🤔Are you a regular reader of our blogs? If so, you may have come across a lot of content related to MFA & Azure AD Conditional Access policies. Why did we bring on most like this? Well, the reason is MFA is one easy step toward getting into the absolute security zone. And as a cherry on top of this, MFA & CA policies come under the Business suite itself!
Here are some MFA and Conditional Access policy blogs that you might find helpful.
- Configuring and Managing MFA in Office 365
- When to use what – Security defaults VS Conditional Access policies
- Safeguard Office 365 Users from MFA Fatigue Attacks
- Use Phishing-Resistant MFA to Implement Stronger MFA Authentication
- How to Safeguard from Security Flaws Found in MFA Push Notification Method?
- Inbuilt Reports on Azure MFA Registration and Reset Events
- External User Types for CA Policies in Azure AD
- 5 Must Know Device-based Conditional Access Policies in Microsoft 365
- An Admin’s Complete Guide to Monitor Conditional Access Policy Changes
And, now adding to the list, Microsoft announced about Azure AD Conditional Access policy templates preview back in November 2021. Yet why does this CA policy template remain in the news for so long? Let’s dig out the answer here!
In this blog, we shall look into the widely spoken CA policy templates and how to deploy them to empower security among enterprises.
What are Office 365 Conditional Access Policy Templates?
Configuring Conditional Access policies is always a challenging task; since we need to consider every individual case, or else the work environment may be adversely affected. So, to make it easier to apply CA policies, Microsoft introduced Conditional Access policy templates.
Conditional Access policy templates are pre-defined set of conditions and controls that provides a convenient method to implement new policies scoped with Microsoft recommendations.
Overall, the CA policy templates are based on Microsoft standards, which takes the organization one step closer to the Zero Trust paradigm.
As Microsoft stated, it comes with 14 Conditional Access policy templates that can be filtered by six different scenarios.
- Secure foundation
- Zero Trust
- Remote work
- Protect administrators
- Emerging threats
- All
Note: Because this is still in Public Preview, some tenants could not find the six filter criteria; rather, they could only view the 14 CA templates. I hope Microsoft rolls out the criteria division soon!
Purpose of Conditional Access Policy Templates:
These CA templates are one powerful update from Microsoft. With its many benefits, it helps to ensure that only authorized users can access sensitive resources within organizations. Some of them are:
- Rather than creating new policies defining controls and accesses from scratch, you can quickly pick a template and apply Conditional Access policies.
- IT security administration departments can streamline the process of managing Office 365 CA policies in their organizations.
- Increased ability to work more on monitoring the Conditional Access policy changes.
- As the templates are Microsoft suggested, we can be sure that the pre-defined policy templates are best in effective and efficient. In the end, organizations can be assured that their policies are up-to-date and reflect best practices for securing corporate assets.
- These templates come with advanced and finely granulated controls, thus helping organizations to meet the absolute compliance requirements.
Isn’t that quite a lot? Absolutely, yes! 💯 Therefore, there is no reason to say NO to using Office 365 Conditional Access policy templates in organizations.
Now that we know what CA templates are, let’s look at how to apply security policy templates.
How to Use the Azure AD Conditional Access Templates?
- Navigate to the below path in the Azure AD admin center and implement access control policies.
Azure Active Directory → Security (Under ‘Manage’ tab) → Conditional Access Policies (Under ‘Protect’ tab)
In the past, deploying access policy templates was part of ‘creating a new policy.’ Now, lately, Microsoft has modified the user interface and added a separate tab for creating new policies from templates.
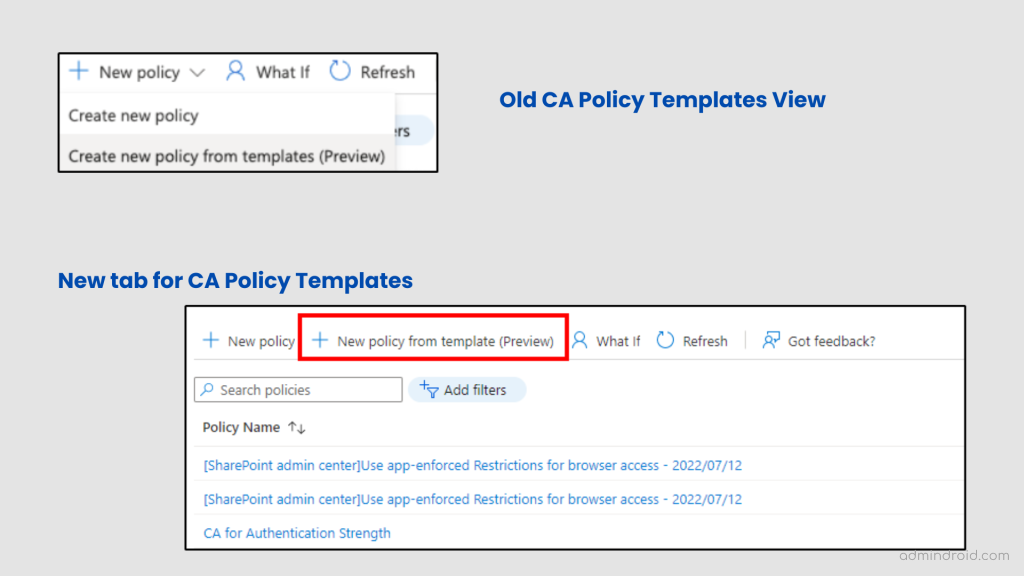
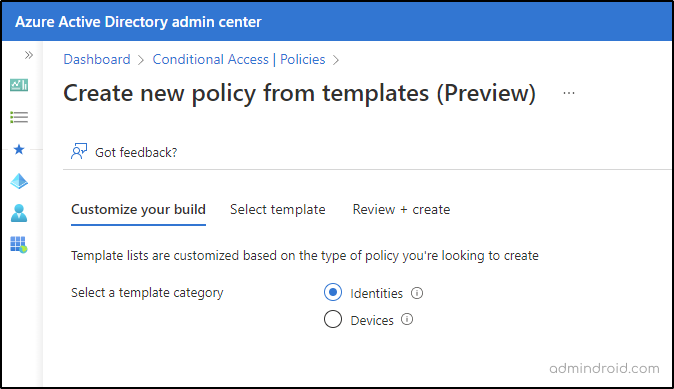
2. As you open up the CA templates page, you’ll see two different template categories.
Identities – Comes with 8 Default Templates – Bring robust protection to each identity and sign-in by requiring strong authentication throughout your digital enterprise.
Devices – Comes with 6 Default Templates – Ensure devices accessing the corporate network comply with compliance standards.
3. Upon selecting the required template category, it will display a library of default policies. The ‘policy summary’ option shows the configuration settings.
Note: Microsoft stated that it’ll provide an option to export the JSON definition of Conditional Access policies for editing purposes. But currently, some tenants couldn’t seem to export the templates. I Hope Microsoft will roll out completely soon!
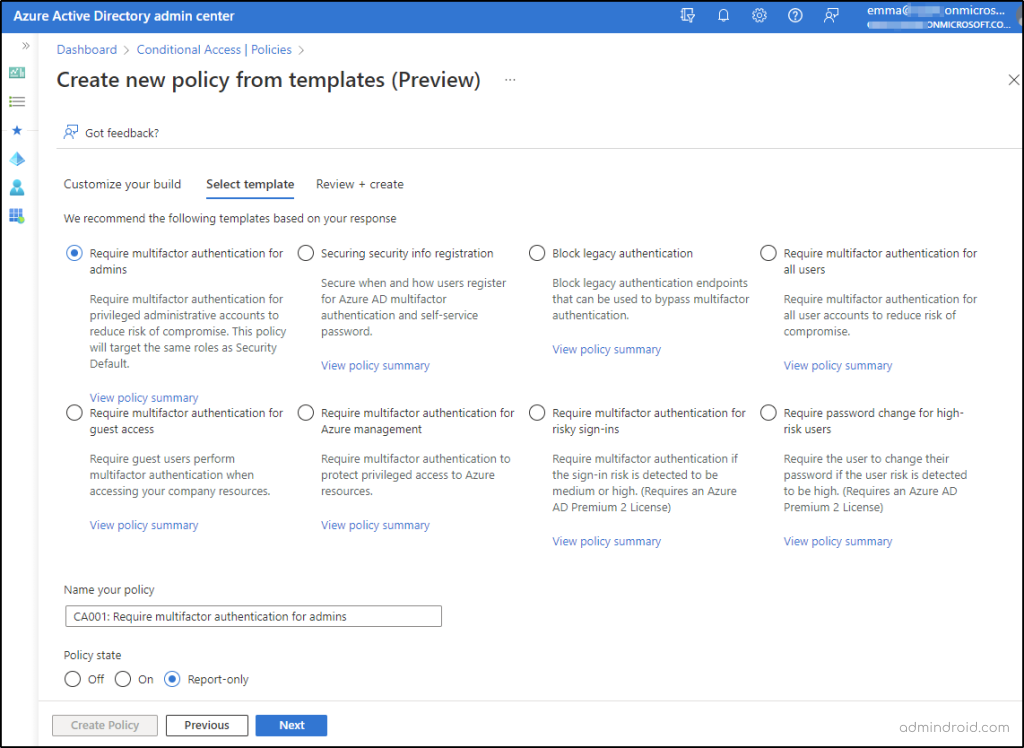
4. Now, after proceeding with Review + Create, a new Office 365 Conditional Access policy is created with an identifiable token number.
That’s it, done in a jiffy! 🚀 But, certain things you might have to know while creating a Conditional Access policy using default templates. They are as follows:
Points to Remember:
- When creating CA policies, all users (except the policy creator) are automatically included and cannot be customized.
- By default, the current user (policy creator) will be excluded from the CA policy. Nevertheless, once a Conditional Access policy is created, you can include/exclude specific accounts or customize the policy using the ‘Edit’ option.
- To prevent disruptions, each policy is created in Report-Only mode by default.
The Rolling Out ‘Conditional Access Policy Templates’
Having learned how to implement Conditional Access policies, let’s now go deeper and learn what Conditional Access policies are added to the list.
| S.No | Conditional Access Policies | Description |
| IDENTITIES | ||
| 1. | Require multifactor authentication for admins. | The attacker’s prime target is administrative accounts, so it is pivotal to give preference and require MFA for admin accounts. Currently, by default, Microsoft requires MFA for the following directory roles: Global administrator Application administrator Authentication administrator Billing administrator Cloud application administrator Conditional Access Administrator Exchange administrator Helpdesk administrator Password administrator Privileged authentication administrator Privileged role administrator Security administrator SharePoint administrator User administrator |
| 2. | Securing security info registration. | This feature is only available to users who have enabled combined registration. This policy requires users to be in a trusted location, do multifactor authentication or use Temporary Access Pass (TAP) credentials. |
| 3. | Block legacy authentication. | Microsoft has started to deprecate basic authentication protocols to mitigate risks among organizations. This will eventually block all basic auth sign-ins. This template is also one of the top 5 Entra ID secure score recommendations to improve your security. |
| 4. | Require multifactor authentication for all users. | Every organization should strictly adhere to this policy to secure firm assets. |
| 5. | Require multifactor authentication for guest access. | Guests can’t be avoided, but we can ensure they are accessing corporate networks in accordance with stricter protocols. This policy template strictly enforces multifactor authentication on every guest’s access. |
| 6. | Require multifactor authentication for Azure management. | Do you know that users can access the Azure portal? Yes, of course! There is no need for users to have access to the Azure portal as this could result in changes to service settings, subscription-wide configurations, etc., As a result, it is prominent to mandate MFA to safeguard privileged access to Azure resources. |
| 7. | Require multifactor authentication for risky sign-ins. | (Requires an Azure AD Premium P2 License) If the sign-in risk is detected to be medium or high, MFA is required. Eventually, this helps to secure Office 365 from risky sign-ins. |
| 8. | Require password change for high-risk users. | (Requires an Azure AD Premium P2 License) If any user-risk is detected, this policy will require them to a password change. |
| DEVICES | ||
| 9. | Require compliant or hybrid Azure AD joined device for admins. | Requiring users with highly privileged rights to perform actions from devices marked as compliant or hybrid Azure AD joined can help limit possible exposure. Microsoft requires MFA for the following directory roles: Global administrator Application administrator Authentication administrator Billing administrator Cloud application administrator Conditional Access Administrator Exchange administrator Helpdesk administrator Password administrator Privileged authentication administrator Privileged role administrator Security administrator SharePoint administrator User administrator |
| 10. | Block access for unknown or unsupported device platforms. | Users will be blocked from accessing business resources if they sign in with either an unknown or unsupported device. |
| 11. | No persistent browser sessions. | This prevents access when an unmanaged device remains signed in to the browser after one hour. |
| 12. | Require approved client apps and app protection. | As well as ensuring that staff can be productive, organizations also want to prevent data loss and secure applications running on devices they do not control. So, this policy requires approved client apps or an app protection policy when using an iOS/iPad/Android device. |
| 13. | Require compliant or hybrid Azure AD joined device or multifactor authentication for all users. | Protect access to company resources by requiring users to use a managed device or perform multifactor authentication. (macOS or Windows only) |
| 14. | Use application-enforced restrictions for unmanaged devices. | Block or limit access to SharePoint, OneDrive, and Exchange content from unmanaged devices. |
Oopsie! Did You Notice This Minor Flaw While Setting?
While I was playing hard with these Conditional Access policy templates, one thing stuck with me! Observed that Microsoft used the newly deployed Filter for devices to one default policy template – No persistent browser sessions.
But there was a minor flaw! 🫤 Although the policy works as expected, the setting description appears to be incorrect.
Here, the policy configuration description says; this prevents access when a trusted device or compliant device remains signed in to the browser after one hour, but the expected behavior is completely different.
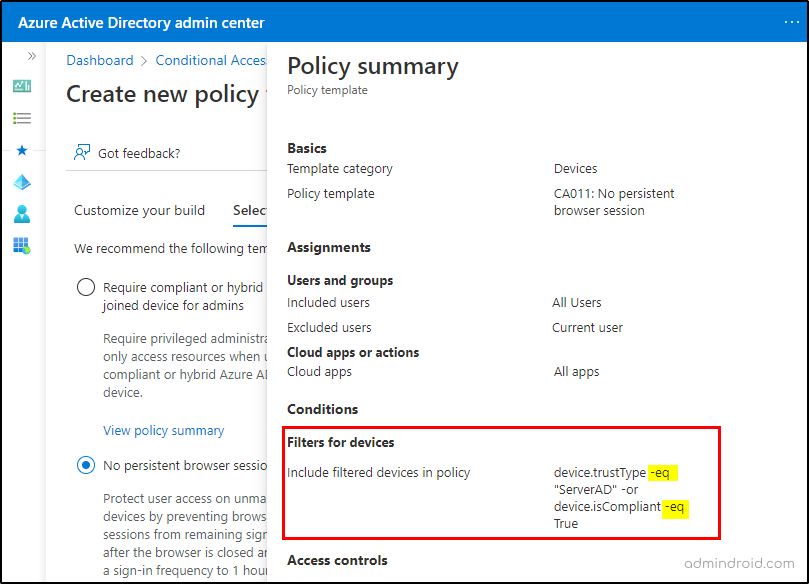
But, when the policy is created, the actual functionality is set as this prevents access when an unmanaged device remains signed in to the browser after one hour.
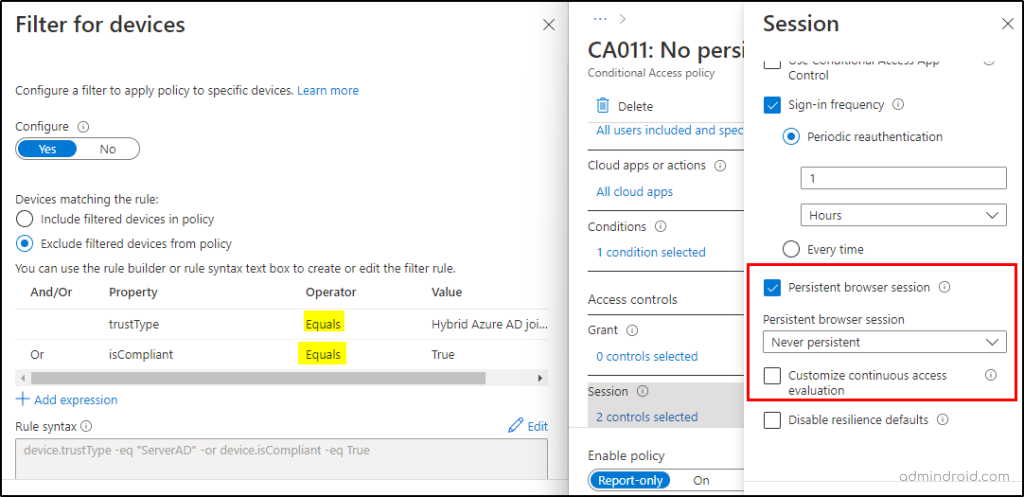
Overall, the functionality appears to work as expected, but the description has a minor mistake. Therefore, I would not take the description at face value. Instead, ensure that the given policy configuration works as expected and then enforce it org-wide.
Finally, here is the final card for the Azure AD Conditional Access policy templates concept! Ensure you remain compliant in this ever-changing digital landscape by deploying best-in-class policies.
Having a robust Conditional Access policy assures your organization’s valuable data is in safe hands.