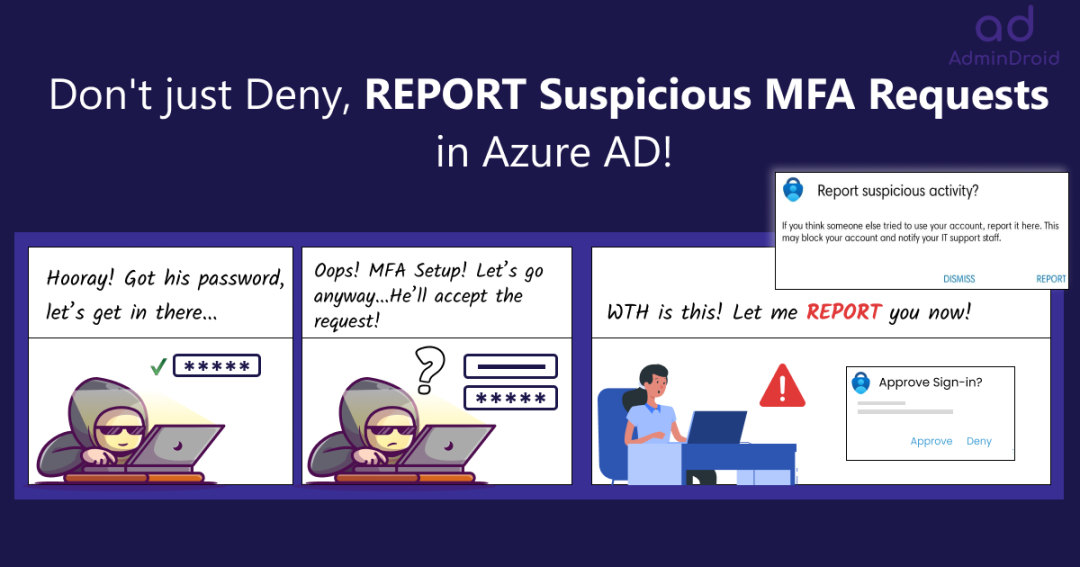
😩Are you tired of constantly denying multi-factor authentication requests that you did not initiate? Well, you’re not alone! Receiving an increasing number of MFA requests that were not initiated by you has become incredibly frustrating, and this ongoing influx has opened the door to MFA fatigue attacks.
It’s like someone knocking on the door, but you didn’t invite them over, right? You might feel annoyed, confused, and scared! 🤯 Although these requests may appear to be less hazardous, they can eventually lead to a more extensive cyber-attack. But what if I told you, you could do more than just deny the requests?
And, that’s where the new feature of ‘reporting suspicious MFA requests’ in Azure AD comes in! 🚀This report suspicious activity is an updated version of the MFA fraud alert feature available in Azure AD. This new security feature allows users to report unusual authentication requests immediately before they turn into full-blown cyber-attacks.
Now, it’s time to take Microsoft 365 user accounts security seriously. Therefore, in this blog, let’s take a deep dive into this feature and discover its workings.
What is Report Suspicious Activity in Azure AD?
With the rise of cybercriminals, it’s becoming all too common for people to receive authentication requests for services they never signed up for. So, here, reporting suspicious login attempts come secondhand! Let’s explore this new feature in detail and see what it holds.
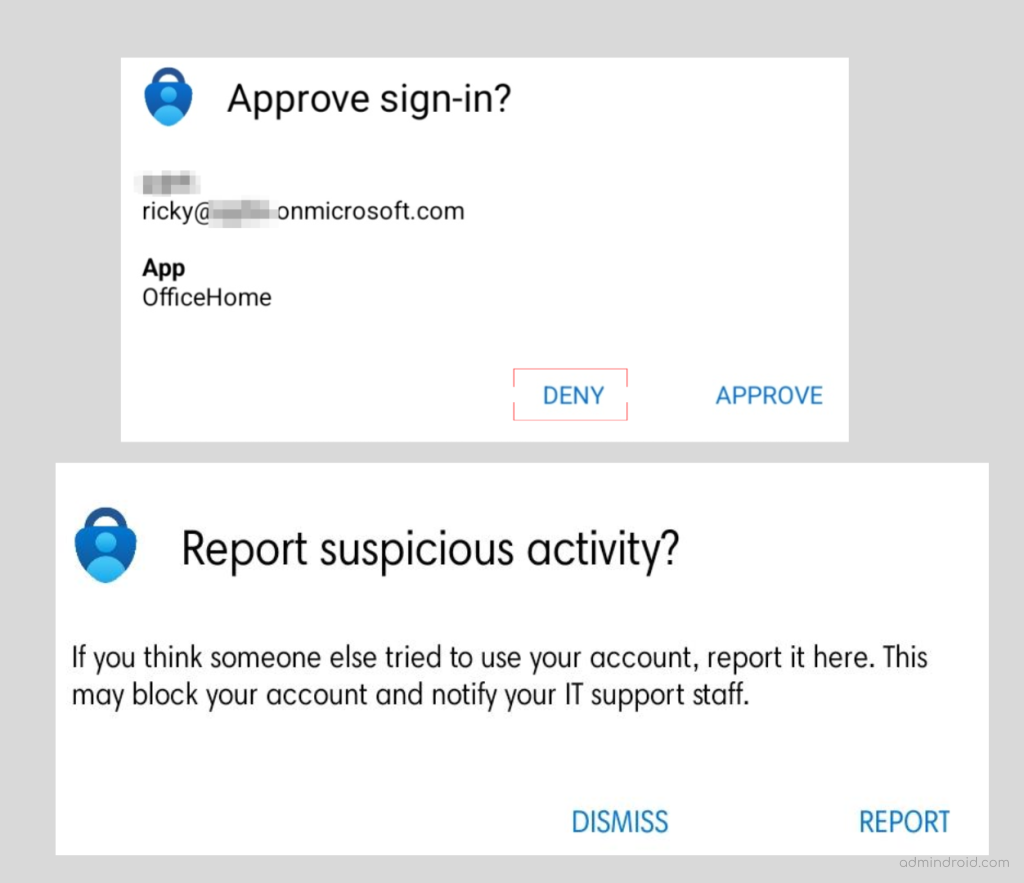
When an unknown and suspicious MFA prompt is received, instead of just denying the MFA prompt, users can use Microsoft Authenticator or their phone to report a fraud attempt.
Consequences of Reporting Suspicious MFA Requests:
The following steps will be taken by Microsoft in the background when a user reports a suspicious login attempt.
- The reported user is set to High User Risk.
Point to Remember: As this is an updated version of the fraud alert feature, both the report suspicious activity and MFA fraud alert can function together, which means,
➤ As part of the pre-existing MFA fraud alert feature, the reported user sign-in will automatically be blocked.
➤ With the new report suspicious activity feature, the status of the reported user will be set to high risk.
Overall, if you have enabled both settings, users will be automatically blocked, and risk status will be updated. To make them work normally, admins must manually remove them from the blocklist and remediate their risk level.
How to Enable Report Suspicious Activity in Microsoft Entra Admin Center?
Now that you have a better understanding of what the new feature on reporting fishy MFA attempts is: let’s look at how to enable the feature.
Microsoft Entra admin center → Protect & secure → Authentication methods → Settings → Report suspicious activity (Preview)
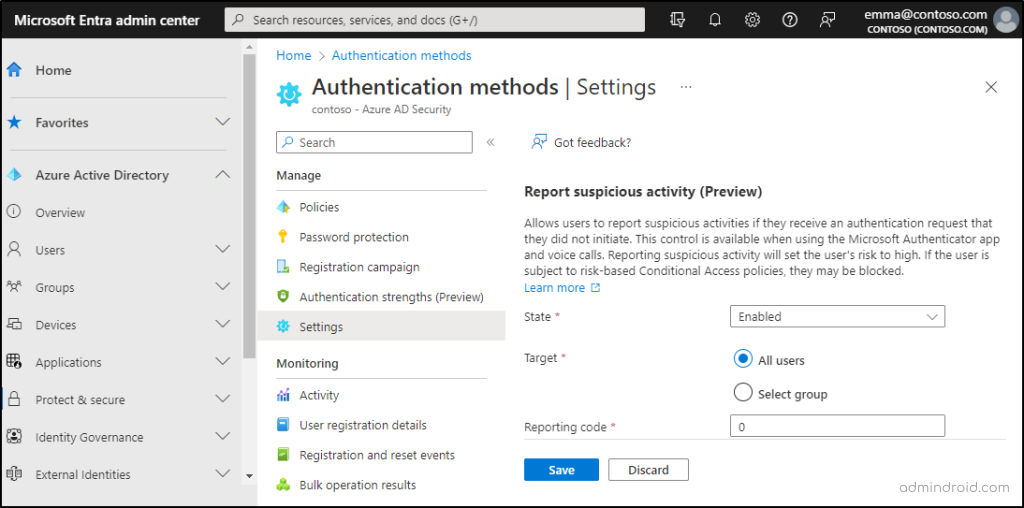
2. Here, you can change the state to Enabled.
3. Then, you can choose between ‘All users’ or a particular ‘targeted group’ and then save your settings.
That’s it! It’s as simple as Childsplay to configure, so why not do it just right away and ensure security among organizations? While denying an MFA request, the user will see a Report option. They can report suspicious MFA requests by using this ‘Report’ option and eventually, this report will be logged in all the Azure AD sign-in reports.
Get Suspicious Activity Reports in Azure AD
Spot Office 365 suspicious activities in a flash! So, now after turning on the setting, it’s crucial to monitor any suspicious activities related to fraud MFA attempts. Therefore, Microsoft provides around 3 different reports to view the suspicious activity logs and proactively investigate any strange MFA-related activities.
POINT TO REMEMBER: Above all, admins can configure email alert notifications to be quickly notified on every user reporting and stay alerted.
Get Risky MFA Attempts Details in Risk Detection Reports:
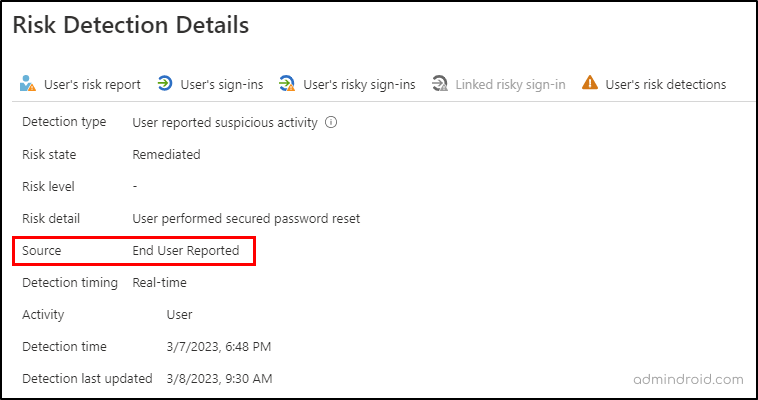
When a user reports an unusual login attempt into their account, it’s an immediate sign of risk. So, as a sort of this, the activity gets logged in the ‘risk detection reports’ in Azure AD. You can navigate the below path to view the risk detection reports:
Microsoft Entra admin center → Protect & secure → Identity protection → Risk detections (under the ‘report’ section)
Admins can identify the user-reported activities by setting the Detection type as ‘User reported suspicious activity’ value and the Source as ‘End User Reported’ value.
Get Suspicious MFA Attempts Information in Azure AD Sign-in Logs:
When a user reports an unusual login attempt, the event is logged in the sign-in logs as the sign-in request was rejected. You can navigate the below path to view the sign-in logs in Azure AD.
Microsoft Entra admin center→ Users → User settings → Sign-in logs
The user-reported activities will be logged as SuspiciousActivityReported in the Authentication detail as below.
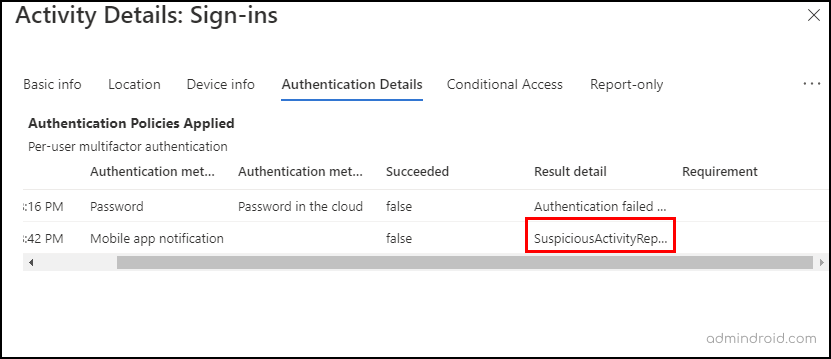
Get Unusual MFA Requests Detail in Azure AD Audit Logs:
When a user reports an unusual login attempt into their account, the event gets logged in the audit logs as the user has been blocked for MFA. So, as a sort of this, the activity gets logged in the ‘audit logs’ in Azure AD. You can navigate the below path to view the audit logs in Azure AD.
Microsoft Entra admin center → Users → User settings → Audit logs
The fraud report will be logged as Fraud reported-user is blocked for MFA under Activity type as below.
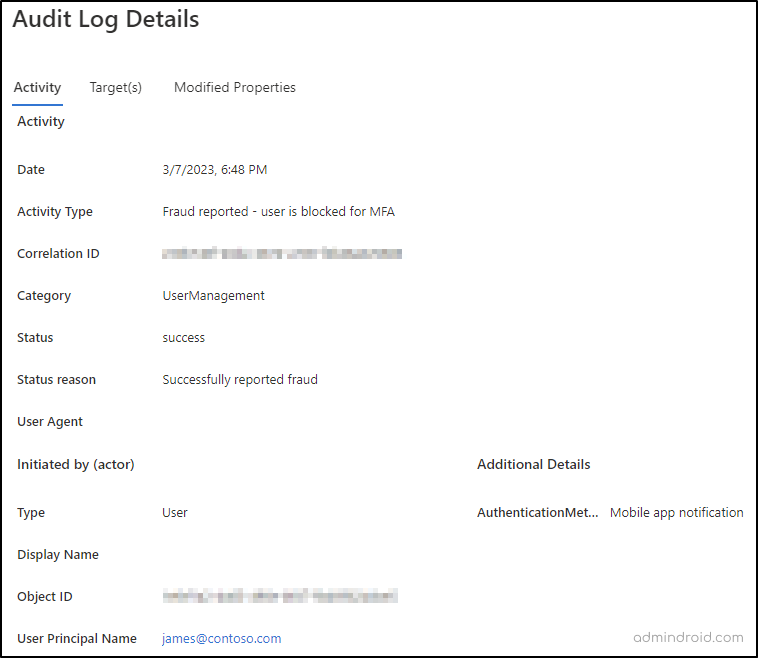
Configure to Send Email Notifications on Fraud Reporting in Azure AD
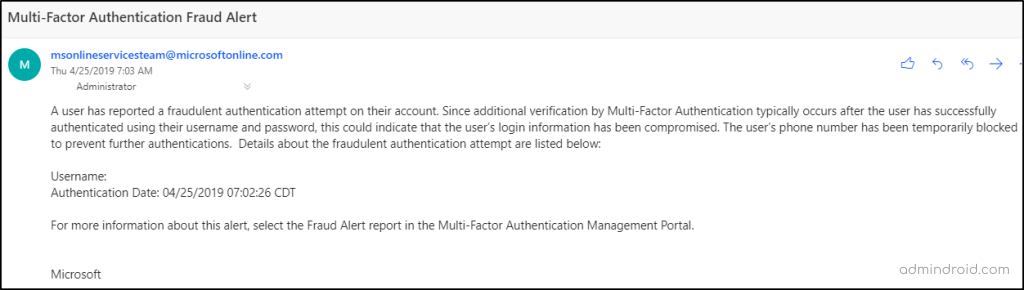
Most importantly, admins can get immediate alert notifications on every user reporting suspicious MFA authentication requests. To configure email notifications, administrators can navigate the path below, add the email address, and then save the settings. Now, configured users and identity administrators will receive email notifications.
Microsoft Entra admin center → Protect & secure → Multifactor authentication → Notifications (under ‘settings’ tab)
That’s it! By using these reports, admins can quickly get notified about any abnormal MFA authentication activities and take proactive measures to safeguard their organization’s data and assets. Therefore, admins can make use of these reports to stay on top of potential security threats!
Effective Safety Measures to Defend Against Suspicious MFA Requests
We’ve covered most of the parts related to unusual MFA requests. Here’s the big question, what to do with such suspicious activity event reports? Therefore, let’s take a look at the safety measures to be taken if you notice abnormal MFA auth requests.
- First and foremost, use risk-based policies and limit sign-in access to the reported users.
- Secondly, enable self-service password reset for the reported users so they can remediate on their own.
- Ensure that users follow a strong Office 365 password policy and use strong passwords that hackers can’t crack.
- In case of a worse emergency, if limiting sign-in access does not work and the hacker continues to send MFA requests, the admin can temporarily disable the user.
Finally, coming to an end, don’t let MFA fatigue get the best of you! Start using the report suspicious activity preview feature as a first-line defense against cyber threats and protect your Office 365 accounts.