On Day 30 of Cybersecurity Awareness Month, we’re exploring one of the most widely used yet often confusing tools in online security, Virtual Private Networks. Explore more insights from our Cybersecurity blog series, where we unpack modern security practices.
Virtual Private Networks (VPNs) are often seen as the first line of defense 🥷 for privacy in today’s connected world. But as cyber threats grow more sophisticated, an important question arises:
“Are VPNs really as secure as they claim to be?” 🤔
Let’s take a closer look at how VPNs work, what makes them secure, their limitations, the risks of free VPNs, and how connectivity is shifting toward identity-based access models.
What Is a Virtual Private Network?
A Virtual Private Network is a service that creates a secure and encrypted connection between your device and the internet. It’s called virtual because it uses software instead of physical cables, private because no one else can see your data, and networked because it links your device with a remote server.
By masking your IP address and encrypting your data, a VPN protects your personal information and allows you to access websites or services that are blocked in your region. In essence, it acts as a private tunnel that keeps your identity hidden, keeping bad actors from accessing your information.
Now that we understand what VPNs do, let’s look at how they help keep your online activities secure.
How VPNs Keep Your Online Activities Private and Secure
Virtual Private Networks play a vital role in maintaining privacy and protecting data by encrypting your online traffic and masking your digital identity. Here is how it helps in different scenarios:
🛡️ Safe Browsing on Public Wi-Fi
Public Wi-Fi networks, such as those in airports, hotels, or cafes, are convenient but often unsecure. Since these networks are often unencrypted, cybercriminals can intercept your activity and steal sensitive information. Using a VPN adds a layer of encryption and keeps your personal data safe from unauthorized access. This protection is especially important for travelers or anyone who connects to free or public Wi-Fi networks while browsing, streaming, or working online.
🏢 Protection for Organizations and Remote Workers
For businesses, VPNs ensure secure access to internal resources. They create encrypted tunnels that protect sensitive corporate data, emails, and financial records. They also enable secure access to company networks from anywhere to protect organizations and remote employees. Beyond VPNs, IT teams should follow remote desktop best practices to secure access and prevent unauthorized use.
👁️ Prevent Online Tracking and Data Collection
Websites, advertisers, and internet service providers often use your IP address to monitor your browsing behavior. A VPN hides your real IP address and replaces it with a virtual one, which helps prevent tracking and profiling. This gives users more control over their personal information and digital identity.
⚔️ Defense Against Cybercrime
By masking your IP address and concealing your location, a VPN provides strong protection against identity theft, doxing, and DDoS attacks. When your digital footprint is hidden, cybercriminals find it much harder to target you.
🌍 Bypass Content Blocks and Censorship
A VPN allows you to connect to servers in other countries, making it possible to bypass regional restrictions, firewalls, and censorship. Whether you are accessing geo-blocked entertainment or connecting to international resources, VPNs help ensure open and secure access to information.
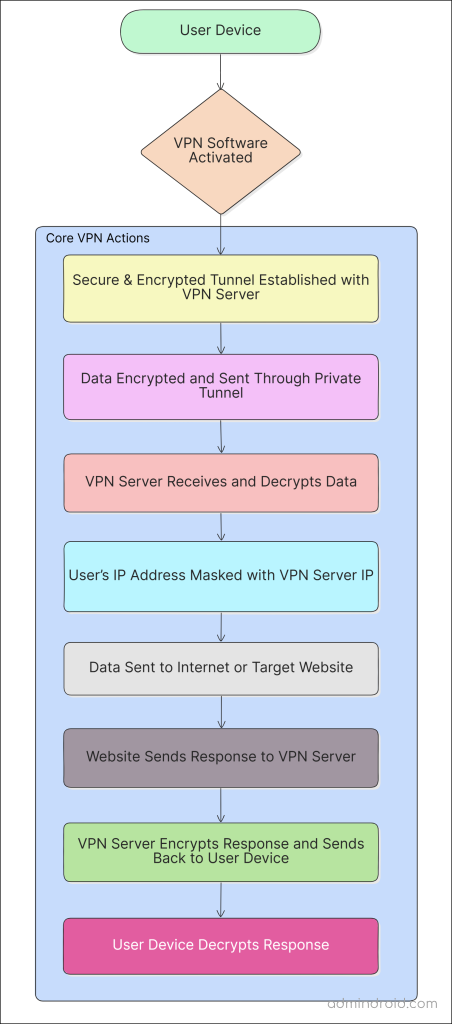
How Does VPN Encryption Work?
When you connect to a VPN server, the provider first authenticates your identity and then creates an encrypted tunnel between your device and the VPN server. All data that passes through this tunnel is scrambled using complex encryption algorithms, making it unreadable to hackers, ISPs, or anyone who does not have the decryption key.
Once the encrypted data reaches the VPN server, it is decrypted using a private key and then sent to your target website along with a masked IP address. This process ensures that your real location, identity, and browsing history remain hidden from anyone trying to monitor your activity.
The strength of the encryption depends on the VPN protocol being used. A VPN protocol defines the set of rules that determine how data is transmitted and protected. Choosing the right protocol is essential to balance speed, privacy, and security.
Below are some of the most common VPN protocols and how they differ in terms of encryption, routing, and usage.
| Protocol Name | Encryption | Routing | Use Case |
| OpenVPN | 256-bit AES encryption using OpenSSL | TCP and UDP, SSL/TLS | Best for overall use |
| SSTP | 256-bit AES encryption | TCP, SSL/TLS | Best for Windows users |
| IKEv2 / IPSec | 256-bit AES encryption | UDP | Best for mobile browsing |
| L2TP / IPSec | 256-bit AES encryption | UDP | Best for basic setups |
| PPTP | 128-bit encryption | TCP | Obsolete; not recommended |
| WireGuard | 256-bit AES encryption | UDP | Best for speed and early adopters |
⚠️ Warning: A VPN doesn’t completely hide your digital fingerprint. Websites can still collect unique details such as your device type, browser settings, screen size, fonts, time zone, and operating system. Regardless of the VPN service you use, this identifying information can still be detected and tracked.
Key Factors that Define VPN Security and Privacy
When configured correctly and supported by robust technology, Virtual Private Networks can be a powerful privacy and security tool. However, not every VPN offers the same level of protection. Here are the key factors that define a truly secure VPN.
1. Strong Encryption: Leading VPNs use advanced encryption standards like AES-256 or ChaCha20, which are virtually impossible to crack through brute force attacks. This level of end-to-end encryption ensures that your online activity and personal information remain private, even on unsecured networks.
2. Secure VPN Protocols: The VPN protocol defines how data travels between your device and the VPN server. Trusted options such as OpenVPN and WireGuard offer an excellent balance of speed, stability, and security. In contrast, outdated protocols like PPTP should be avoided due to known encryption weaknesses and vulnerability to attacks.
3. VPN with No-Logs Policy: Even with encryption, some VPNs may store logs of your browsing data. A strict no-logs policy, preferably verified through independent third-party audits, ensures that no user activity or identifiable data is collected, stored, or shared with external entities. This guarantees complete privacy and user trust.
4. VPN Kill Switch and Leak Protection: If your VPN connection unexpectedly drops, a kill switch automatically cuts off internet access to prevent your real IP address or unencrypted data from leaking. Features like DNS leak protection and IPv6 leak prevention further ensure all traffic stays inside the encrypted tunnel, maintaining full privacy.
5. Independent Security Audits: Top-rated VPN providers undergo regular third-party security audits to validate their privacy claims and verify that their systems are safe. These audits provide additional assurance for users who prioritize transparency and trustworthiness.
Why Free VPNs Might Be a Major Security Risk
Free VPNs promise online privacy and unrestricted access, but in reality, they often do the opposite. Many free VPN services compromise user data, weaken security, or even expose devices to cyber threats. Understanding these weaknesses helps you choose a VPN that truly safeguards your data.
1. Data Logging and Selling: Many free VPN services earn revenue by tracking user activity and selling that data to advertisers or data brokers. This completely defeats the purpose of using a VPN, as your browsing history and personal details may still be collected and monetized. Users often place blind trust in these providers, unaware that the VPN itself may be the one violating their privacy.
2. Weak or Outdated VPN Protocols: Some VPNs still rely on outdated protocols such as PPTP, which can be easily exploited by attackers. Using old or misconfigured encryption standards leaves your traffic exposed to interception, decryption, and unauthorized access. Always choose a VPN that supports modern and secure protocols like OpenVPN, IKEv2/IPSec, or WireGuard.
3. Fake or Malicious VPN Apps: Several so-called “free VPN” apps available on mobile app stores are actually malicious software. They are designed to collect sensitive information, inject intrusive ads, or even install spyware on your device. Always verify the reputation, reviews, and transparency of a VPN provider before downloading.
4. DNS and IP Leaks: Even a secure VPN can leak your true IP address or send DNS requests outside its encrypted tunnel if it is not properly configured. These leaks expose your browsing history, location, and identity. A reliable VPN provider will include built-in DNS and IP leak protection features to prevent this issue.
5. Limited Servers and Slow Speeds: Free VPNs usually offer a very small number of servers shared by thousands of users. This leads to slower connection speeds, higher latency, and frequent disconnections. Limited server locations can also restrict access to certain regions or content. Paid VPNs, by contrast, provide optimized servers and better bandwidth for a faster, more stable experience.
“Free isn’t always safe, especially when it comes to your privacy. So, think before you trust a free VPN.”
📝Note: These weaknesses aren’t only limited to free Virtual Private Networks. Some paid VPN services have also been found logging user data, using weak encryption, or misrepresenting their privacy policies. Always verify independent audits, transparency reports, and technical security standards before trusting any VPN provider.
Limitations of VPN Security
Even though VPNs provide a valuable layer of protection, they are not a complete security solution. Understanding their limitations helps set realistic expectations.
- A VPN encrypts your traffic, but it cannot stop phishing, malware infections, or credential theft that happens after you connect. It secures the channel, not the context of your actions online.
- Traditional VPN setups often grant users full access to the internal network once connected. If a user account is compromised, an attacker could move laterally within that network and reach other systems.
- VPN providers must comply with the laws of the country in which they operate. In certain regions, they may be required to store logs or share user data with authorities, which can reduce privacy guarantees.
- Routing traffic through distant VPN servers can slow down your internet speed and affect latency, especially during streaming or large data transfers. This trade-off between performance and privacy is a common limitation of VPN technology.
- As organizations shift to cloud-based applications, VPNs can become complex to manage and scale. They are less effective in environments where access control depends on user identity, device health, or real-time context rather than static network location.
So, is a VPN truly secure? The answer depends on how it’s configured, who provides it, and what you’re protecting. For individual users, a trusted VPN enhances privacy and reduces exposure to public networks. But for enterprises, traditional Virtual Private Networks often struggle to keep pace with today’s cloud, identity-driven environments.
That’s why organizations must look beyond Virtual Private Networks to embrace modern, context-aware solutions for the future of secure connectivity.
Alternatives for VPN Connections in the Corporate World
As digital workspaces expand and hybrid work becomes the norm, traditional VPNs are showing their age. Organizations now need to secure remote access solutions that can protect users and data regardless of where they connect from.
This shift has led to the adoption of modern frameworks that deliver more flexible and scalable protection than legacy VPNs. The following models go beyond conventional VPNs, offering more adaptive, identity-based, and scalable protection for distributed and cloud-driven environments.
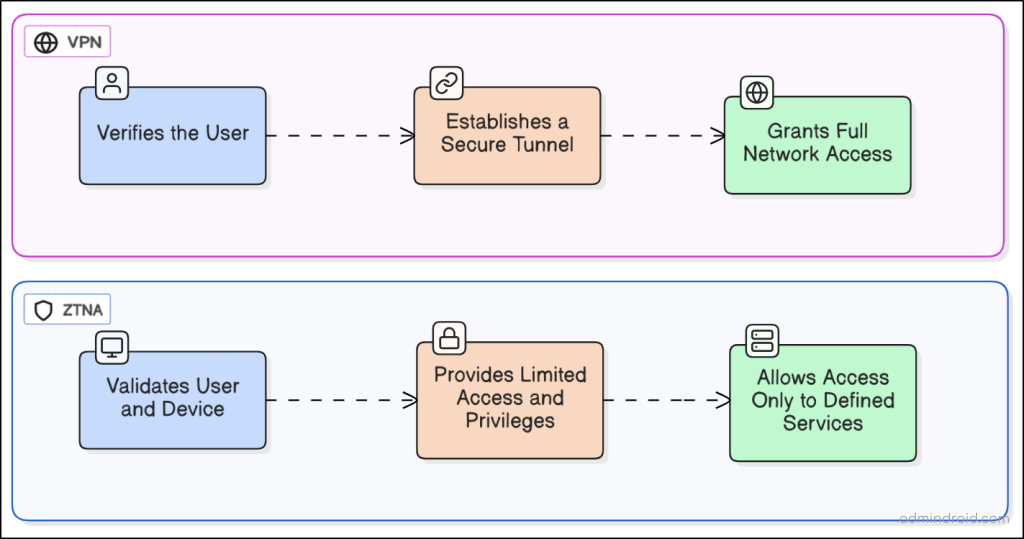
Zero Trust Network Access (ZTNA)
ZTNA is a core pillar of identity and network access for Zero Trust security model and operates on a simple principle: “Never trust, always verify.” Instead of providing full network access, users are granted least-privileged access based on user identity, device health, security posture, and real-time context (e.g., location, risk signals). This minimizes the attack surface, even if credentials are stolen; attackers can’t move laterally through the network.
One example of the ZTNA component in practice is Microsoft Entra Private Access, part of the Global Secure Access (GSA). It delivers identity based, Zero Trust connectivity for private applications and IP ranges, enforcing access through Entra ID Conditional Access policies.
Of course, Microsoft isn’t alone. Other major platforms like Zscaler, Cloudflare, Palo Alto Networks, and Cisco offer ZTNA services built for global scalability.
Software-Defined Wide Area Network (SD-WAN)
For companies operating across multiple branches or remote sites, consistent and secure connectivity is essential. That’s where the Software-Defined Wide Area Network (SD-WAN) comes in.
Unlike traditional WANs that rely on rigid hardware configurations, SD-WAN uses software to intelligently manage and optimize network traffic. It introduces a smart software layer over existing infrastructure, allowing administrators to automatically route traffic based on business priorities, application types, and real-time network performance.
This not only ensures faster, more reliable connectivity between offices, data centers, and cloud services but also strengthens security and visibility for IT teams managing hybrid networks.
In the Microsoft ecosystem, Azure Virtual WAN serves as the cloud-based backbone that integrates with SD-WAN. This enables enterprises to securely connect branch offices and remote users to Azure and other cloud services with policy-based routing.
Secure Access Service Edge (SASE)
While ZTNA secures access and verifies identity, it doesn’t optimize network performance. Conversely, SD-WAN enhances routing and connectivity but lacks deep, identity-based security controls. But thankfully, SASE merges technologies like SD-WAN, Zero Trust Network Access (ZTNA), Firewall-as-a-Service (FWaaS), and Cloud Access Security Broker (CASB).
SASE provides secure, direct access to cloud applications without routing traffic back through a central data center. It delivers consistent policy enforcement, identity-based access control, and real-time threat protection across all users and devices regardless of where they connect from.
In short, SASE addresses the performance and security limitations of traditional VPNs by blending network efficiency with Zero Trust protection in a single, scalable solution.
Wrapping Up
In the end, Virtual Private Networks protect your connection, while Zero Trust access delivers identity-aware, context-driven protection across distributed environments. They establish a comprehensive security framework that strengthens both network protection and access control.
“The safest approach isn’t choosing one over the other but understanding when each fits your needs.”
We hope this blog helps you understand how VPNs protect your organization and the evolving future of secure connectivity. Stay tuned for more insights on managing security across on-premises, cloud, and hybrid environments.