in danger than when we think ourselves most secure, nor in reality more secure than when we seem to be most in danger.”
~ William Cowper
What is a Break Glass Account in Microsoft 365?
Always being prepared is the best practice. So, we need a break glass account to help us with emergency situations. A break glass account is a substitute account for your regular admin account with global admin privilege, used in emergency situations. Generally, it is not suggested to assign a license to a break glass account.
Why Do You Need a Break Glass Account?
Break glass account is your way out of all the below-mentioned situations.
- MFA Outage: When the authentication method used for MFA is in an outage, the users cannot log in to their accounts. Here, such emergency access accounts could be used for Microsoft 365 login purposes.
- Conditional Access Policy Lockout: In case you get locked out of your admin account due to a conditional access policy restriction, a break glass account acts as a backup to regain access and remove the policy.
- Departure of Global Admin: If the organization’s Global admin departs abruptly without transferring critical account information or access details, a break glass account helps regain control & access to essential resources.
- Natural Calamities or Service Outages: In the worst case, due to any natural calamities, all the mobile service can be down, and a break glass account provides a means to access systems.
Microsoft Entra Break Glass Accounts Best Practices – The Do’s & Don’ts:
A break glass account is a highly permissioned account, so access to these accounts must be regulated. You must learn the best practices for break glass accounts to ensure you’re never locked out of your Microsoft 365 tenant.
Do’s
- Create at least two emergency access accounts that are exclusively cloud-based, utilizing the *.onmicrosoft.com domain and operating independently of on-premises systems or federated environments.
- This account must be connected to a cloud to reduce Privilege Identity Management and federation issues.
- The break glass account must be equipped with a complex password that includes the alphabet, symbols, numerals, etc., and secure the password safely.
- This account must be provided with the “Global Admin” privilege.
- Providing an unusual name to the break glass account to keep the account away from password spray attacks. E.g.: Mailtemplate@org.com
- These accounts must be excluded from all conditional access policies to prevent accidental lockouts during critical situations.
Don’ts
- Multi-factor authentication(MFA) can be disabled for a break glass account. (At your own risk)
Point to be considered: Disabling MFA for break glass accounts could expose systems to unauthorized access but may be considered if the complex password is stored securely. Instead of using MFA disabled break-glass accounts, consider setting up a break-glass access application that let you perform the same critical actions like break-glass accounts in emergency situations.
Do We Need to Disable MFA for Break Glass Accounts in Entra ID?
Long story short: Ideally, it is suggested to enable MFA for break glass accounts, but there’s some flexibility based on security setups.
Here are a few things to consider before setting up MFA for emergency access accounts:
- Use a different MFA method for break glass accounts rather than the non-emergency accounts.
- Like, if your regular admin account uses Authenticator, then consider something completely different, like FIDO2 security keys for break glass accounts.
- Because, when implementing a second factor, its dependencies are added to the first factor. For instance, SMS & voice calls as second factors share similar dependencies, increasing vulnerability. However, passwordless authentication holds different dependencies to avoid this issue.
Overall, carefully consider the dependencies of various authentication methods and implement appropriate MFA for break glass accounts to optimize security.
How To Create a Break Glass Account in Microsoft Entra ID?
Creating a break glass account is the same as creating a new user in Azure Active Directory. The difference is the configuration you set for the account. The Previously mentioned Guidelines can be followed to create a user.
- Go to Microsoft Entra admin center.
- Navigate to the “Identity” section and choose “All Users.”
- Select “New user” and opt for “Create a new user.”
- Fill in the necessary details, including username, and notably ensure to set a complex password that is hard to break!
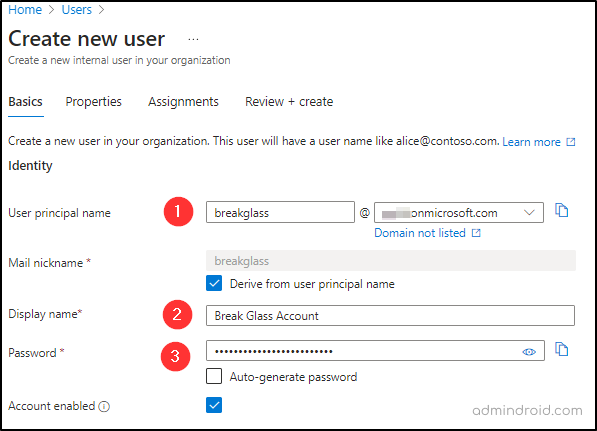
- Proceed by clicking “Next” and input the required properties.
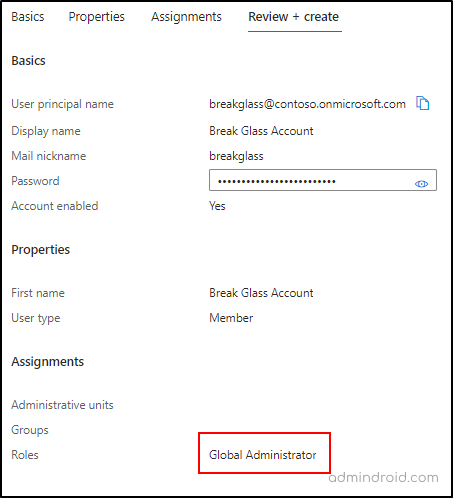
- Move to the “Assignments” page, select “Add role,” and assign the “Global administrator role.”
- Finally, review the details and create the emergency access account.
How To Preserve Emergency Access Accounts?
A break glass account is an account with Global Admin privilege, the user who accesses the account will get entire access to the organization and sensitive data. So, it is important to maintain it in a proper manner. The most effective ways to maintain the break glass account are
- Protect the emergency access account password securely.
- Check Sign-in using audit logs in Entra ID.
- Setting up Login alerts for break glass account sign-ins.
Break Glass Account – How to Securely Store the Passwords?
Setting a strong password for the Break Glass account is not enough; securely storing it also plays a major role! So, how to store it? Here is a list of a few different ways to secure passwords.
1. Only a select group of trusted admins should have access to these emergency passwords.
2. Save the password by segregating the password into two or more pieces and storing it in a fireproof safe place with strict access control & encryption.
3. The third approach can be considered based on the organization’s wish. It is also suggested to go passwordless for break glass accounts and use FIDO2 security keys. These keys should be kept in a highly secure physical space.
4. After any emergency use, always change or update the Break Glass account password for the next use.
By implementing these measures, you can significantly enhance the security of break glass account passwords and reduce the risk of unauthorized access or misuse.
Monitor Break Glass Account Sign-Ins Using Audit Logs:
Being a highly privileged account, it is important to keep an eye on the login activities of the break glass account. Therefore, monitor break glass account sign-in activity in the Audit logs in Entra ID to ensure that they are not being used inappropriately. Follow the below path to monitor Microsoft 365 audit logs activity from the emergency accounts:
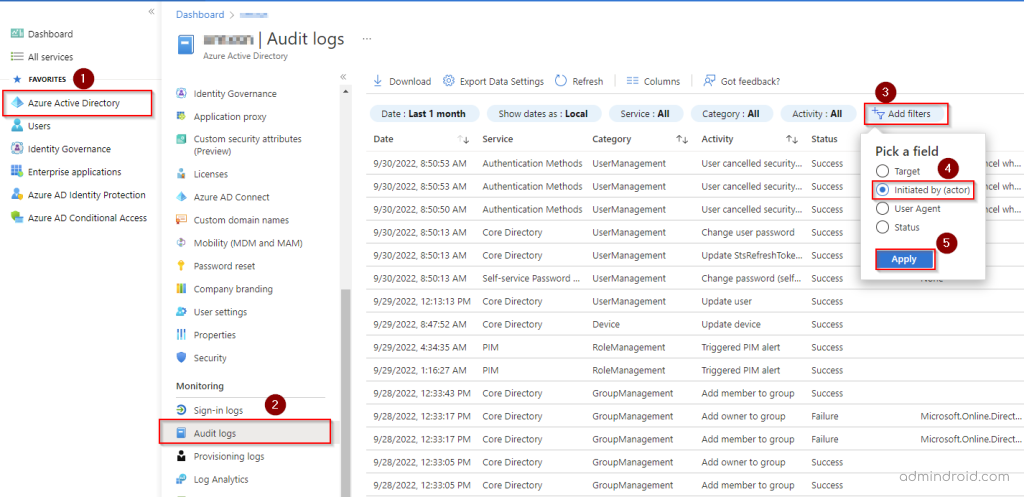
- Go to Microsoft Entra admin center.
- Select Audit Log from the Left pane.
- The audit activities are displayed, click the Add filter and select Initiated by field.
- Then enter the break glass account name and click Apply.
In addition to monitoring break glass account sign-in activity in the Audit logs in Entra ID, admins can also monitor Azure AD break glass accounts with Microsoft Sentinel. This requires an Azure subscription.
How to Set Up Login Alerts for Break Glass Account Sign-ins?
All the time we can’t check on the sign-in activities manually instead, we can set an alert that notifies us whenever a user signs in using the break glass account. To create an alert policy, you can follow the listed steps.
- Go to the Microsoft Defender.
- Click Policies and Rules under the Email & collaboration category.
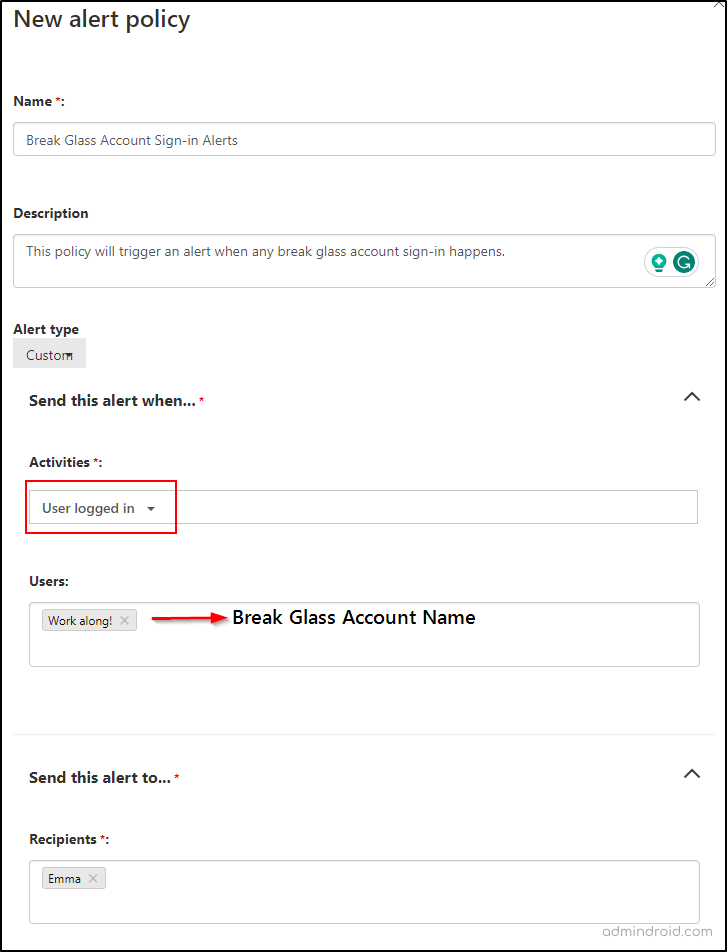
- Navigate to Alert policies.
- Click New Alert Policy, and fill in the required details like Name, Description, Severity, and Category.
- Select “User logged in” under the Activities section and the “break glass account name” under Users.
- Click Save.
Note: Activity alerts in Microsoft 365 are being deprecated, so Microsoft suggests relying on alert policies in Defender.
Unfortunately, these alert policies don’t let you specifically track user logins, which complicates monitoring break glass account usage. While you can create alerts using Azure Log Analytics, it comes with an extra cost through an Azure subscription.
Luckily, using the AdminDroid Microsoft 365 alerting tool, you can create alerts for break glass account sign-ins for FREE. Stay in the loop and keep track of crucial sign-in activities effortlessly!
Unleash AdminDroid’s Powerful Insights for Admin Account Security
Break glass accounts, which possess powerful permissions, require stringent regulations for effective management. While Office 365 audit logs offer valuable insights, their limitations can hinder the comprehensive auditing of critical events. That’s where AdminDroid Microsoft 365 reporter comes into play, offering dedicated reports 📊specifically focused on admin activities!
With AdminDroid, you can stay on top of account changes with dedicated admin dashboards and report boards that offer complete visibility into admin activities and a wide range of Microsoft 365 admin reports including,
- All Global Admins
- Admins with Management Roles
- Admins with Read Access Roles
- Admin Roles by Users
- Administrative Apps
- Admins with Password Never Expire
- Admins without MFA
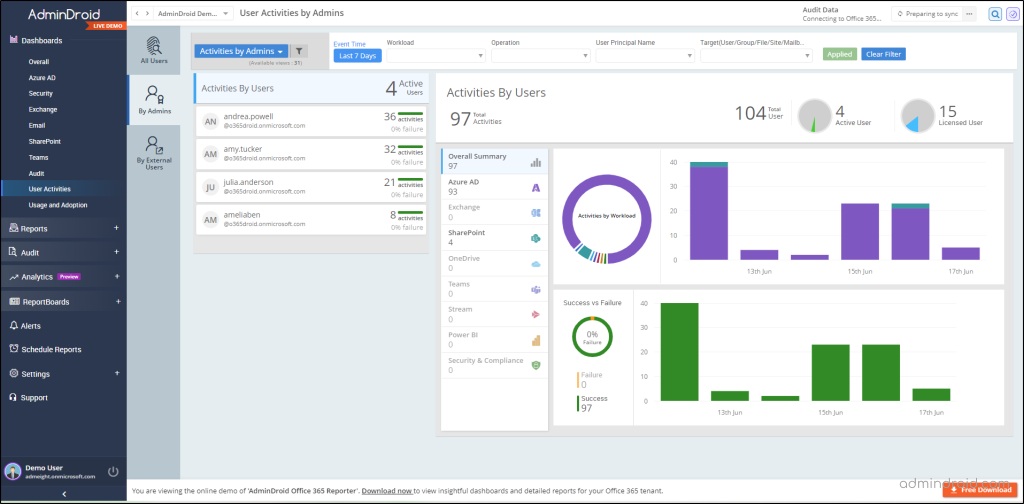
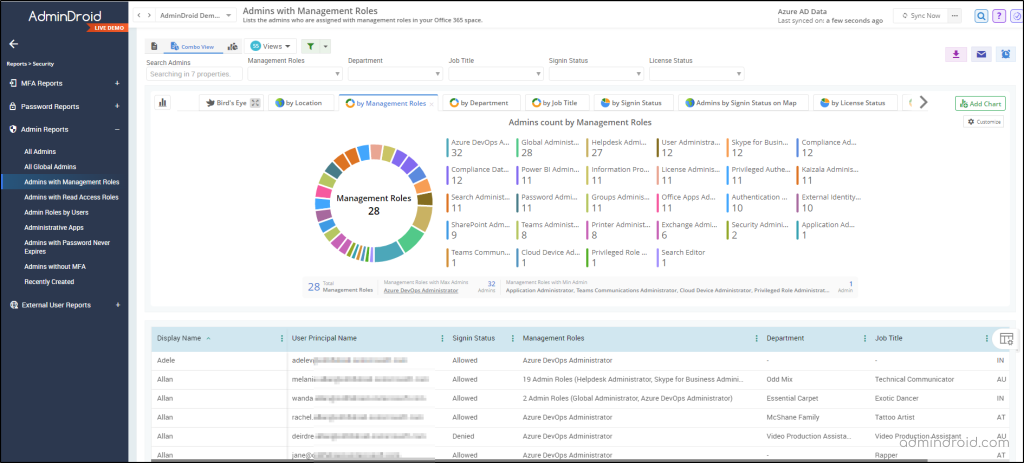
For every Office 365 admin, the AdminDroid Microsoft 365 reporting tool is a must-have solution for effectively monitoring and managing administrative actions. Further, it provides insightful reports on accounts that need to be given special attention in the organization, such as admin role changes, license reports, password reports, group reports, etc.
AdminDroid Azure AD management tool offers over 190 insightful reports for administrative activities. But that’s not all – this platform also offers more than 1800 all-inclusive reports and over 30 dashboards for a variety of other Office 365 services, including Exchange Online, Microsoft Teams, OneDrive for Business, and more.
Don’t wait any longer! Download AdminDroid today and enjoy seamless Office 365 monitoring.
In general, a break glass account is an emergency entrance to your organization that provides you with all the admin access. Hope we have fulfilled your requirements regarding the break glass accounts. If you have any further queries, feel free to reach us through social media. We would be glad to assist you!






