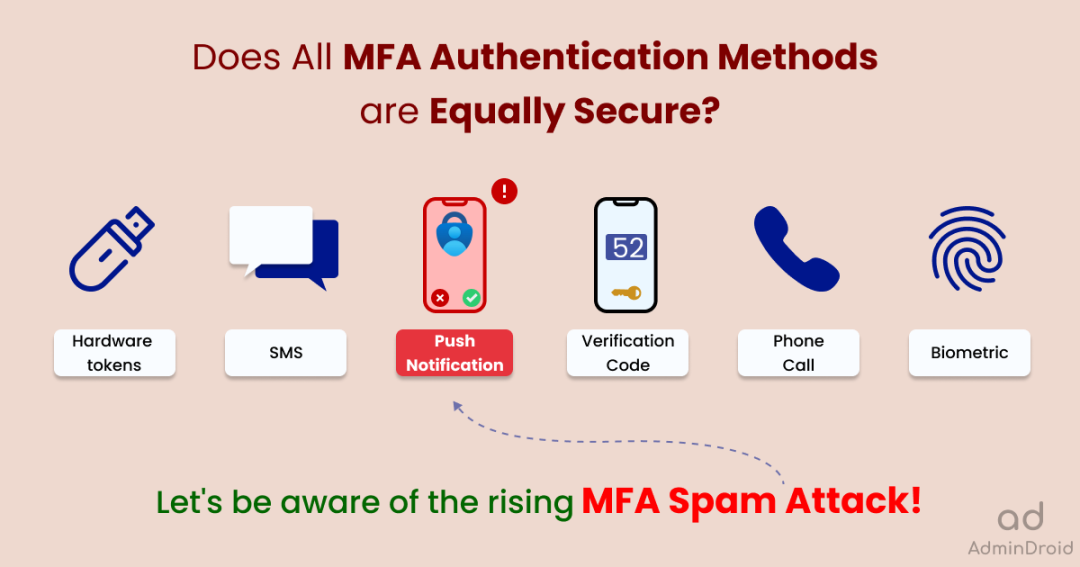
Multi-factor or two-factor authentication is the security gateway to protect our Office 365 accounts. With MFA, your organization will have enhanced security because the users will have to use more than their username and password to identify themselves. In conclusion, MFA is the sole reason that gives an extra layer of security to Office 365 and should be supposed to limit attacks, right?
But what about if I said that the two-factor authentication could also be bypassed? Doesn’t that seem fishy? Can hackers beat strong two-factor authentication?
Yes, a serious attack has started to arise that bypasses the MFA technique and compromises the security posture of the Office 365 environment. MFA spamming is an intrusion technique relying on human factors, started to invade the two-step authentication technique, and proved that not all MFA solutions are secure. It is also referred to as
- MFA Fatigue
- MFA bombing
- MFA abuse attacks
What are MFA Fatigue Attacks?
MFA fatigue is a technique of constantly spamming the user with push notifications for MFA verification in the hope they will accept it thinking it is from a reputable source. Thus, they gain access to the victim’s Office 365 account or the organization’s systems.
Fatigue means exhaustion from something. Attacker overloads the user with MFA push notifications, and eventually overwhelmed by the volume, the user accepts the MFA requests.
Are you curious about how these attacks are carried out? Now, let’s take a closer look at how this MFA prompt bombing attack works.
How is MFA Spamming Done?
MFA bombing attacks are technically simple. It’s way easier to trick humans than machines, so these MFA attacks completely rely on human factors or human errors.
- Initially, the hacker gains access to the user’s account via password spray attacks, phishing or brute-force attacks.
- After gaining access to the credentials, the attacker starts sending continuous push notifications to the user.
- The user will usually deny the request since it was not initiated by them.
- But the hacker continues to spam the victim with multiple push notifications and therefore Office 365 keeps asking login for several times until the victim confirms the MFA request.
- Eventually, the victim accepts the MFA request due to too many attempts of MFA requests or to get rid of the continuous notifications.
- That’s it! Finally, the attacker gains access to the victim’s Office 365 account. This is how MFA spamming is done!
Most Office 365 users are unaware of these kinds of attacks, and they assume the request is coming from a legitimate source, such as their organization, and accept the MFA request. Rather than targeting technology, the attacker targets the human factor in this attack.
Can MFA Fatigue be Prevented?
Several prevention methods exist for these types of attacks.
- Use default MFA service limits.
- Use Number Matching and MFA Additional Contexts.
- Use Microsoft 365 Passkeys for passwordless authentication.
Default MFA service limits – To protect Office 365 accounts from MFA fatigue, configure default MFA service limits.
Use Number Matching and MFA Additional Contexts – To have a secure MFA push notification system, there are different methods available. They are:
- Show application name in the push and passwordless notification – Shows which application the user is attempting to sign in.
- Show geographic location in the push and passwordless notification – Displays from where the request is attempted.
- Number matching with push notification.
Since the hacker cannot enter the number and approve, there is no possibility of attacks. Thus, these attacks are reduced. This method is the most suggested way to protect users from MFA Fatigue attacks and also the attackers will find this method challenging since both sides must confirm the code.
Use Microsoft 365 Passkeys for passwordless authentication – To have simple yet secure logins, passkeys can be configured. As it is phishing-resistant and stored directly on user’s device, you can prevent phishing attacks effectively. Also, it eliminates the need of using passwords, preventing password spray and MFA fatigue attacks.
How to Detect Multiple Push Notification Attacks in Office 365?
There is no direct way to find the instances of MFA Fatigue attacks. However, Azure Active Directory logs allow you to get a hint about these suspicious MFA bombing attacks.
In Azure AD, View Monitoring tab –> Sign-in logs. This gives overall reports on the user sign-ins and successful and failed sign-in attempts.
- Azure AD sign-in analytic reports are unable to detect attacks directly. You must examine all failed cases and interpret only the probability of attack. Here, only the probability of the attack is given, not the possibility.
- Generally, Azure sign-in reports show only successful and unsuccessful sign-ins. The reports do not provide a more detailed explanation. Moreover, the options for filtering are limited, and it does not provide the total counts of sign-ins.
But what if there was a better way to get detailed analytic reports that provide all the insights under a single dashboard instead of searching and goofing around all over the place?
Everything seems to be rolled into one, right? Yes, AdminDroid offers all the reports related to MFA authentication methods under one roof.
Detect the Push Notification Attacks from AdminDroid:
You can discover if any MFA fatigue attacks happened across your organization in the
Analytics –> Sign-in Analytics —> MFA Analysis –> MFA Authentication Methods —> Via Mobile App Notification.
- This lists and audits how many users authenticated through the authentication app, along with details about the signed-in application and IP address. Further, this will help you detect suspicious login attempts.
- To identify MFA spam attacks, set the MFA authentication status to failed. The continual decline of MFA reveals the possibility of an attack.
- Also, you can determine the cause of MFA decline by selecting the particular row and look for reasons for failure. The continuously denied MFA requests can be a sign of MFA spam.
Get Instant Alerts on Every MFA Fatigue Attack Attempts with AdminDroid!
Like a cherry on the top, AdminDroid allows you to set alerts for any audit-related reports. Therefore, you will not only view the MFA spam attacks but also be notified of all suspicious login attempts.
Create custom policies to generate alerts for actions on resources that cause serious threats to your Office 365 environment. Alerts can be set up for all possible risks associated with multifactor authentication, such as
- Users failed to pass the MFA challenge.
- Failure Details of the users who failed in the MFA challenge.
- Max MFA verification failures reached sign-in.
A policy can be triggered and generate an alert when anyone fails the MFA request attempt. Upon triggering this, users might be notified about suspicious attempts to log into their Office 365 account.
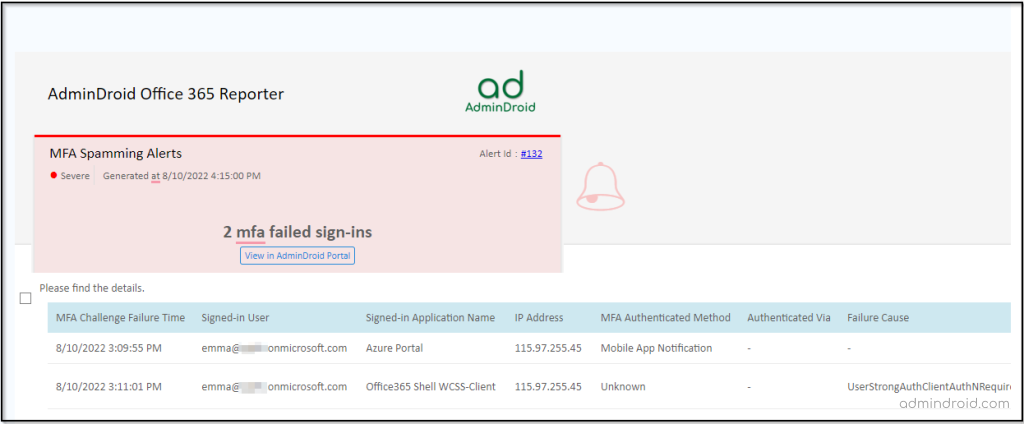
Sample MFA Spamming Alert:
When any matches are found for the report, an alert will be triggered and sent to the corresponding email address.
Ensure MFA is Safeguarding Your Organization as Expected
AdminDroid provides detailed information on each MFA authentication method separately and lets you audit the Office 365 environment effectively. Like how MFA is enforced, how it’s used, and what risks are associated with MFA. Let’s explore AdminDroid’s MFA analytical reports in more detail.
MFA analysis reports by AdminDroid provide clear and detailed answers to all the questions below.
- How are users registered for MFA?
- What are the MFA authentication methods used by your Office 365 users?
- Failures rates of each authentication method and why do they fail?
- Does anyone register for MFA through conditional access policies?
- If registered through CA, how many users and their status?
MFA authentication methods in the MFA analytics provide an exhaustive view of users’ authentication methods. It enables the admins to
- Monitor authentication methods usage across their organization.
- Shows the number of user interactive sign-ins (success and failure) by authentication method used.
- How are these MFA authentication methods used?
Failed in MFA Challenge – Lists the user sign-ins that failed during multi-factor authentication challenge by failure details such as failure reason, failure cause, etc.
All MFA User Sign-Ins Verified via Mobile App Notification – Audits the user sign-ins that are authenticated via Mobile App Notification.
All MFA User Sign-Ins Verified via Mobile App Verification Code– Audits the user sign-ins that are authenticated via Mobile App Verification Code.
All MFA User Sign-Ins Verified via Text Message – Audits the user sign-ins that are authenticated via Text Message.
All MFA User Sign-Ins Verified via Phone Call – Audits the user sign-ins that are authenticated via Phone call.
All Successful User Sign-ins – Audits the user sign-ins with successful multi-factor authentication.
Organization Sign-Ins Count – Gives a summary of the sign-ins count based on the Authentication methods.
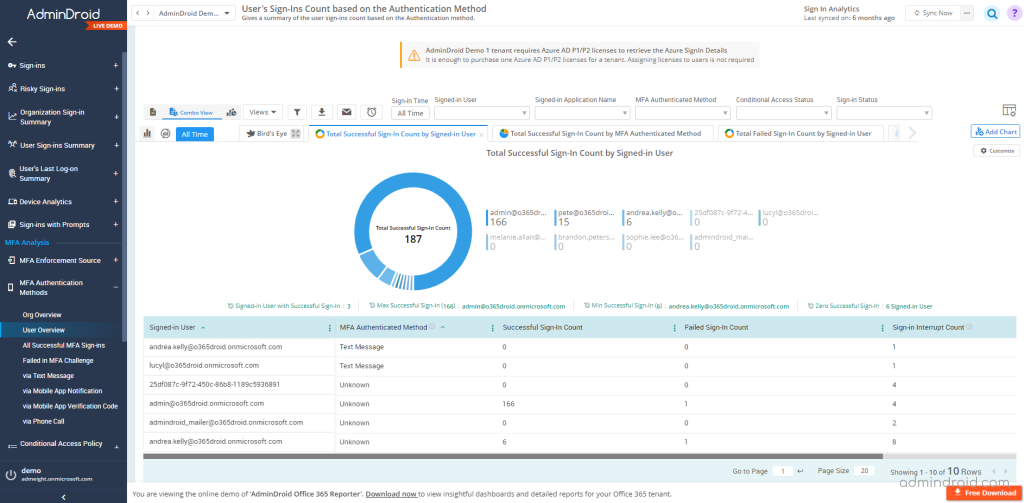
User’s Sign-Ins Count – Gives a summary of the user sign-ins count based on the Authentication method.
Still, pondering your next move? Explore all the features of AdminDroid with a free trial now!
In light of the recent increase in MFA fatigue attacks, it is imperative to safeguard Office 365 users without compromising their security. I hope this blog helped you to gain a better understanding of MFA spam attacks and the solution for these attacks.