On Day 19 of the cybersecurity awareness month, learn about the Microsoft Entra ID Protection dashboard to analyze the security exposure of organizations better. Stay tuned for more blogs in the M365 Cybersecurity blog series.
In the rapidly changing digital environment of today, standard security measures are not enough to protect an organization’s identity. It is essential to have a robust security system in place to defend against evolving identity attacks in Microsoft 365. This is where the Microsoft Entra ID Protection Dashboard comes into play, which is currently generally available. It is an innovative feature that not only detects identity attacks but also helps you monitor risky sign-ins and strengthen your overall security. 💯 In this blog, let’s explore the compelling features of the Microsoft Entra ID Protection dashboard, providing you with insights into how it can benefit you.
In the world of technology, we need to take security seriously because the risks are real.
– Jim Fowler
What is Entra ID Protection?
Microsoft Entra ID protection is like a security system that is aimed at assisting organizations in the identification, analysis, and resolution of identity-related vulnerabilities. Moreover, the data gathered from these identity-based risk assessments can be integrated into various security tools, including Conditional Access systems and Security Information & Event Management (SIEM). This collaboration enhances the organization’s capacity to conduct more in-depth investigations, correlate data, and strengthen its overall security framework. 🚀
What is the Purpose of the Microsoft Entra ID Protection Dashboard?
Microsoft Entra ID Protection dashboard helps safeguard your organization by tracking and investigating risks, setting up access policies, and even automatically fixing issues. It aims to assist IT administrators in enhancing defenses against cyber threats. This dashboard empowers organizations with tailored insights and actionable recommendations, providing a clear view of your security posture. 📊
License Requirements to Access Entra ID Protection Dashboard
Before you dive into the features and capabilities of this dashboard, there are a few prerequisites that you need to meet:
- You must have either Microsoft Entra ID Free, P1, or P2 licenses.
- Users accessing the dashboard must have at least the Security Reader role assigned.
- To access a comprehensive list of recommendations and carry out the suggested actions, a Microsoft Entra ID P2 license is required.
Where to Find Microsoft Entra ID Protection Dashboard?
Once you’ve met the prerequisites, follow the steps below to access the dashboard.
- Sign in to the Microsoft Entra admin center.
- Browse to Protection > Identity Protection > Dashboard (Preview).
What is Included in the Microsoft Entra ID Protection Dashboard?
The Microsoft Entra ID Protection dashboard compromises of,
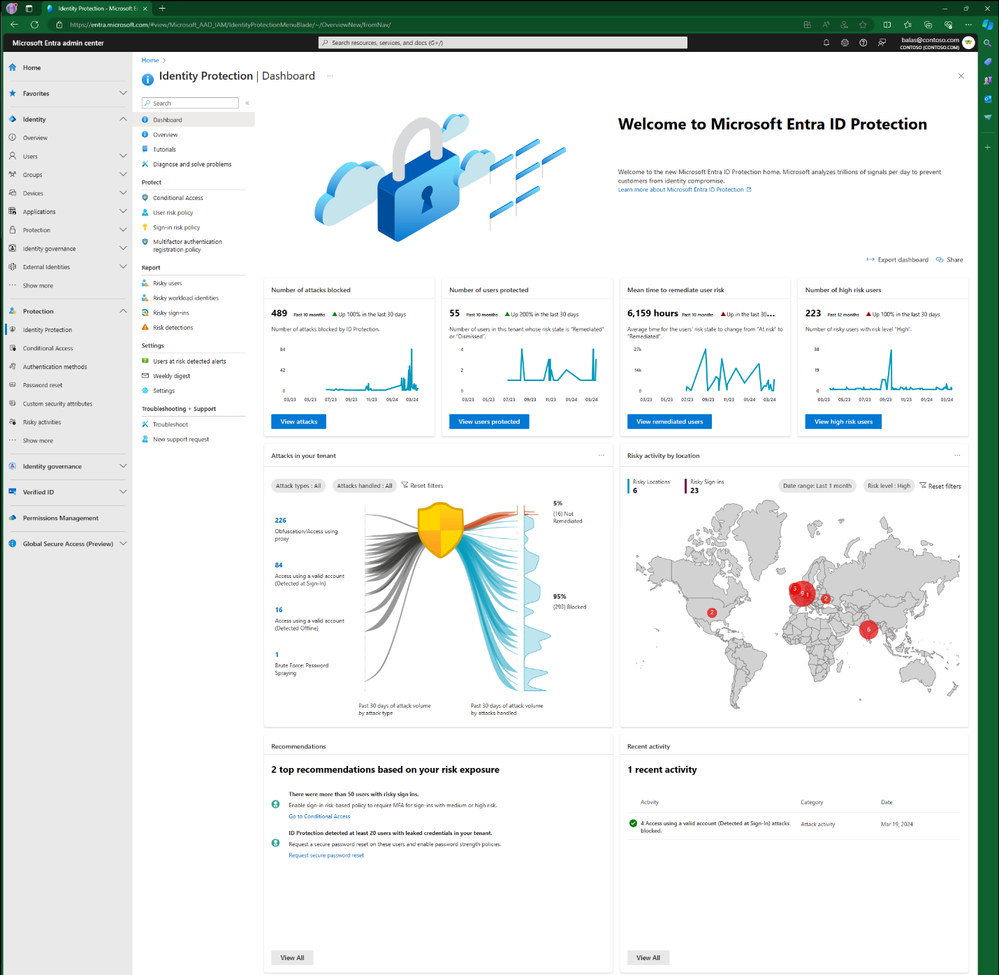
1. Metric Cards in Microsoft Entra
A tenant’s protection becomes more robust as you enhance your security measures, such as implementing risk-based policies. This dashboard provides four key metrics to help you evaluate the effectiveness of your security measures.
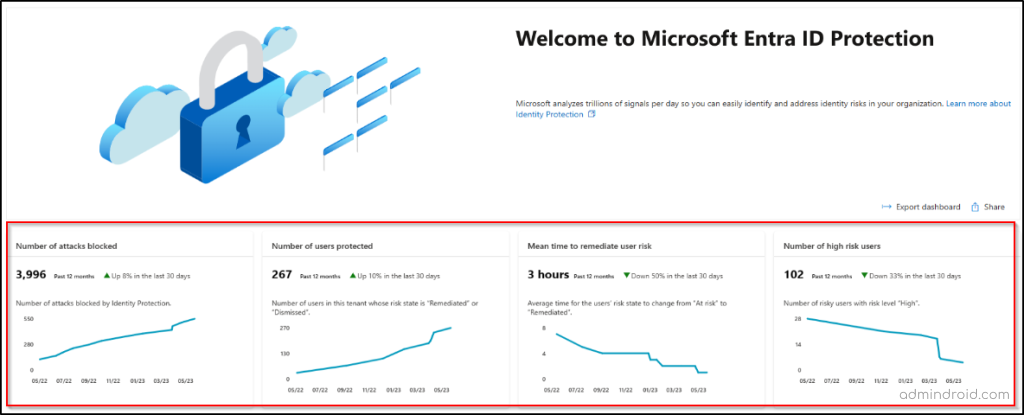
1. Number of attacks blocked – This metric tracks the number of attacks blocked for your tenant each day. An attack is considered blocked if a risky sign-in is interrupted by any access policy.
2. Number of users protected – This metric counts the number of users in your tenant whose risk state changed from ‘At risk’ to ‘Remediated’ or ‘Dismissed’ each day.
3. Mean time to remediate user risk – This metric measures the average time it takes for risky users in your tenant to change their risk state from ‘At risk’ to ‘Remediated’.
4. Number of high-risk users – This metric tracks the number of new risky users with a high-risk level detected each day.
These metrics are based on a rolling 12-month window of data that is refreshed every 24 hours.
2. Microsoft Entra ID Attack Graph
Microsoft Entra ID Protection introduces an innovative Attack Graphic to gain a better understanding of an organization’s risk exposure. This graphical representation showcases prevalent identity-based attack patterns discovered within your tenant. The attack counts in the Attack Graphic are now clickable, allowing you to easily investigate them in the Risk Detections report. This report includes a new column labeled ‘Attack type’, which highlights the main attack method using MITRE ATT&CK techniques for each detection.
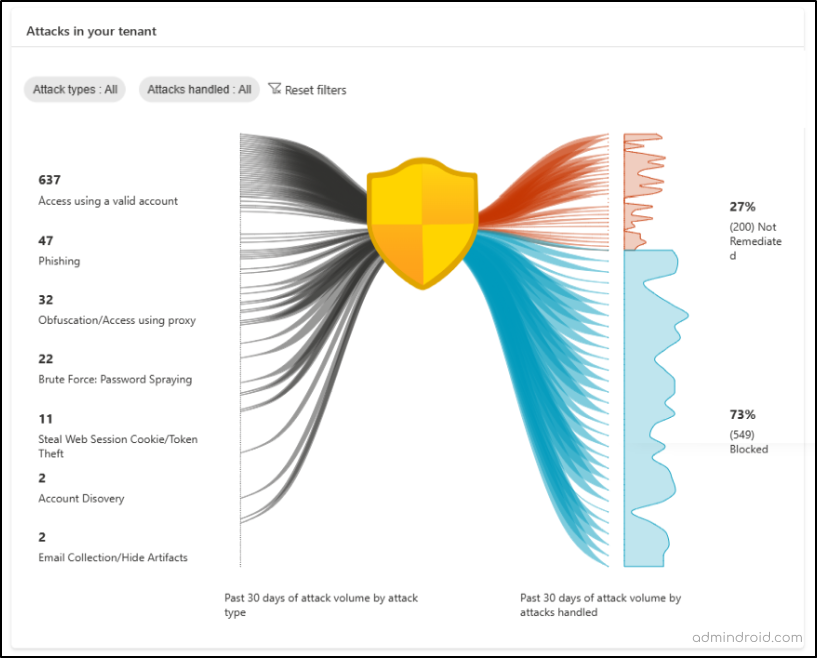
- Attack Graphic provides you with insights into the attack types impacting your organization over the past 30 days.
- The graphic displays two main pieces of information. On the left, it shows the number of each type of attack that has occurred. On the right, it shows how many of these attacks were blocked and how many were not yet fixed.
- An attack is considered “blocked” if it was stopped by a security measure, such as requiring a second form of authentication when signing in.
- If an attack was successful and not stopped, it is labeled as “not remediated.” This means it still needs to be fixed or “remediated.”
- You can use two filters on the graph to customize what you see:
Attack Types: This filter lets you focus on specific attack patterns.
Attacks Handled: This filter allows you to view either the attacks that were blocked or those that were not yet fixed separately.
3. Risky Activity by Location
A map is included in the dashboard to display the country location of risky sign-ins in your tenant. The bubble’s size indicates the extent of risk sign-ins at a specific location. When you hover over the bubble, a call-out box appears, displaying the country’s name and the count of risky sign-ins from that particular area.
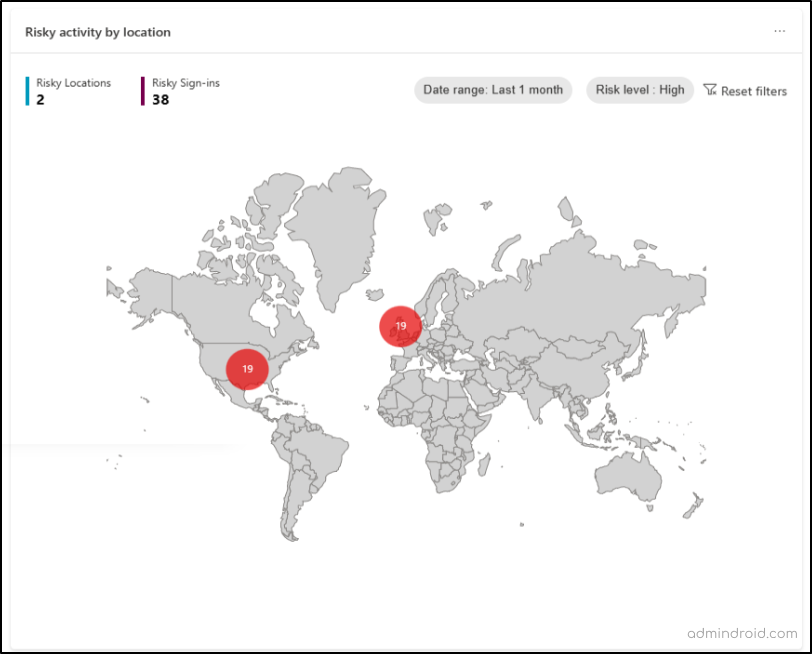
You can find the following filters in the map to keep track of risky sign-ins efficiently.
- Date Range – You can choose a specific period, like the last day, the last week, or the last month, and then the tool will show you the risky sign-ins that happened during that time.
- Risk Level – You can also select the level of risk associated with these sign-ins. You have options like “High,” “Medium,” and “Low.”
- Risky Locations Count – This tells you how many different places these risky sign-ins came from. It considers both the date range and risk level you selected.
- Risky Sign-Ins Count – This count shows you the total number of risky sign-ins that match the risk level and date range you selected.
4. Top Recommendations Based on Risk Exposures in Microsoft Entra
Microsoft Entra ID Protection offers recommendations based on the attacks detected in your tenant over the past 30 days. These recommendations guide your security staff with actions to take, enhancing your security posture.
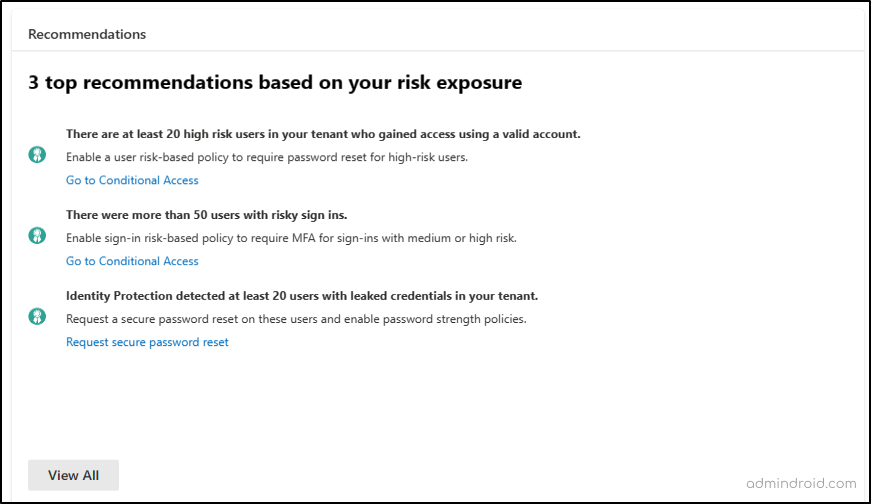
In the new dashboard, users find recommendations when there are specific attacks in their system. These recommendations give insights into the attack’s effects and offer direct links for fixing the issues. Customers with P2 licenses can access a comprehensive list of recommendations to gain further insights. Clicking “View All” opens a panel with additional recommendations generated based on the security incidents in your system.
5. Recent Activities in Microsoft Entra
The dashboard also keeps you informed about recent risk-related activities in your tenant. These activities may include attack activity, admin remediation activity, self-remediation activity, and the detection of new high-risk users.
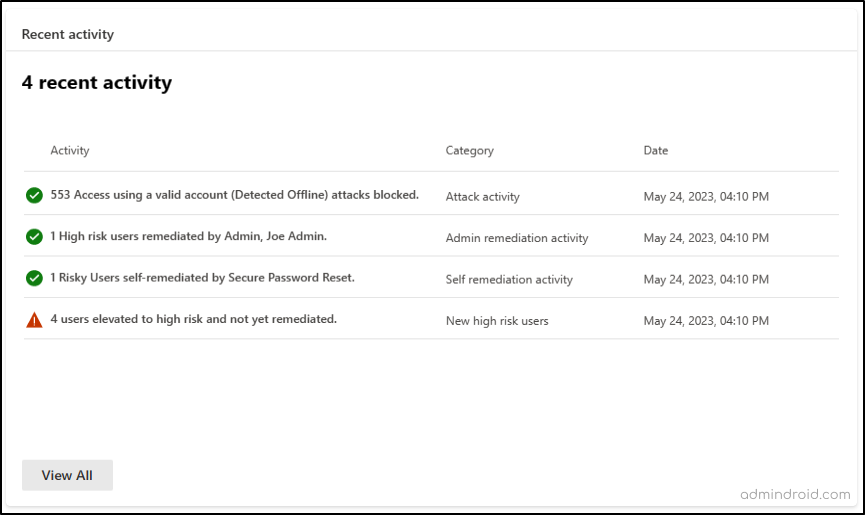
While the Microsoft Entra ID Protection Dashboard is packed with features, it’s essential to be aware of potential limitations. Depending on the configuration of your tenant, you may or may not see recommendations or recent activities.
Additionally, the Identity Threat Detection and Response (ITDR) dashboard in Microsoft Defender can be used to monitor identity related incidents, view ITDR health status, and analyze correlated threat signals to further strengthen your identity threat monitoring.
Final Thoughts:
In conclusion, the Microsoft Entra ID Protection dashboard brings a new level of control and insight to your organization’s security measures. It empowers you to detect, prevent, and remediate identity attacks effectively, ultimately fortifying your digital defenses.
While strengthening security, it’s equally important to address common Entra ID errors that can impact access and authentication.






