Recently, remote work has become increasingly popular. Rather than being limited to the traditional office-based working system, users have switched to an “anywhere-anytime” culture. As a result, users have now started to communicate using multiple devices.
There has been lots of positive feedback from employees since this switch, as it reduces costs, increases flexibility, and increases productivity, but in the long run, it is not as easy as it seems. Having a remote work culture can pose multiple risks for your organization, like causing serious security implications and making it difficult to monitor the performance of employees.
Out of these, the most vulnerable ones that might not seem as risky but cause potential danger to the organization are unmanaged devices. Unmanaged devices are the means by which attackers perform their malicious activities. Using unmanaged devices in an insecure network causes Office 365 users to be likely to lose huge enterprise data.
So let’s follow up on this blog by exploring what Azure AD unmanaged devices are, how unmanaged devices pose risks to businesses, and also how to monitor these devices.
What are Office 365 Unmanaged Devices?
Unmanaged devices are devices that are not actively managed and monitored by your IT department. Devices such as mobile phones, printers, etc., fall within these categories.
Businesses generally benefit from allowing their employees to work from anywhere with any device as long as they take the necessary safety precautions. Even though unmanaged devices in Azure AD have many benefits, they also carry some risks. When unmanaged devices (BYOD) are not fully understood, they can pose a security risk to business systems.
For this reason, it’s better to either limit device access or monitor access from unmanaged devices. Below are a few ways to mitigate the increased business risks associated with unmanaged devices in Office 365.
Block Access from Unmanaged Devices:
BYOD(Bring your own device) approaches pose a higher risk of complications, so it’s essential to ensure all privacy and security issues are addressed. Therefore, it’s a good idea to block access to cloud apps from unmanaged devices.
As a result, conditional access policy for unmanaged devices is one supreme feature that allows one to access unmanaged devices securely. You can also restrict device registration using Entra ID device settings.
Steps to Block Access to Microsoft 365 Resources from Unmanaged Devices:
Following are the configuration steps to create an Azure AD conditional access policy that completely blocks access for all apps and services in your organization.
- Open the Azure AD portal.
- On the left side of the Azure AD portal, click Azure Active Directory.
- Next, select the Security tab under the Manage section in the left pane.
- Further, move on to select Conditional Access under the Protect section.
- Then, proceed to click on the New policy to create a conditional access policy to block access to Office 365 apps or selected services.
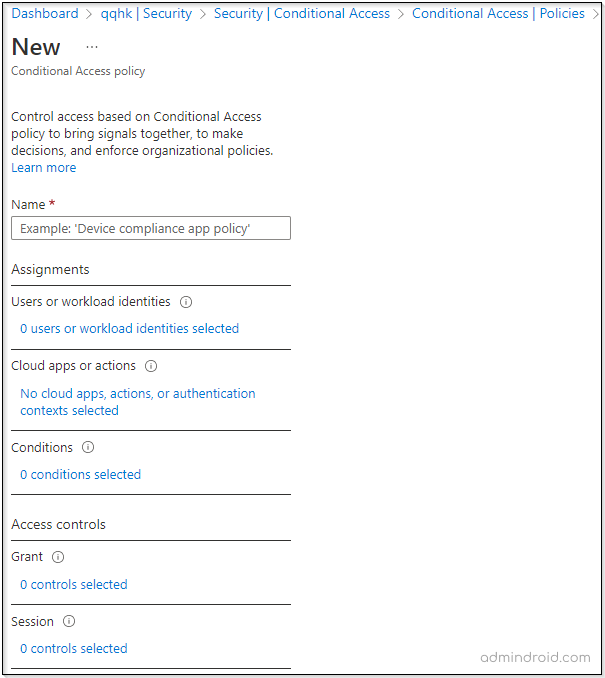
6. Under cloud apps or actions, if you wish to restrict access to Office 365 apps and services via mobile apps or personal devices, you can select the Office 365 apps. This will prevent all access to Office 365 apps and services.
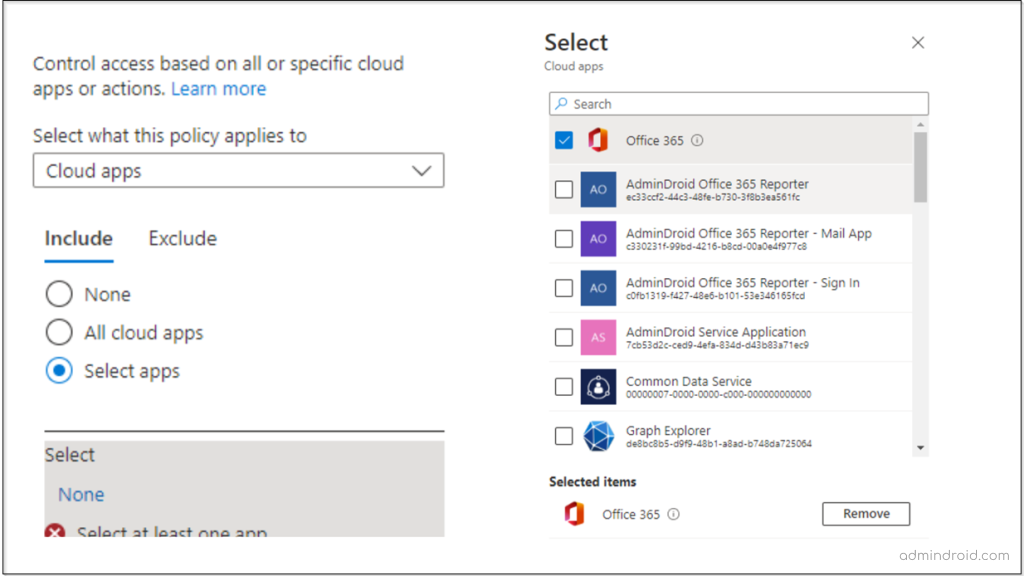
Upon enabling this Azure AD conditional access policy in Office 365, users will see the following error message.
Due to organizational policies, you can’t access this resource from this untrusted device.

Note: You can also limit unmanaged devices accessing apps by deploying the ‘Use application enforced restriction for O365 apps’ pre-built CA policy template for securing applications in Microsoft 365.
Setting Up Access Limit to SharePoint Files:
Creating conditional access policies to block access to all Office 365 apps and services is not a best practice. Users might need permission to access some apps anywhere for instant communication in certain cases.
Among the other Office 365 apps, SharePoint and OneDrive store the confidential files of your Office 365 environment. So, it is important to limit access to SharePoint and OneDrive content from unmanaged devices.
For instance, assume that your organization wishes to give all Office 365 users access to all services except SharePoint.
To perform this action, open the SharePoint admin center and follow the instructions below:
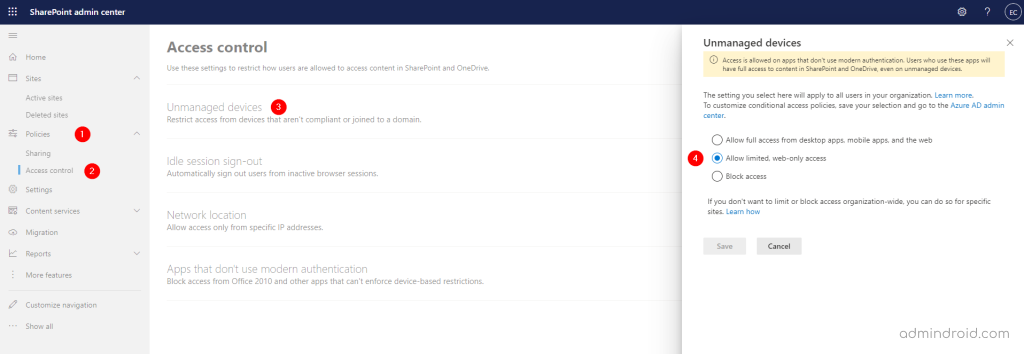
Keeping user access limited reduces the risk of accidental data loss in unmanaged devices. With the above setup, users on unmanaged devices have browser-only access (only previewing files) and cannot download, print, or sync files.
Users will begin to notice the below type of error when you limit access to SharePoint contents.
Your organization doesn’t allow you to download, print, or sync using this device. To use other actions, use a device that’s joined to a domain or marked compliant by Intune. For help, contact your IT department.
Never Slip Away with Unmanaged Devices:
Security threats are the major concern with unmanaged devices in Office 365.
For instance: Imagine a user requires instant communication, but if you prevent unmanaged devices from accessing the network, how will they communicate? There occurs the communication lapse! Therefore, blocking access to unmanaged devices as a whole won’t work in all cases.
We can’t avoid using unmanaged devices, but we can manage and monitor those devices and have secure Office 365 access.
How to Monitor Unmanaged Devices?
Office 365 provides only subtle information about unmanaged devices. To access the unmanaged device reports in Office 365, follow the below steps:
- Open the Microsoft Endpoint Manager admin center.
- Navigate to Users –> Sign-in logs (under Activity section)
- In the Sign-in logs section, you can filter the reports to check the failed status.
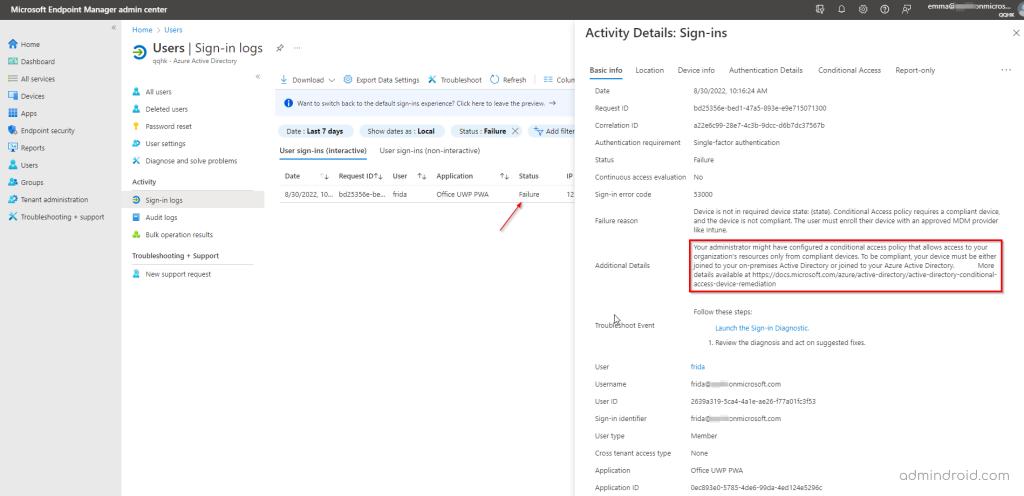
Isn’t that a lot of hassle? Yes, it is! As there is no direct access to the reports, we have to search and goof around with every failed unmanaged device login case.
It’s not yet possible to monitor unmanaged devices in Azure AD in depth. Therefore, the IT department stumbles on risky behaviors by unmanaged devices, which expose the network to malicious threats.
Manage the Unmanaged Devices with AdminDroid:
Office 365 admin center reports are presented in a collection of huge lists without any classification. Consequently, categorizing and interpreting those data for unmanaged devices takes quite some time. So, is there a way to directly access reports about unmanaged Azure devices?
Yes, we have got a tool! Look no further than AdminDroid, an Office 365 reporting, and auditing tool. AdminDroid, a robust Office 365 Reporting tool, bridges the information gap between Azure AD reports and manages your Office 365 reporting efficiently.
AdminDroid’s Sign-in analytical reports allow you to break the limitations in Office 365 and identify suspicious Azure AD user sign-in risks or other unusual sign-in behaviors.
With one dashboard, AdminDroid offers clear-cut reporting on unmanaged devices in Azure AD. Apart from displaying detailed logs, AdminDroid also identifies the last login information, distinguishes between successful and unsuccessful logins, and more.
Aside from viewing Azure AD unmanaged device sign-in errors, admins can also set alerts for these unmanaged device sign-in reports using AdminDroid.
These reports will provide information on all aspects of unmanaged device sign-ins. Some of them are,
- Where are my users logging in?
- What are the locations that have encountered the most sign-in errors?
- What are the user accounts involved in sign-in errors?
- How often do these errors happen?
- What’s the reason behind the unmanaged device sign-in errors?
- What are the risks encountered during the device sign-in process?
With the AdminDroid unmanaged device sign-in analytic dashboard, you get detailed information on all queries on the comprehensive Azure AD analytics dashboard. It provides a comprehensive view of all user actions signed in from devices other than those under your Office 365 organization asset.
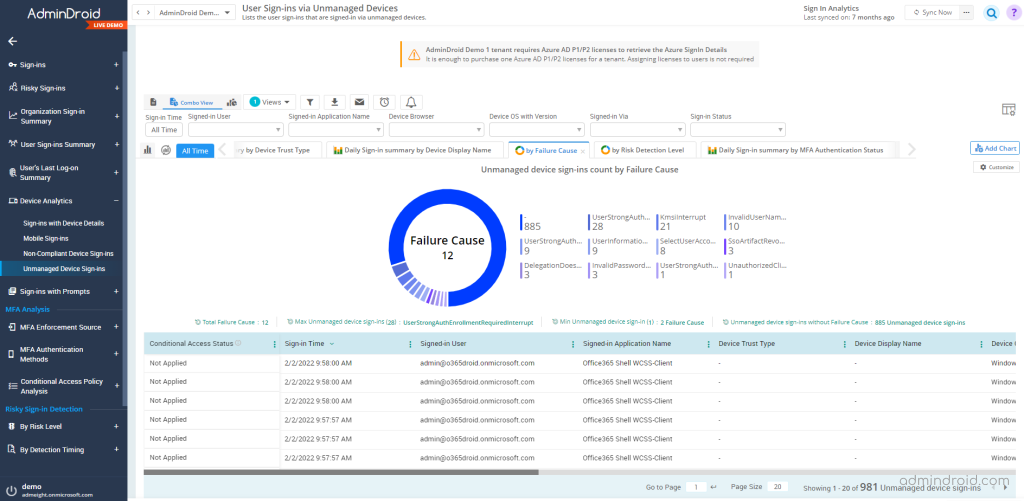
Looks like all the reports are rolled into one, doesn’t it? It is! It is essential to monitor risky log-in attempts made by unmanaged devices and remain compliant. AdminDroid sign-in analytical reports enable you to pull out comprehensive reports on mobile sign-ins, non-compliant device sign-ins, and unmanaged device sign-ins in just a few clicks.
Take a look at the features of AdminDroid with a free trial now!






