On Day 20 of Cybersecurity Awareness Month, learn how to deploy honeypot accounts in on-premises Active Directory to shine a light on attackers in the act. Stay tuned for upcoming blogs in our ongoing Cybersecurity blog series to fortify your security posture.
When securing your Active Directory environment, timing is everything. The earlier you spot suspicious activity, the faster you can catch attackers red-handed before they escalate privileges or move laterally. While monitoring real user accounts is essential, it often produces so many routine events that critical threats can get lost in the noise. This noise makes it easier for stealthy techniques like credential dumping, Kerberoasting, or service account abuse to slip through unnoticed.
That’s where deploying honeypot accounts comes in, helping you spot unauthorized access attempts early, before real damage occurs. These are fake accounts that look real but are actually highly monitored traps. Because no legitimate user should ever log into them, any interaction with them is a near-certain sign of malicious activity.
This helps you detect unauthorized access attempts to your Active Directory, and gain actionable intelligence, all without sorting through noisy logs from real accounts. In this blog, we’ll walk you through how to create honeypot accounts in Active Directory to distract attackers and get valuable insights to protect your organization more effectively.
What is an Active Directory Honeypot Account?
A honeypot account is essentially a decoy user account in Active Directory designed to catch the eye of attackers during their information gathering phase. In this phase, attackers explore the domain to map accounts, their privileges, and potential entry points before attempting to perform attacks.
Honeypot accounts are created to stand out during this search, appearing to be a high-privilege or frequently used service account. However, they are intentionally configured with no real access or functionality and serve purely as detection mechanisms.
By placing these accounts strategically, security teams can detect suspicious activity and analyze potential threats. They also help distract attackers without disrupting normal operations.
How to Create Honeypot Accounts in Active Directory
The goal is to make honey users look legitimate, as if they belong to critical services, without giving away that they’re traps. If a honeypot account appears too obviously fake, attackers may easily identify it. But if it’s too real, it could pose a security vulnerability. The challenge lies in striking the right balance: making the account convincing enough to attract attention, while ensuring it remains harmless to our organization.
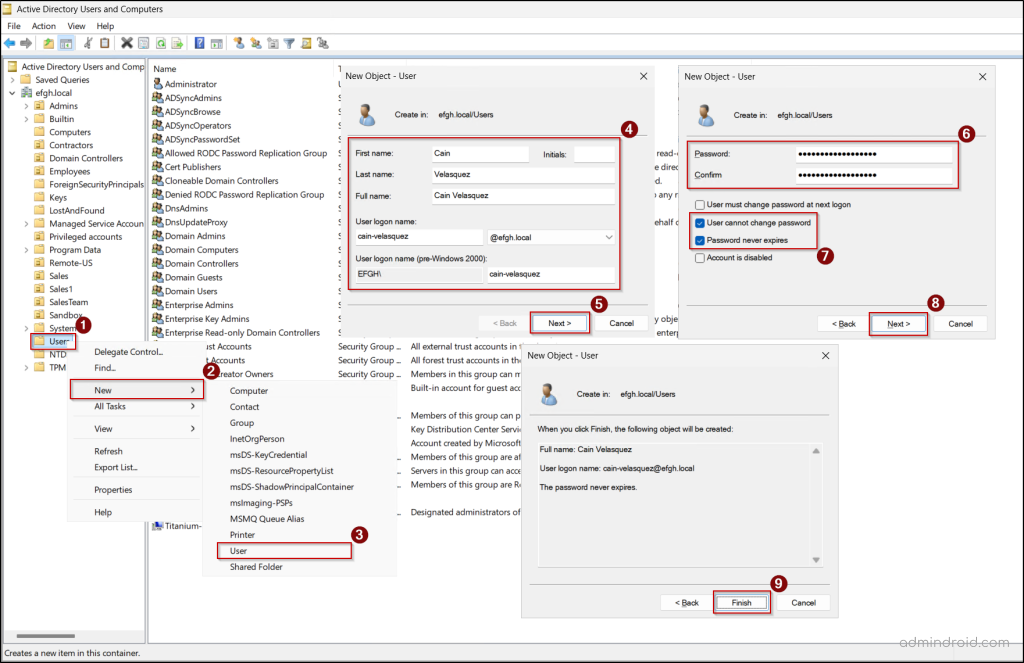
Let’s see the steps to create a honeypot user in Active Directory.
- Open Server Manager in the Active Directory domain controller.
- Navigate to Tools and select Active Directory Users and Computers.
- Then, right-click on the desired OU or container, where attackers are likely to search for privileged accounts, and select New → User.
- Enter the realistic Full name and the User logon name that blends in and click Next.
- Set a strong, unique password for the account that you must not use or document elsewhere.
- To keep security and realism, select the following check-box options.
- User cannot change password
- Password never expires
- Click Next, verify the honey user’s details, and select Finish.
Assign Group Membership and Logon Restrictions for Honeypot Accounts
Now, we’ve created a honeypot user account. Next, we’re going to take the most important step for safety and ensure the account is useless to an attacker even if they compromise the password.
- Group Membership:
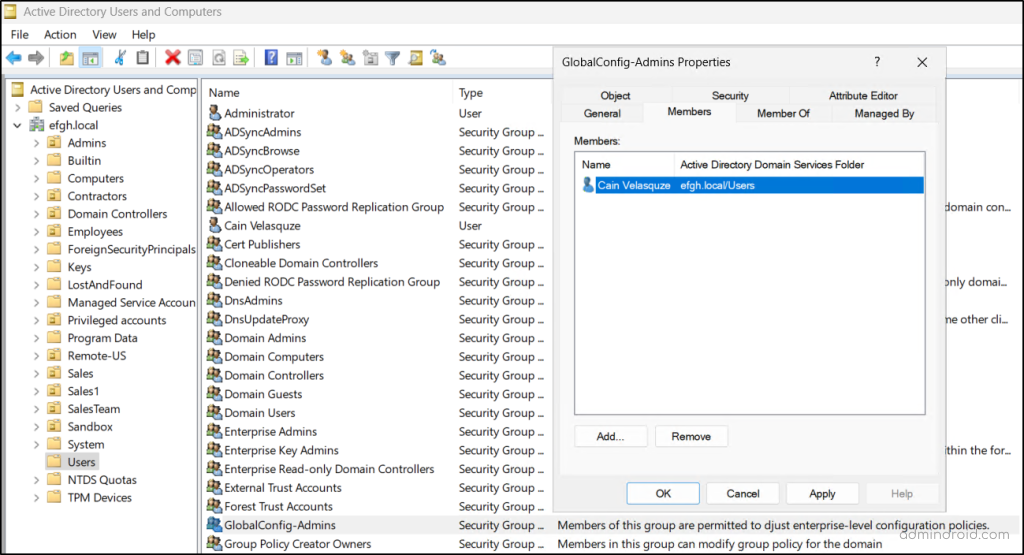
- Groups are the heart of access management in Active Directory. Therefore, providing honey user membership in attractive groups will distract the attackers.
- So, add the honey account to one or more attractive, but functionally empty, security groups.
- Restrict Logon Hours and Log On To:
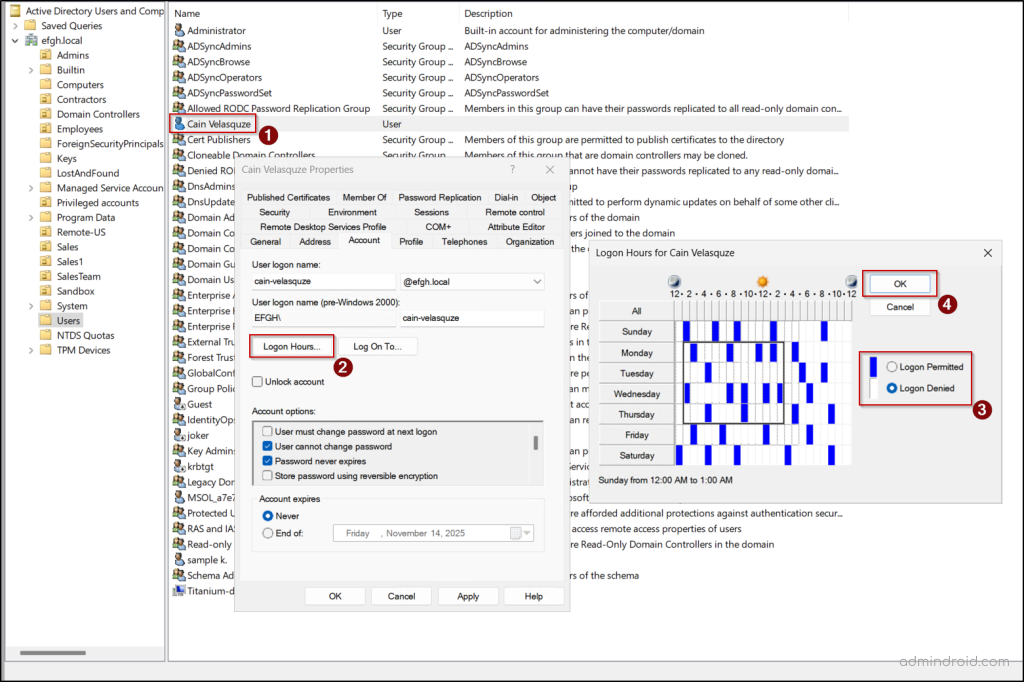
To fail any login attempt to the honey accounts, you can deny all logon access.- Right-click the honey account and go to Properties > Account tab > Logon Hours…
- Select the minimum logon hours in the grid to mimic the actual user account, click the Logon Denied checkbox, and hit OK.
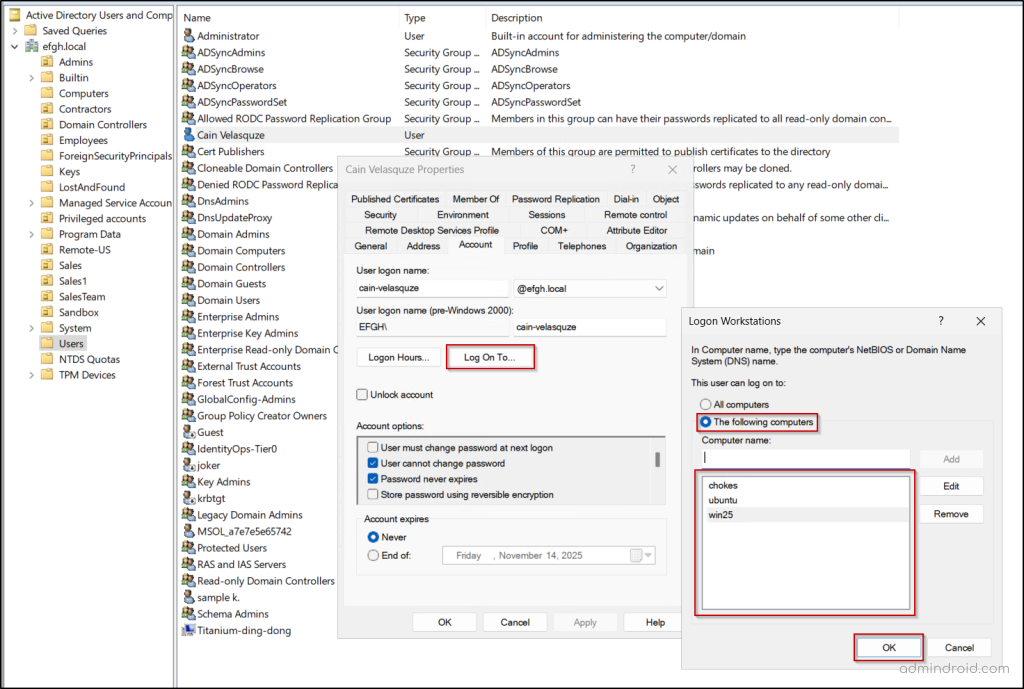
- Click Log On To.. and choose ‘The following computers’ option.
- Add the name of a non-existent locked-down host, make the host name realistic so the decoy appears authentic, and then click OK.
- Finally, select Apply and OK from the honey user’s properties window.
Audit Activities on Active Directory Honey Accounts
With the honeypot account deployed, the focus shifts to detection. Any interactions with this account have zero tolerance. Whether it’s a failed logon or a simple property read, it signals that an attacker is active in your environment.
Let’s see how to monitor the interactions with a honey user account in Active Directory.
Configure Logon Auditing via GPO
You can use the Advanced Audit Policy Configuration to precisely target the necessary events on your Domain Controllers.
- Open the Group Policy Management console by navigating to Server Manager → Tools.
- Right-click the Default Domain Policy or the GPO linked to the specific OU where the honeypot account exists and select Edit.
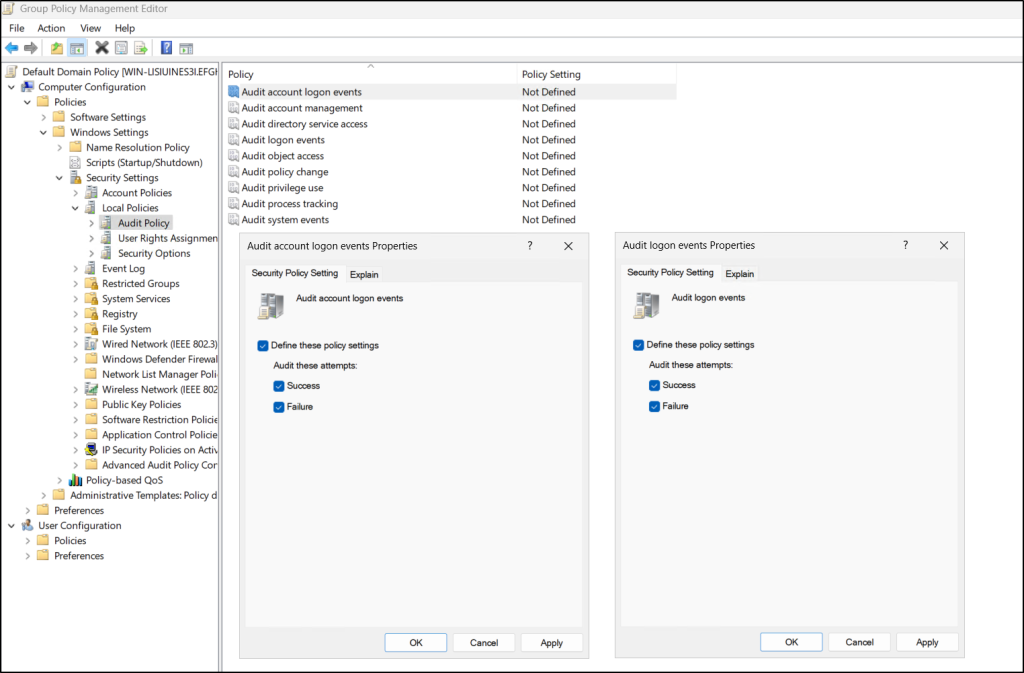
- In the Group Policy Management Editor, navigate to Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Audit Policy.
- Double-click Audit account logon events, select the “Define these policy settings” checkbox, and choose both Success and Failure. Then click OK.
- Repeat the above step for the Audit logon events policy. Close the GPME and run the gpupdate /force cmdlet in PowerShell on your domain controllers to apply the new security settings.
Configure Object-Level Auditing for Reconnaissance
Follow this step to detect attackers early in their information gathering phase. Even if someone only tries to view the honeypot account details, the action is recorded as a security event.
- In Active Directory Users and Computers (ADUC), go to View → Advanced Features.
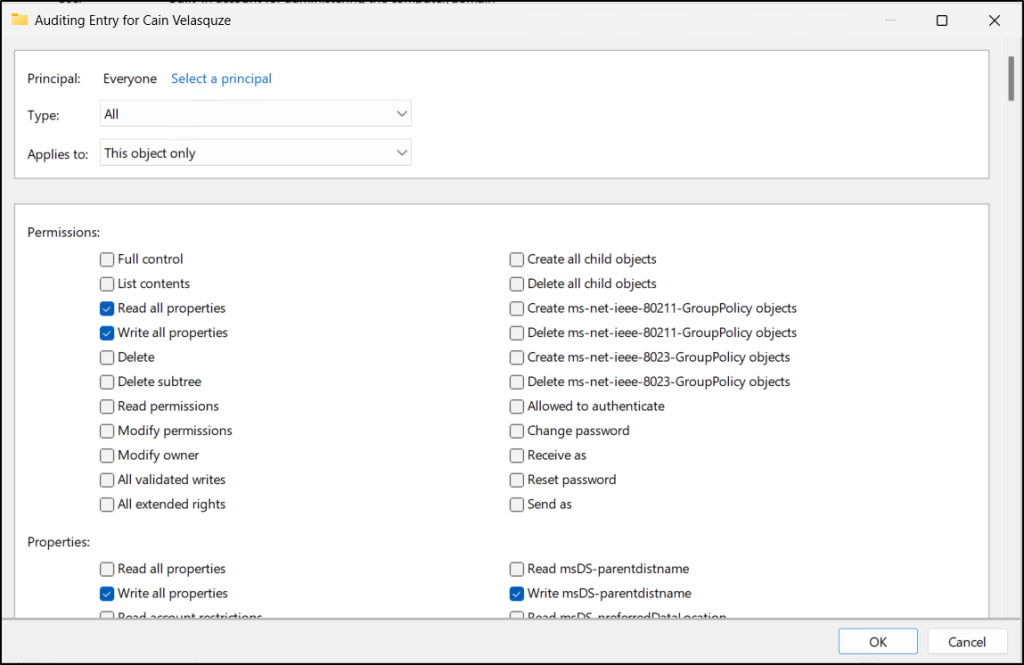
- Right-click the honeypot account, select Properties, and switch to the Security tab.
- Then, click Advanced and open the Auditing tab, then select Add.
- In the audit entry dialog, click Select a principal, enter Everyone in the “Enter object name to select (examples)” field, and click OK.
- Next, in the Type dropdown, select All and choose “This object only” under Applies to dropdown.
- Select the following permissions under Permissions.
- Read all properties
- Write all properties
- Click OK, click Apply to save audit entry. Then, click OK twice more to save the changes for the honey account.
Check Event Viewer for Honey User Logon Failures
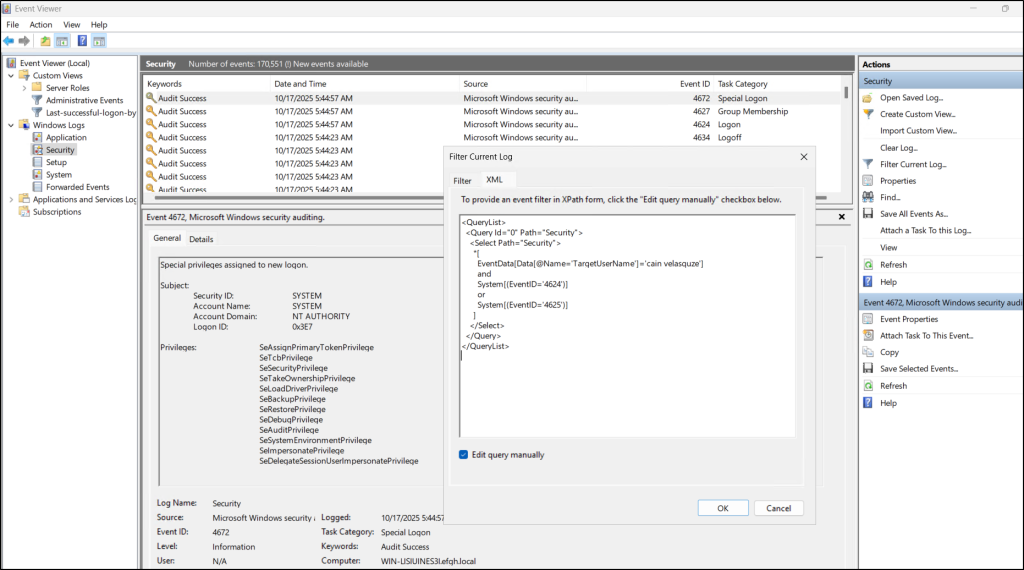
You can search for a failed and successful logon attempt (Event ID 4624 & 4625) on your honeypot user account directly in the Security Log.
- Open Event Viewer on a domain controller and navigate to Windows Logs → Security.
- Click Filter Current Log… in the Actions pane and switch to the XML tab.
- Check the box for “Edit query manually” and click Yes in the prompt.
- Paste the XML query below, replacing <HoneyAccountName> with your actual honeypot user account name, and click OK.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
<QueryList> <Query Id="0" Path="Security"> <Select Path="Security"> *[ EventData[Data[@Name='TargetUserName']='<HoneyAccountName>'] and System[(EventID='4624')] or System[(EventID='4625')] ] </Select> </Query> </QueryList> |
This will list the login failure events of the honeypot user account that help you find the attackers trying to intrude into your AD.
Active Directory Honeypot Account Best Practices
Here are some best practices you can follow to create more attractive and secure Active Directory honeypot accounts.
Use believable names and profiles: Follow your organization’s naming patterns and profile conventions (e.g., initials + surname). Avoid obvious placeholders such as test1 or fake users.
Mimic normal profile details: Populate description, job title, department, manager, phone number, and other attributes, so the account appears like a real employee.
Age the accounts: When possible, reuse or restore old, long-existing accounts rather than creating brand-new ones. This is because older accounts look more credible.
Avoid actual elevated rights: Ensure the honey account cannot perform sensitive operations. The goal is deception, not risk.
Test safely in an AD lab: Before deploying honeypot accounts in production, test their configurations and detection rules in an Active Directory test environment. This helps ensure the accounts behave as intended, trigger alerts properly, and introduce no unintended access or operational risks.
Create decoy resources: Associate the account with fake documents or directories that look sensitive (project plans, financial spreadsheets) but contain no real data.
Place accounts across the environment: Populate honey accounts in different domains, OUs, or service areas to increase coverage of likely attack paths. Additionally, you can assign honeypot users to multiple groups to increase the likelihood of catching an attacker’s interest.
Vary roles and apparent functions: Make some honey accounts resemble admins, others service accounts, and some standard users to attract different attacker behaviors.
Periodic activity: Schedule safe automated actions (e.g., scripted logins or file accesses), so accounts don’t look permanently dormant.
Refresh details regularly: Update profile information, permissions, and associated decoy data on a schedule, so the accounts remain plausible.
Instrument for detection: Monitor account activity closely and review logons, privilege changes, or attempts to access decoy resources for early signs of compromise.
In conclusion, honeypot accounts are a powerful yet low-cost way to strengthen your organization’s security posture. When designed to look genuine and strategically placed across your environment, they act as early warning systems, exposing unauthorized access attempts before real damage occurs. Ultimately, well-crafted honeypot accounts don’t just trap attackers. They provide valuable insights into attacker TTPs, helping you fine-tune defenses and stay one step ahead of adversaries.
We’re only on the 20th day of Cybersecurity Awareness Month, and there’s still halfway to go! Stay tuned for more insights on our upcoming cybersecurity blogs. We hope this blog helps you get started with honeypot accounts in Active Directory. Thanks for reading. For more queries, feel free to reach us through the comments section.