In every organization, devices are the entry point to corporate data. From laptops and phones to tablets, they connect users to apps and the sensitive data that powers everyday work. But what happens if a device isn’t secure — maybe it’s running an outdated OS, is jailbroken, or fails to meet device password requirements?
It only takes one such device to create a gap in your organization’s security posture. And when hundreds of devices connect to your Microsoft 365 environment every day, keeping track of which ones are safe becomes nearly impossible without proper controls.
To manage this challenge, Microsoft Intune provides compliance policies, which act as a security baseline that lets you define the rules determining whether a device meets your organization’s security and compliance standards. This is achieved through compliance policy settings and by creating device compliance policies that enforce specific requirements.
In this guide, you’ll learn what device compliance policies are, how they work, and how to configure them in Intune.
Difference Between Compliance Policy Setting and Device Compliance Policies in Intune
Intune compliance is divided into two parts that work together to determine whether a device is allowed access to resources: Compliance Policy Settings (Tenant-Wide) and Device Compliance Policies (Per-Platform).
- Compliance Policy Settings: The tenant-wide settings tell Intune how to treat devices overall — for example, what to do if a device has no assigned policy or hasn’t reported in for a while.
- Device Compliance Policies: The per-platform compliance policies tell Intune what to check on each device (passwords, encryption, OS version, etc.).
Intune uses both to decide the device’s final compliance status.
➡️ “One provides the framework and the other defines the rules within that framework”.
Now that we know the difference, let’s look at the key component of Intune compliance — the device compliance policy.
What is a Device Compliance Policy in Intune?
A device compliance policy in Microsoft Intune is a collection of rules and settings that specify the minimum security requirements a device must meet to be considered compliant and securely access your organization’s Microsoft 365 resources.
These policies act as a checkpoint — Intune evaluates managed devices against these rules to determine whether they are compliant (meet all requirements) or noncompliant (fail to meet one or more).
You can create device compliance policies in Intune by grouping together specific security requirements. Once defined, these policies can be assigned to particular users or groups, allowing Intune to evaluate their devices against the configured rules.
Common requirements include:
- Enforcing strong passwords
- Enabling device encryption
- Requiring a minimum supported OS version
- Blocking jailbroken or rooted devices
- Verifying device health status
Multiple compliance policies can be created with different rule sets tailored to various departments, roles, or device types, depending on your organization’s security needs and priorities.
If a device doesn’t meet these requirements, Intune marks it as “noncompliant”.
To Which Devices Can You Deploy a Device Compliance Policy
You can deploy a device compliance policy to any managed device in Intune. Once a device is enrolled, Intune can check whether it meets your organization’s security requirements.
You can create compliance policies for the following platforms:
- Android device administrator
- Android AOSP
- Android Enterprise
- iOS
- Linux – Ubuntu Desktop, version 22.04 LTS or 24.04 LTS
- macOS
- Windows
Note: Different platforms support different compliance settings. Each platform requires a separate policy.
Prerequisites for Creating a Device Compliance Policy in Intune
Ensure the following prerequisites are met:
- Devices are enrolled and managed in Intune: Only enrolled (managed) devices can be checked and evaluated for compliance.
- You’ll need either the Intune Administrator, Policy and Profile Manager, or Global Administrator role to create and manage compliance policies.
- Microsoft Intune subscription
- If you plan to use Conditional Access to block or allow devices based on their compliance status, you’ll need an Entra ID P1 or P2 license.
- Ensure your devices run on Intune-supported platforms.
How to Configure Device Compliance Policies in Intune?
Before creating a device compliance policy, the first step is to configure the tenant-wide compliance settings in Intune. These settings define how Intune evaluates devices across your organization and set the baseline for all future compliance policies.
You can follow the steps below in order:
Configure Compliance Policy Settings in Intune
To configure compliance policy setting in Intune, follow the steps below:
- Sign in to the Microsoft Intune admin center.
- Go to Endpoint security -> Device compliance -> Compliance policy settings.
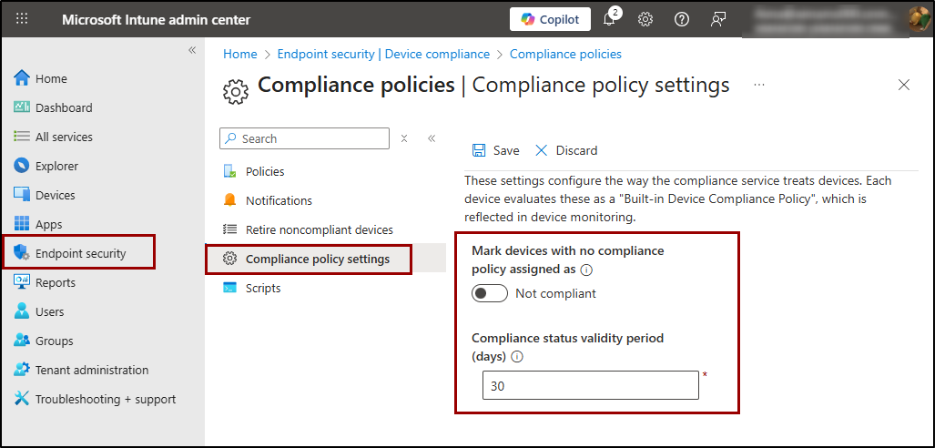
Here, you’ll find two main settings to configure:
- Mark devices with no compliance policy assigned as: This setting defines how Intune should treat devices that don’t have a compliance policy.
- If set to ‘Compliant’: This is the default setting. Any device without a compliance policy is automatically treated as compliant — even if it’s unmanaged or insecure.
- If set to ‘Not compliant’: Ensures that only devices that actually meet your compliance rules can access company resources.
- Compliance status validity period: Specifies how long a device’s compliance report remains valid before it must check in again. The default period is 30 days, but you can adjust it as needed.
For example, if your organization requires frequent compliance checks for high-security environments, you can reduce the validity period to 7 days. This ensures that devices regularly report their status and stay compliant with the latest security requirements.
Create a Device Compliance Policy in Intune
Once you’ve set the tenant-wide compliance rules that define how Intune handles devices overall, you establish the baseline for device security. The next step is to create specific device compliance policies that check security settings on each platform.
- Sign in to the Microsoft Intune admin center.
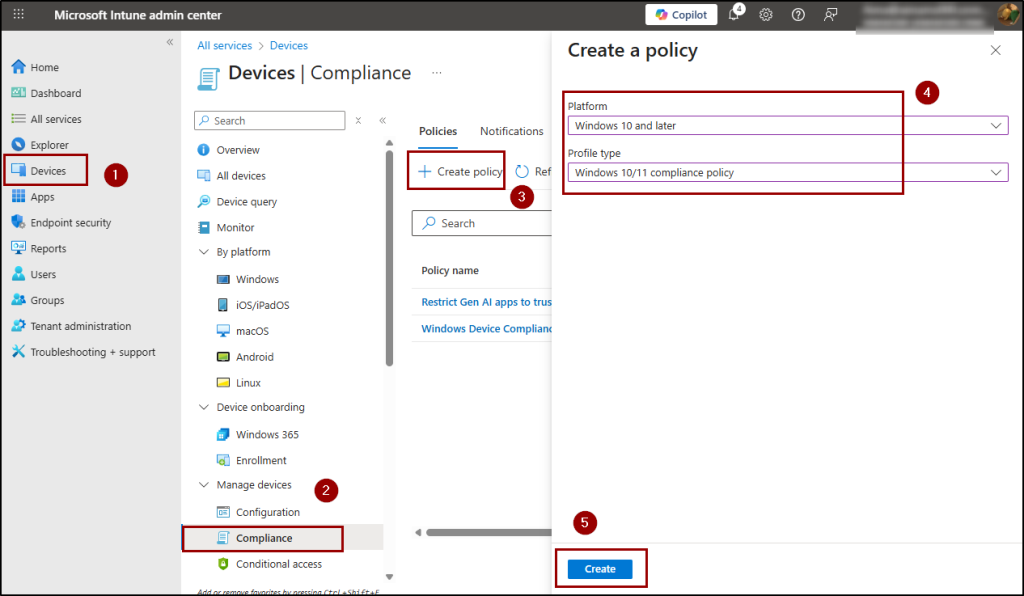
- Select Devices -> Manage devices -> Compliance -> Create policy.
- Select the platform and profile type, then click Create. Profile type is a required sub-category that specifies the intended management method for the device platform.
Each device platform has a required profile type that defines its intended management method. You can also use templates, which are predefined groups of settings organized by functionality, when you don’t want to build policies manually.
4: Basics
- Enter a name and optionally add a description.
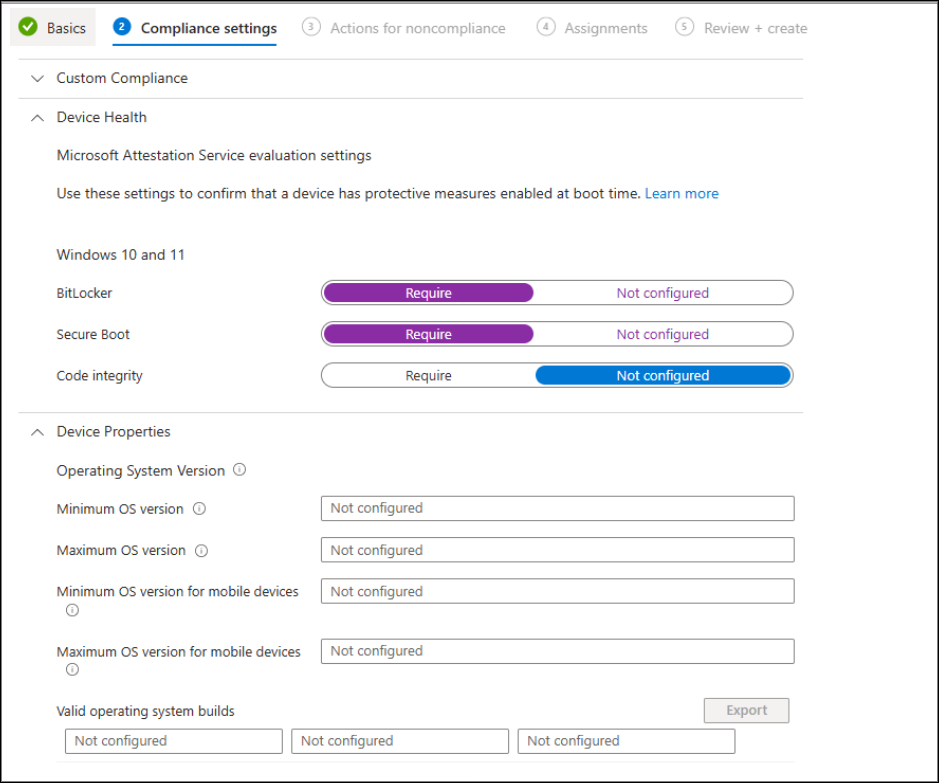
5. Compliance settings: Intune provides predefined categories that group related compliance settings. Under each category, you can configure specific rules that define what makes a device “compliant” in your organization. Once these settings are in place, Intune automatically evaluates enrolled devices against them to determine their compliance status.
- So, expand each category and configure compliance options for your platform (like password requirements, encryption, etc.).
- For Linux and Windows, you can configure custom compliance settings if built-in settings aren’t enough.
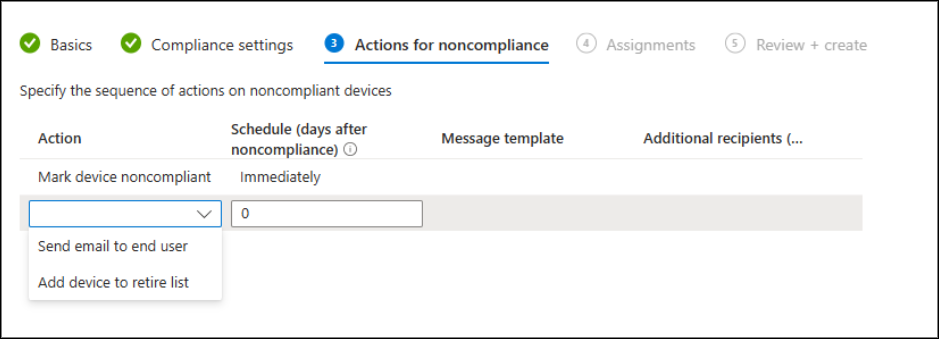
6. Actions for noncompliance
In this step, select the actions that Intune should automatically apply when a device is found noncompliant.
- By default, Intune marks the device as noncompliant.
- You can also add optional actions:
- Send an email to end user: Sends a notification or email to the user, informing them that their device is noncompliant and providing instructions to fix the issue. You must add a message template, specify recipients, and ensure the template includes instructions to help users fix the issue.
- Add device to retire list: Marks the device for retirement, which removes all company data, apps, and settings from the device without affecting the user’s personal data.
Note: You can schedule the retirement 0–365 days after the device is detected as noncompliant. This scheduling controls when the action is applied, but the device remains noncompliant until the action runs.
If your organization has created scope tags, you’ll see a Scope tags tab as the next tab, where you can assign them to control which admins can view or manage the policy.
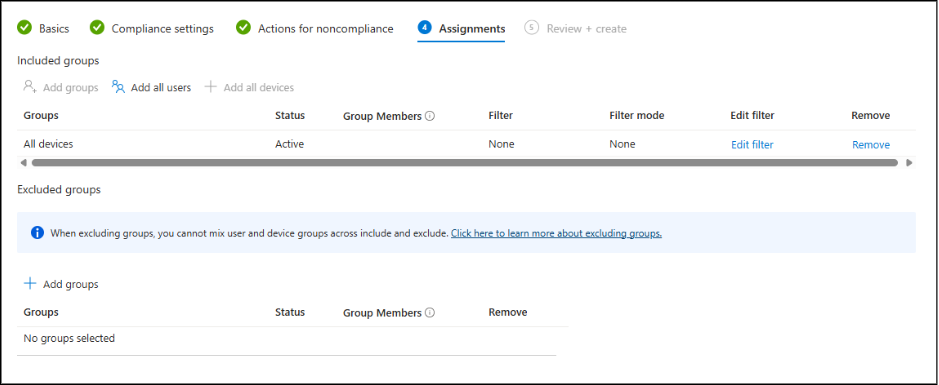
7. Assignments
Here, you can assign the compliance policy to specific groups, all users, or all devices.
- Add Groups: Lets you choose specific user or device groups.
- Add all users: Applies to every user account in the organization.
- Add all devices: Applies to every enrolled device, regardless of who owns it.
- Use excluded groups if certain users/devices should not be affected.
8. Review + create.
- Review settings and click Create.
- Devices will be evaluated for compliance the next time they check in.
Use Conditional Access Policies to Enforce Device Compliance
Creating a compliance policy only identifies whether a device is compliant or not, but it doesn’t automatically stop users from signing in. To add an extra layer of security control, use Conditional Access in Entra ID, which leverages compliance results to enforce access requirements based on device compliance.
To enforce access control based on compliance, you need to pair compliance policies with Conditional Access:
- Sign in to the Microsoft Entra admin center.
- Navigate to Entra ID -> Conditional Access -> Policies -> Create new policy.
- Name your policy using a standard naming convention.
- Under Assignments, add users and target resources.
- Under Access controls -> Grant, select Require device to be marked as compliant.
- Enable the policy and click Create.
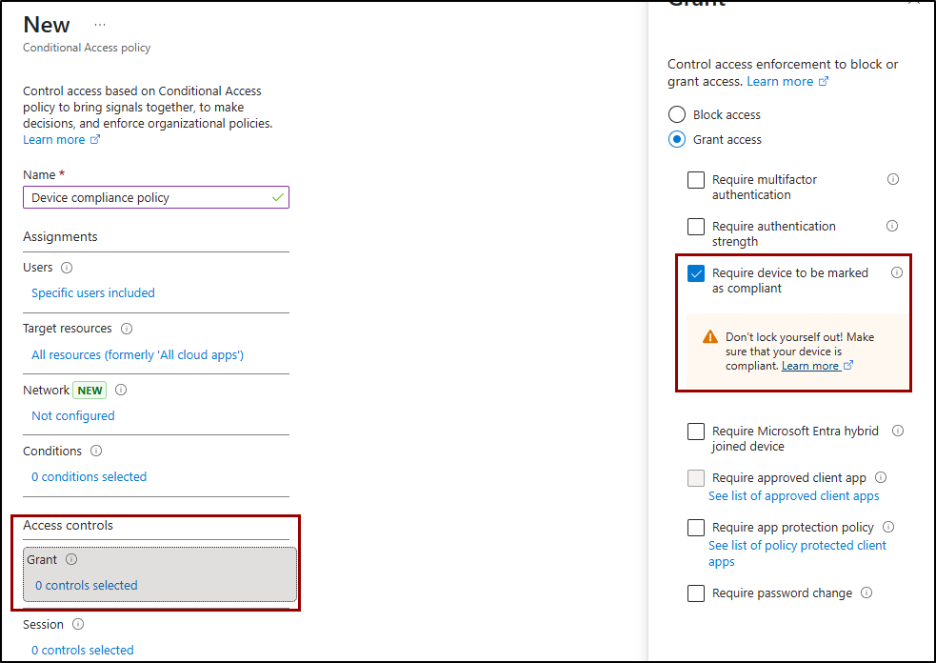
Thus, the device-based Conditional Access policy ensures that only compliant devices can access resources. Any device that’s noncompliant, unenrolled, or not recognized by Intune will be blocked from signing in until it becomes compliant.
How It Works Behind the Scenes:
The compliance policy in Intune evaluates each enrolled device’s health based on your defined conditions. The resulting compliance status is then reported to Microsoft Entra ID, where it’s stored.
When a user attempts to sign in, the Conditional Access policy in Entra checks this compliance flag to determine whether access should be granted or blocked. This seamless integration ensures that only secure, compliant devices can connect to your organization’s resources.
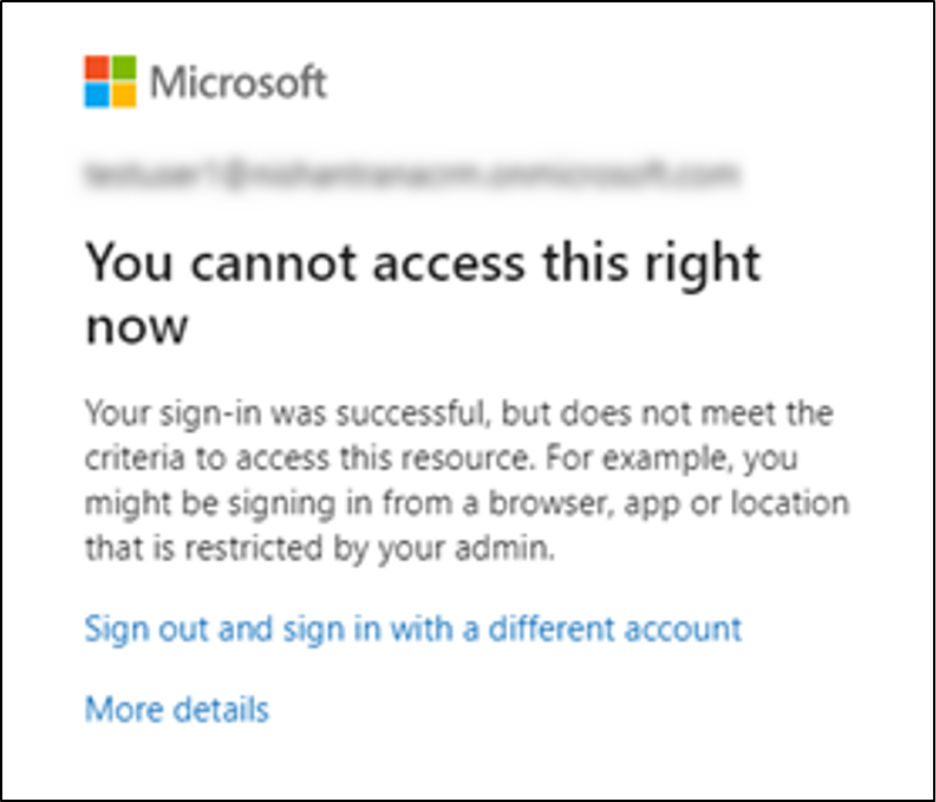
The image below shows the error message displayed when a device is non-compliant and access is restricted:
💡Tip: To ensure your Intune compliance and Conditional Access policies are working effectively, you can use the Conditional Access Optimization Agent. This AI-powered assistant reviews your policies, identifies potential gaps, and suggests fixes.
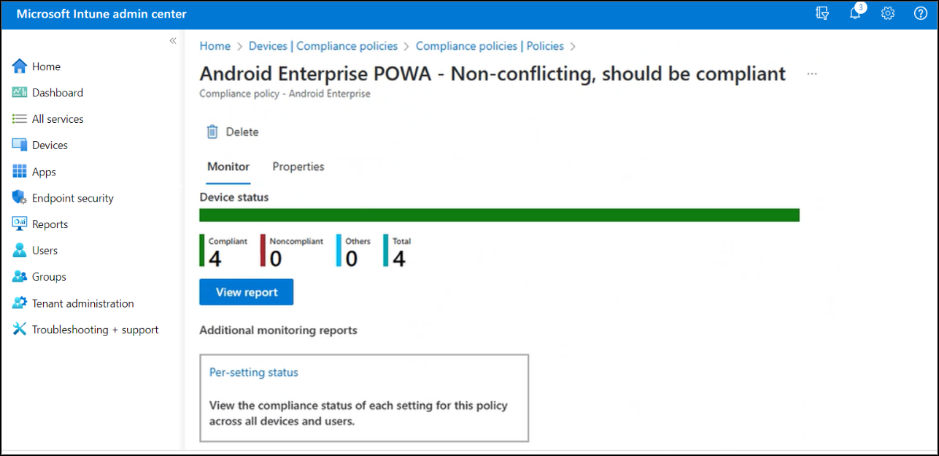
Monitor Device Compliance Policies in Intune
Now, with the policy in place, the compliance dashboard shows insights such as the number of devices that are compliant, noncompliant, or not evaluated. You can also view detailed reports per compliance setting and access additional monitoring reports to track issues across your organization.
You can view device compliance policy reports in the Microsoft Intune admin center by going to:
Devices -> Compliance -> Monitor tab.
That’s it! We hope this guide gives you a clear understanding of how to set up and manage device compliance policies in Intune. Beyond compliance policies, Intune also allows you to block risky apps across managed devices, adding another layer of protection to your organization. Thanks for reading. For more queries, feel free to reach us through the comments section.