On Day 12 of Cybersecurity Awareness Month, learn how to grant just-in-time access to approved AI tools using Microsoft Entra Access Packages, ensuring innovation doesn’t come at the cost of security. Stay tuned for upcoming blogs in the Cybersecurity blog series.
We’ve all heard the saying: “Give a man a fish, and you feed him for a day. Teach a man to fish, and you feed him for a lifetime.” But in cybersecurity, the modern equivalent is:
“Block a user from AI, and you stop risk for a day. Give a user governed access to AI, and you enable secure productivity indefinitely.”
Previously, we saw how to block Generative AI and prevent users from uploading sensitive content to AI using web content filtering policies in Microsoft Entra. But what if a user needs an AI tool to perform their job? What if blocking them creates friction and this pushes towards shadow AI?
In this blog, we’ll explore a smarter alternative to an outright block: providing just-in-time, time-bound access to approved AI applications using Access Packages in Microsoft Entra Identity Governance.
Why Blocking All Generative AI Access Backfires
Imagine this: Sarah, a financial analyst, is finalizing a critical report. She needs to analyze vast amounts of customer feedback data. Manually, it would take days. She knows an AI tool could summarize trends in minutes.
She tries to access ChatGPT, but it’s blocked. Frustrated, she spends hours on a tedious task, missing her deadline. Alternatively, she might use her personal phone to access the AI tool, inadvertently uploading sensitive customer data to an unmonitored platform. This is the hidden cost of a “block everything” strategy.
Provide Time-Bound Access to Secure GenAI App Access in Microsoft 365
As AI usage expands, so do the risks of shadow IT and uncontrolled data sharing. To counter these challenges, the Microsoft Entra Suite offers powerful capabilities to detect shadow AI usage and protect internet access.
The guiding principle is simple: why give permanent 24/7 access to powerful AI tools when users typically need them only temporarily? Permanent access increases the attack surface and risk of inadvertent data exposure. The modern principle is just-in-time access. ⏳
This is where the integrated power of Microsoft Entra comes into play, delivering a secure yet seamless experience through three core services.
Let’s revisit Sarah’s situation, but this time with our new solution in place.
- Sarah tries to access ChatGPT and is initially blocked by a global policy.
- Sarah navigates to the My Access Portal, finds an Access Package named “Just-in-Time ChatGPT Access,” and clicks “Request.”
- Her manager receives an approval request, reviews the justification, and approves it.
- Instantly, Sarah is added to a security group that grants her access to ChatGPT. Crucially, this access is time-bound. It will automatically expire in 2 hours, perfect for completing her task.
- Sarah can now access ChatGPT seamlessly through her corporate device! This helps her stay productive while maintaining compliance.
How to Grant Just-In-Time Access to Authorized AI Apps in Microsoft 365
Let’s see how to set this up!
- Create web content filtering policy to block all AI apps
- Allow only ChatGPT in web content filtering policies
- Use Conditional Access to allow selected users to access ChatGPT
- Set up access package to allow just-in-time ChatGPT access
Before configuring time-bound access, ensure the following requirements are met:
✅ Users must have a Microsoft Entra joined or Microsoft Entra hybrid joined device.
✅ Have a Microsoft Entra Suite license to install and configure Global Secure Access (GSA).
✅ Alternatively, you can activate a Microsoft Entra trial subscription to explore the features.
✅ Hold the Global Secure Access Administrator role to configure GSA settings and manage Security Profiles.
✅ Hold the Conditional Access Administrator role to enforce Conditional Access policies for AI security controls on end user devices.
1. Configure Web Content Filtering Policy to Block All AI Apps
The first crucial step involves creating a secure baseline by blocking access to all Generative AI platforms. This proactive measure prevents uncontrolled usage while the governed access framework is being implemented.
Important: To make the web content filtering policies for Microsoft Entra Internet access work, you must need to do the following:
- Install the Global Secure Access (GSA) client on devices targeted for site blocking, which acts as the foundation for enforcing security profiles.
- Enable internet access traffic forwarding profile in Microsoft Entra for your tenant. After enabling it, you must scope all users and groups.
Create a Web Content Filtering Policy to Block All AI Platform:
Create a web content filtering policy to prohibit access to all Generative AI websites.
- Navigate to Global Secure Access from the Microsoft Entra admin center.
- Click “Web content filtering policies” from the Secure dropdown.
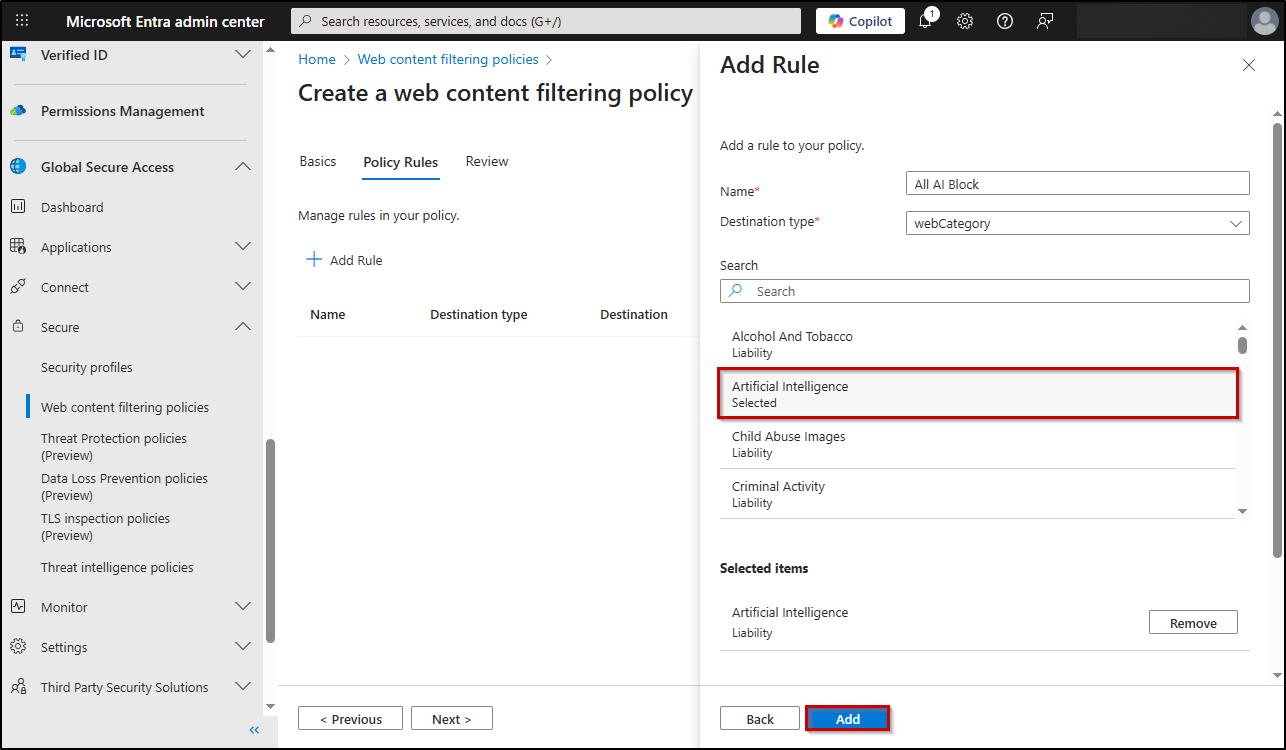
- Click on +Create policy, then give a suitable name & description for it and select “Block” in Action dropdown.
- After that, click “Next” and select +Add rule. Give a name to your policy ‘AI Block’ in this case.
- In the “Destination Type” field, choose webCategory, select Artificial Intelligence, and click Add.
- Finally, click Create Policy to save your web content filtering policy.
Link the ‘Blocking All AI Site’ Filtering Policy to Baseline Profile:
Apply the blocking policy to all users by associating it with the default security profile.
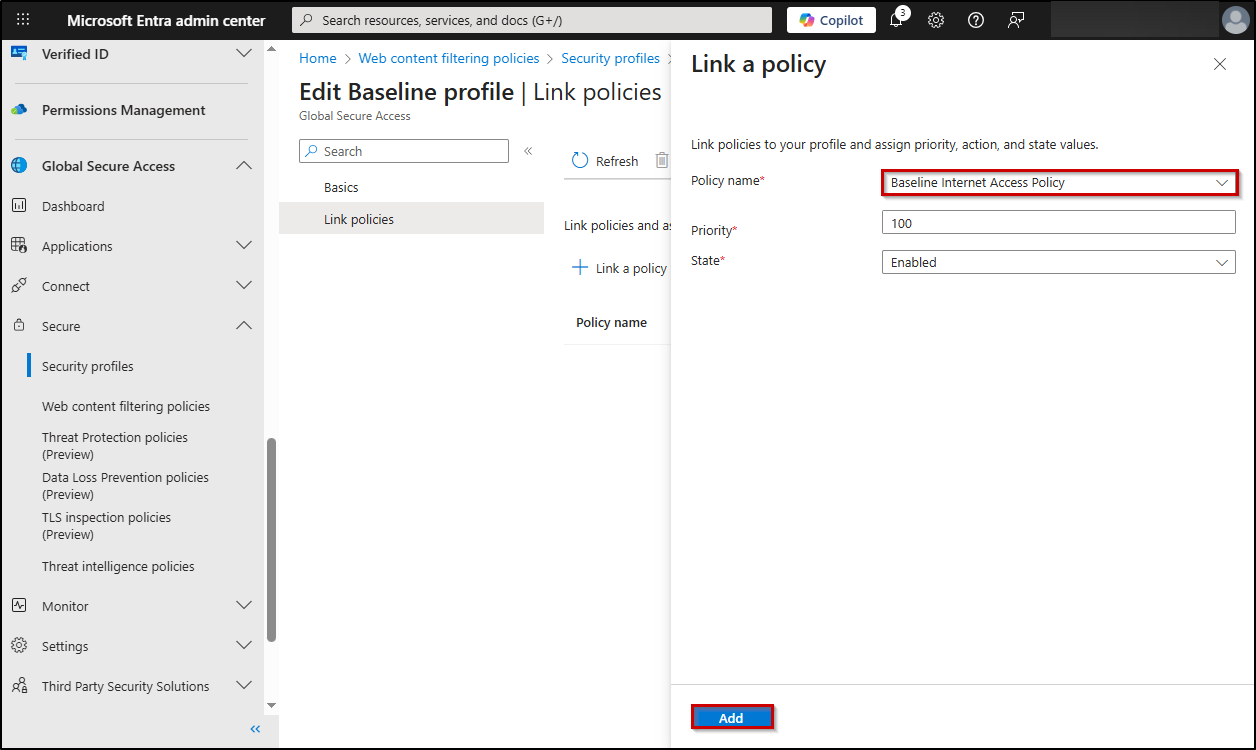
- Navigate to Global Secure Access –> Secure –> Security profiles –> Baseline Profile –> Edit profile.
- Enter a suitable Profile name, set the State to Enabled, and keep the Priority at the default value of 65000.
- In the “Link policies” tab and click + Link a policy → Existing web filtering policy.
- From the Policy name drop-down menu, select the web content filtering policy you have created above, and click Add.
This configuration establishes a secure default state where all users are automatically blocked from accessing Generative AI platforms.
2. Allow ChatGPT in Web Content Filtering Policies
With the foundational block policy in place, the next step involves creating precisely scoped exceptions for approved AI applications.
Create Web Content Filtering Policy to Allow ChatGPT Access:
Create a targeted web filtering exception to permit access to the approved ChatGPT service.
- Expand the Global Secure Access section in the Entra admin center.
- Click Secure and select Web content filtering policies.
- Click Create policy, then provide a name and description for it.
- In the “Action” dropdown, choose Allow and click Next.
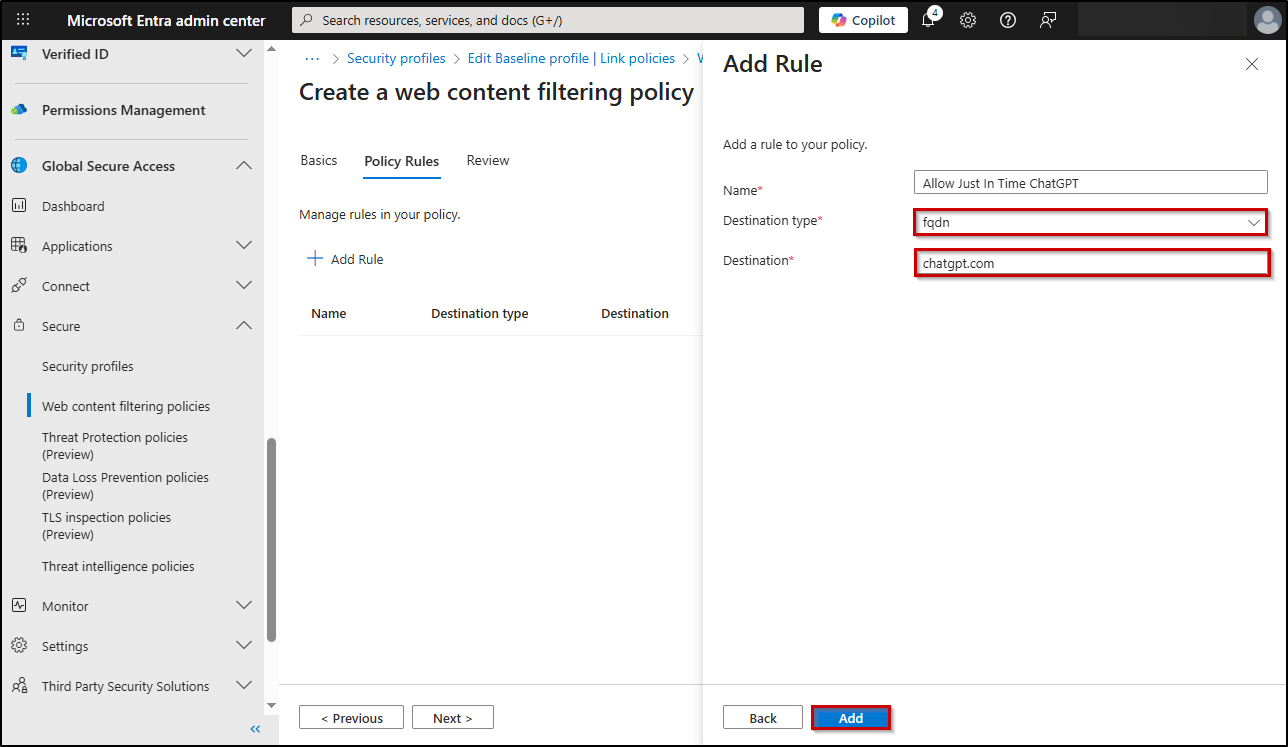
- Click “Next” and select +Add rule. Give the rule a Name.
- To allow specific AI domains, select fqdn in the “Destination Type” field, enter the domains (chatgpt.com) you want to allow, and click Add.
- Following the Next button, click Create Policy to save your web content filtering policy.
Unlike ChatGPT and other Gen AI platforms, web content filtering cannot be applied to Microsoft 365 Copilot Chat. Since Copilot is deeply integrated with the Microsoft 365 ecosystem, applying network-level restrictions may lead to unpredictable behaviour or even disrupt access to M365 apps.
Therefore, to prevent oversharing, Copilot access should be managed through CA policies, ensuring that only trusted users or specific groups can interact with it.
Link ‘Allow ChatGPT’ Filtering Policy to Security Profile:
Assign the allow ChatGPT web filtering policy to a dedicated security profile.
- Navigate to Global Secure Access → Secure → Security profiles and create a new security profile by clicking + Create profile.
- Enter security profile a suitable name, leave state and priority as 100.
- In the “Link policies” tab and click + Link a policy → Existing web filtering policy.
- From the drop-down menu, select web content filtering policy you have created above, give priority 100 and click Add.
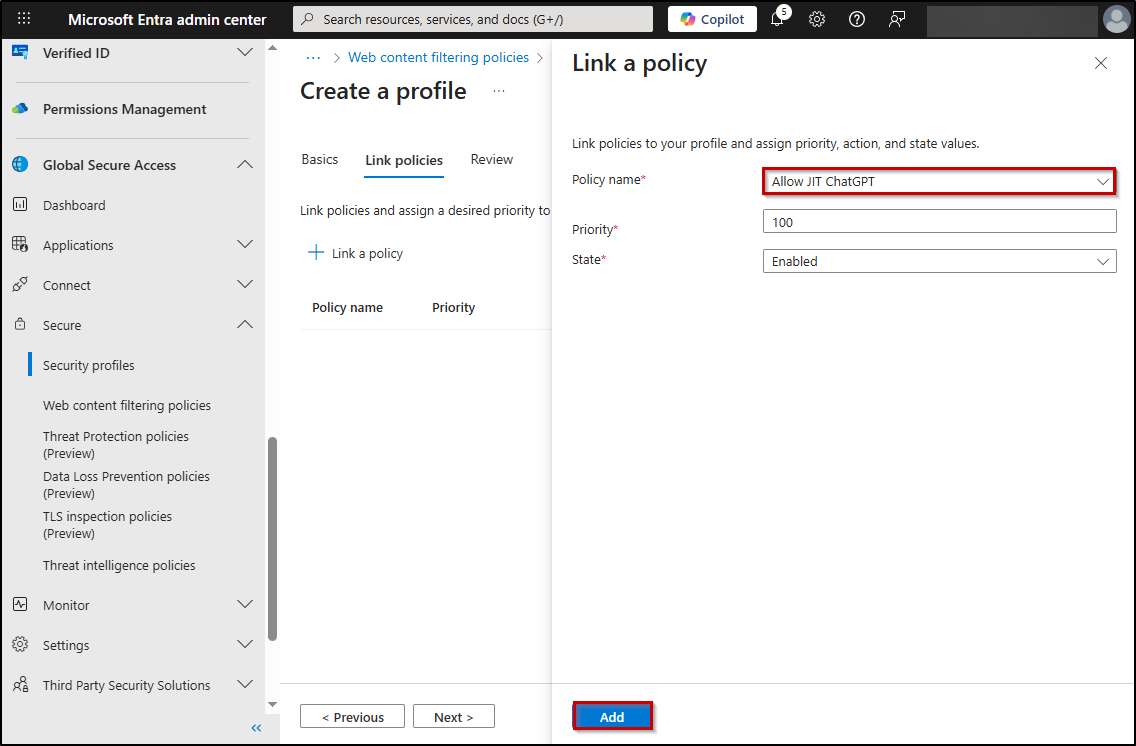
The dedicated security profile serves as a carefully controlled exception pathway, ensuring ChatGPT access is only permitted when triggered by the Entra entitlement management system.
3. Enforce ‘Allow ChatGPT’ Security Profile with a Conditional Access Policy
Now that you’ve created the security profile to allow ChatGPT access, the next step is to enforce it using a Conditional Access policy. By default, Global Secure Access applies a baseline security profile to all users and traffic. While this ensures broad protection, it doesn’t differentiate between everyday access and governed, time-bound AI access.
To grant controlled access only to approved users and sessions, you must create a Conditional Access policy. This policy links your custom security profile to specific users or groups, ensuring that only authorized users can access ChatGPT.
- Navigate to Microsoft Entra admin center > Entra ID > Conditional Access.
- Click +Create new policy and enter a name for the policy.
- Under ‘Users’, include a security group.
Hint: In this case, I am including an empty security group named “Allow ChatGPT Access”. Make sure the group is empty; otherwise, users may gain ChatGPT access without going through the access package request process.
- In ‘Target resources’, select All internet resources with Global Secure Access under Include.
- Under ‘Conditions’, you can set Sign-in Risks to be low.
- Under ‘Session’, check the Use Global Secure Access security profile option.
- From the dropdown, choose the security profile “Allow Just-in-time ChatGPT Access” you created in the previous step and click Select.
- Finally, set Enable policy to On, and click Create to enable the web content filtering enforcement that allows access for ChatGPT.
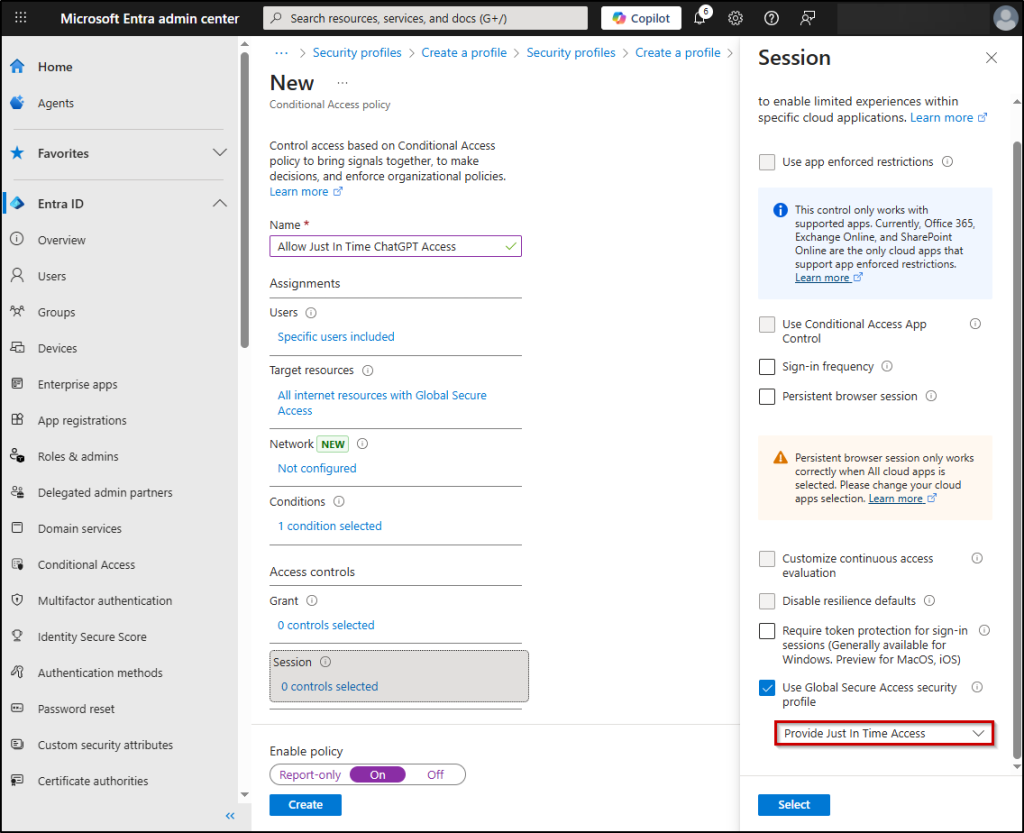
This step bridges the gap between identity governance and network-level security, ensuring the right users gain access under the right conditions.
Note: Changes in Conditional Access for web content filtering take effect in about 1 hour.
4. Set Up Access Package to Implement Just-in-time ChatGPT Access
Next step is to create an access package that grants user access to the security group added above in the CA policy for a specific duration.
Name Your Access Package and Add Resource Roles:
- Sign in to the Microsoft Entra admin center as at least an Identity Governance administrator.
- Navigate to ID Governance –> Entitlement management –> Access packages. Click on ‘+New access package’.
- On the ‘Basics’ tab, name your access package (Allow Just-in-time ChatGPT) and provide a description.
- In the ‘Catalog’ dropdown, select the desired catalog in which you want to include the access package.
- Select the ‘Next: Resource roles’ button.
- Click on ‘+ Groups and Teams’ and choose the group to whom you want to provide ChatGPT access from the list. (In this case, its “Allow ChatGPT Access” security group)
- Then, you should specify the role for each added resource by clicking on the ‘Select role’ dropdown and choosing the desired role as per your requirements.
- Select the ‘Next: Requests’ button.
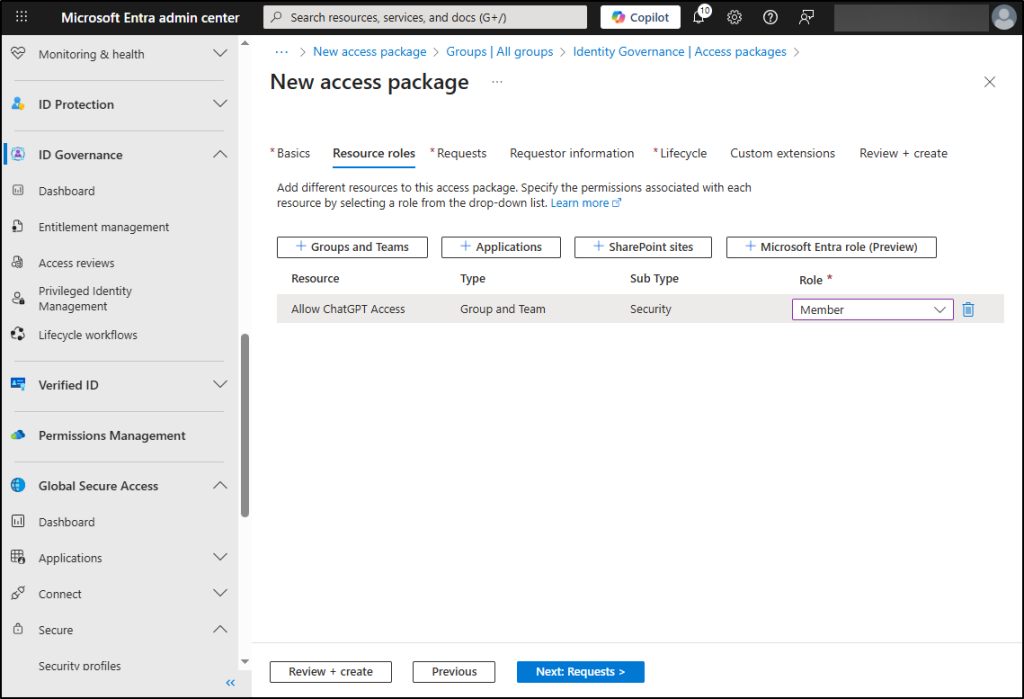
Specify Access Package Request and Approval:
9. On the ‘Requests’ tab, choose the desired option under the ‘Users who can request access’ section. Select ‘For users in your directory’ to allow all users in your organization to request this access package.
10. Then, you will have the option to select specific users, all users excluding guests, or including guests. I selected Finance Team to allow only its members to request this access package.
11. You can configure up to 3 stages of approvers and choose the number of stages required. By default, it will be 1. For our use case, we proceed with the single stage review.
12. Under the ‘First Approver’ section, you can choose either managers, specific users, or sponsors as approvers.
13. Specify the number of days (maximum of 14 days) within which the approver should act on the access package request. If no action is taken within that period, the request will be automatically rejected.
14. The ‘Require approver justification’ will be set to ‘Yes’ by default. You can also choose ‘No’ if the approver justification is not required
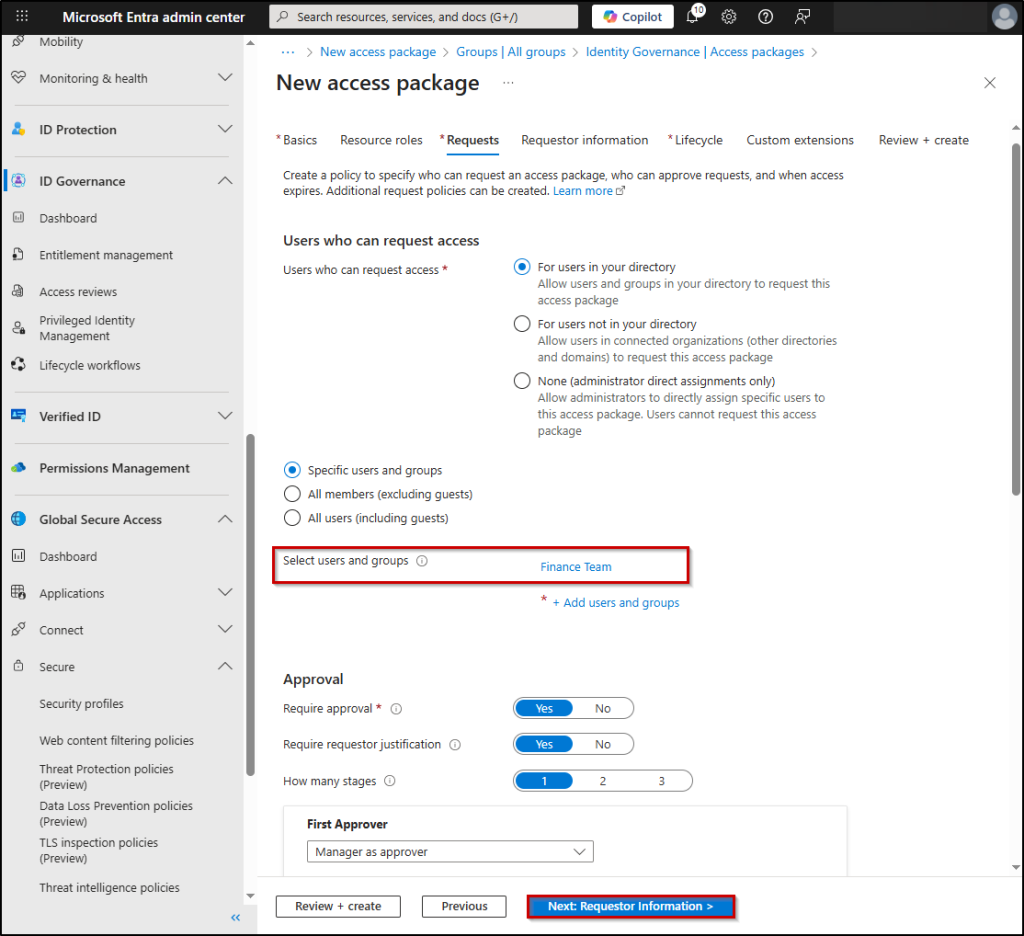
15. Select the ‘Next: Requestor Information’ button. Here, you can configure custom questions and response formats to help approvers validate requests.
Determine Access Package Expiration in the Lifecycle Setting:
16. After adding the required ‘Requestor Info’, select the ‘Next: Lifecycle’ button.
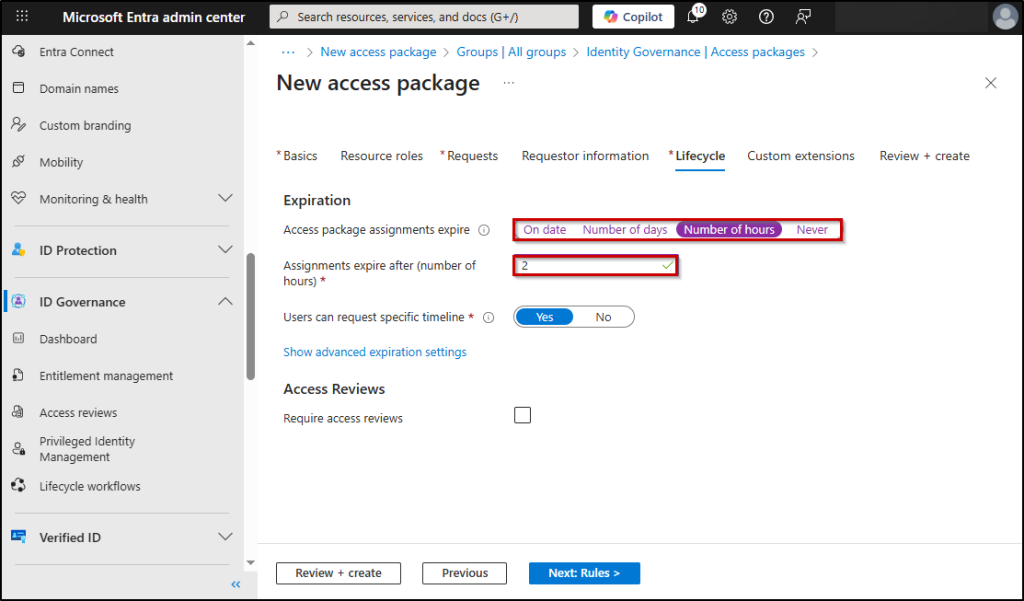
17. On the ‘Lifecycle’ tab, we have to specify whether the access package assignments should expire, when they should expire, whether users can request access for specific timelines.
18. In ‘Access package assignments expire’ field, specify a time span to provide Just-in-time access to ChatGPT, I am specifying 2 hours by choosing Number of hours setting.
19. Set ‘Users can request specific timeline’ is set to No.
20. Then, you can configure whether the access reviews are required or not under the ‘Access Reviews’ section. Choose ‘Yes’ or ‘No’ as per your wish.
21. Select the ‘Next: Rules’ button.
22. Select the ‘Next: Review + create’ button.
23. As the final step, verify all the settings are specified properly in the access package and click on ‘Create’ to create a new access package in Microsoft Entra entitlement management!
This Access Package implementation creates a comprehensive governance workflow that:
- Provides a self-service portal for legitimate AI access requests.
- Enforces business justification and managerial approval processes.
- Automatically assigns approved users to the security group that triggers Conditional Access policies.
- Guarantees automatic access revocation after the predetermined 2-hour window.
End User Experience: Requesting Temporary Access to AI Tools
Before initiating any access request, All Generative AI platforms, including ChatGPT, remain blocked by the foundational web content filtering policy.
Now, users like Sarah can easily request temporary access to authorized AI applications like ChatGPT. Here’s how:
How to Request Access to Approved AI Tools Using Entra Entitlement Management
This is how a user request AI access through access packages in Microsoft 365.
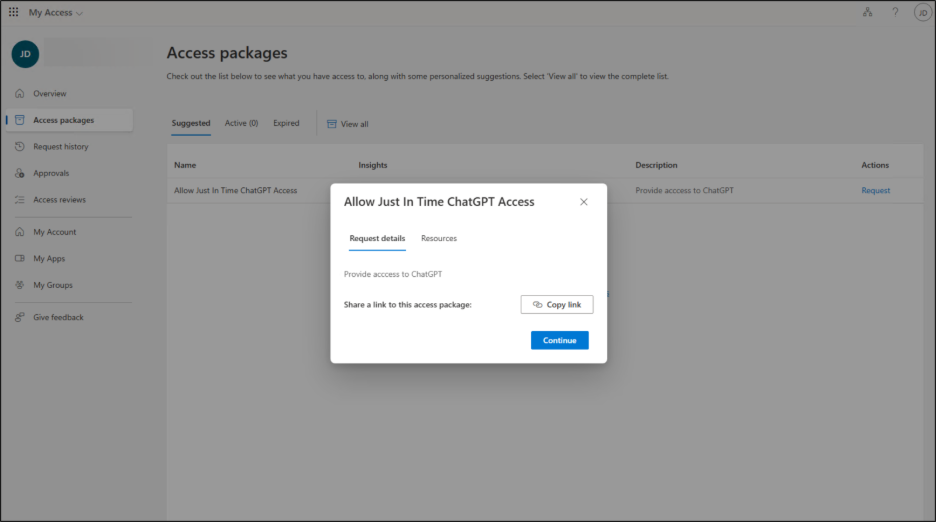
- Navigate to My Access Overview portal –> Access Packages —> View all tab in Microsoft 365.
- Select Request button on the Access Package that allows ChatGPT.
- Click on Continue.
- Provide the justification on why you need to access ChatGPT and click Submit.
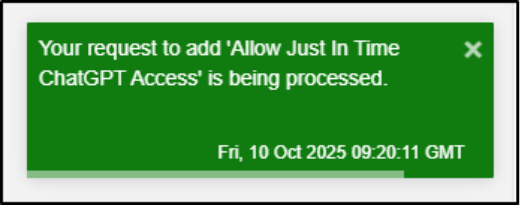
Upon approval, the system automatically grants Sarah access to ChatGPT. This is typically done by adding her to a security group that is allowed through the web filter.
Sarah now navigates to ChatGPT in her browser. The site is unblocked, and she can use it for her task. Crucially, this access is granted for a limited time only (2 hours) as specified in the Access Package policy.
Note: There can be a short propagation delay (a few minutes) for the access permission to sync across systems.
This end-to-end journey demonstrates how Sarah, and users like her, can leverage powerful AI tools safely and efficiently, turning potential security risks into governed productivity gains!
The goal of cybersecurity is not to build impenetrable walls that hinder your team, but to create smart, flexible gates that open under the right conditions. By combining Microsoft Entra Access Packages with Conditional Access and Global Secure Access, you can replace a frustrating “block” with governed access. Stay tuned for more insights in our Cybersecurity Awareness Month blog series!