On Day 7 of Cybersecurity awareness month, learn to conceal your organization by implementing strong authentication methods. Stay tuned for more blogs in Office 365 Cybersecurity blog series.

Do you think setting up complex passwords will help you? Nah! Password complexity alone is not sufficient to make passwords secure. Thus, configuring MFA with a strong authentication method is the only way to secure your Office 365 accounts. So, we are back to the grind of discovering new hidden MFA security configurations and implementing stronger authentication!
Microsoft released grant control and authentication strengths in conditional access policies.
Multiple-case implementation in CA policies is now possible! Specifically disabling weaker MFA authentication methods like SMS and categorizing MFA authentication methods based on the user category. Confused about what am I saying? Don’t worry, though! Without further ado, let’s get deeper into how to implement authentication strength in your organization.
“Conditional Access Authentication Strength” Setting:
As Microsoft mandates MFA for accessing portals like Entra, Intune, and Azure, you can prepare for these changes by configuring strong authentication methods like phishing-resistant MFA for all users. Are you wondering where this can be found? You can navigate to the path below to find the newly released “require authentication strength” checkbox:
Azure AD Admin Center → Azure Active Directory → Security (Under Manage Tab) → Conditional Access.
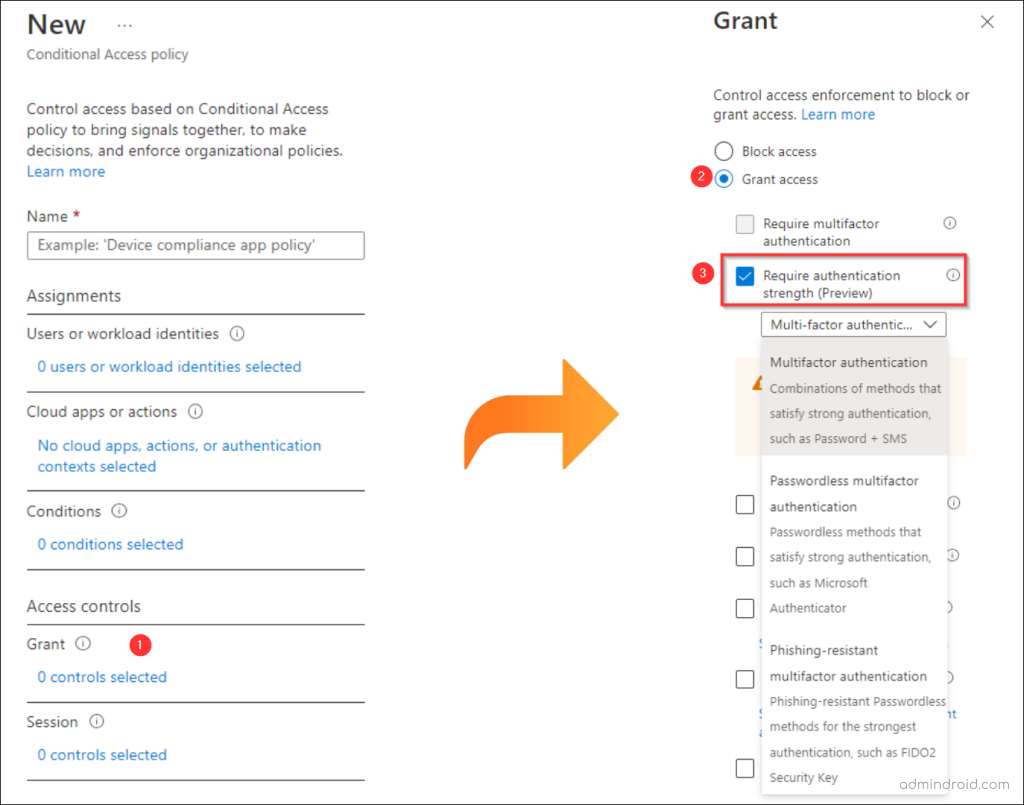
That’s it! Now, you can proceed to create a new conditional access policy. As you create the policy, you will notice a newly added grant control that requires authentication strength.
Note: It’s official! Starting in June 2023, this feature was out in general availability. Also, make sure to have an Azure AD Premium P1 license or Microsoft 365 Business Premium license to access conditional access policies.
What’s the Purpose of Grant Controls in Conditional Access Policies?
For every lock, there is someone out there trying to pick it or break in.
– David Bernstein
🚨Don’t let your MFAs get broken! While playing out with this new grant control in preview mode, I noticed some of its use cases.
One of them is disabling weaker MFA authentication methods like SMS.
While SMS authentication methods can be disabled in numerous ways, there is no clearer way to exclude SMS as an MFA factor for specific groups. And now the solution is here! As the name suggests, the users can require stronger authentication methods, like passwordless multi-factor authentication or security keys.
Secondly, require different authentication methods for different circumstances.
For example, Responsibilities in your organization may range from basic-level workers (contingent staff) to design teams, development teams, highly privileged accounts, etc. Although requiring similar levels of authentication for all users is relatively straightforward, it’s not always necessary!
For instance, it might not be essential to deploy FIDO2 security keys for contingent staff.
So, the only issue is that implementing different MFA techniques for different users might take a long time. Previously, conditional access policies merely required “multi-factor authentication.” Therefore, the MFA method cannot be differentiated.
But, hereafter, you can categorize the users in different circumstances and require them to implement different MFA authentication strengths like SMS auth methods, passwordless authentications, and FIDO2 security key types.
Three Different Types of Conditional Access Authentication Strengths:
Apparently, Microsoft is removing the “require multi-factor authentication” checkbox and replacing it with “require multi-factor authentication strengths.”
Following a thorough analysis of all authentication methods, Microsoft has categorized different authentication strengths under the grant control. They are,
- Basic multi-factor authentication.
- Passwordless multi-factor authentication.
- Phishing-resistant multi-factor authentication.
- Custom multi-factor authentication.
Basic Multi-factor Authentication:
Combination of methods that satisfy medium assurance authentication strength, such as password + SMS.
Any policy that applies this grant access will require all specific users and groups to satisfy the minimum SMS authentication method. Also, they can instead use several multi-factor authentication methods like
- MFA push notifications.
- Verification code
- Text SMS
⚠️Did you notice!? Microsoft has brought the MFA push notification system under a minimum-security level. This is due to the increase in different MFA attacks. So, it’s time to get out of the MFA push notification system and get into a more secure one.
Passwordless Authentication:
Passwordless methods that satisfy high assurance authentication strength, such as Microsoft Authenticator, FIDO2 Security Key.
Passwordless authentication is considered the second most secure method of multifactor authentication? Doubting it? You can get insights on the benefits of passwordless authentication and why it should be implemented with this Microsoft article.
Now, coming to the CA policy, this grant type is available only if the user has enabled passwordless authentication. Otherwise, this might not work as you expected! It’ll show the following error message if you attempt to log in with other authentication methods while applied in this policy.
You can’t get there from here...
Additional sign-in methods are required to access this resource.
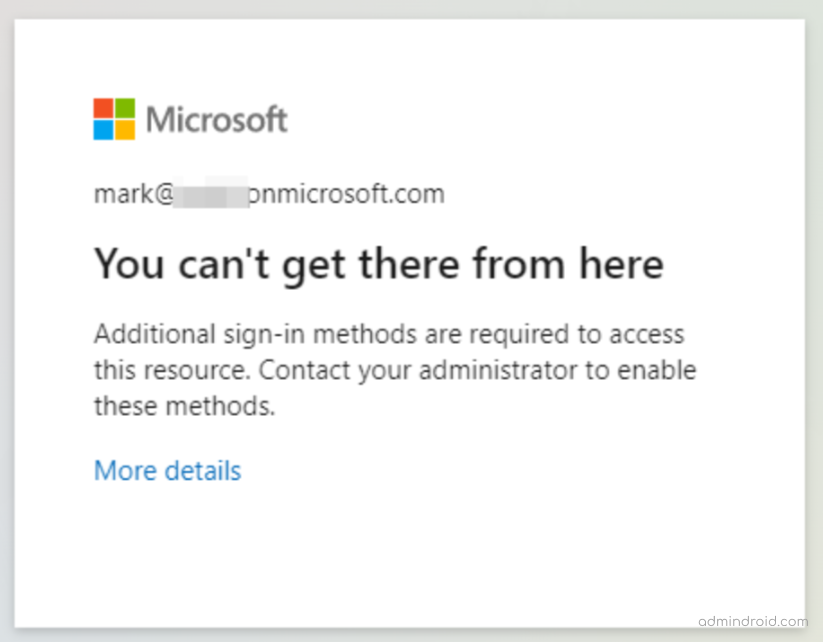
So, make sure to enable passwordless authentication for the user before applying the policy.
Enable Passwordless Authentication in Azure AD:
To enable passwordless authentication for any user, navigate to the path below.
Azure portal → Azure Active Directory → Security → Authentication methods → Policies.
Under the Microsoft authenticator, you can add the required users and set the authentication type (passwordless or any). Later, the user can configure the passwordless authentication in their Microsoft Authenticator app.
Note: You can only enable one work or school account in the Microsoft Authenticator app. If you attempt to add another work/school account, you will receive the following message:
Your organization does not allow you to add your account to Microsoft authenticator.
Phishing–resistant Multifactor Authentication:
Phishing-resistant MFA methods such as FIDO2 Security Keys or Windows Hello for Business.
It’s finally time for the most secure form of MFA: the FIDO2 Security key. That’s exactly what it sounds like! Even the most sophisticated phishing attacks cannot compromise this phishing-resistant MFA. Research by Barracuda Networks says that around 667% of phishing attacks arose during the pandemic. Woah! That’s an alarming count, isn’t it? So, phishing-resistant MFA was discovered to counter such suspicious attacks.
What are security keys?
It is a hardware token that goes beyond traditional MFA techniques. This delivers a more seamless authentication experience because users no longer need to memorize passwords, wait for OTPs, and input them into the website. Rather, the app accesses the user’s private key on their device, and the user authenticates themselves using a fingerprint or other biometric feature.
This type of authentication method can be used for highly-privileged admin and executive accounts. No data can be theft with this kind of phishing-resistant MFA.
Also, you can utilize Microsoft 365 passkeys, an another phishing-resistant method with FIDO2 credentials. It is stored directly on user’s device to provide more convenient logins. This method prevents password spray attacks and harmful phishing attacks effectively.
Note: FIDO2 security keys are now compatible with Microsoft Entra ID federated apps on iOS and macOS web browsers. Since January 2024, MS Entra supports passkeys to be stored on computers or mobile devices.
Custom Multi-Factor Authentication:
Strengthen the authentication step by combining multiple MFA methods into one based on your requirements.
Now the cherry on top of this, we have CUSTOM AUTHENTICATION STRENGTH. Not only can you select between the above three types, but you can also create your own custom authentication strength and use them with conditional access policies.
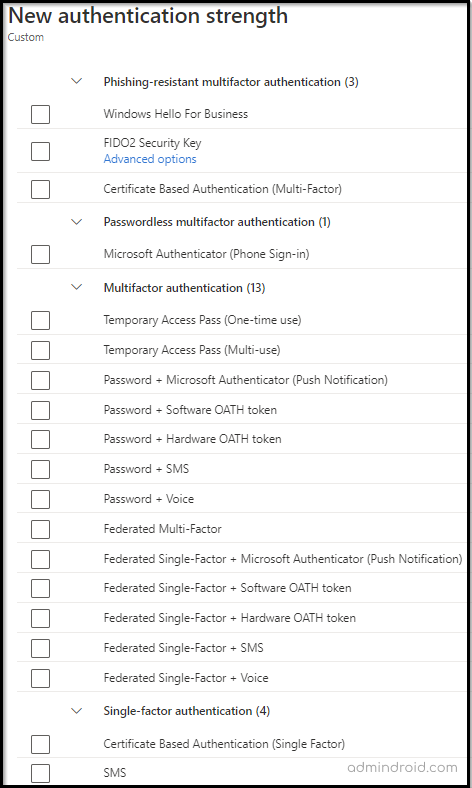
Combining the above authentication type and defining an MFA method of your own can give you a good chance to ban weaker authentication methods like SMS and phone calls. It also enables you the power to control your organization’s second-factor authentication and empowers you to have an attack-free environment.
Is Azure AD Premium P1 License the Only Solution for Better Security?
No, not at all! You can configure MFA security configurations and protect Office 365 accounts from MFA bypass using a Free Azure AD license. Yes, you heard it right!
Researchers say that most users use MFA push notification authentication. But the question is, is it really safe to use the MFA push notification system? Yes, 100 percent! But only if you enable the below-recommended setting along with push notification. If not, you will be put in serious danger! Moreover, most of us failed to notice and configure this hidden setting in Azure AD.
Wondering how to set it up? Navigate to the path given below to add additional contexts:
Azure portal → Azure Active Directory → Security → Authentication methods → Microsoft Authenticator → Configure tab.
Why not enable it now in just a toggle? Read the steps defined here, and follow them to turn it on and experience attack-free multi-factor authentication:
Enable MFA number-matching techniques and additional contexts.
The bottom line is that passwordless authentication is very useful for organizations needing strong protection without exceeding their budget. For those with the resources to invest in high-level security, phishing-resistant MFA methods are the way to go. So, Consider removing phone-based MFA and transitioning your users to phishing-resistant MFA methods. To further enhance your security, fine-tune your phishing protection with Microsoft Secure Score recommendations.