In this digital world, we can access data from anywhere using any device. Consider accessing an application from your device that asks you to enter your credentials. Some devices have complex authentication processes to enter your credentials which is truly frustrating! Here comes authentication flows in Conditional Access that streamline the authentication process and make it easy for end users.
Most of the apps require users to authenticate for accessing the data. There are various flows in Microsoft Entra ID like authorization code flow, device code flow, implicit flow, hybrid flow, etc., used to authenticate the apps accessed by users. Let’s see authentication flows in Azure AD in detail.
Authentication Flow Policy in Conditional Access
As previously said, there are various authentication flows available in Microsoft Entra ID. Among them, the authentication flows considered as high-risk (device code flow and authentication transfer) are included in the Conditional Access policy to control or block them. These authentication flows in the Conditional Access policy are currently in preview and included to have more power over security in your organization.
Device Code Flow in Conditional Access
Device code authentication flow is used to authenticate non-browser or input-constrained devices like smart TVs, etc. This flow makes the authentication process easier for end users, eliminating the difficult process of authentication.
For example, consider if you want to open an app on your smart TV that requires you to type the credentials using the on-screen keyboard and the remote buttons. Isn’t it frustrating!? Here comes device code flow in which you can use your secondary device to authenticate the app opening in your smart TV, making the process smoother.
Authentication Transfer Flow in Conditional Access
Authentication transfer is a new flow that transfers an authenticated state from one device to another seamlessly to provide an easy user experience.
For example, if you have a QR code in the desktop version of any app and you scanned the QR code in the mobile version, the authenticated state will be transferred from the desktop to the mobile device.
Block Authentication Flows in Conditional Access Policy
Authentication flows being considered as high-risk among others must be blocked in the organization to maintain security. Microsoft has now provided the option to restrict authentication flows using the CA policy. Though they make the authentication process easier for users, they have certain loopholes through which attackers can interrupt and gain access. To avoid such unauthorized actions, MS recommends blocking or controlling high-risk authentication flows using the Conditional Access policy. Let’s see how to do that.
- Block Device Code Flow Using Conditional Access Policy
- Block Authentication Transfer Flow Using Conditional Access Policy
Block Device Code Flow Using Conditional Access Policy
The device code flow is authenticated by any of the following methods.
- Navigating to a URL and entering a user code
- Interacting with a QR code with an embedded user code
- Directly navigating to a verification page with an embedded user code.
As the user code is entered manually by users, it might be possible for brute force attack or remote phishing to occur where an attacker tries to initiate a device code request and gain access to resources. To avoid such attacks, MS recommends using device code flow wherever necessary and should block using it in other places.
To block the device code flow using CA policy, do the below steps.
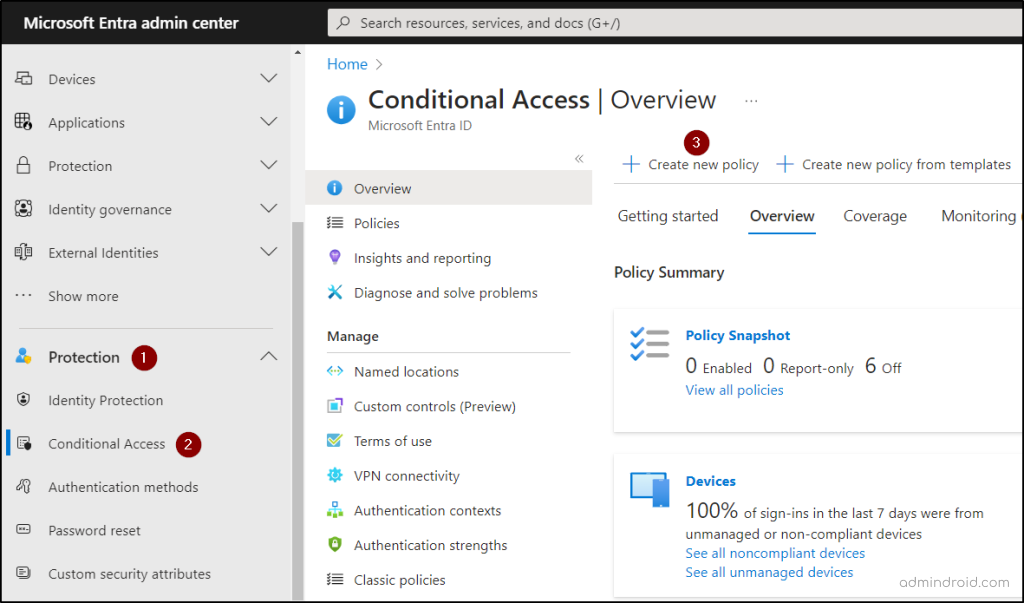
- Sign in to the Microsoft Entra admin center with the necessary administrative privileges.
- Navigate to Protection-> Conditional Access in the left pane.
- Click the ‘Create new policy’ option.
- Give a suitable name to your CA policy.
- Under Assignments, select ‘Users’ and include/exclude required users.
- Then, select ‘Target resources’ and choose ‘Cloud apps’ from the dropdown. And include all apps or required apps based on your preferences.
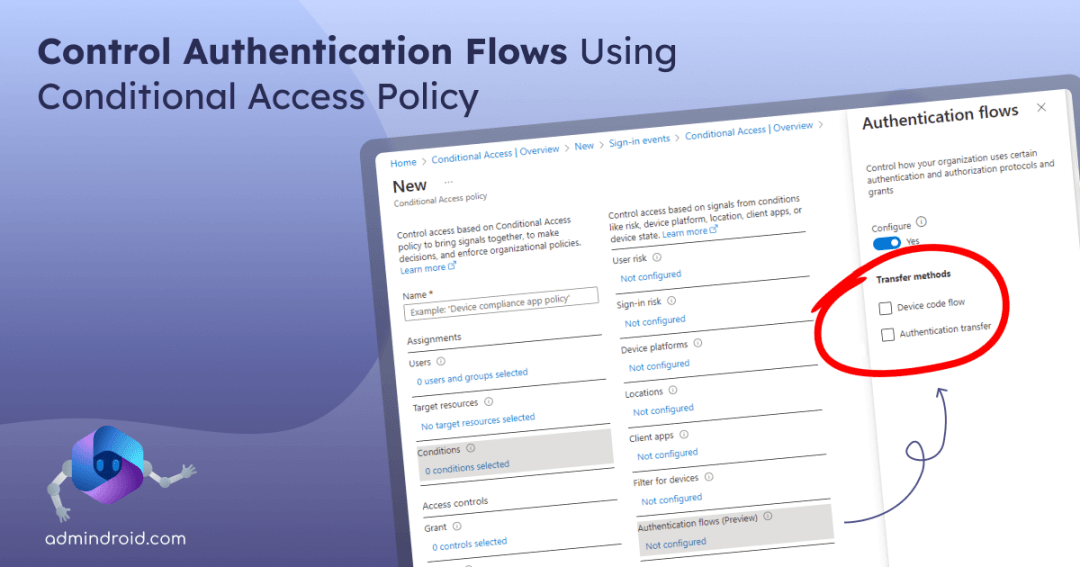
Note: Though it reduces device code attacks, it may block legit requests from mobile devices. So, ensure only necessary users/services are included. - Select ‘Conditions’ and you will notice a newly added condition named ‘Authentication flows’ which is currently in preview. Choose that option and turn the toggle to ‘Yes’ under Configure in the right pane.
- Then, check the ‘Device code flow’ checkbox and click ‘Save’.
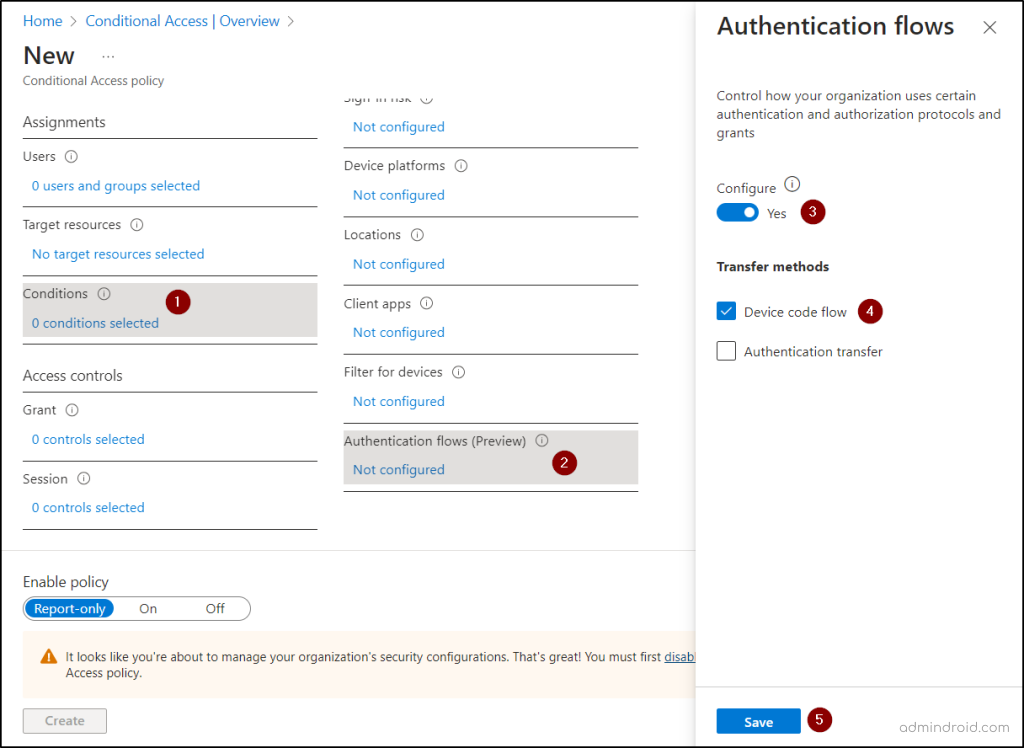
- Under Access Controls, select ‘Grant’ and choose the ‘Block access’ option. Then, click the ‘Select’ button.
- Confirm your settings and enable the policy in ‘Report-only’ mode.
- Click ‘Create’ to create your CA policy.
After creating this CA policy, users accessing any apps using device code flow sessions that are not allowed in this policy will be blocked in the organization.
Block Authentication Transfer Flow Using Conditional Access Policy
Controlling authentication transfer using CA policy is now in preview. Admins might want to restrict users from accessing Outlook from personal devices. In such scenarios, the authentication transfer flow can be blocked in the organization.
To restrict the authentication transfer flow using the Conditional Access policy, follow the same steps used for device code flow.
Instead of checking the ‘device code flow’ checkbox, you can check the ‘Authentication transfer’ checkbox under ‘Conditions’.
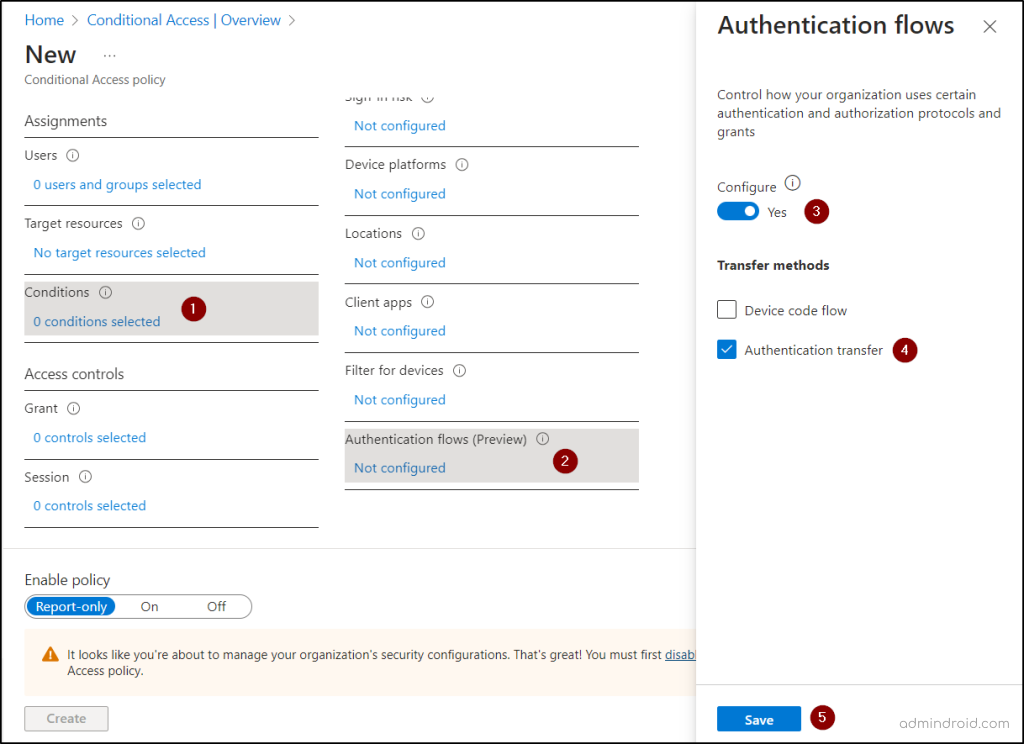
Note: You can also block both of the authentication flows by checking both checkboxes.
Monitor Authentication Flow Events with Azure AD Sign-in Logs
While configuring CA policy to restrict or block authentication flows, it’s better to monitor Conditional Access changes and understand whether the restriction works properly as you expected. Otherwise, it may block legitimate sessions and require policy modification. Thus, you can track the authentication flow events either by creating a policy in ‘Report-only’ mode or using the Azure AD sign-in logs.
To monitor the authentication flow events, you can apply necessary filters to the sign-in logs. Follow the below steps to apply filters.
- Navigate to ‘Monitoring & health -> sign-in logs’ in the Microsoft Entra admin center.
- Click the ‘Add filters’ option and select the ‘Authentication protocol’ filter.
- Then, select ‘device code flow or authentication transfer’ for which you wish to monitor the events.
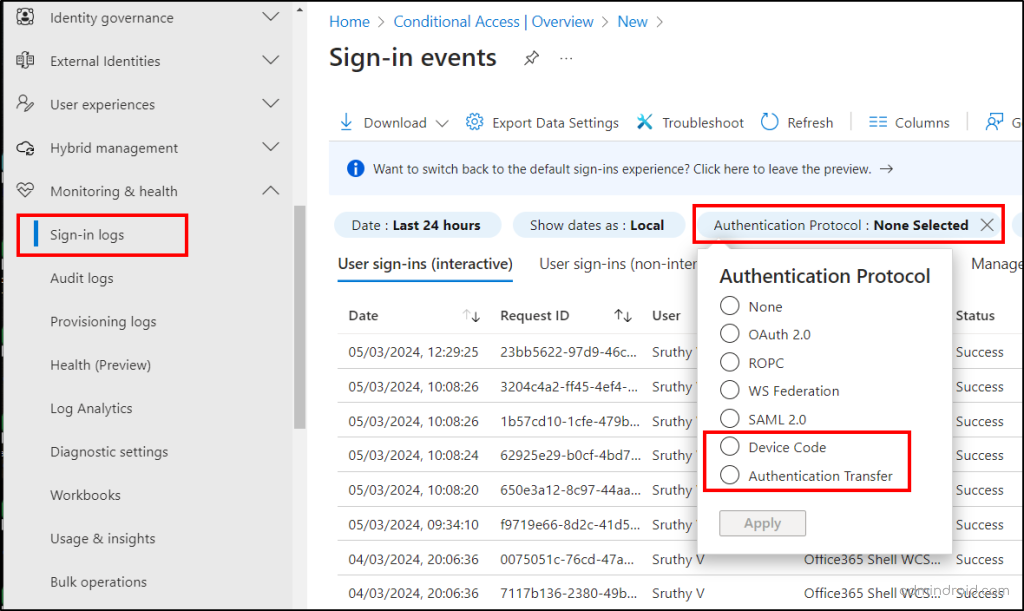
Note: If you want to monitor the sign-in events based on the CA policy alone, you can navigate to Protection -> Conditional Access -> Monitoring -> Sign-in logs.
Authentication flows included in the Conditional Access policy are a delight for admins to maintain the Microsoft 365 security best practices in the organization. I hope this blog gives a better understanding of why authentication flow is included in CA policy and how it can be blocked in the organization. Feel free to drop your queries in the comment section. We’re ready to hear from you! Happy securing!