On the 10th day of Cybersecurity Awareness Month, learn how to restrict AI apps on Microsoft Intune-managed devices. Keep following for more security insights across legacy Active Directory, evolving Microsoft 365, modern AI, and complex hybrid setups in our Cybersecurity blog series.
From drafting emails to analyzing data, AI tools have fully embraced the workforce, evolving into an everyday companion for productivity and innovation. But as quickly as it delivers productivity, unchecked AI adoption in Microsoft 365 can also turn into a cybersecurity nightmare.
“By far, the greatest danger of Artificial Intelligence is that people conclude too early that they understand it.”
And that quote couldn’t be more accurate! Not all friendly chatbots, AI problem-solving tools, or generative AI apps are as safe as users assume. AI apps can leak sensitive data, harvest credentials, enable sophisticated phishing attacks, or even deploy malware. That’s why securing the perimeter by blocking or removing unauthorized AI apps on every corporate-managed device is essential.
Without delay, let’s dive into how to ban unapproved AI apps across iOS, Android, macOS, and Windows devices enrolled in Microsoft Intune.
How to Block AI Apps on Managed Devices in Microsoft Intune
Consider this: an employee starts using an AI productivity app for quick tasks. Frustrated by constant logouts and switching between tabs, they install the native app on their company device. What starts as a harmless convenience soon leaves a bold digital footprint on your endpoints. Now imagine these AI apps spreading across your company iPads, Windows PCs, Android phones, and Macs. With widespread adoption, every prompt could contain a piece of confidential data, and that’s when the real risk begins.
The data exchanged with AI tools often resides on external servers, beyond your organization’s control, making it nearly impossible to retrieve or delete. This increases the risk of data leaks, breaches, and misuse of confidential information. As an admin, the need to govern AI apps by identifying, controlling, and restricting their use across all devices has never been higher.
Now, navigate to the Discovered apps report and check how many AI apps are being used across your organization. Imagine the potential exposure if even a few of these apps handle sensitive company data without proper oversight.
Microsoft Intune admin center → Apps → Monitor → Discovered apps
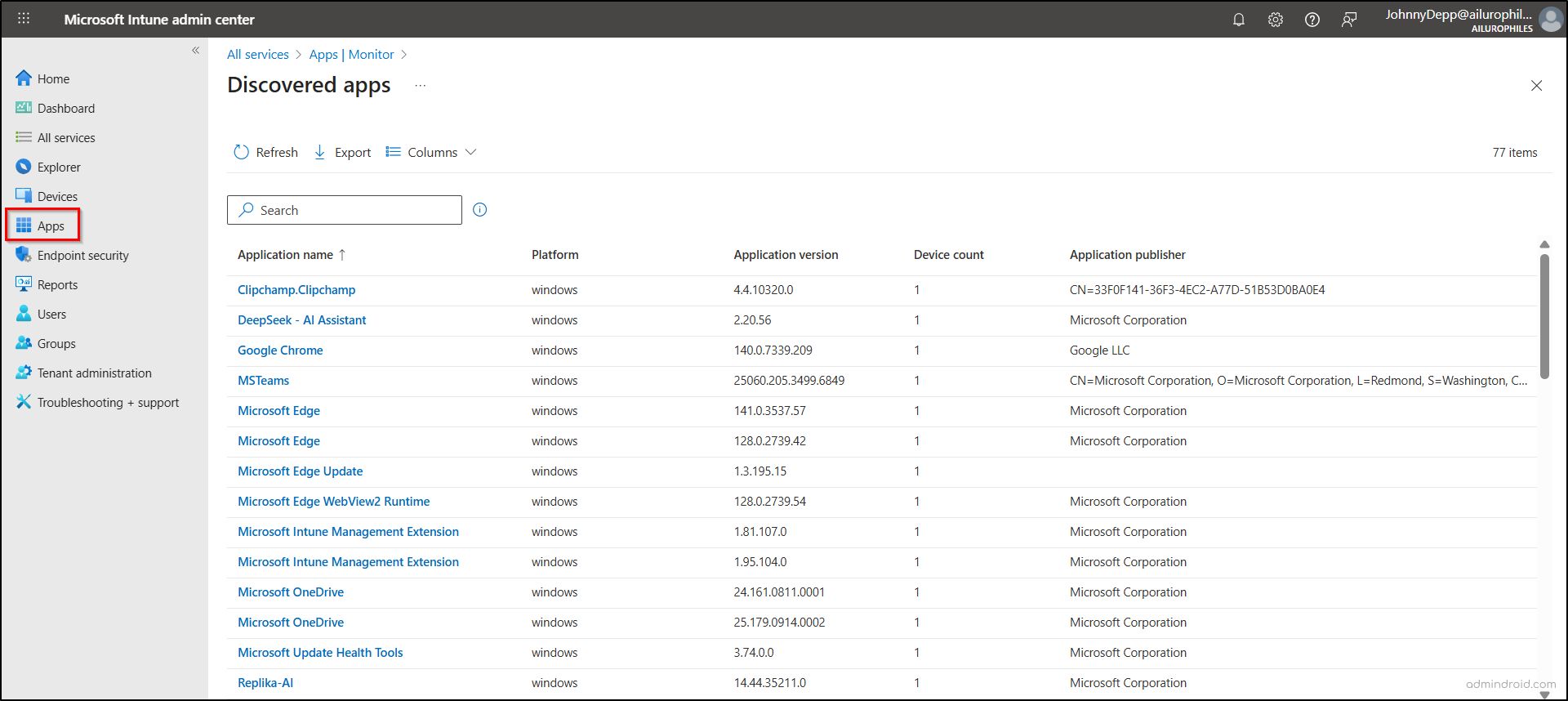
From the Discovered Apps list, select an AI app to see all devices where it’s installed, including device name, email address, operating system, OS version, and IMEI number.
Once you’ve identified the devices that need restrictions, apply the appropriate measures based on the device type:
- Company-managed devices: Fully enrolled and controlled by your organization. You can block or remove unauthorized AI apps directly using Intune policies.
- Personally owned (BYOD) devices: User-owned devices accessing corporate data. Apply app protection policies to restrict access without managing the entire device.
Restrict AI Apps on Intune-Managed Corporate Devices
Let’s walk through how to block risky AI apps on Intune-managed devices across iOS/iPadOS, Android, Windows, and macOS.
- iOS/iPadOS
- Android
- Windows Devices
- MacOS
1a) Hide and Prevent AI Apps from Launching on Corporate iOS/iPadOS Devices
Recently, with rising security concerns, even government bodies are stepping in to restrict certain AI apps. Imagine one of your users installed such a restricted or risky AI app on a corporate iOS or iPadOS device. To prevent data exposure, you need to hide the app or block it from being launched on their devices.
You can block these apps from being displayed or launched by creating a device configuration profile in Intune:
Microsoft Intune admin center → Devices → iOS/iPadOS → Manage devices → Configuration → Create → New Policy
- On the Create a profile pane, choose Settings catalog as the profile type and click Create.
- In the Basics tab, provide a suitable name and description for the policy, then click Next.
- In the Configuration settings section, click Add settings.
- On the Settings picker pane, search and select Restrictions, then check the Block App Bundle IDs option. Enter the AI app bundle ID and click Next.
- Select ‘Next’ again to proceed to the Assignments page. Assign the policy to the required user or device group and hit Next.
- Finally, review the profile settings and click Create to deploy the device configuration profile.
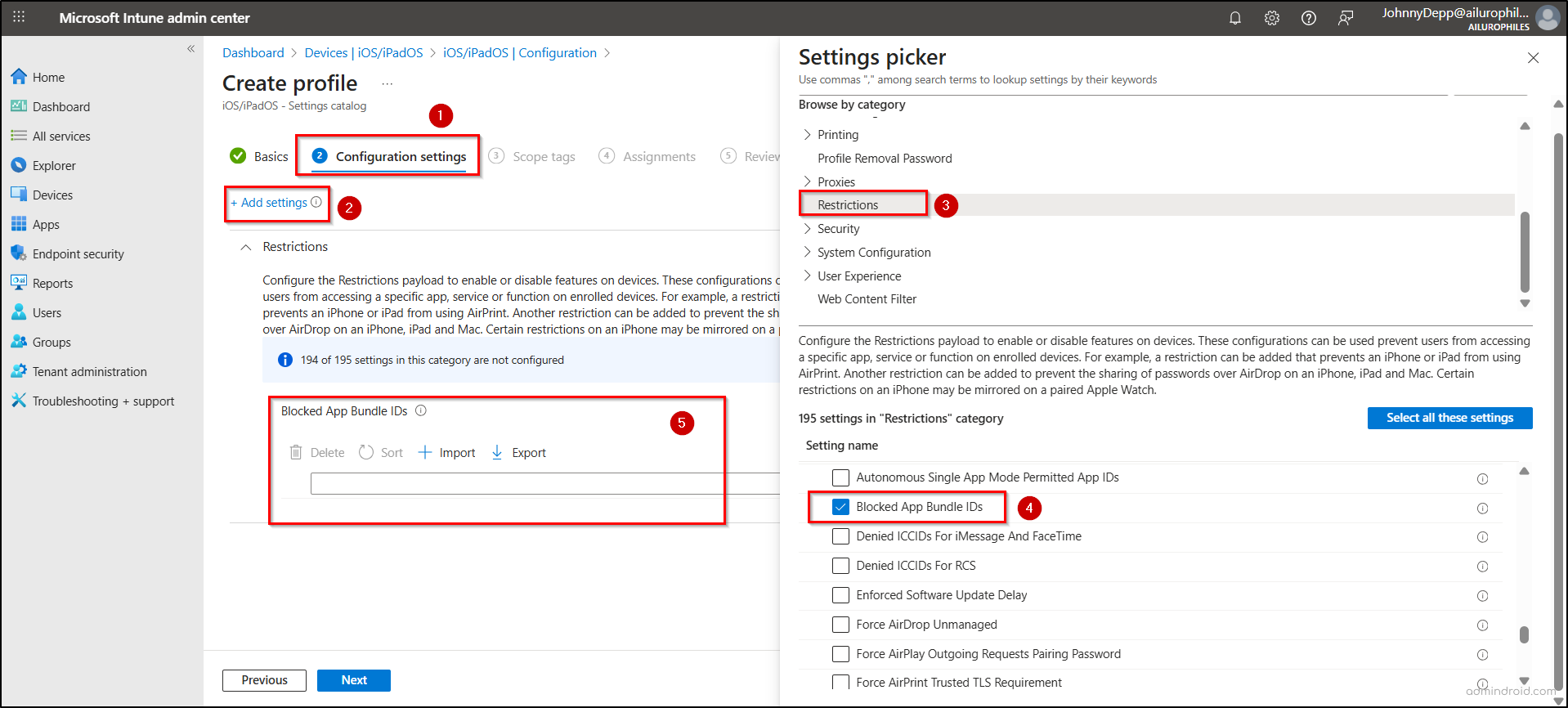
Note: Settings to hide and prevent the launch of apps are available only on supervised iOS/iPadOS devices and are not supported on unsupervised or personal devices.
1b) Uninstall the AI App in iOS/iPadOS Devices Directly Using Microsoft Intune
Even if you hide or block the launch of a risky AI app using a configuration profile, the app may remain on devices if the user has already installed it from the Apple App Store.
To address this, admins can automatically uninstall the unauthorized app on supervised iOS/iPadOS devices by setting up a policy using the following path.
Microsoft Intune admin center → Apps → iOS/iPadOS → Create→ iOS store app → Select.
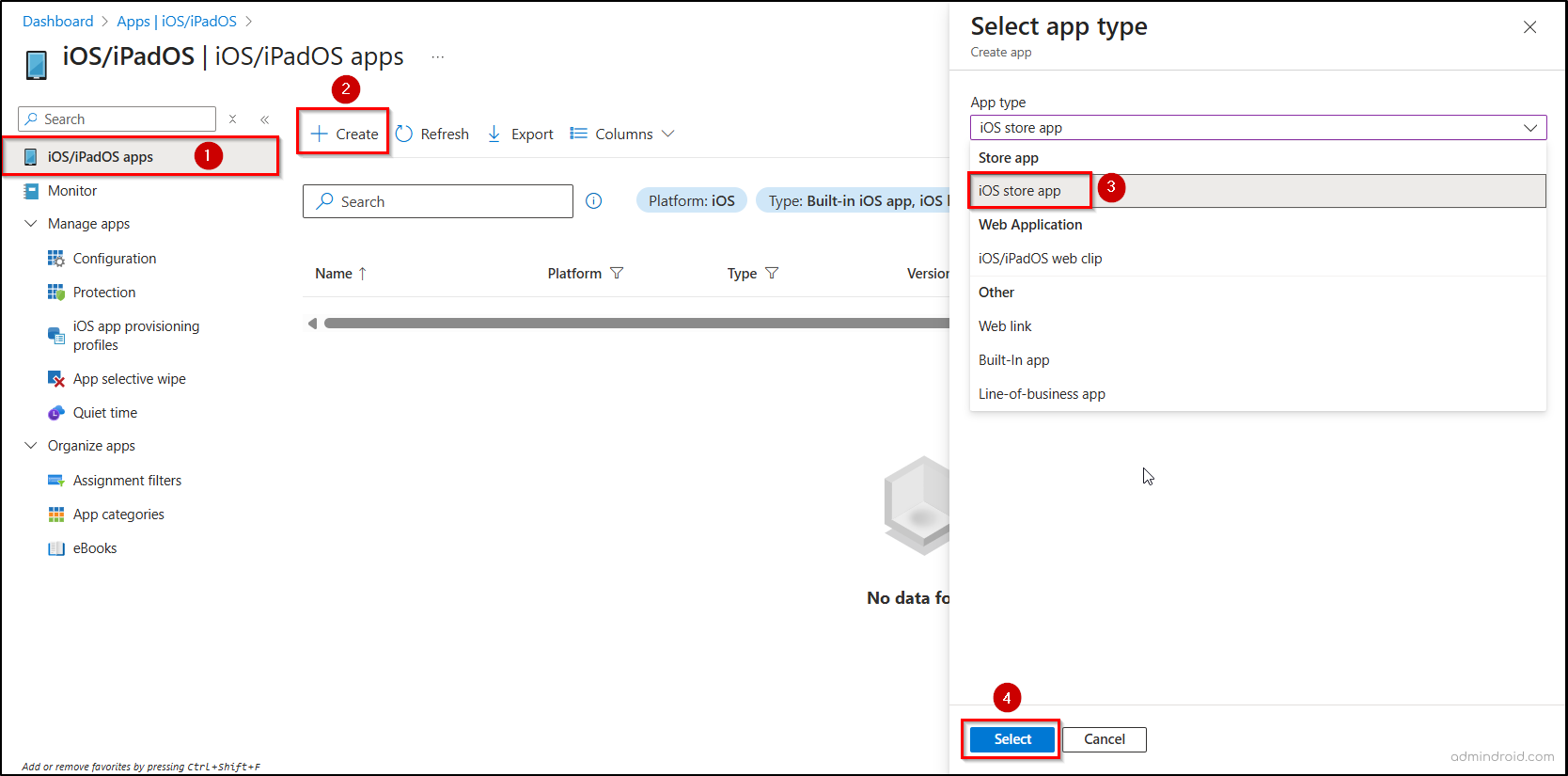
- After clicking Select, go to the App information tab and click Search the App Store.
- Search and select the AI app you want to remove, then click Select.
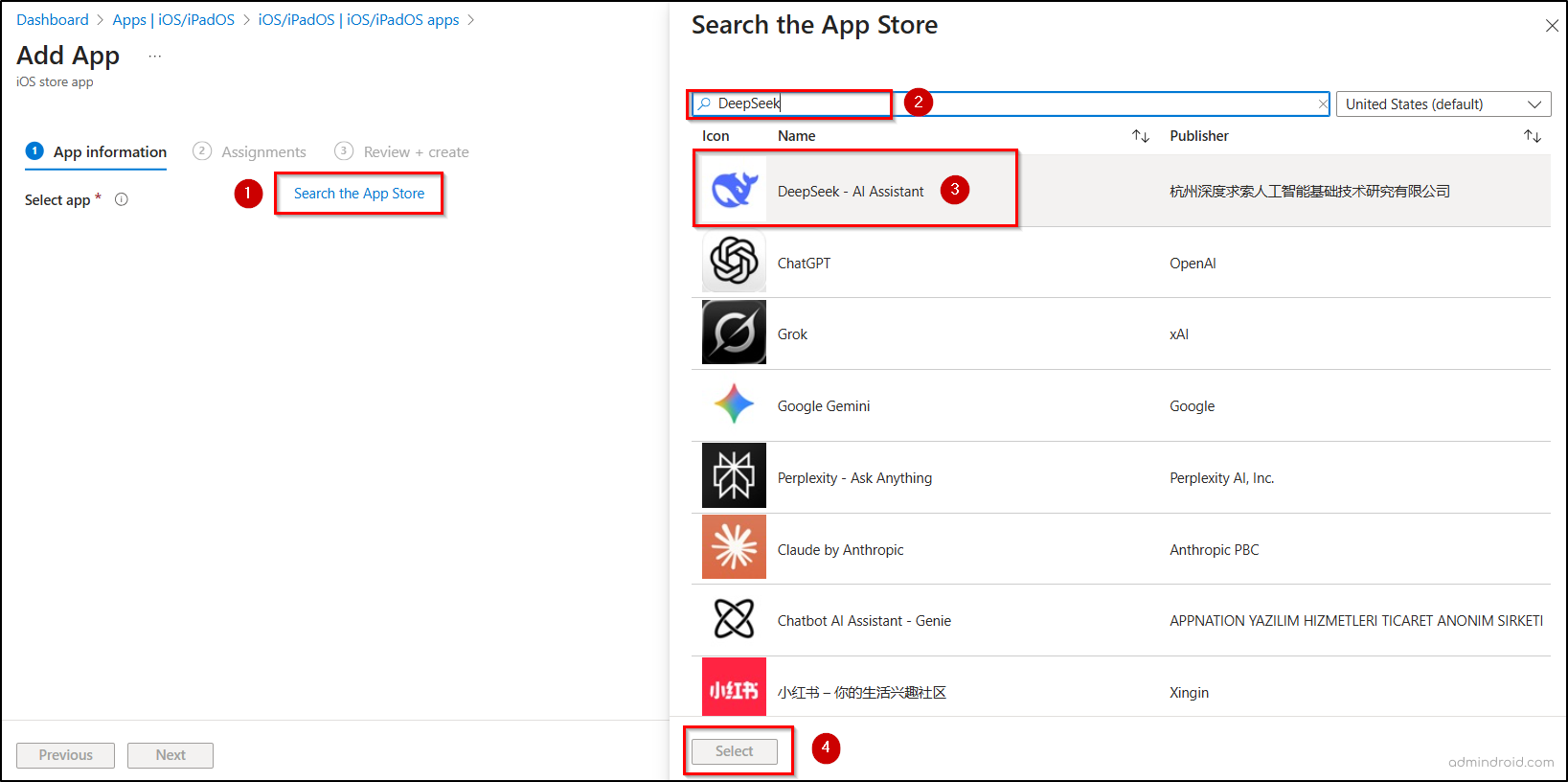
- Review the app information and click Next.
- On the Assignments tab, go to the Uninstall section and add the relevant groups, users, or devices from which the AI apps should be removed.
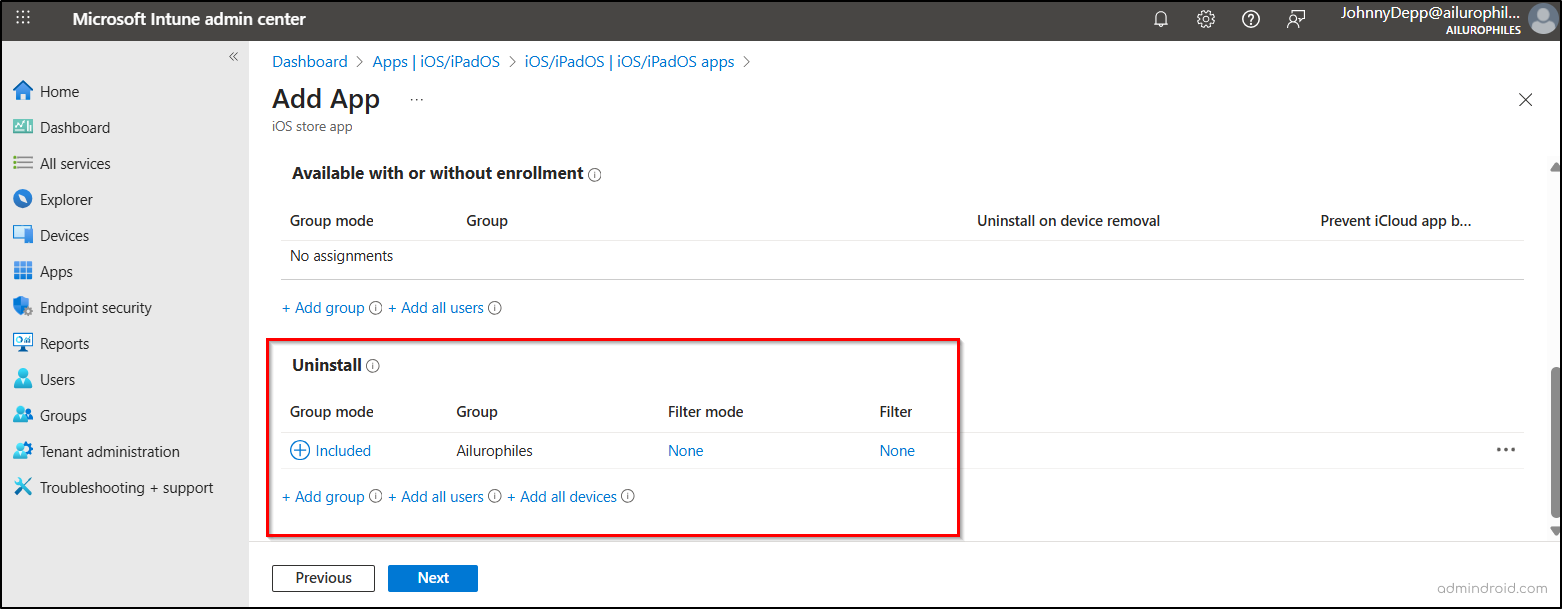
- Click Create on the Review + Create tab to finish setting up the policy.
Once assigned, this policy automatically removes the specified app from devices where it is currently installed. It will also remove the app if it is installed in the future, as long as the policy remains assigned.
2a) Restrict Access to All Apps in Google Play Store for Corporate Android Devices
By default, users on managed devices can install only organization-approved apps via Managed Google Play. However, a single change could allow users to install any app, including AI apps that put sensitive data at risk. Unchecked, this permissive environment is an invitation for Shadow AI. It transforms personal productivity tools into silent vectors for serious security headaches.
To regain control, admins should restrict the installation of unauthorized apps across all Microsoft 365 managed devices. This helps safeguard your organization from risky AI apps that may introduce security threats or data leaks.
- Open the Android Device configuration page and select Create > New Policy.
- Set Platform to Android Enterprise and Profile type to Templates.
- Under the Fully Managed, Dedicated, and Corporate-Owned Work Profile category, select Device restrictions, then click Create.
- In the Basics tab, enter a name and description, then click Next.
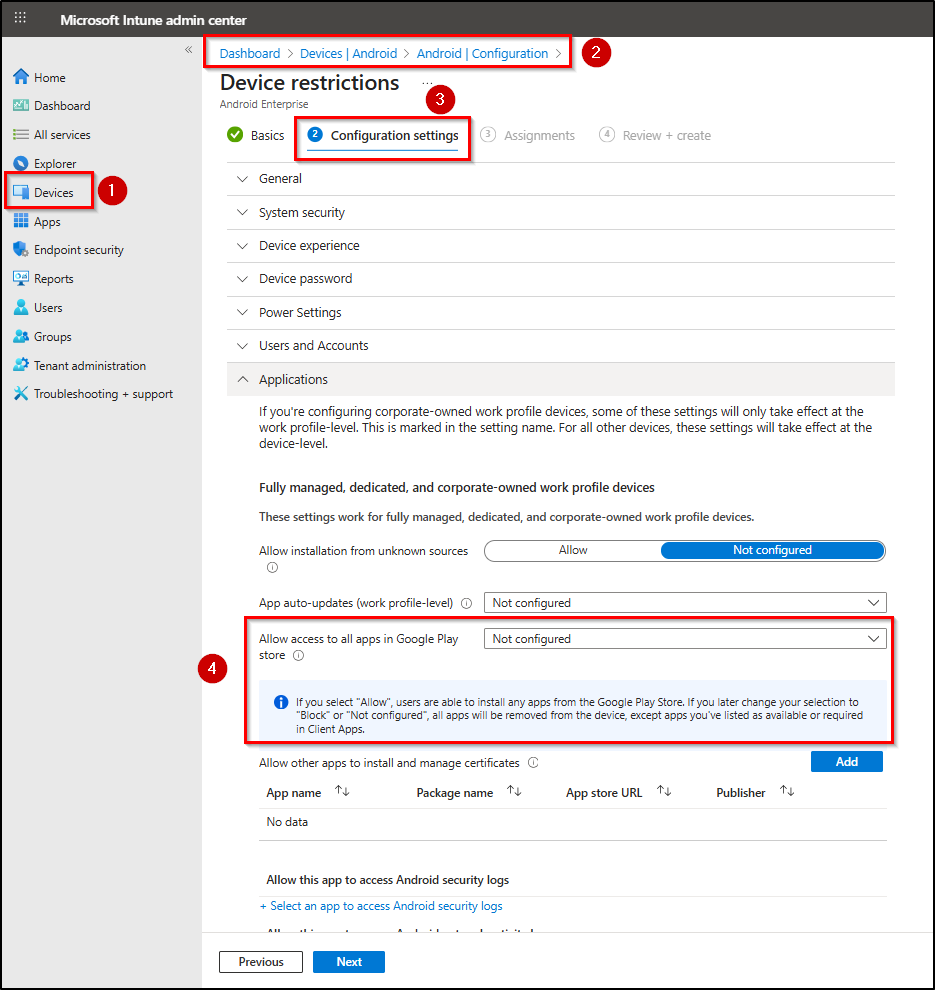
- Under the Configuration settings tab, expand Applications category.
- Change the Allow access to all apps in Google Play Store setting from Allow to Not configured.
- Adjust the assignments according to your requirements, then review the settings and create the policy.
When this setting is changed from Allow to Not configured, all apps not allowed for the user will be removed from the device. The user will receive a notification indicating that the app has been deleted.
2b) Uninstall the Restricted AI Apps on Android Devices
Consider a scenario where you initially restrict users from installing any apps except company-managed ones. While this might seem like the safest approach, it’s rarely practical in real-world environments. The smarter strategy is to target the actual risk, rather than blocking everything.
Picture this: an unapproved AI chatbot app makes its way onto a company-managed Android device that has access to sensitive corporate data. That’s when you need to act—uninstall the app and block it from being reinstalled through the Google Play Store. Here’s how to remove the specific restricted AI app on Android devices using Intune.
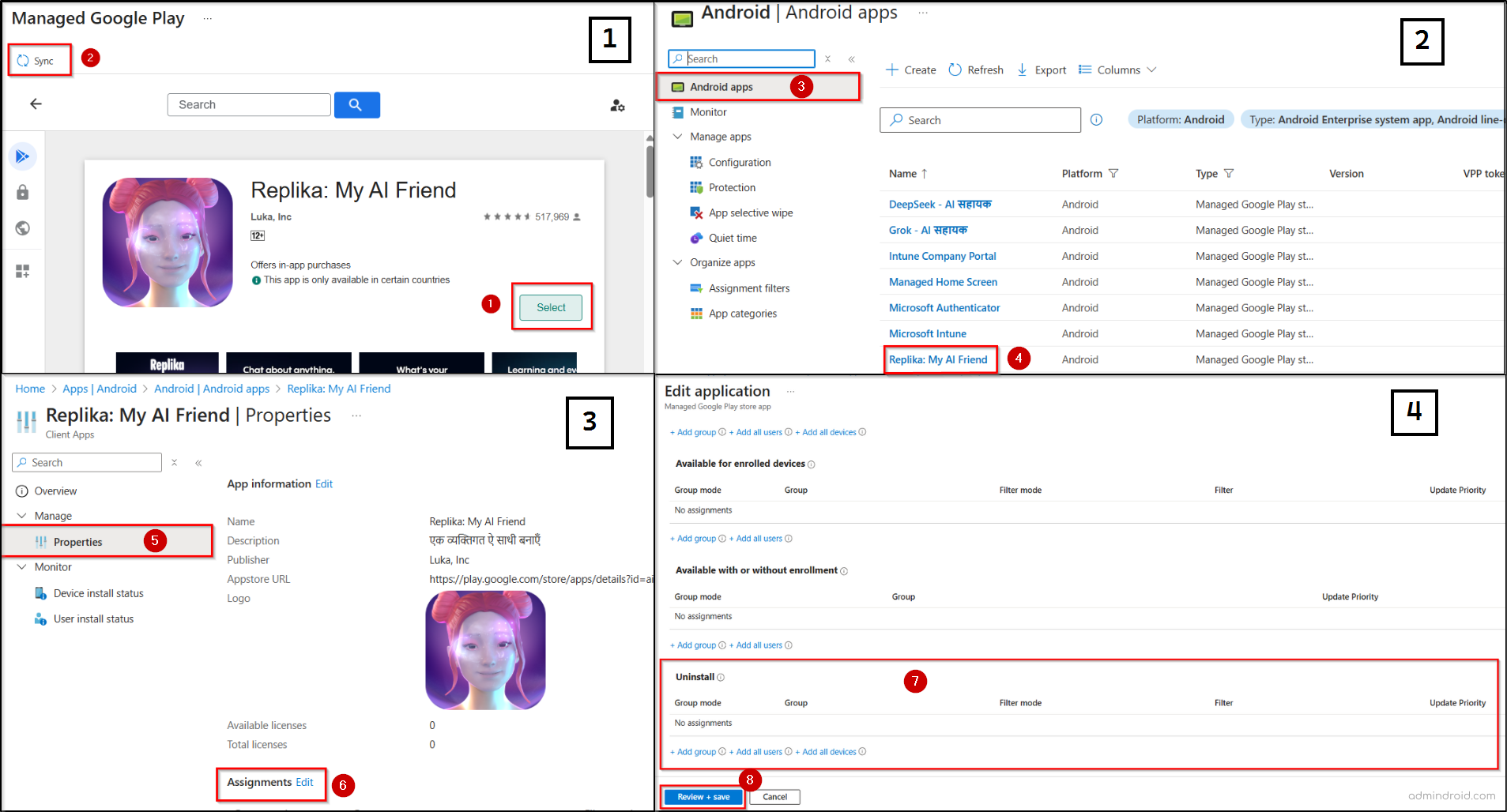
- Open the Microsoft Intune admin center and go to the following path.
Apps → Android → Create → Managed Google Play app →Select.
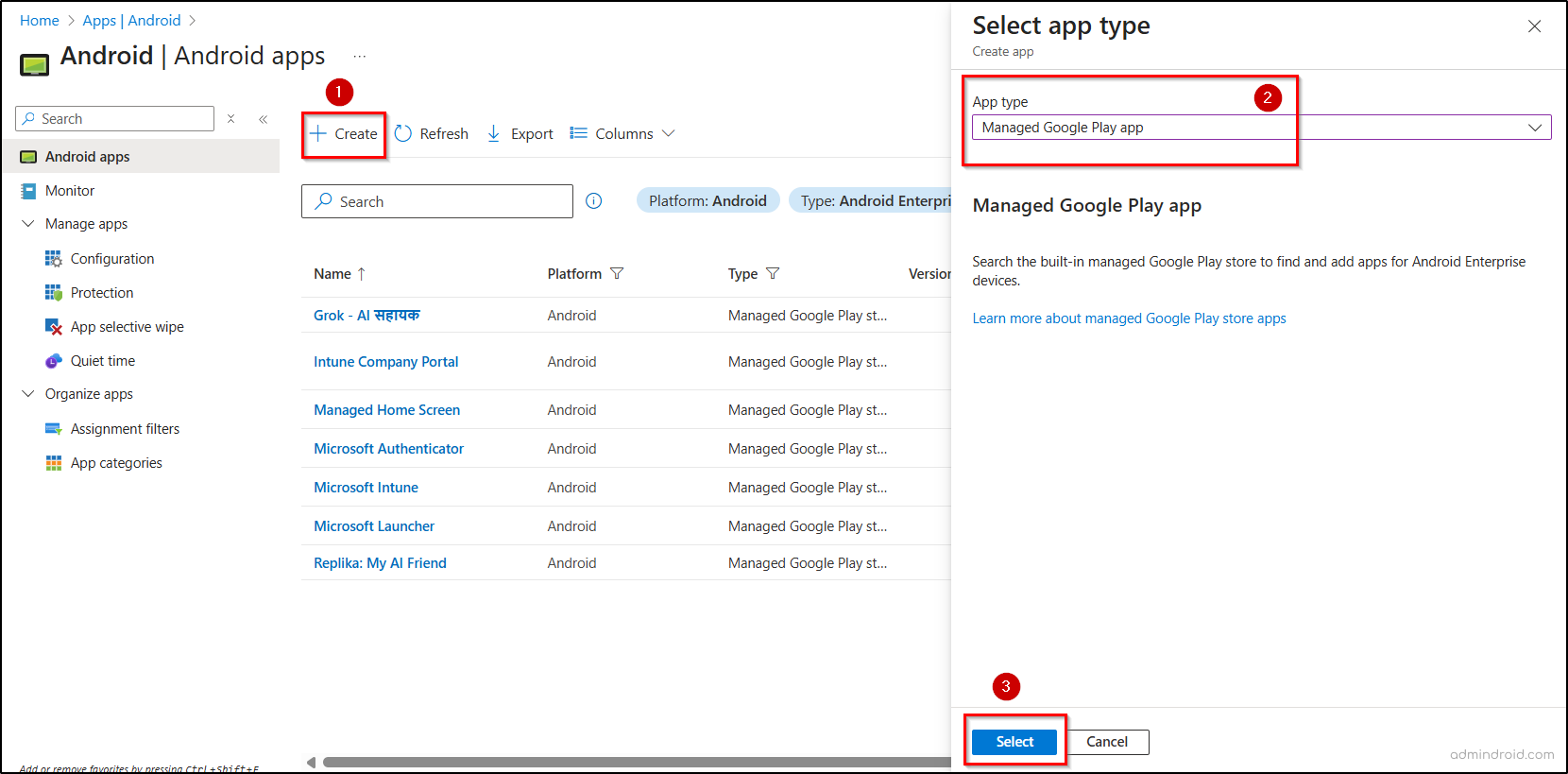
- Go to the Managed Google Play page, search and select the AI app you want to uninstall, click Select, and then click Sync.
- Navigate to the Android apps page, select the unauthorized AI app.
- Under Manage, choose Properties. Click Edit next to Assignments.
- On the Edit application page, deselect all the previous assignments. Then, under Uninstall, add the groups, users, or devices that should have the app removed. Click Review + save, and then select Save again.
After the next sync, the unauthorized AI app will be uninstalled, and users will receive a prompt notifying them that the app has been removed.
Once the app is removed, it will no longer be available in the Google Play Store for reinstallation. And if a user tries to access it directly through a link, they’ll encounter an error.
Tip: You can also use this app restriction method to block risk AI app installations on Android Enterprise personally owned devices with a work profile. This restriction applies only to apps installed within the work profile and does not prevent users from installing apps in their personal space.
2c) Block AI Apps on Android Corporate Owned Devices with Work Profile
Corporate-owned work profile devices are provided by the company and allow personal use. While employees can use personal apps, unregulated AI apps on these devices can inadvertently leak corporate data or compromise compliance.
Here’s how you can restrict AI apps on the personal profile of Android corporate-owned devices using Microsoft Intune. Before proceeding, ensure the AI app you want to restrict already exists in Managed Google Play.
- Go to Android Device Configuration page and select Create > New Policy.
- Set Platform to Android Enterprise and Profile type to Templates.
- Within Fully Managed, Dedicated, and Corporate-owned work profile, choose Device restrictions, then click Create.
- In Basics, enter a name and description, then select Next.
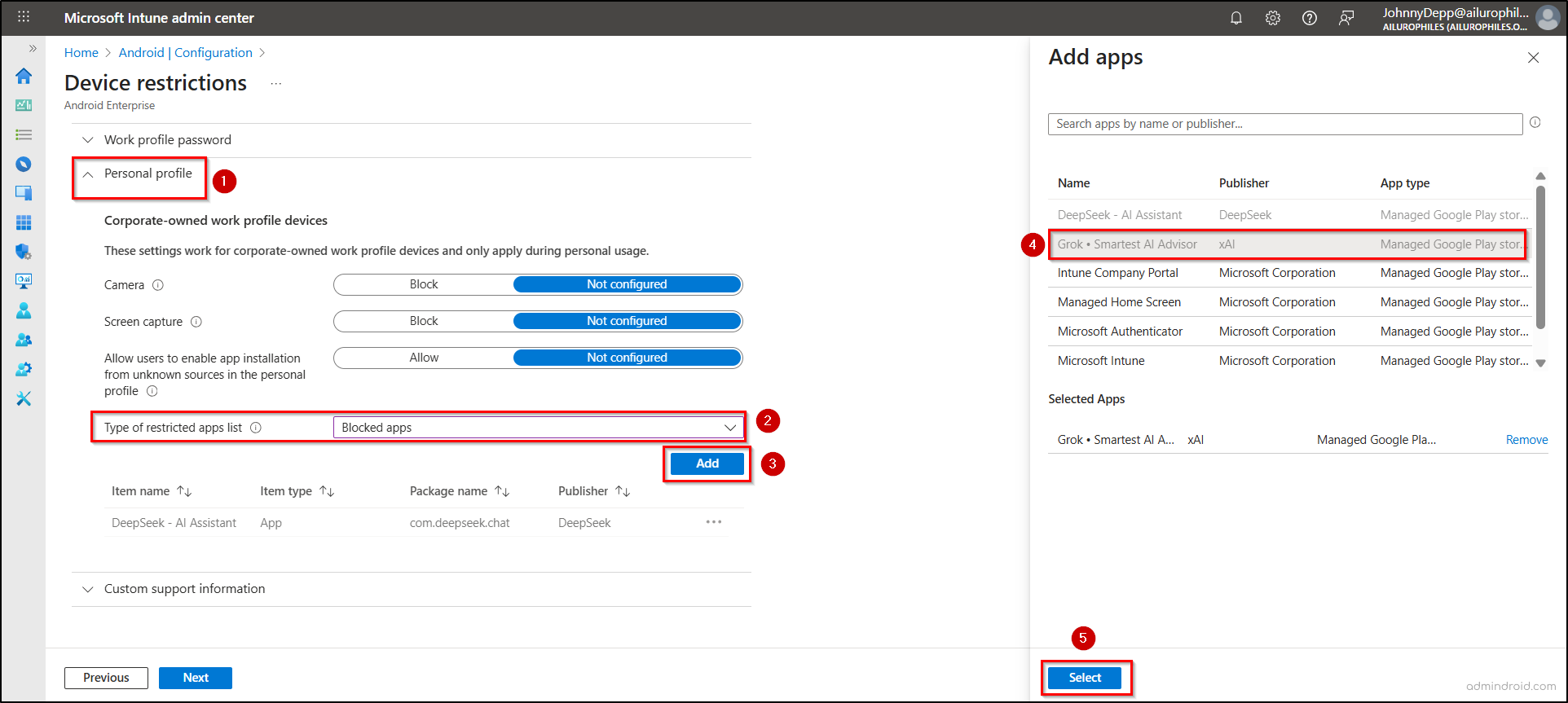
- In the Configuration settings section, open the Personal profile category.
- From the Type of restricted apps list dropdown, select Blocked apps, then click Add.
- Choose the AI apps that need to be blocked. Select Next.
- Assign the policy to a group, all users, or all devices, and click Next. Review the policy and click Create to finalize it.
After deployment, users will see a notification stating that the restricted AI app has been removed and is no longer allowed by their IT admin.
3a) Block Windows Device Website Access in Edge Using Microsoft Defender for Endpoint
Picture an employee trying to visit restricted AI websites for quick research, out of curiosity, or even adding it as a progressive web app (PWA) on their Windows device. With Microsoft Defender for Endpoint, admins can block these sites entirely, preventing both direct access and PWA installations while keeping sensitive data and organizational policies protected.
Let’s start with how to block access to AI websites in the Microsoft Edge browser.
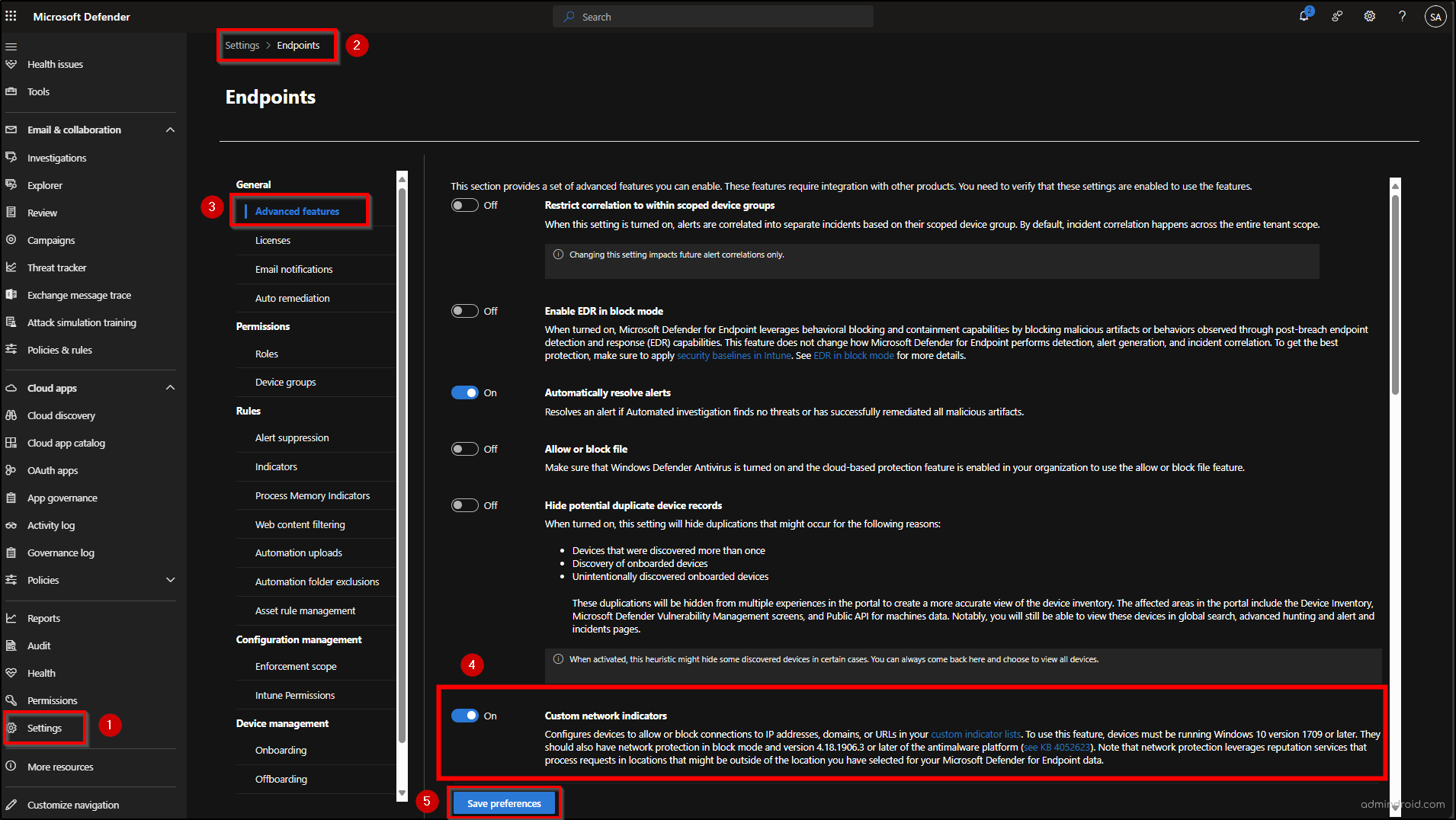
- Go to Microsoft Defender to enable Custom Network Indicators using the following path.
Microsoft Defender → Settings → Endpoints → Advanced features → Custom network indicators → Save preferences.
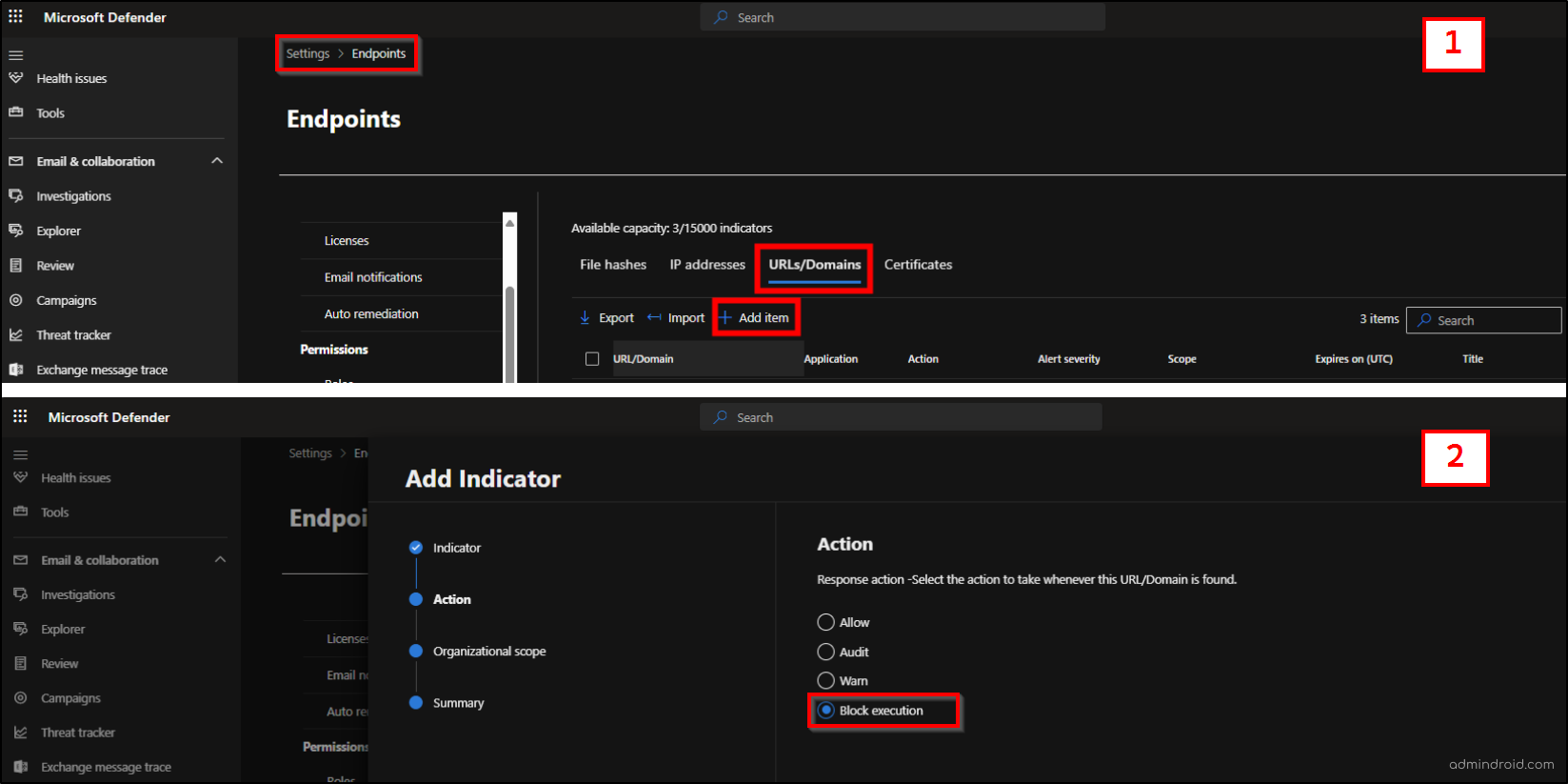
- Once saved, navigate to Settings → Endpoints → Indicators → URLs/Domains → Add Item to create a new custom network indicator.
- Enter the details of the AI website you want to block in your organization, including URL/Domain, Title, Description, and Expires on.
- Click Next. Set Action to Block execution, click Next, review the Organizational scope, and then submit the configuration.
It may take up to 48 hours for the custom network indicator to take effect. Once active, any user attempting to access the site in Microsoft Edge will see a message stating, ‘This website is blocked by your organization.
3b) Block AI Websites in Other Browsers Using Defender for Endpoint
You’ve blocked privacy-intrusive AI websites in Microsoft Edge, but users might try to get around the restriction by opening the same sites in Chrome or Firefox. To close this loophole, admins can extend protection across all browsers using Network Protection, ensuring that AI apps remain inaccessible regardless of which browser employees use.
Note: Ensure that the Custom Network Indicator is enabled and the restrictions are applied, as described in the section above, so you can use Network Protection to extend the restriction to other browsers.
- Open the Windows Device configuration page and go to Create > New policy.
- Under Platform, select Windows 10 and later, and for Profile type, choose Settings catalog. Then, click Create.
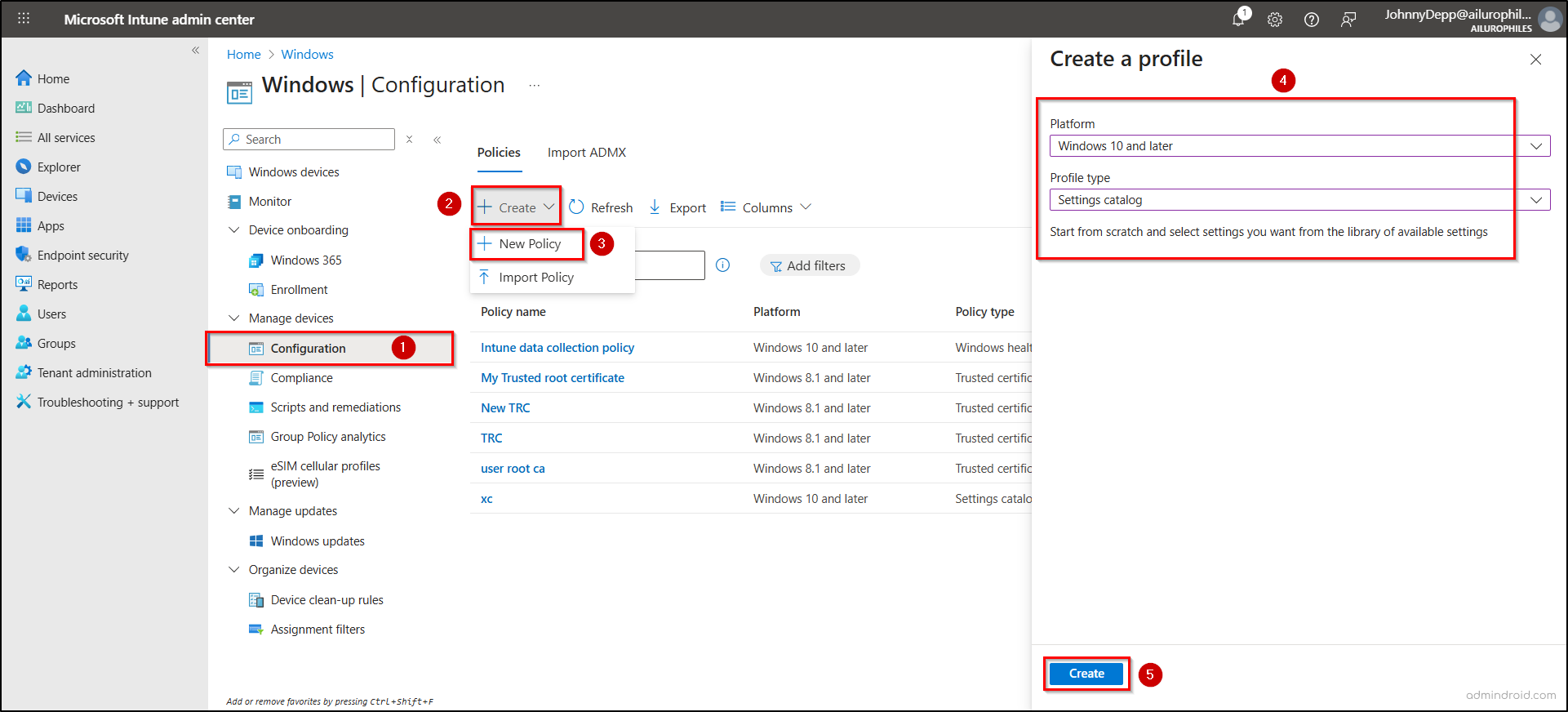
- In the Basics tab, provide a suitable name and description, then click Next.
- Select Add settings under the Configuration settings tab. Under the Selection picker pane, search and select Defender. Then select Enable Network Protection by checking the box.
- Close the settings picker, set the drop-down to Enabled (block mode), and click Next.
- Add scope tags to control access and visibility based on administrative roles. Then assign the policy to a device or user group and click Create.
4a) Enable Network Protection for macOS Devices
macOS devices onboarded to Defender for Endpoint with Network Protection enabled can also be blocked from accessing the restricted AI websites in any browser. This ensures consistent protection across all devices, keeping organizational data secure while maintaining user productivity. The same Custom Network Indicator used for Windows applies to macOS, so make sure it is configured as described earlier in this guidance.
- To enable Network Protection via Microsoft Intune, navigate to:
macOS Device configuration page → Create → New policy → Settings Catalog → Create.
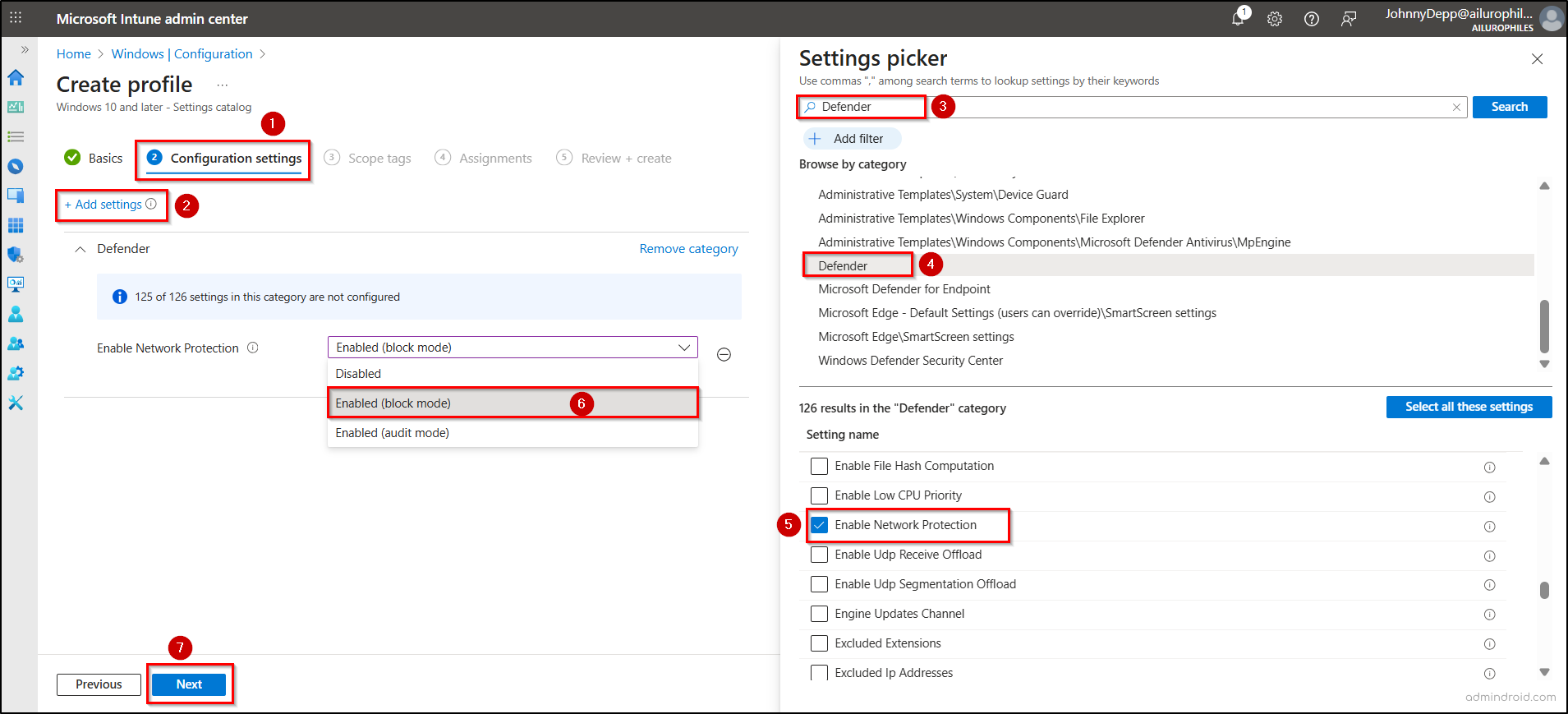
- Provide a name and description under the Basics tab, then click Next.
- On the Configuration settings tab, select + Add settings, search and choose Microsoft Defender Network Protection.
- Check the box next to Enforcement Level and close the Settings Picker. From the dropdown next to Enforcement Level, select Block, then click Next.
- Add Scope Tags as needed, assign the policy to a user or device group, click Next, review the policy, and select Create.
Once applied, users attempting to access any restricted AI website on macOS devices will see a block message or error indicating the site is inaccessible.
With a wide range of options available for corporate-owned devices, let’s now turn to the serious risks of BYOD—the personal devices users bring into the corporate environment.
Block AI Apps Usage on Personally Owned (Bring Your Own Devices) Devices
Users enjoy the flexibility of using their personally owned devices that have been voluntarily enrolled into Intune to access organizational email, apps, and other data. This approach is convenient, familiar, and can boost productivity. However, that freedom comes with hidden risks: unapproved AI apps can easily slip onto these devices, potentially leaking corporate data or bypassing security controls.
While admins have fewer ways to enforce policies on BYOD devices, there are practical strategies to limit AI exposure and protect corporate data.
Restrict Personal iOS Devices with Risky AI Apps from Connecting to Microsoft 365
You can create a compliance policy in Intune to mark an iOS device as compliant or noncompliant based on whether a specific app is installed.
- In Microsoft Intune, navigate to the following path to create a compliance policy.
Microsoft Intune admin center → Devices → iOS/iPadOS → Compliance policies → Create policy → Create.
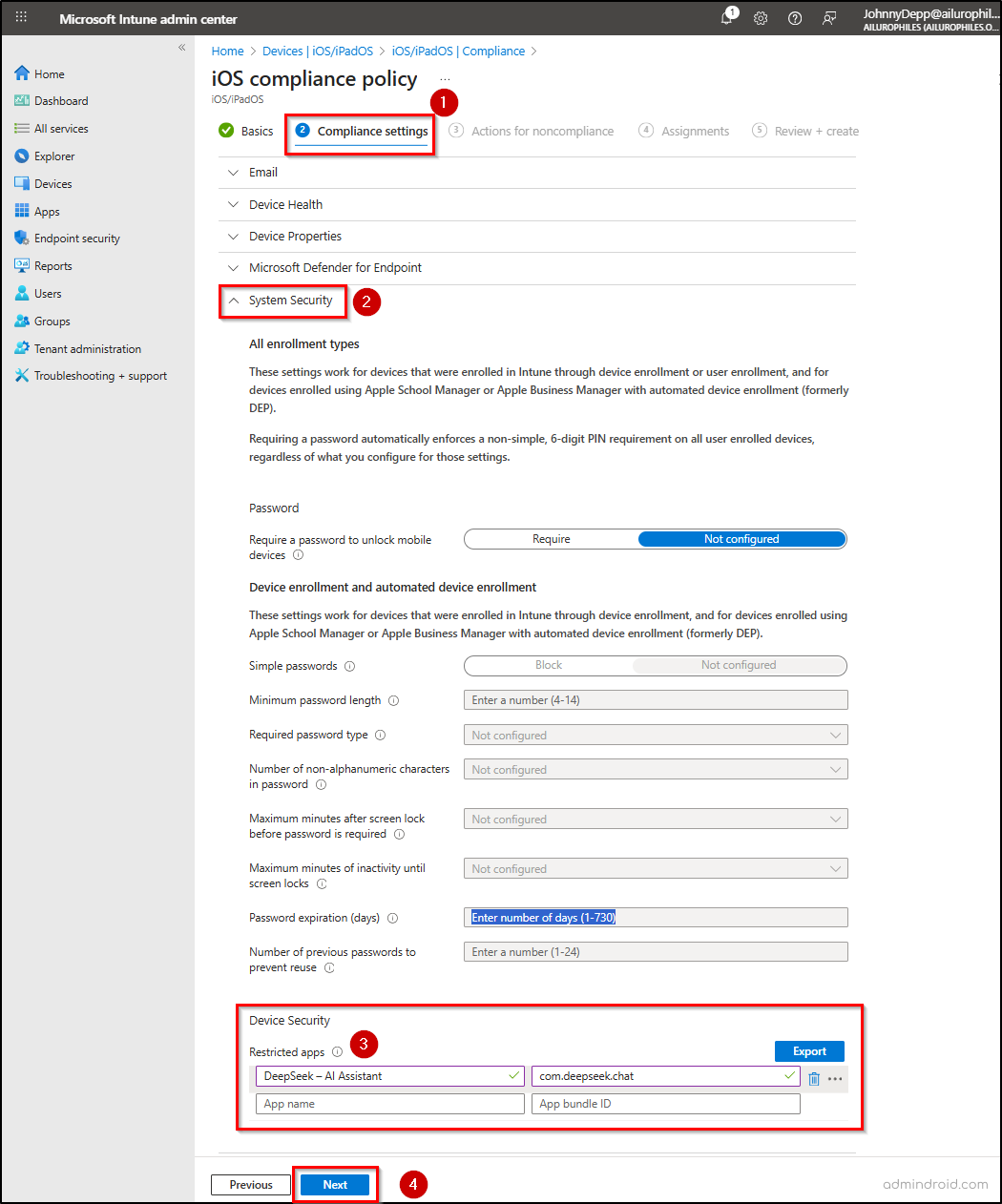
- In the Basics section, enter the policy name and description, then click Next.
- On the Configuration settings tab, go to System security → Restricted apps. Enter the app name and bundle ID, then click Next.
- Under Actions for noncompliance, set it to Mark device noncompliant and Immediately, then click Next.
- Assign the required users, groups, or devices, and click Next.
- Review the policy settings and click Create to finalize.
After creating the compliance policy, go to Monitor →Device status → View report to see which devices are marked compliant or noncompliant based on the app installation status.
Devices with the restricted app installed will appear in the report and be marked as Not compliant. This compliance status can then be used with Conditional Access to block noncompliant devices, preventing users from accessing Microsoft 365 resources from those devices.
Manage the Risky Apps in BYOD iOS Devices Using Microsoft Intune
After identifying devices with the restricted AI app installed, follow the steps below to control or uninstall the app through Intune policies.
- Create a group in Microsoft Entra containing all devices with the restricted app installed.
- Add the restricted app as an iOS Store app in Microsoft Intune by navigating to Apps > All Apps > Create.
- On the Select app type pane, choose the iOS store app and click Select.
- On the App information tab, click Search the App Store, select the app, and click Next.
- Under Assignments, add the device group created in step 1, then click Review + Save to complete the configuration.
Once applied, users on BYOD devices will see an App Management Change prompt asking whether to allow the organization to manage the app.
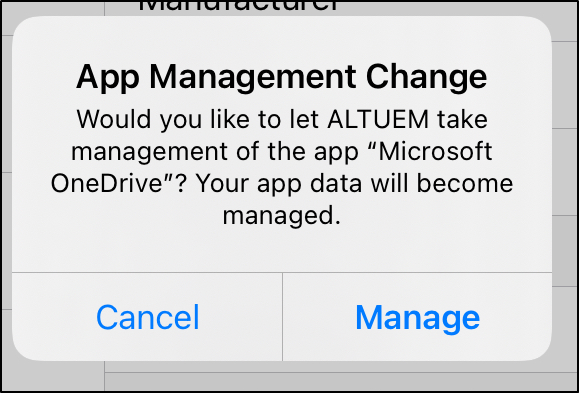
- If the user selects Cancel, the app remains unmanaged. The device will be marked non-compliant, and if a Conditional Access policy requires compliance, access to corporate resources will be blocked.
- If the user selects Manage, the app becomes managed and appears under Managed Apps on the device object in Intune, giving the organization the ability to uninstall it.
To uninstall the managed app:
- Set up a new group containing the device with the restricted app.
- Go to Apps > Prohibited App > Properties > Assignments > Edit.
- Under Uninstall, add the group and choose Included as the mode.
- Then, under Required, add the same group and set it to Excluded.
- Save the changes to initiate the uninstall process.
Note: The method above applies only to iOS/iPadOS devices. On Android devices, apps installed outside the work profile cannot be managed. For other BYOD device types, replacing a personal device with a managed one and enrolling it under Intune remains the recommended approach.
We hope this guide helped you understand how to block risky AI apps on Intune-managed devices and gave practical insights on extending protection to BYOD devices. Additionally, you can leverage features like web content filtering to restrict generative AI usage in your Microsoft 365 environment. Happy reading!