On Day 13 of Cybersecurity awareness month, learn to safeguard your Office 365 environment from phishing attacks by reviewing permissions granted to applications. Stay tuned for more blogs in the Office 365 Cybersecurity blog series.
In today’s rapidly advancing technology, users are no longer required to perform vital activities instead they can manage everything with applications. Users can easily handle files, calendars, and storage by granting required permissions to added applications. Once the app consent is granted, the application will manage, categorize and streamline users’ work without their help, and provide necessary statistics.
“The main element you cannot delegate to your cloud service provider is your responsibility for security, compliance and customer trust.”
– Stephane Nappo
That’s a fact! Some suspicious applications will additionally request crucial permissions and gain access to all organizational information. Therefore, Microsoft warns admins about consent grant attacks that surge so fast as users are unaware and careless.
Does Your O365 Tenant Use a Greater Number of OAuth Applications?
OAuth is a flexible gateway that grants third-party applications access to users’ data without requesting sensitive information. As it is the most ‘secure and simple delegated framework‘, it provides a seamless user experience, easier authentication and data authorization.
However, a few vulnerabilities of the OAuth framework can easily compromise critical data even though authentication methods like MFA have been configured in the O365 tenants.
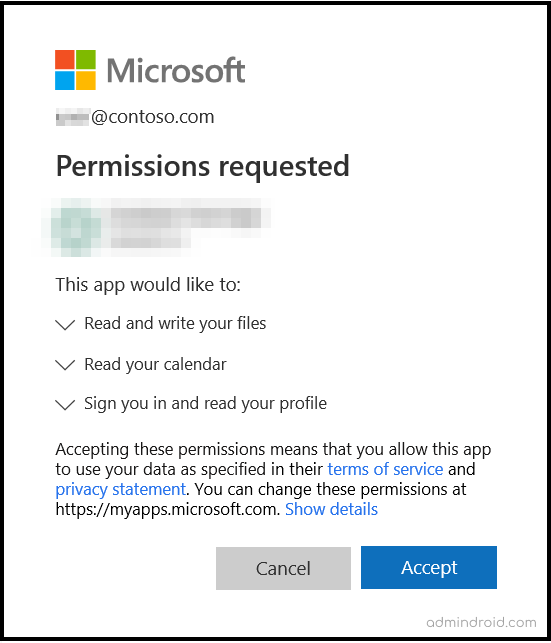
How to Manage Application Permissions in the Microsoft 365?
Since attackers follow different patterns to steal our confidential information, OAuth applications alone are not vulnerable to our enterprise. Any applications that are added to Office 365 may compromise security and exploit compliance standards.
Therefore, we came up with a solution to manage the application permissions effectively. Follow the below four essential steps to configure and manage app permissions in Office 365.
- ‘Review’ existing applications that are accessing your enterprise data via permissions.
- ‘Monitor’ the newly added apps with malicious permissions.
- ‘Remediate’ by revoking the app permissions immediately.
- ‘Defend’ against malicious app consent grants in your Office 365.
1. ‘Review’ Permissions Granted to Existing Applications in Microsoft 365
Admins should review permissions granted to existing applications at least once a week. They should be the Global Administrator, Cloud Application Administrator, Application Administrator or a Service Principal owner to review app consent grants.
Follow the below two ways to review the already added applications’ access to the organization’s data quickly.
Get Report of Application Permissions Using Azure AD PowerShell:
Microsoft has offered the PowerShell script – Get-AzureADPSPermissions.ps1 to export all the OAuth consent grants and OAuth apps quickly in your O365 tenancy. Admins can run the above script and export the report to review the app permissions.
Review Applications Permissions Using Azure AD Portal:
Admins can also review permissions granted to applications in their organizations via the Azure portal by following the steps below.
- Sign in to the Azure portal. Click Azure Active Directory, and then select Enterprise applications.
- Select the application that you want to review and restrict access to.
- Then, select Permissions under the ‘Security’ tab in the left pane like the screenshot below.
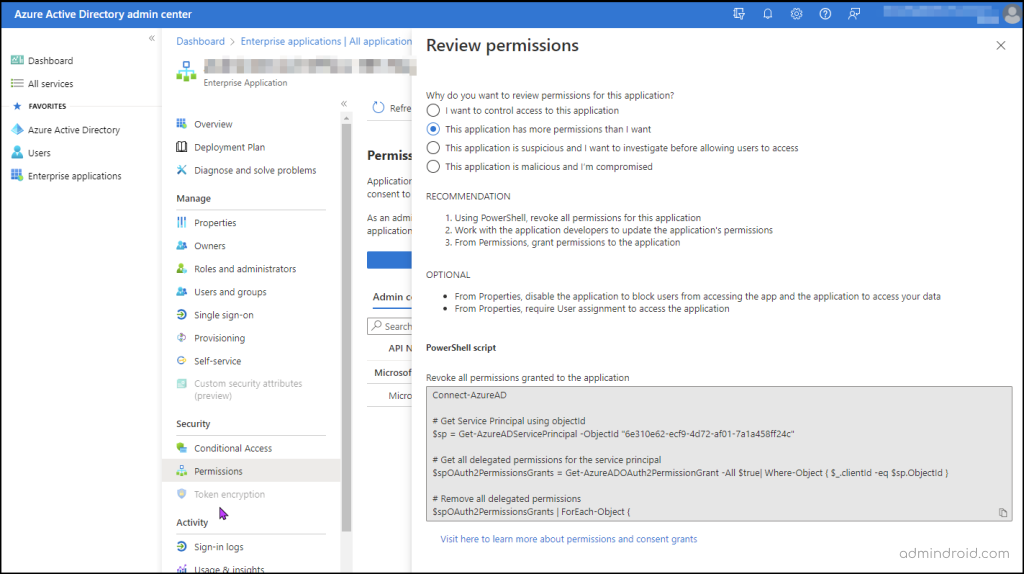
- Further, select the reason to review app permissions by choosing any one of the options listed after the ‘Why do you want to review permissions for this application?’
However, there is no immediate remedy or settings that can be done in the portal instead each option generates PowerShell scripts that allow admins to control the user access to illicit applications via PowerShell.
2. ‘Monitor’ the Newly Added Applications to Avoid App Consent Grant Attacks
After removing the additional privileges for existing applications, admins can detect the newly added applications by using the following way:
Admins can search the newly added application using Audit Log Search in the Security and compliance center.
- On the Audit page, set a ‘Date and time range’ and search for all activities as there is no specific activity name for application consents in Office 365.
- Once selected the required details, click Search.
- Manually sort the results, then click the Activity column and look for Consent to Application.
The major drawback is, there is no automation like generating alerts for this event in Microsoft 365. Admins should have either Microsoft 365 E5 or a standalone Microsoft Cloud App Security license to manage suspicious app permissions efficiently.
3. ‘Remediate’ by Revoking Consent to Malicious Azure AD Applications
If you find an application with illicit permissions, immediately follow the below remediation steps to block and prevent it from recurrence.
- Permanently delete application permissions in the Azure Portal by navigating to the path in the Azure Active Directory -> Applications -> Properties like below.
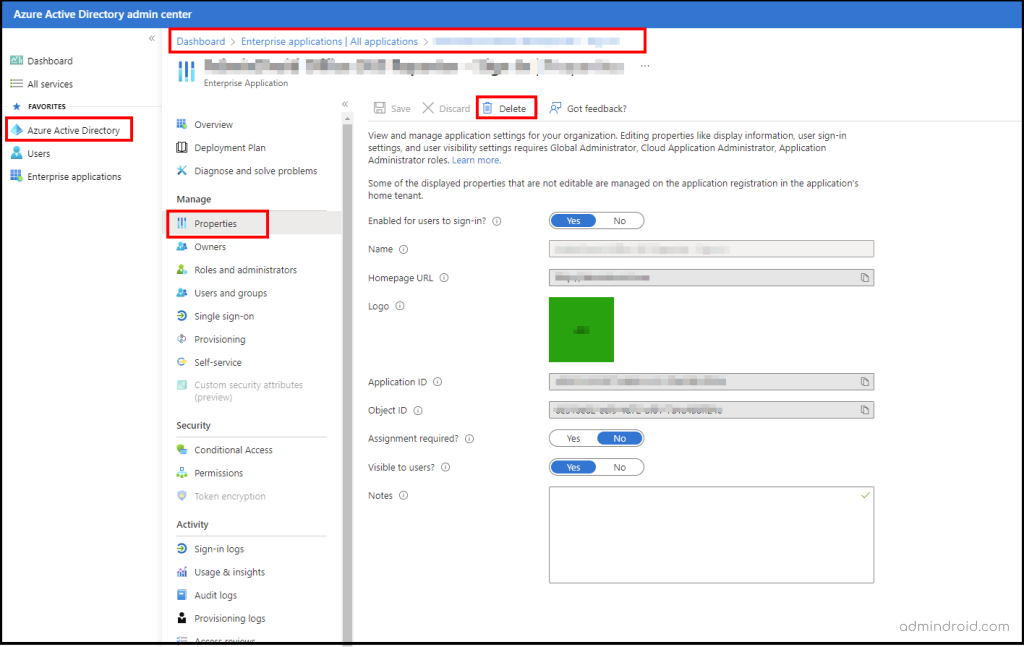
- Revoke the OAuth Consent Grant via Microsoft PowerShell by running the Remove-AzureADOAuth2PermissionGrant cmdlet to completely block OAuth permissions in Azure AD.
- Revoke the Service App Role Assignment using Microsoft PowerShell by running the Remove-AzureADServiceAppRoleAssignment cmdlet to completely block service app role assignments.
4. ‘Defend’ Against Malicious App Consent Grants in Office 365
To avoid the above circumstances, admins can stop the unnecessary applications that are requesting high-level permissions by performing the below ways.
- Configure how user consent to apps in your O365 environment.
- Enable admin consent workflow
- Create custom app consent policies to securely approve application access and provide robust security to their enterprise.
- Allow only legitimate applications from Microsoft verified publishers and reduce the risk.
Do Native Reports Provide Detailed Statistics for Reviewing M365 App Consents?
It’s well-known that native reporting methods for reviewing consented apps and their permissions offer only a general overview. They don’t provide enough depth of metrics to counter potential malicious consent attacks. The lack of detailed and uncategorized statistics can also make decision-making challenging, potentially allowing security threats to go unnoticed.
Hurray! Here is where AdminDroid comes to the rescue!
Manage the Microsoft 365 Application Permissions with AdminDroid
AdminDroid’s Azure AD auditing solution offers in-depth insights into all Microsoft 365 app consents and permissions, enhancing the safety and security of your organization. It possesses a combination of app-related reports that present clear-cut statistics, helping you identify malicious application permissions promptly. These reports include:
- “Consent to Applications” – This report shows all applications that users in your organization have consented to. It allows you to verify whether users have given consent to trustworthy applications.
- “OAuth2 Permissions Grant” – Given that attackers often target OAuth applications to access sensitive organizational data, this report aids in identifying all OAuth-related consents, helping you stay ahead of potential security threats.
- “Administrative Apps” – This report reveals any potentially harmful app consents granted by other M365 admins in your organization. It allows you to question them and, if necessary, request the removal of such app consents.
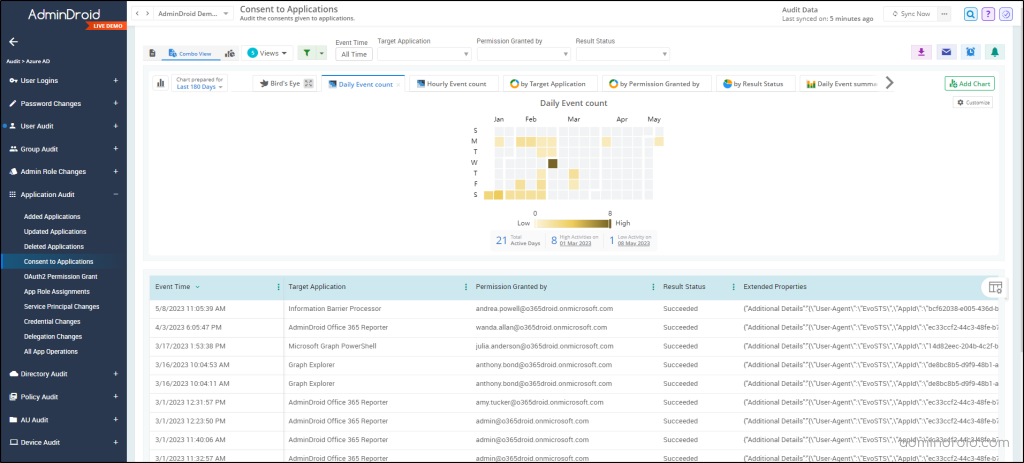
Moreover, AdminDroid provides a series of Azure AD audit reports to help you thoroughly analyze the status of installed applications:
- Added Applications
- Updated Applications
- Deleted Applications
- Azure AD App Service Principal Changes and more.
Surprisingly, all these valuable reports are at no cost. AdminDroid’s Azure AD management tool offers 120+ free reports and 10+ dashboards, providing an all-around view of your Azure AD environment and assisting you in making informed decisions.
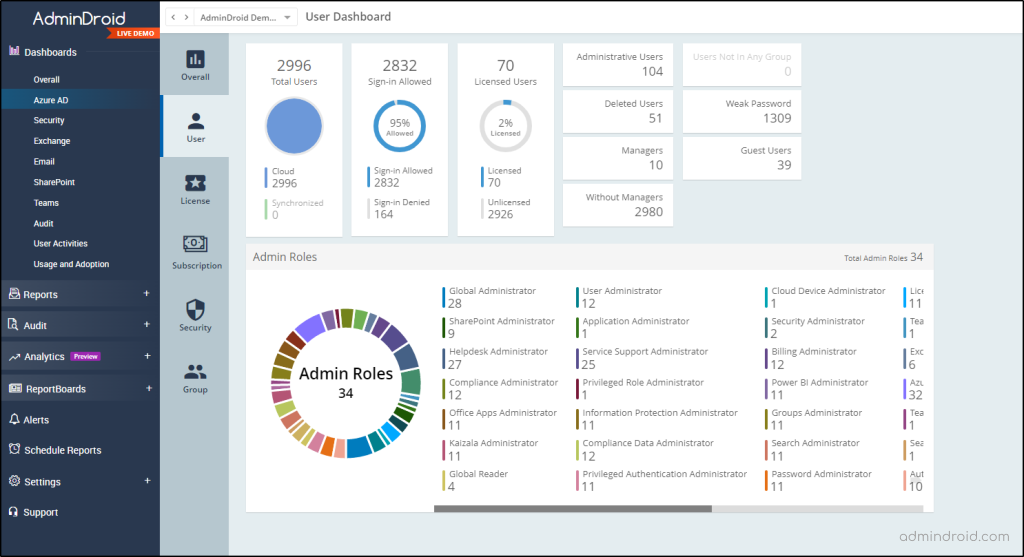
But that’s not all! AdminDroid also offers a wide range of reports and visually appealing dashboards on other Microsoft 365 services, such as Exchange Online, SharePoint Online, Email, OneDrive, and more.
All you have to do is download and install AdminDroid Microsoft 365 reporting tool to start reaping these benefits!
Therefore, being IT admins, we should not let users fall victim to phishing attacks through granted permissions. Even though many security barriers are in place to block malicious apps, we must educate and ensure that our users are aware of consent phishing attacks.
I hope this blog will alert you to review permissions that have been granted to apps and aid you to stop and remediate consent phishing attacks.