Over the past few years, Microsoft has warned admins about the basic authentication deprecation in Exchange Online. Since it is one of the oldest authentication methods, it comes with numerous security flaws. Hackers will easily attack accounts that use basic auth as it requires only a username and a password to log in. Therefore, Microsoft brought in the idea to deprecate basic authentication.
Due to the pandemic, Microsoft started to postpone the deprecation. But it’s not over yet! Despite Microsoft continuously warning about the deprecation, many organizations are not ready to make the switch to Modern authentication. To those, the deadline is here!
Microsoft will begin to disable basic authentication for Exchange Online on October 1, 2022.
Therefore, instructing organizations to never mention that they aren’t ready for this change!
What Are the Consequences of Basic Authentication Deprecation?
Microsoft stated that it would disable basic authentication in Exchange Online for the following:
- Exchange ActiveSync (EAS)
- POP
- IMAP
- Remote PowerShell
- Exchange Web Services (EWS)
- Offline Address Book (OAB)
- Outlook for Windows and Mac
Is SMTP protocol also being deprecated by Microsoft?
As many multifunction devices like printers and scanners can’t use modern authentication, the SMTP protocol is not deprecated if you are using this consistently in the organization. However, if you stop using it for a while, your SMTP protocol will be disabled. The SMTP will be disabled for tenants who never used the protocol previously.
Timeline of Microsoft Exchange Basic Auth Deprecation:
The below image describes the announcements made by Microsoft regarding basic authentication deprecation.

Can You Postpone the Basic Authentication Deprecation?
Basic authentication will be disabled by default for Microsoft 365 tenants created after October 22, 2019. This is due to security defaults being enabled by default.
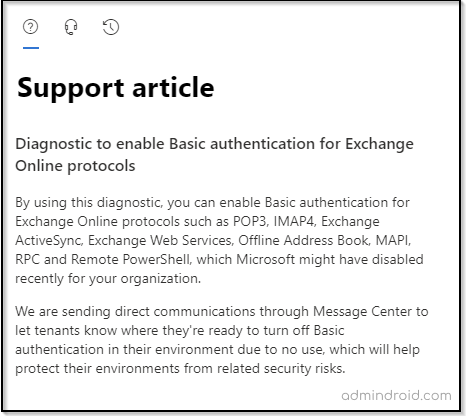
Microsoft will randomly select tenants and disable basic auth for all the protocols, excluding the SMTP protocol. While planning to deprecate basic auth for your organization, Microsoft sends a notification to the message center of your organization. But if you want to get one last chance to pause and re-enable basic authentication for Office 365, you can send a request through the message center dialog box.
Step 1: Open the Help & Support.
Step 2: Send a request as Enable basic auth in EXO in the text box to enable basic authentication.
Then, Microsoft will enable basic authentication for Exchange Online protocols like POP3, IMAP4, Exchange ActiveSync, Exchange Web Services, Offline Address Book, MAPI, RPC, and Remote PowerShell.
Note to Remember: However, all the re-enabled Exchange protocols will be permanently disabled on January 1, 2023, with the exception of Office 365 Operated by 21Vianet. Microsoft will begin to disable basic authentication for Office 365 Operated by 21Vianet from March 31, 2023.
Time to Switch to Modern Authentication
What do you need to do before Microsoft disables basic authentication in your tenant? All you need to do is to switch from Basic authentication to Modern authentication!
The use of modern authentication makes it easier to manage user identities in both on-premises and in hybrid Exchange environments.
Modern authentication strengthens the authentication step and deploys protocols like OAuth 2.0, SAML, etc., for authorization, intending to boost the traditional authentication technique and simplify the admin barriers.
Now further on this blog, let’s see how to deal with this basic authentication deprecation.
Step 1: Identify basic authentication usage using the Azure Sign-in report.
Step 2: Upgrade your scripts and apps which are still using basic auth.
Step 1: Identify Basic Authentication Usage Using the Azure Sign-in Report:
It is necessary to find users who use basic authentication in your organization, so use the Exchange Online Basic authentication report. Let’s look at the two different methods available to identify users using Basic authentication.
Export Office 365 Basic Authentication Report Using MS Azure:
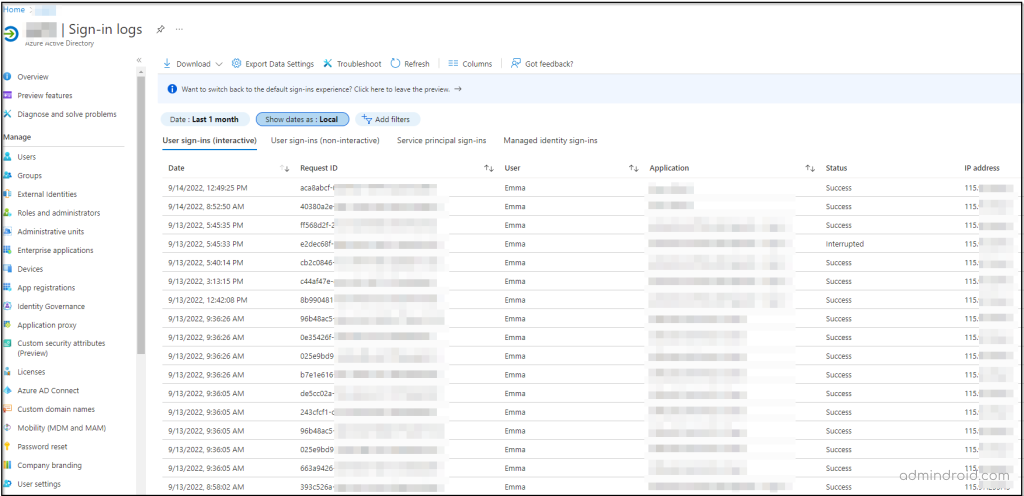
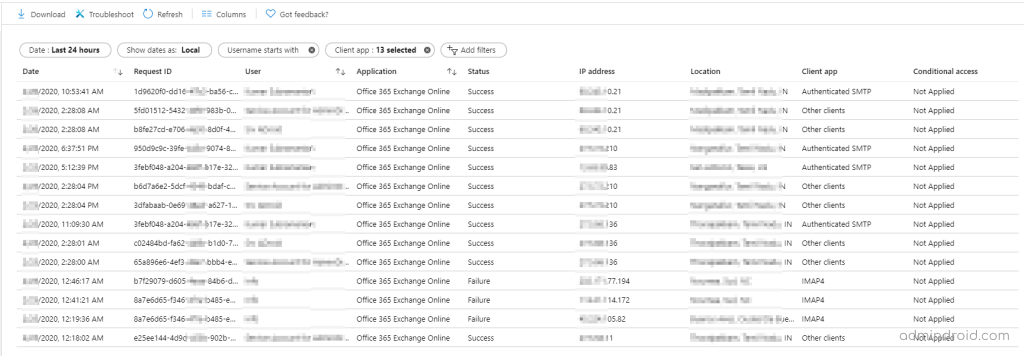
1. Open the Azure Sign-in report in Microsoft Azure. This page displays the overall user sign-in details along with Application, IP Address, Location, CA policy status, etc.,
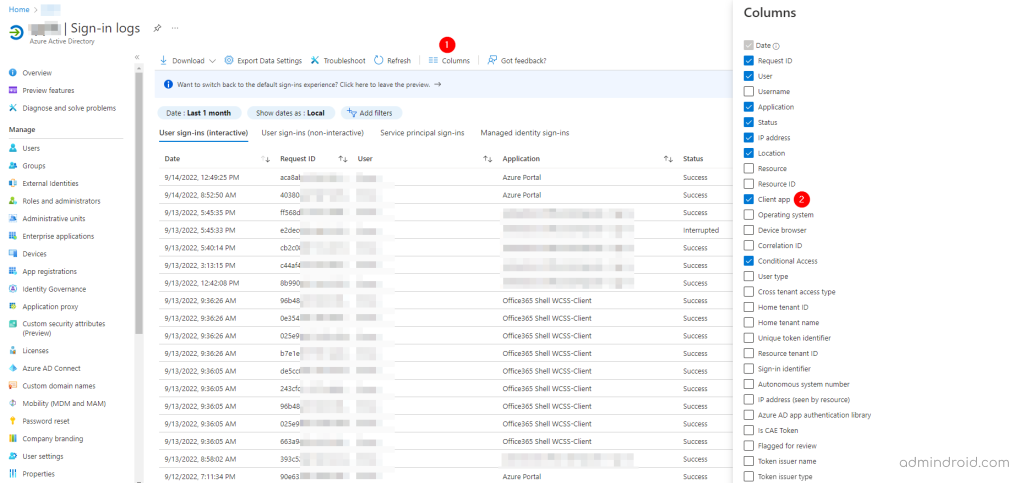
2. Next, add the “Client App” column to the current sign-in report, since it’s not displayed by default. This identifies the protocols used by your users in your organization.
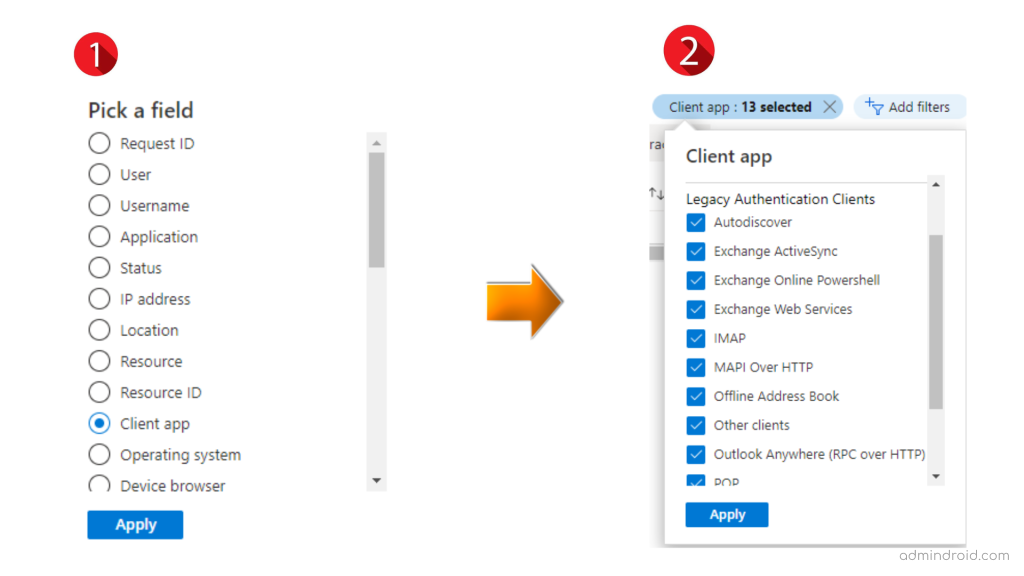
3. Then, click on the Add filters and select the Client App. To further get the Office 365 basic authentication report, select the Client app filter and check in all the available legacy authentications like Exchange Active sync, Exchange Online PowerShell, IMAP4, POP3, etc.
Note: While selecting the clients, choose all the “Legacy Authentication Clients” except Browser and Mobile Apps & Desktop Clients.
4. In sum, this will display the users who use basic authentication in your organization, additionally you can export the basic authentication report as CSV or JSON file for further verifications.
Get Instant Alerts and Schedule the Basic Authentication Reports:
Rather than searching and tweaking basic authentication reports in Azure AD, you can get detailed reports on every protocol in a single dashboard with AdminDroid. Further, it gives you detailed insights into all the Office 365 user sign-ins and basic authentication reports at a fast pace.
You can get Office 365 basic auth reports by filtering the available basic auth protocols, and further set alerts and schedule these reports for getting notified instantly.

Step 2: How to Upgrade Scripts/Applications that Already Use Basic Auth Protocols?
Let’s examine how disabling basic authentication will affect the following protocols in Office 365 and what you need to do.
- POP, IMAP, and SMTP Auth
- Exchange Online PowerShell
- Exchange ActiveSync (EAS)
- Exchange Web Services (EWS)
- Outlook
For POP, IMAP, and SMTP Auth
- In order to provide secure modern authentication for their users, application developers should upgrade apps that previously used these protocols to send, receive, and process emails.
- If the in-house application needs to access protocols like IMAP, POP, and SMTP Auth in Exchange Online, you can advise them to implement OAuth 2.0 Authentication for the protocols.
- OAuth 2.0 support for POP, IMAP, and SMTP Auth protocols have been released, so users can switch to OAuth.
Note: Outlook can connect using MAPI/HTTP (Windows Clients) and EWS (Outlook for Mac).
For Exchange Online PowerShell
Due to the Microsoft Exchange basic auth deprecation, Microsoft introduced the EXO V2 module to connect to Exchange Online PowerShell with modern authentication. While EXO V2 uses modern authentication, WinRM basic authentication is necessary to transport modern authentication tokens.
So, to overcome this issue, you can use the EXO V2 Module Preview, which lets admins connect to Exchange Online without enabling WinRM basic authentication. Follow the steps below to install EXO V2 Preview Module and disable WinRM basic authentication.
Install EXO V2 Preview Module:
To install the EXO V2 Preview module, run the following cmdlet,
|
1 |
Install-Module -Name ExchangeOnlineManagement -RequiredVersion 2.0.6-Preview3 –AllowPrerelease |
Disable WinRM Basic Authentication:
To check whether the basic authentication is enabled, run the command below in the command prompt.
|
1 |
winrm get winrm/config/client/auth |
If you find Basic= true set, you need to run the following command to disable WinRM basic auth.
|
1 |
winrm set winrm/config/client/auth @{Basic="false"} |
For Exchange ActiveSync (EAS)
So, users can switch to
- Use Outlook for iOS and Android or
- Start using other mobile device email apps that support modern authentication.
For Exchange Web Services (EWS)
In a recent announcement, Microsoft announced that they would no longer push updates for Exchange Web Services and instructed users to switch to MS Graph instead.
You can do any of the methods below to have continuous access to mailbox and calendar data using Exchange Web Services.
- Shift to Microsoft Graph or
- Switch to Modern authentication with EWS.
For Outlook
Here are the Outlook versions that support and do not support Modern authentication. If your Outlook version does not support Modern authentication, you can upgrade to the newer version to have improved security.
| Outlook Versions | Support Modern Authentication |
| Outlook 2007 | No |
| Outlook 2010 | No |
| Outlook 2013 | Yes (Requires setting to enable Modern authentication) |
| Versions above Outlook 2016 | Yes (By default) |
| Outlook for Mac | Yes |
This pretty much wraps up the update! I hope it helped you to understand Microsoft Exchange deprecation and the steps to be taken.
With the rise in email phishing attempts and multiple email attacks, it is essential to have an efficient Exchange Online mailbox management system to have a secure workspace. Therefore, get rid of basic authentication methods, and start implementing strong authentication methods in your organizations.
Stronger the Authentication! Safer the Organization!!






