Statistics say that around 613 million passwords have been breached in the last few years. Definitely, that’s an alarming count, isn’t it? 🫤
Therefore, Microsoft announced that multi-factor authentication can prevent 90% of password attacks from happening in the organization. Besides, adding MFA to an organization’s security framework enhances corporate security and significantly reduces risks. Thus, organizations began implementing multi-factor authentication on user accounts to pose more security. But eventually, threats against MFA techniques from attackers resulted in multiple vulnerable attacks.
Why does MFA Falls Short?
MFA fails to protect us for multiple reasons which include erroneous handling of authentication codes, intercepting authentication methods, replicating biometrics, etc. Consequently, this led to the rise of several MFA attacks. Some of the MFA attacks are,
- Man-in-the-middle (MitM attacks)
- MFA Spamming
- SIM- Swapping attacks
- Pass-the-cookie attacks
One such attack that proves that not all multi-factor authentication methods are safe is the MFA Fatigue attack. It is one of the suspicious attacks carried out by tricking human factors. In this blog, let’s take a closer look at how to prevent MFA attacks in your organization.
MFA Fatigue Attack
MFA Fatigue is a technique of constantly spamming the user with MFA push notifications for additional verification. By continuously spamming, attackers assume users will approve requests considering that they came from a reputable source.
Therefore, attackers trickily gain access to the user account or the organization’s systems. This attack relies heavily on social engineering, so it is essential to take a look at it.
Managing multiple systems is relatively easy, but being vigilant for your Office 365 users is almost impossible. So, hackers take advantage of this downside to threaten Office 365 user accounts. Therefore, admins should take serious concern about MFA Fatigue attacks.
Several Ways to Avoid MFA Push Notification Methods
Choosing the right MFA authentication method is the most important step otherwise, you could put yourself at risk. Therefore, always insist on Microsoft Authenticator over SMS or phone calls. Also, you can use the “Authentication prompts analysis workbook” in Entra ID to investigate and analyse about the excessive MFA push notifications.
Although cyber attackers make the utmost effort to compromise user accounts, Microsoft has devised multiple MFA features like remember MFA on trusted devices, MFA number matching, and more to safeguard them. Yet, most Office 365 admins don’t know about this hidden feature behind the Azure portal.
Though this feature came into Public Preview in November 2021, most organizations have not implemented it! And, this strong security feature went General Availability in October 2022. So, now, it’s time to hang upon the weaker authentication methods like phone calls and SMS. Let’s dig deeper into the least popular MFA authentication methods that are truly a savior for your organization.
Prevent MFA Attacks with Number Matching and MFA Additional Context
MFA push notifications are the sole reason behind MFA fatigue attacks. Thus, to have a secure MFA push notification system, there are different methods available. They are:
- Show application name in the push and passwordless notification – Shows which application the user is attempting to sign in.
- Show geographic location in the push and passwordless notification – Displays from where the request is attempted.
- Number matching with push notification.
These techniques help you to have secure MFA authentication and improve user sign-in security.
MFA Additional Context for MFA Push Notification:
What is additional context for Microsoft Authenticator?
An additional context means extra information will be displayed to users when prompted for an MFA authentication request. This additional information might include the geographic location from where the request originated or the sign-in application details to which the user is trying to sign in.
Navigate to the path given below to add additional contexts:
Microsoft Entra admin center → Protect & Secure → Authentication methods → Microsoft Authenticator → Configure tab.
Under the “Configure” tab, you can find two different cool features.
- Show application name in push and passwordless notifications.
- Show geographic location in push and passwordless notifications.
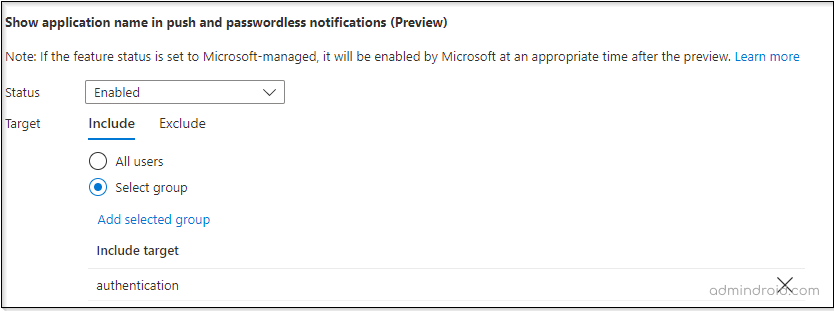
Show application name in push and passwordless notification:
After enabling this feature, the application name appears in the MFA push notification for which the user tries to sign in.
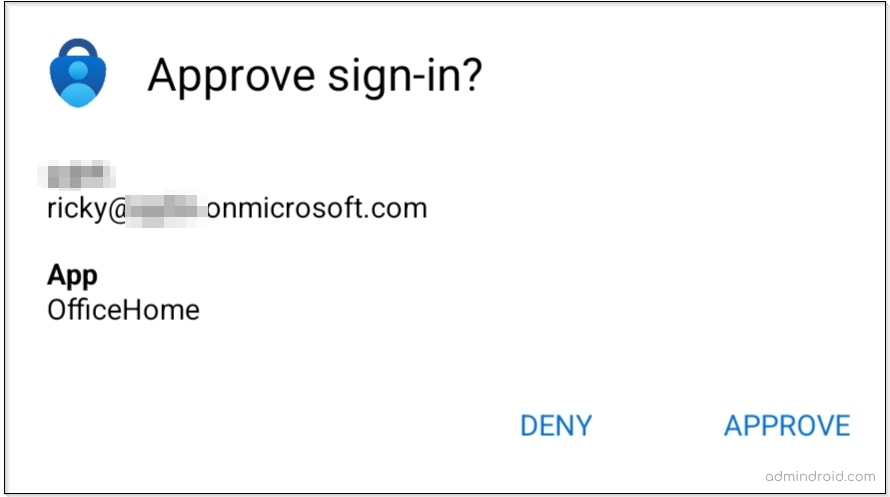
Therefore, Office 365 users who have enabled MFA push notifications will receive notifications with the application name when trying to log in to any Office 365 application.
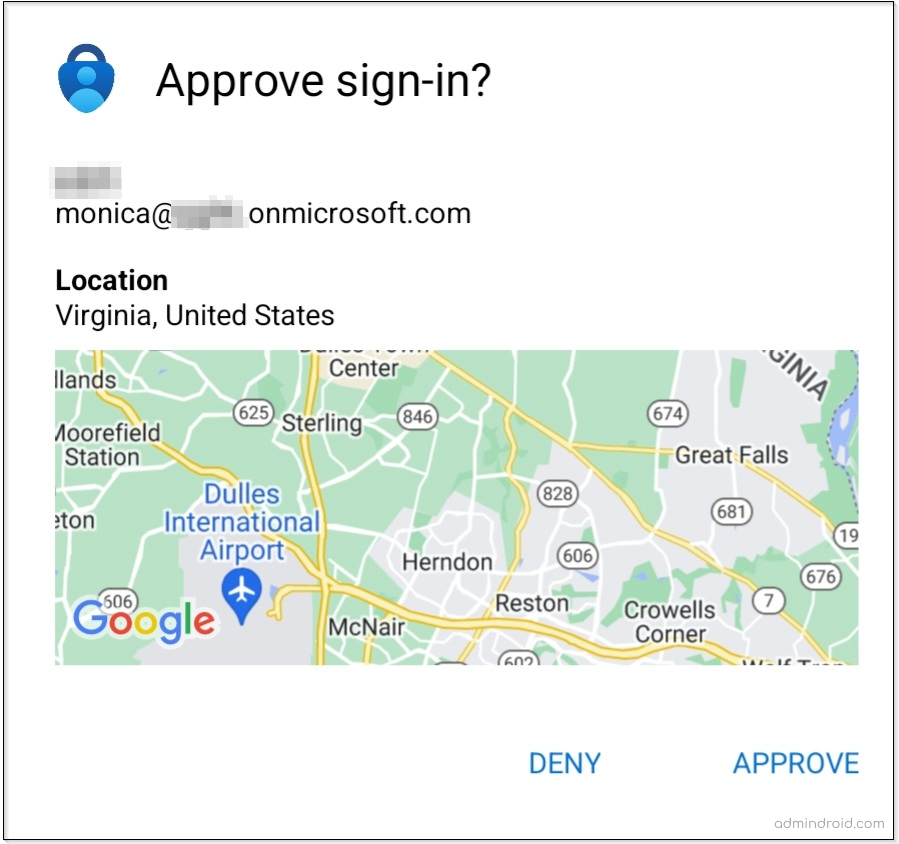
Enable Geographical Location for Multi-factor Authentication:
By mid-November 2021, Microsoft released this super handy feature called the MFA location that displays the user sign-in location in the MFA push notifications. No more worries about suspicious logins!
Number Matching in MFA
Previously, MFA push notifications would be sent to the users from which they can approve or deny the authentication request. Consequently, MFA Fatigue attacks rose due to these push notifications. Therefore, the best and only way to combat all of these MFA attacks is to enable number matching in multi-factor authentication.
Microsoft has announced that by May 8, 2023, users with the default MFA method as Microsoft Authenticator will have number matching enabled by default. However, if the user has a different default authentication method, nothing will change. So, start rushing up your users to set their default method as Microsoft Authenticator.
What is number matching?
Using the number matching technique, the user can enter the exact two-digit number displayed on the login screen into the Microsoft Authenticator app to confirm their identity.
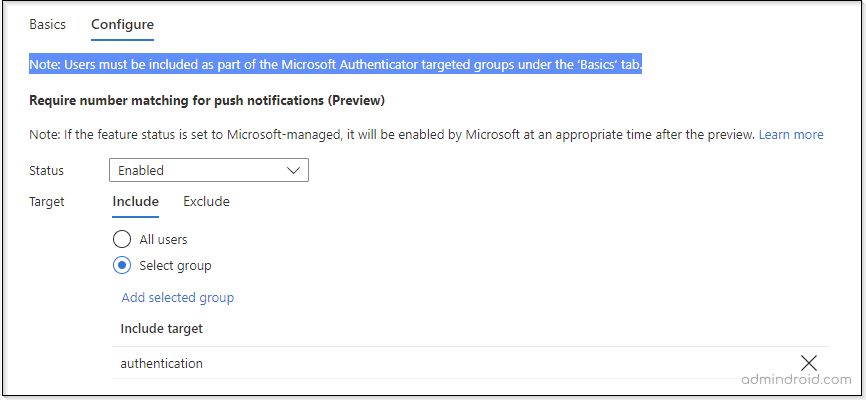
Steps to Enable MFA Number Matching:
- Log in to the Azure portal.
- Navigate to Azure Active Directory –> Security –> Authentication methods –> Microsoft Authenticator –> Configure tab.
- Now, under the Require number matching, turn the Status to Enabled.
Note: By default, the status will be Microsoft Managed. Setting Microsoft Managed enables Azure AD to decide when a feature is to be enabled by default.
- Next, you can select the target for Microsoft MFA number matching.
- Set for all users.
- Set only to a particular group.
- Exclude some users using the Exclude tab.
Tip: If you want to set it only for particular users, you can add them to a group and enable MFA number matching only for the specific users.
Working of Azure MFA Number Matching:
When Azure MFA number matching for push notifications is enabled, your users will get a two-digit number on their login screen.
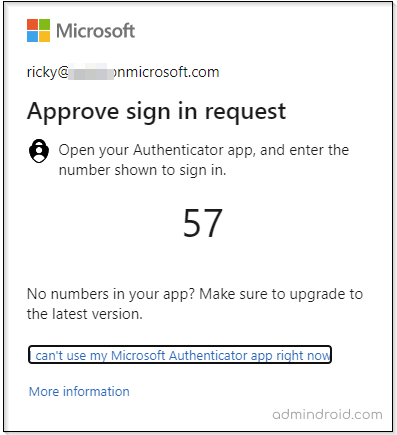
Here, users have to enter the number, which is displayed on the login screen, in the Microsoft Authenticator app. Thus, there is no possibility for the attacker to find the two-digit number displayed on the user’s login screen. Thereby, eliminating the risk of MFA spam attacks and more.
Prerequisites to Use MFA Additional Contexts and Number Matching:
- You should be either a global administrator or authentication policy administrator to enable number matching and additional contexts in MFA.
- MFA with push notifications should be enabled for Office 365 users in the Azure portal.
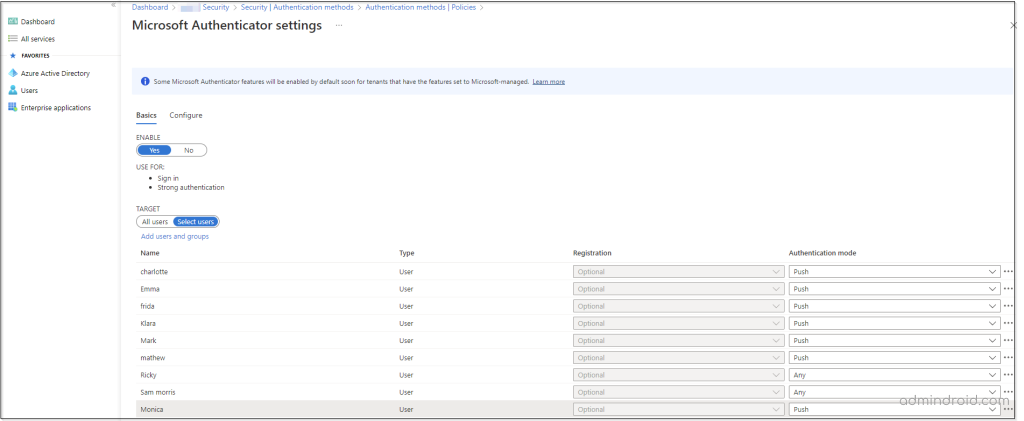
- To add MFA additional contexts for all users, your Office 365 users must be a part of the Microsoft Authenticator Settings.
Next, navigate to the path given below to add users to Microsoft authenticator settings:
Azure portal → Azure Active Directory –> Security –> Authentication methods –> Microsoft Authenticator –> Basic tab.
Note: Please note that only users available under the Basic tab can benefit from the MFA additional context and number matching features.
Why Admins Should Choose These Methods?
Hereafter, you won’t have to worry about users who are mindlessly approving any MFA request on their phone without recognizing that it didn’t come from their own device. Subsequently, the additional contexts and MFA number matching reduces the likelihood of accidental approvals in Microsoft authenticator. Thereby, you can get rid of the MFA fatigue attacks and more MFA attacks.
In conclusion, adding MFA to your Office 365 accounts creates a robust layer of protection, so implement the best security practices and secure your accounts from today. And, concurrently, make sure you don’t fall victim to MFA fatigue. Enhance your safety and always opt for a defense-in-depth strategy.
Summing up now! Share your thoughts about this feature, and for more inquiries and discussions, reach us out in the comment section. We would be glad to assist you!