
👀I see multi-factor authentication everywhere nowadays! As with the rise of numerous cyber threats such as phishing attacks, password breaches, etc., multi-factor authentication has been the go-to solution for securing Office 365 accounts & systems. But with different MFA methods available, it’s harder than ever for an organization to enforce a consistent and secure authentication policy.
Now, if you are one among those thinking of a way to implement a consistent and secure authentication process across all users, then it is a bingo! 🤛System-preferred MFA in Microsoft 365 was announced in early March 2023 for public preview, but this feature just went general availability in June 2023(MC565271).
This newly developed security technology bypasses the risks associated with the default MFA method and lets Microsoft move the coins for you to have a seamless and secure MFA experience! So, without any further delay, let’s jump into the new concept of system-preferred MFA in this blog. Here, we’ll walk you through everything from how it works to how to get started, leaving you with a better understanding of how to safeguard against today’s ever-evolving threats.
What is System-preferred Multi-factor Authentication?
Don’t worry about juggling multiple MFA methods for your organization anymore! Because this system-preferred MFA comes as a great relief for IT administrators. So, let’s see what these actual system-preferred MFA are released for.
With the system-preferred MFA enabled, Microsoft determines the most secure method among the registered methods for users to sign in, irrespective of the default MFA method.
Let’s see an example for this case – Consider a user registered for phone call authentication and MS Authenticator push notification method. The default authentication method for the user is set up as phone call authentication. Now, if the system-preferred MFA is enabled for the user; Microsoft will override the weaker default auth method (phone call) and prompt them to sign in by means of an MS push notification method.
Note: The system-preferred MFA isn’t limited to users specified by authentication method policies; it also extends to users who have enabled MFA through the legacy MFA policy (per-user MFA).
Release Status of the System-Preferred MFA:
By default, system-preferred MFAs are set to a Microsoft-managed state.
Public Preview – The public preview rollout is from March 1st, 2023 and admins can enable system-preferred MFA using GraphAPI. A new admin UI will be introduced to manage system-preferred MFA in Microsoft 365 from the end of March 2023.
Note: Since this feature is only in public preview, the Microsoft-managed state is now set to the disabled state.
General Availability – The feature became generally available in June 2023.
Until the end of June 2023, the state will be set to “Microsoft-managed,” giving admins the flexibility to manage it. From the “Microsoft managed” state, it’ll be changed to “Enabled” from the end of June 2023.
✅The Major Update – From mid-July to mid-August, the system-preferred MFA will be enabled by default for all users eventually, with no option to disable it and the toggle will be moved away.
So, what are we still waiting for? Let’s get into the track early and check how it works! 😎
How to Enable System-preferred MFA in Microsoft 365?
Now that we’ve seen how this feature can help save us from potential threats- let’s move on to the steps to enable this important security feature. There are two ways possible to enable system-preferred MFA in Microsoft 365 and they are:
But before we delve into the steps, it’s essential to note that there is a restriction that comes with it, which is –
➤ You can only include/exclude only one group at a time. (The groups can be either dynamic or nested groups.)
Enable System-preferred MFA in the Azure Portal:
1. To manage system-preferred MFA in the Azure portal, navigate to the following path.
Azure portal 🡢 Security 🡢 Authentication methods 🡢 Settings🡢 System-preferred multifactor authentication.
2. As the feature is now available generally, the “disabled” state is updated and now is set to the “Microsoft Managed” state by default for all users.
3. Further, admins can enable system-preferred MFA for all users or only for specific groups in the Target and Save.
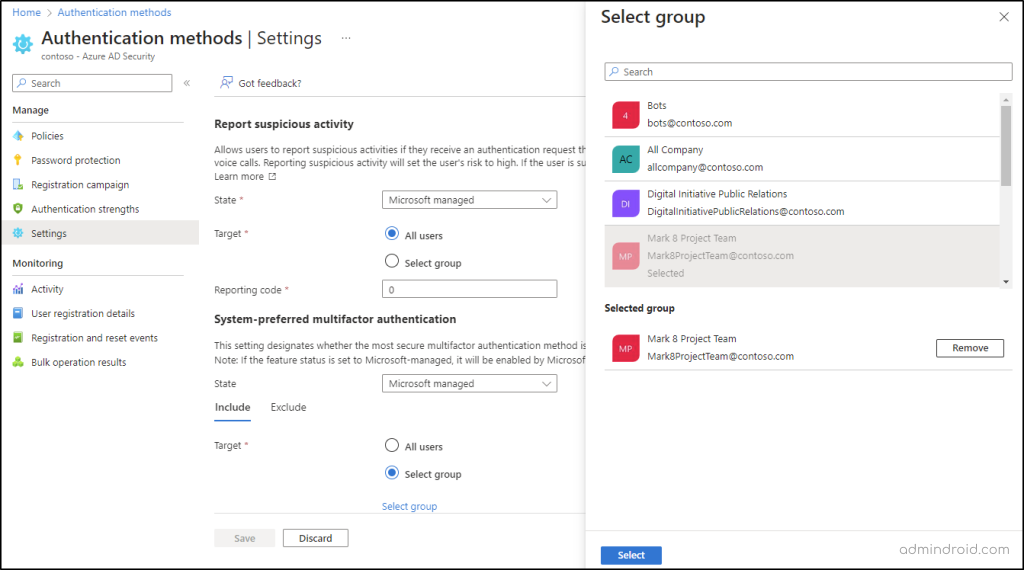
Enable System-preferred MFA through GraphAPI:
Log in to the Microsoft Graph developer portal and ensure that you have the permission, Policy.ReadWrite.AuthenticationMethod granted.
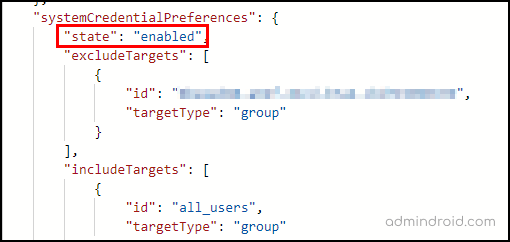
You can use the following sample code to enable system-preferred MFA to all users and exclude a specific group.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
PATCH https://graph.microsoft.com/beta/policies/authenticationMethodsPolicy Content-Type: application/json { "systemCredentialPreferences": { "state": "enabled", "excludeTargets": [ { "id": "d1411007-6fcf-4b4c-8d70-1da1857ed33c", "targetType": "group" } ], "includeTargets": [ { "id": "all_users", "targetType": "group" } ] } } |
The above query disables system-preferred MFA for the selected group and overrides other users’ weaker authentication with their strong MFA authentication method. Now, if you want to check whether the code works as expected, you can use the following query and check:
|
1 |
GET https://graph.microsoft.com/beta/authenticationMethodsPolicy |
How System-preferred MFA Work to Secure Office 365 Accounts?
Are we done yet? Probably not! So far, we have discussed how to enable system-preferred MFA and why it is a good idea to use it. Therefore, let’s take a look at how this works.
Firstly, we’re testing this case with the user authy@contoso.com. So, let’s get all the MFA methods registered with this account before we enable this feature. Run the below cmdlet to find the multi-factor authentication methods registered for the user and discover the default MFA method.
|
1 |
Get-MsolUser -UserPrincipalName "authy@contoso.com" | Select-Object -ExpandProperty StrongAuthenticationMethods |
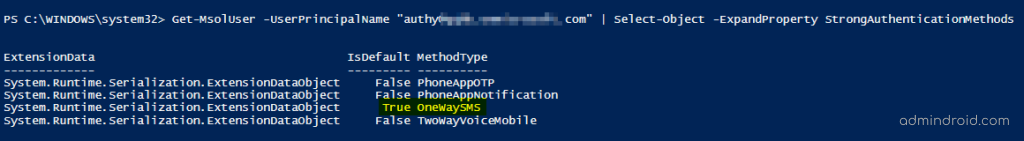
Based on the above example, we can see that SMS authentication is the default method, and a further three multi-factor authentication types are registered for the user. As a result, when MFA is prompted, Microsoft will ask the user to choose an authentication method as shown below.
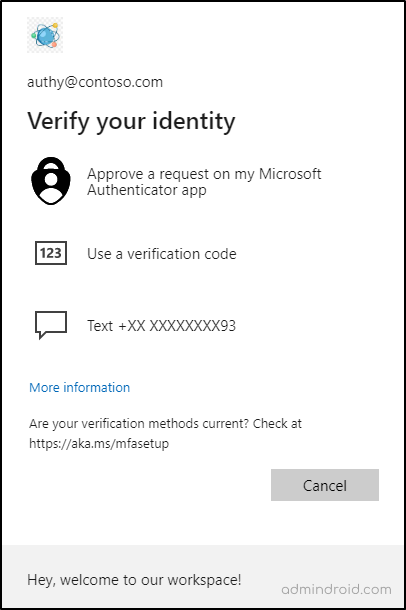
However, once the system-preferred MFA has been enabled for the user, Microsoft will select the strongest authentication method among those registered. Accordingly, by precedence, the Microsoft Authenticator push notification is the strongest of all registered methods. So, the user will be prompted to satisfy the authentication type as below.
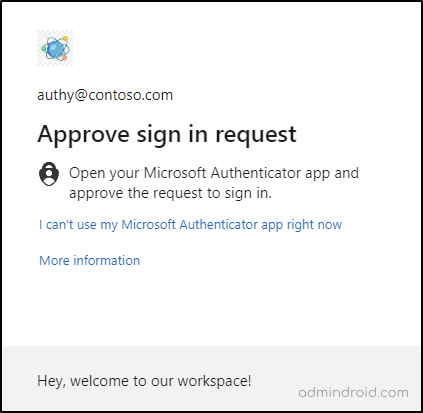
This is definitely a more robust and reliable feature, isn’t it? Therefore, enforcement of this advanced security control helps us implement stronger authentication methods and reduce the risk of multiple MFA attacks in one go! So, get ready now and start testing out in your tenants soon.
That’s it! I hope we have shown a clear idea of how this system-preferred MFA will work for your organization. From reducing the risk of unauthorized access & data breaches to simplifying the authentication process for end-users, system-preferred MFA is a must-have for any organization looking to take its security to the next level. Still, having second thoughts on enabling this?
Start using system-preferred MFA right now and enjoy a space where authentication is no longer a headache, but a breeze!






