We are obviously in an AI-agent era, where these digital workers are quietly becoming the new shadow workforce. They write code, analyze data, move files, build workflows, and handle tasks we once expected only humans to do. Helpful? Absolutely. But this is also where the real problem begins.
As AI becomes more accessible, users across the organization are creating agents every day—through Microsoft Copilot, Azure AI Foundry, and countless third-party tools. Agents are multiplying fast, but our ability to see them, manage them, or secure them hasn’t kept up.
That’s why Microsoft first introduced Microsoft Entra Agent ID in May 2025 to help organizations gain basic visibility into how many AI agents they have. Now, at Ignite 2025, Microsoft has expanded these capabilities and announced the Public Preview, bringing the visibility, protection, and control organizations urgently need for this new AI-driven world.
In this blog, let’s explore what Microsoft Entra Agent ID is and how it helps you with the new capabilities.
What is Microsoft Entra Agent ID
Microsoft Entra Agent ID is an identity and security framework designed to help organizations securely manage, govern, and protect their digital teammates, AI agents. When Microsoft released the initial preview in May, the goal was simple: give organizations visibility into how many AI agents they have using the Enterprise Applications view in Microsoft Entra.
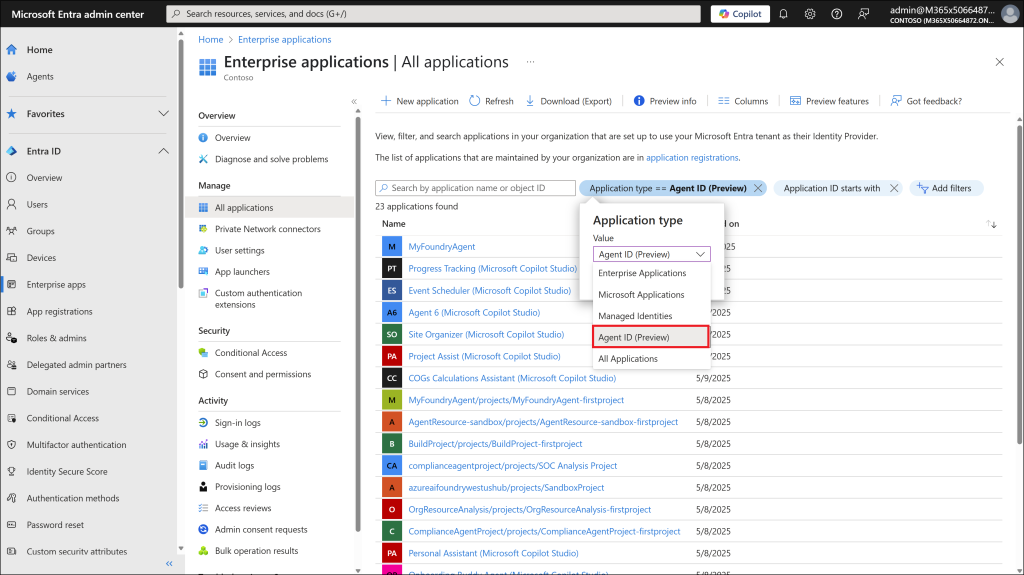
Now, Microsoft has expanded Entra Agent ID beyond basic visibility. It allows you to register agents with proper identities, control their permissions and lifecycle, and apply the same security infrastructure, like Conditional Access, identity protection, and network controls, that you already trust for workload identities.
This ensures every AI agent, whether built in-house, created in Copilot Studio, or coming from third-party platforms, operates securely in your tenant.
What are the New Capabilities in Microsoft Entra Agent ID
With the expanded preview, Microsoft Entra Agent ID now has three major capabilities to manage AI agents just like humans and workload identities.
1. Register and Manage AI Agents in Microsoft Entra
One of the biggest challenges organizations face today is AI agent sprawl—agents being created across Copilot Studio, Azure AI Foundry, Power Platform, SaaS applications, and even third-party tools, often without IT visibility. This results in unmanaged identities, unknown access paths, and security blind spots.
Microsoft addresses this challenge directly with the Register and Manage capability in Entra Agent ID. This feature gives organizations a centralized, consistent, and secure way to identify every AI agent running in their environment, no matter where it was created.
How to View and Manage All Agents in Microsoft Entra
- Sign in to the Microsoft Entra admin center.
- Navigate to Entra ID → Agent ID (Preview).
Here, you’ll see a dedicated workspace that provides full visibility into all AI agents in your tenant
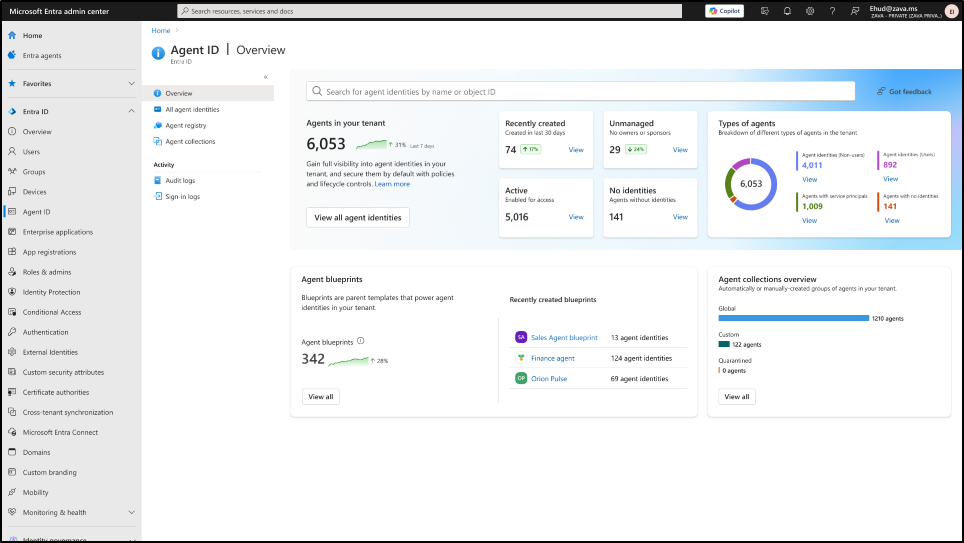
Overview: Complete Visibility Over AI Agents
The uncontrolled proliferation of agents often leads to unmonitored access and excessive permissions. The Overview section is your antidote to this chaos.
This acts as a single pane of glass, giving you a complete list of all agents operating in your organization, regardless of whether they were created by a developer, a third-party tool, or a Microsoft service. This immediate visibility helps you spot unauthorized agents, agents without identities, and prevent agent sprawl.
The overview provides crucial, at-a-glance details, like
- Total agents in your tenant
- Active agents
- Agents without owners or sponsors
- Recently created agents
- Types of agents
- Agent blueprints, and much more.
All Agent Identities: Purpose-Built Identity for AI Agents
This section lists every agent identity created in your Microsoft Entra tenant. These identities are special identity accounts in Entra ID designed specifically for AI agents. An agent identity acts as the primary account an AI agent uses to authenticate to various systems. Each agent identity has two identifiers, the Object ID and the App ID, which always share the same value. This consistency makes them reliable for authorization and access decisions.
Agent identities do not use passwords or secrets. Instead, they authenticate only using access tokens issued to the platform or service where the agent runs. This eliminates the risks associated with stored credentials and aligns with Zero Trust principles.
You can create agent identities in Microsoft Entra either through Graph API or PowerShell.
Agent Registry: Central Repository for All AI Agents
The Agent Registry acts as the central source of truth for all AI agents in your organization. As AI adoption grows, IT teams are left dealing with blind spots, inconsistent governance, and discovery challenges.
The Agent Registry solves this by maintaining rich metadata for every registered agent, who created it, where it runs, what capabilities it has, and how it should be governed. Instead of hunting through individual apps or custom logs, administrators get a unified catalog of all agents across Microsoft and non-Microsoft ecosystems.
Agent Collection: Organized Governance for Agent Groups
It helps you logically organize agents based on trust level, visibility, purpose, or business logic. Instead of managing agents individually, collections allow you to group them and apply shared governance controls at scale. Microsoft includes several built-in collections, such as Global and Quarantined. These built-in collections ensure that even newly registered agents fall into an appropriate trust boundary immediately. You can also create custom collections tailored to your environment.
Note: During the preview phase, each collection can contain up to 100 agents, but there is no limit on the number of custom collections you can create.
2. Govern Microsoft Entra Agent Identities and Lifecycles
Once an AI agent gets its own identity in Microsoft Entra, the next critical step is making sure it only has the right level of access—not too much, not too little, and never permanently. This is where Microsoft Entra Agent ID brings human-grade governance to machine identities.
AI agents operate very differently from people. They spin up quickly, run automated tasks, and may exist for minutes or hours instead of months or years. Without proper lifecycle controls, an agent can easily end up with excessive privileges or leftover access long after it’s no longer used. Entra Agent ID solves this by applying the same identity governance framework you already use for your users.
Once an agent identity is created for an AI agent, you can assign access through access packages in Microsoft Entra. This ensures every permission is intentional, reviewed, and logged. With access packages, you can assign the following permissions to the AI agents:
- Security groups
- Application roles
- API permissions
- Microsoft Entra roles
3. Protect AI Agents with Microsoft Entra Agent ID
AI agents in Microsoft 365 make real-time decisions, adapt their behaviour based on incoming data, respond to user input, and interact with systems depending on environmental conditions. This flexibility introduces several security challenges, like an expanded attack surface, agent sprawl, shadow AI, over-privileged access, and compliance gaps.
These risks vary depending on the agent’s purpose and where it runs. That’s why Microsoft Entra Agent ID extends the same Zero Trust protections used for human and application identities to your AI agents. It ensures every agent follows strong identity, access, and governance controls, no matter how quickly they’re created or how dynamically they operate.
Let’s take a look at the key security features Microsoft Entra Agent ID provides for AI agents.
- Conditional Access policy in Microsoft Entra
- Identity protection for Microsoft Entra AI agents
- Network control to secure AI agents in Microsoft 365
Conditional Access for Agent ID in Microsoft Entra
Conditional Access treats AI agents as first-class identities and evaluates their access requests using agent-specific signals. This means every AI agent is subject to the same Zero Trust checks as any human or application identity when requesting a token for a resource in your tenant.
Imagine you want to block high-risk AI agents from accessing any organizational resources. With Conditional Access, you can enforce this with just a few steps:
- Sign in to the Microsoft Entra admin center with Conditional Access admin permissions.
- Navigate to Entra ID → Protection → Conditional Access.
- Click + Create new policy and give your policy a name.
- Under Assignments, include All agent identities.
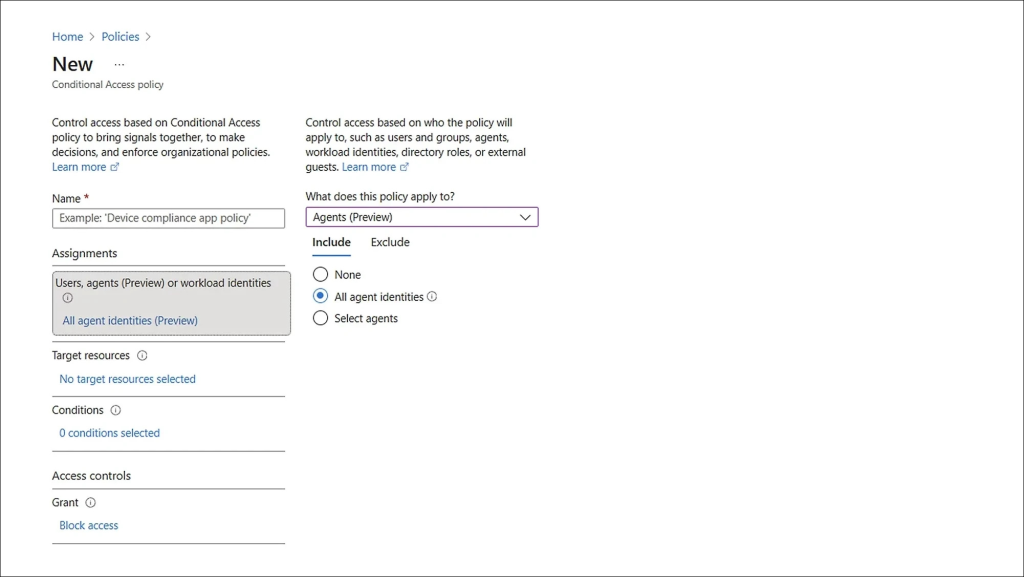
- Under Target resources, include “All cloud apps” or the specific resources you want to protect.
- Under Conditions, open Agent risk (Preview) and set “Configure to Yes”. Also, choose the risk levels to trigger the policy based on your organization’s requirements.
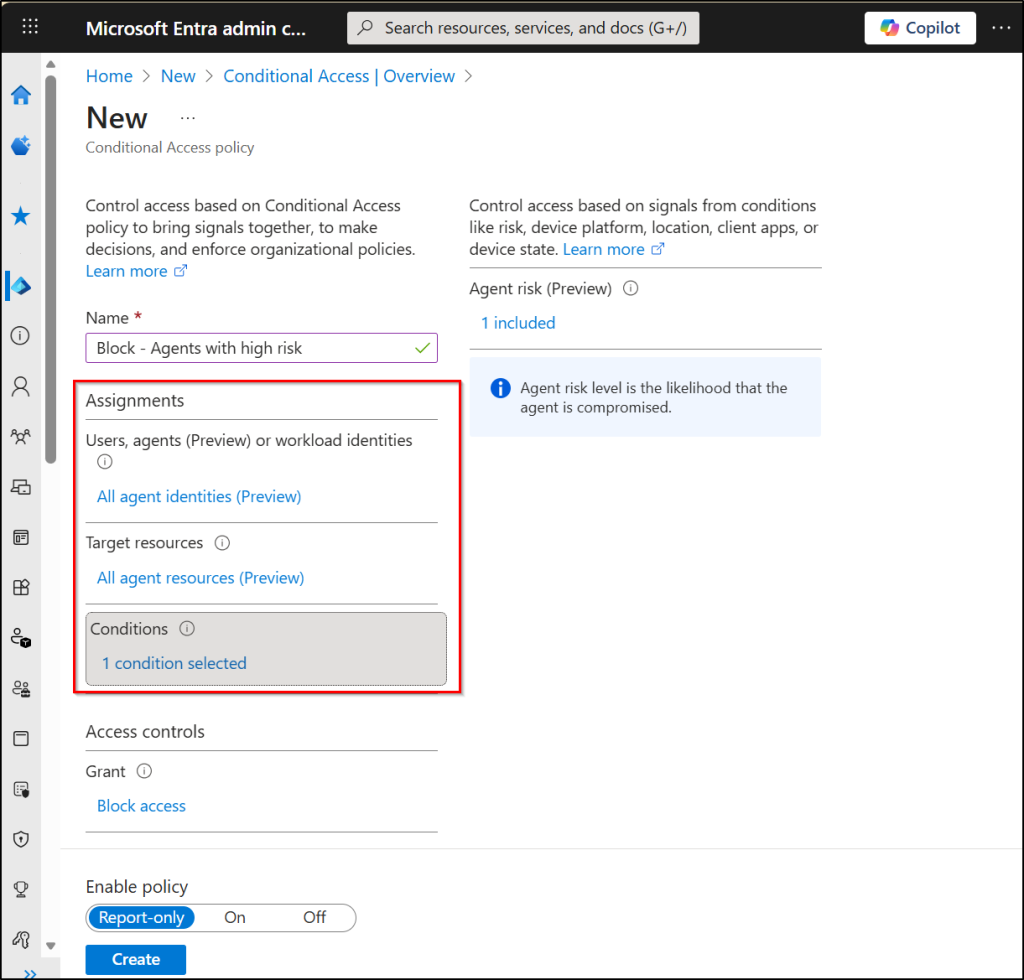
- Under Access controls, choose Block access and click Select.
- Set Enable policy to ‘Report-only’, review your settings, and click Create to apply the policy.
Validate the CA policy behavior using the Microsoft Entra sign-in logs. If everything works as expected, switch the toggle from Report-only to On to enforce the policy across all AI agents. After the policy is enabled, Microsoft Entra will automatically block any AI agent flagged as high-risk from accessing your protected resources.
Identity Protection for Microsoft Entra AI Agents
Continuous monitoring is essential to keep AI agents safe throughout their lifecycle. Microsoft Entra ID Protection helps by automatically detecting and responding to identity-related risks in agent activity. It builds a baseline of what “normal” behaviour looks like for each agent and continuously evaluates their sign-ins and actions.
When an agent behaves unusually, Entra ID Protection flags the activity and marks the agent as risky. Risk is calculated based on several anomalous behaviours, such as:
- Unfamiliar resource access – when an agent tries to access resources it normally never touches.
- Sign-in spikes – a sudden increase in sign-ins compared to its usual pattern.
- Failed access attempts – repeated failures when trying to access resources it doesn’t have permission to use.
- Sign-in by a risky user – when an agent attempts to sign in on behalf of a user flagged as risky.
- Confirmed compromise – when an admin manually confirms that the agent identity is compromised.
- Threat intelligence signals – Microsoft detects activity that aligns with known attack patterns.
You can view all risky agents directly in the Risky Agents report inside Microsoft Entra Identity Protection. This report provides key details such as agent display name, ID, risk level, risk state, agent type, and sponsor.
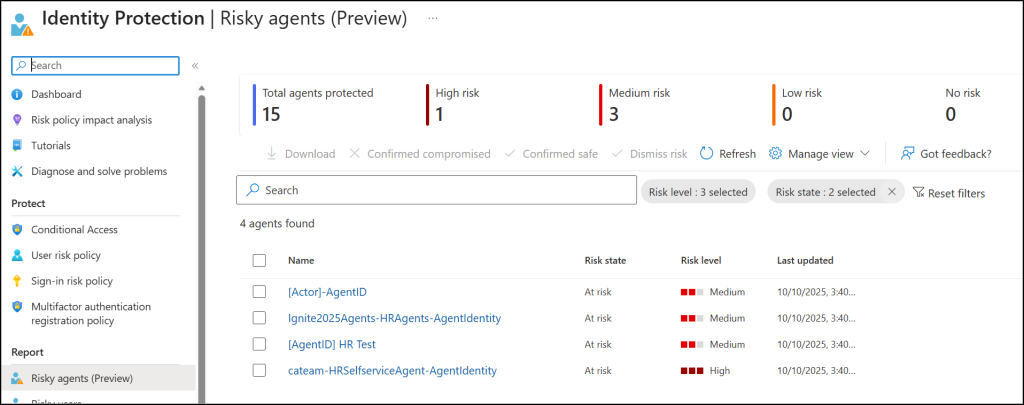
Once you’ve identified risky agents, you can take immediate action from within the report, such as confirming compromise, dismissing the risk, or disabling the agent identity entirely.
Network Controls for AI Agents in Microsoft Entra
Once an AI agent is authenticated and authorized, the next challenge is controlling where it can go and what it can do on the network. Even a well-permissioned agent can still pose a risk if it connects to malicious domains, uploads sensitive files, or interacts with unsafe APIs.
With Microsoft’s Global Secure Access, Entra Agent ID brings network-level protection directly to AI agents. This gives you visibility, policy enforcement, and threat prevention across every connection your agents make.
Global Secure Access lets you log all network activity performed by your AI agents. With this visibility, you can:
- Audit the URLs, APIs, and services an agent contacts
- Detect suspicious or unusual traffic patterns
- Investigate policy violations or risky destinations
- Maintain compliance across agent-driven data flows
This makes it far easier to identify anomalies early—before they turn into security incidents. You can further strengthen agent protection by applying network policies such as:
- Web categorization for APIs and MCP servers
- Restrictions on file uploads and downloads
- Automatic blocking of malicious destinations
These controls ensure AI agents interact only with safe, approved, and compliant endpoints, closing one of the largest attack surfaces.
In conclusion, by combining centralized visibility, lifecycle governance, and protection, Entra Agent ID ensures your AI agents operate with the same Zero Trust rigor you expect for human and application identities. Whether an agent is built in-house, generated through Copilot tools, or provided by third-party platforms, you get consistent guardrails, clear ownership, and complete control.
As AI adoption accelerates, securing agents isn’t optional—it’s foundational. With Entra Agent ID, we hope your organizations can embrace AI, knowing every agent is managed, governed, and protected from the moment it comes to life.
Stay tuned for more rollout announcements and updates as Microsoft brings additional capabilities to this rapidly evolving AI era.






