With the rise of the work-from-home culture, the rise of unusual logins started to increase. Since employees are working from different locations, the IT department cannot interpret what’s happening with users signing in from different places.
To help with this, Microsoft introduced Azure AD sign-in logs. Office 365 sign-in logs answer the following questions.
- What are the sign-in trends for a user, service, or application?
- Has the user successfully signed in or failed?
- How many sign-ins happened over a week or month?
But what if these are not enough to secure your Office 365 workspace? Office 365 provides Azure AD sign-in logs, revealing when, where, and what each user signed in. But it lacks details on the sign-in prompts, and detailed device analytics, making it trickier to uncover potentially malicious activity before it causes any trouble.
AdminDroid, a robust Office 365 Reporting tool, bridges the information gap between Azure AD reports and manages your Office 365 reporting efficiently. AdminDroid’s Sign-in analytical reports allow you to break the limitations in Office 365 and identify suspicious Azure AD user sign-in risks or other unusual sign-ins behaviors.
Aside from simply displaying detailed logs, AdminDroid also classifies the activity logs into summary reports, distinguishes between successful and failed logins, identifies the last login information, and more.
Admins can use AdminDroid to not only view Azure AD sign-in errors but also set a “risky sign-in alert found” alert when a user attempts to sign in from a blocked IP address. It also provides a complete insight into the users’ access to resources and helps to find out the users who still use basic authentication.
Get to know who’s signing from where, and when in your organization:
AdminDroid categorizes the usual user sign-ins and the risky sign-ins that happened across your organization.
For Risky sign-ins, AdminDroid reports on suspicious attempts that have been performed by someone who is not the actual owner of a user account and also reports on user accounts that may have been compromised. Sign-in analytical reports answer every question like,
- From where are my users signing-in from?
- What are the locations that have encountered the most sign-in errors?
- Are the user accounts involved in sign-in errors?
- How often do these errors happen?
- Where do my guest users belong to?
- Do my guest users have any inappropriate sign-in locations?
- How many risk detections were reported?
AdminDroid’s sign-in analytical reports answer all the above queries with a sleek comprehensive Azure AD sign-in analytics dashboard covering all the user actions that occur across your Office 365 environment.
Summarize the Sign-in Patterns Happening in Your Organization:
AdminDroid covers you up with the summarized details of all the sign-in entries performed in the organization by granularly categorizing them based on each signed in application, location, device details, etc.
- Organization sign-in summary
- User sign-in summary
- User last logon summary
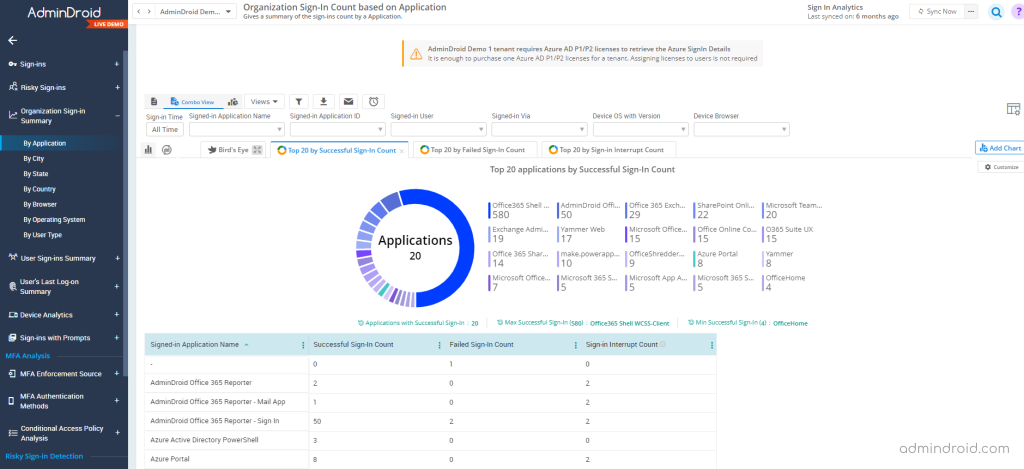
Organization sign-in summary:
Users may use multiple applications for work purposes, and that requires signing into third-party tools. What if your users sign in to any suspicious application? Discovering your Office 365 users’ sign-in is easy, but is there anything to find where your organization gets signed in?
Yes, it is possible. With AdminDroid, you can keep track of all the details like if your organization has been signed up for any new applications, countries, or operating systems.
User sign-in summary:
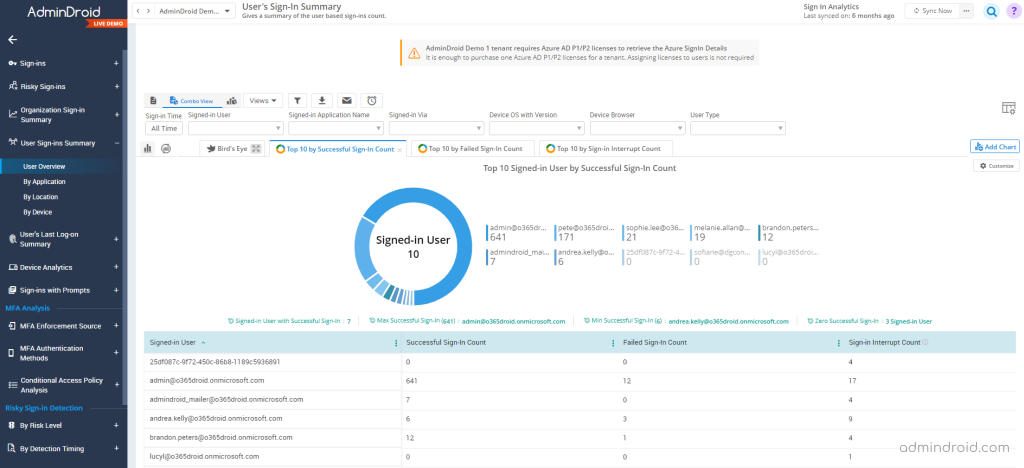
When user sign-ins from multiple locations, there happens the risk of unusual sign-in detection. With the user sign-in summary report, admins can keep monitoring the users’ sign-in trends and know what they are up to and avoid the unusual location sign-in risks with AdminDroid.
AdminDroid records every action of users, such as successful, failed, and interrupted logins, and detects any suspicious activity that happened across the Office 365 environment. It also provides information about the usage of managed applications and the user sign-in activities within them.
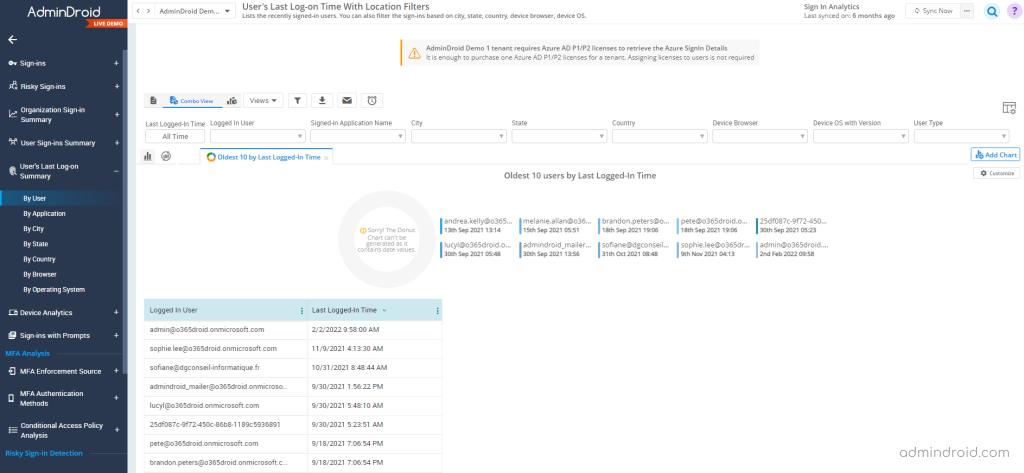
User’s last logon summary:
There are numerous benefits a single report can offer. And that is the User’s last logon summary report. With this, admins can get the last sign-in time/inactive time of the user and if a user continues to be inactive for long, they can find the reason and terminate the account. Thereby, helping to cut off the license spent on the respective Office 365 user.
AdminDroid also granularly categorizes Azure AD sign-in logs into a detailed last logon summary based on sign-ins by application, city, country, operating system, and browser.
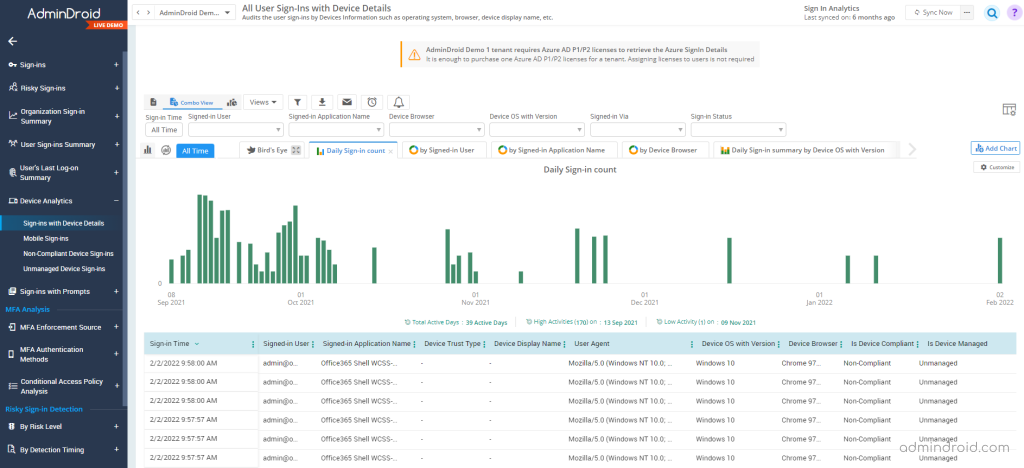
Track the device usage to avoid suspicious activities:
Every device is possible to be attacked and must be monitored and managed properly. Even if the device is personally owned but used for work, admins must include those devices to account for. AdminDroid reports detailed device analytics on the following categories:
Sign–ins happened along with device details – Audits the user sign-ins by Devices Information such as operating system, browser, device display name, etc.
Mobile sign-ins details – Audits the users who have signed in via Mobile.
Non-compliant device sign-ins – Lists the user sign-ins that are signed in via non-compliant devices.
Unmanaged device sign-ins – Lists the user sign-ins that are signed in via unmanaged devices.
Never Miss an Update on the Changes in Your Office 365 Environment:
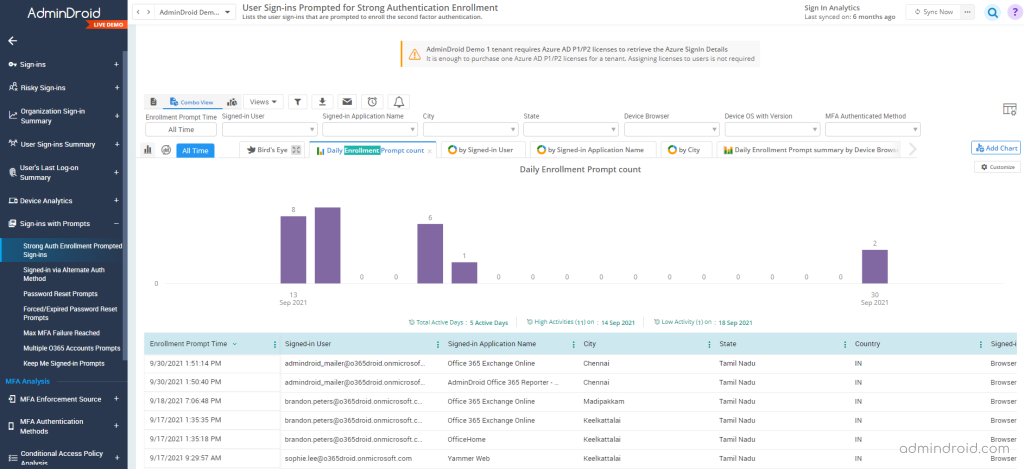
Office 365 periodically prompts users to reset passwords due to expiration or other security-related prompts. However, does Office 365 provide any detailed analysis of how users respond to these security prompts? Probably not! AdminDroid logs all sign-in prompts in your organization as well as how users respond in detail. Detailed reports include:
Strong Auth Enrollment Prompted Sign-ins – Lists the user sign-ins that are prompted to enroll the second factor authentication.
Signed-in via Alternate Auth Method – List the user sign-ins who have selected alternative methods for authentication. (Like the user choosing the “Sign-in Another Way” option)
Password Reset Prompts – Lists the user sign-ins that are prompted to reset the password or for password registration entry.
Forced/Expired Password Reset Prompts – Users reset the password after the password is expired or after admin set force change user password.
Max MFA Verification Failures Reached Sign-ins – Lists the activities where the MFA failure threshold is reached, and users are forced to use other MFA methods to log in.
Multiple O365 Accounts Prompts – Lists the user sign-ins with the multiple Office 365 accounts connected.
Keep me Signed in Prompts – Lists the user sign-ins who chose “Keep Me Signed-in” during the authentication procedure.
Finally, AdminDroid will help you analyze all sign-in-related queries in just a few clicks. With AdminDroid, you can easily solve problems you might not be aware of. Get started now and explore the features of AdminDroid!






