⏪The last three years brought so many revolutions and impacted the way people work, learn, and communicate, leading to various trends in Microsoft 365 environment. Some of them are hybrid work environments, high cloud adoption, AI & automation, BYOD trends, etc. But do you realize that this might lead to security and compliance issues?
Among them is the BYOD (Bring your own device) trend, which could gradually put you at high risk without your knowledge. 📲Though this can be convenient as more users access organizations’ data from their personal devices, it can also lead to huge security risks if those devices aren’t properly secured.
But let me suggest you a strong savior to escape these unknown threats- device-based conditional access policies are the way to go! Configure policies now to control access and ensure that only authorized devices can access sensitive data. Here, let me suggest 5 different conditional access policies for devices that you can configure and stay secure for the rest. Let’s get into the spot!
Requirements to Create Device-based Conditional Access Policies
By provisioning a Conditional Access policy for devices, admins can secure corporate resources and enable compliant device users to access services. The device-based conditional access policies can be configured via the Azure portal and Microsoft Intune admin center. But before getting into see the CA policies, let’s see what steps and Office 365 roles are required to start with.
Just a heads up! – Only Office 365 users with specific roles can create Conditional Access policies. So before you start configuring it, make sure you’ve got the right role assigned to you!
- Global administrator
- Security administrator and
- Conditional Access administrator.
NOTE: Azure AD Premium P1 license is required for Conditional Access policies.
REGISTER DEVICES WITH AZURE AD & MICROSOFT INTUNE:
- Also, don’t forget a crucial step before applying device policies – users need to register their devices with the Entra ID device registration service.
- In Microsoft Intune, users can use Workplace join and enroll devices into Intune MDM to receive device-level policies.
Once you’ve got access and let the users know about device registration, it’s time to start the game and create device-based conditional access policies & set up Intune device compliance policies.
Combine Intune Policy Results with Azure AD Conditional Access Policies
Users can bring their personal devices within the organization circle only when they’re registered with Azure AD. As part of the registration process, the device compliance policy will determine the compliance status and report it to Intune and Azure AD. Wondering how can we use this device’s compliance status results?
Let me give an idea on this! So, if you want to control which devices can access your corporate resources, follow the below steps:
Steps to Configure: While creating a Conditional Access policy in the Azure portal, use the access control ‘Require device to be marked as compliant’. Now, Azure AD will use the device compliance status issued by Microsoft Intune to check whether the device is eligible to access the organization network or not.
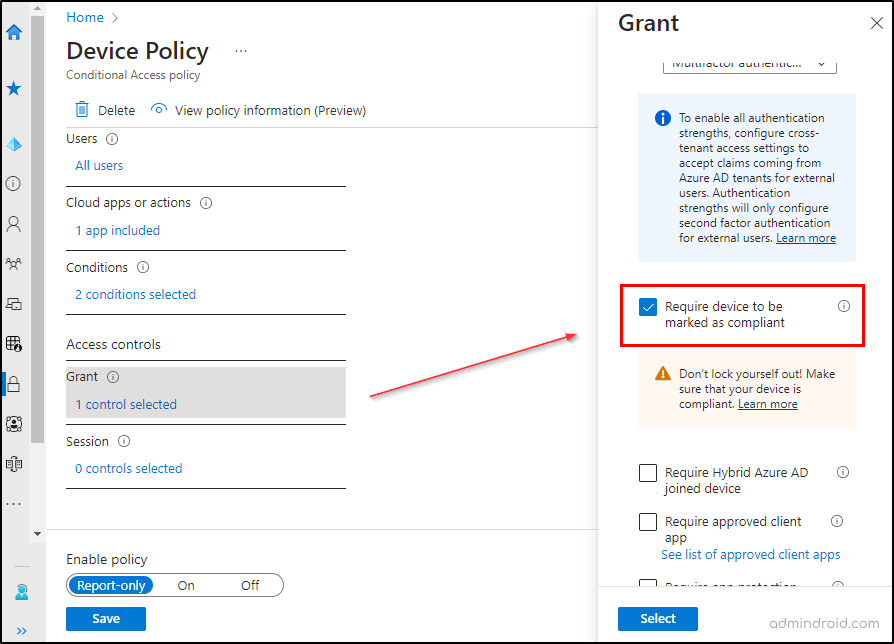
NOTE: To clarify, the Conditional Access feature available through Microsoft Intune is functionally identical to the one offered through Azure AD. However, Intune does offer additional capabilities such as mobile device compliance and mobile app management.
By doing so, you can easily integrate and deploy Conditional Access policies to determine to verify that a device meets configuration and security standards.
5 Must Know Device-based Conditional Access Policies
Remember I talked about the 5 essential device-based Conditional Access policies that should be set up in any Office 365 organization? Well, now it’s time to take a closer look at the policies that can help fortify your device enrollment process and make sure only compliant devices can access your resources.
- Block access for unknown or unsupported device platforms
- Require an approved app or app protection policy for Android & iOS Devices
- Require multi-factor authentication for Intune device enrollment
- Require multi-factor authentication to register or join devices to Azure AD
- Require compliant, hybrid joined devices or MFA
Block Unsupported Platforms with Conditional Access:
What if your users try to authenticate from devices not specified or unidentified by Microsoft? Oopsie, this will pose a significant risk to the company’s data. Therefore, one crucial measure to achieve this is by implementing the policy that ‘Block access to devices for unknown or unsupported device platforms.’
➤ With this Conditional Access policy in place, you’ll have a top-level view of all the devices attempting to access your company’s resources and receive alerts for any unauthorized access attempts, ensuring the IT security team stays in the loop.
You can configure the policy by applying the below controls or plan to use the default CA policy template from the MS Entra admin center.
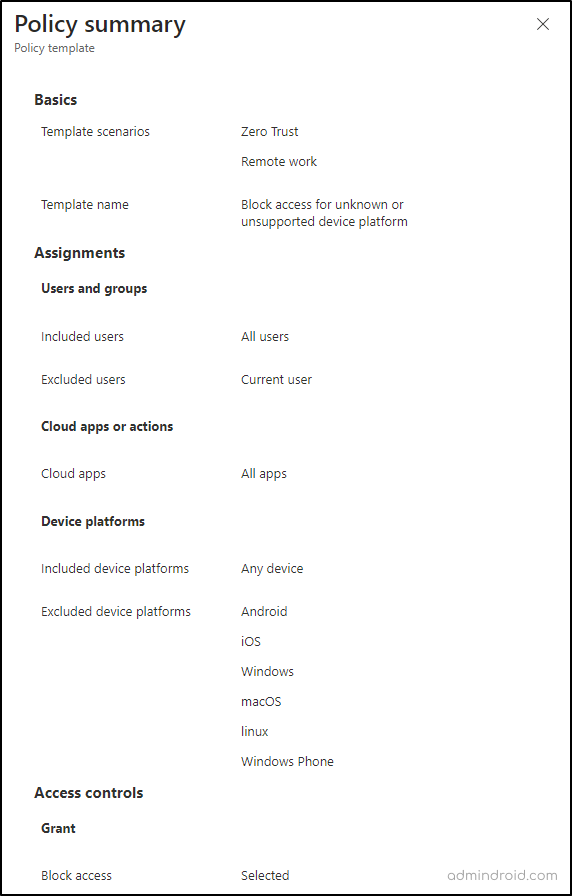
That’s how you configure the policy! Once this is set up, if there’s a sign-in attempt from an unspecified device type, access will be immediately blocked, reducing the potential attack surface for any threats.
Require Approved App or App Protection Policy for Android & iOS Devices:
Imagine a case where a company wants its employees to access data solely through secure and authorized apps. That means they can’t use unapproved email clients or third-party apps to access corporate data. So, to satisfy the above requirement, the Conditional Access policy named ‘Require approved app and app protection” comes as a second hand! When you enable this policy, users need to authenticate using either the approved client app or an app that has the app protection policy
You can configure the policy by applying the below controls or even plan to use the direct Conditional Access policy template.
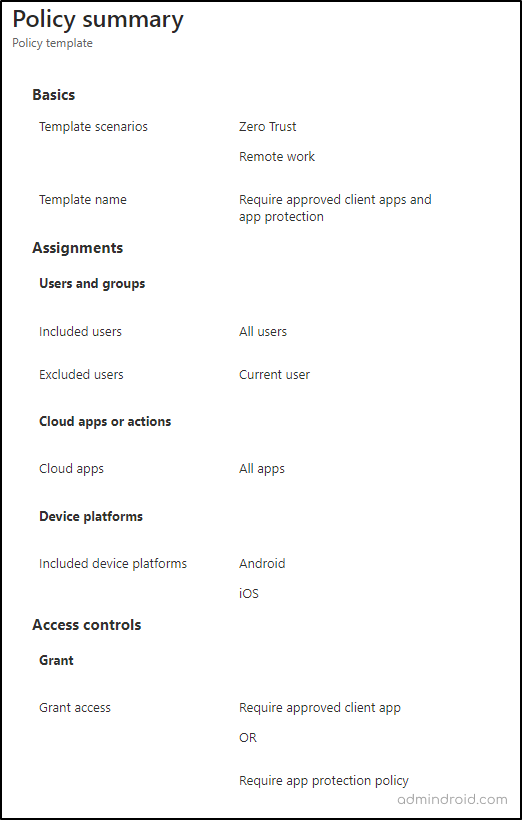
Require Multi-factor Authentication for Intune Device Enrollment:
Perhaps you are wondering why MFA is so specific to Intune device enrollment. Well, let me break down the answer now! Enrolling a device in Microsoft Intune often involves access to sensitive data and resources, which means it typically allows a user to access and manage corporate resources & data from their device. It’s very crucial to ensure that only authorized individuals can enroll devices, since Intune offers remote management capabilities like enforcing security policies, wiping devices, etc.
The only major requirement for this policy is admins must assign Azure AD Premium P1 to users. To enable MFA for Intune device enrollment, follow the steps below.
Microsoft Entra admin Center 🡢 Protect & secure 🡢 Conditional Access 🡢 Policies 🡢 New policy
- Name the policy and mention which users or groups you intend to exclude and include.
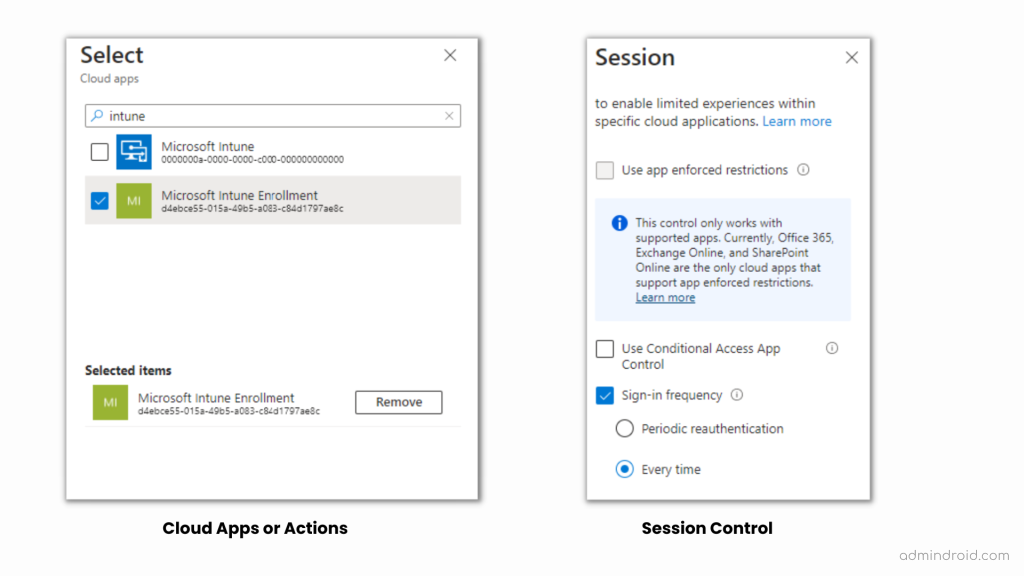
- Then, on selecting the next category, Cloud apps or actions, follow the below step:
Include 🡢 Select Apps 🡢 Select 🡢 Microsoft Intune Enrollment 🡢 Select
- Now, after getting into the Grant section, check in the require multi-factor authentication and require the device to be marked as compliant boxes. And, in the ‘For multiple controls’ box, select the ‘require all selected controls’ option.
- Then, in the ‘conditions’ category, for optimal results, it is recommended to use the device platform in conjunction with Microsoft Intune device compliance policies, or as a component of a block statement.
- As we need MFA to be prompted every time, proceed to the ‘Session’ category and set the ‘Sign-in frequency – Every time’.
- That’s it, done! Now save and enable the policy.
On the effect of this policy, users will see a one-time MFA prompt when they enroll device in Microsoft Intune. Overall, there is no reason to say no to MFA for Intune Device Enrollment! Therefore, requiring MFA can help improve the security of an organization’s data and resources and protect against attacks such as phishing. Now, with the new external authentication methods in Microsoft Entra support, you can also select your favorite third-party identity provider to fulfill MFA requirements during sign-in.
Require MFA to Register or Join Devices with Azure AD
Enforcing MFA for device registration in Azure AD is both more important and recommended as it provides an additional authentication factor that prevents attackers from accessing organization resources, even if they steal user credentials. So, follow the below steps and require MFA while users register their devices in Azure AD.
Microsoft Entra admin Center 🡢 Protect & secure 🡢 Conditional Access 🡢 Policies 🡢 New policy
- Name the policy and mention which users or groups you intend to exclude and include.
- Then, on selecting the next category, Cloud apps or actions, follow the below step:
➤Change the Cloud apps setting to User actions.
➤Tick the check box, Register or join devices.
- Now, after getting into the ‘Grant’ section, check in the Require multi-factor authentication check box.
- That’s it, done! Now save and enable the policy.
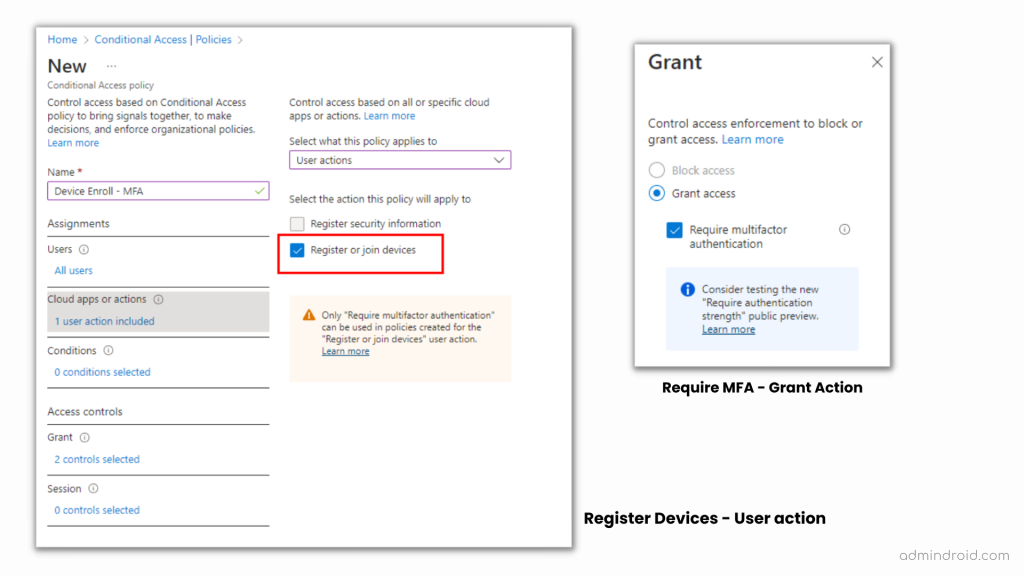
Overall, requiring an MFA to register or join devices with Azure AD is the best choice admins would make! Configure this setting now and protect your organization’s resources from unauthorized access and comply with security regulations.
The Basic Common Policy – Require Compliant, Hybrid Azure AD Joined Device or MFA for All Users
So, requiring compliant, hybrid joined devices or MFA for all Office 365 users is the best practice ever. Because that will eventually keep your data & networks secure, ensure compliance with industry regulations, and build trust with stakeholders.
Therefore Microsoft has provided a default policy template named “Require MFA to Register or Join Devices with Azure AD” to ease your process. You can either follow the below steps mentioned in the figure or opt to implement the policy template.
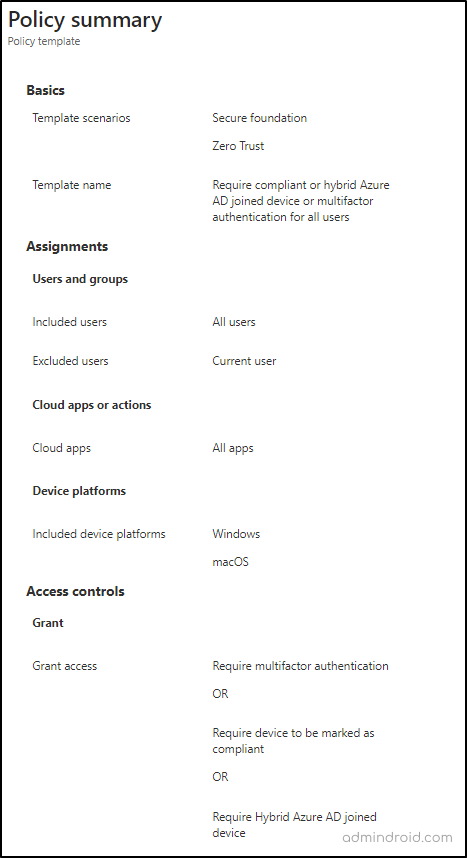
In conclusion, don’t let BYOD put your organization at risk! Implement these policies now, monitor Conditional Access policy changes, empower the device enrollment process, enforce strict device-based access controls, and leverage device-related Microsoft Secure Score recommendations to further enhance device security. These policies provide a simple and effective way to ensure that only authorized devices can access your organization’s data and networks.
Remember, in the world of cybersecurity, prevention is always better than cure! Still thinking about what to do? Take action now and implement these essential policies, including Secure Score recommendations, to stay one step ahead of pesky security threats.






