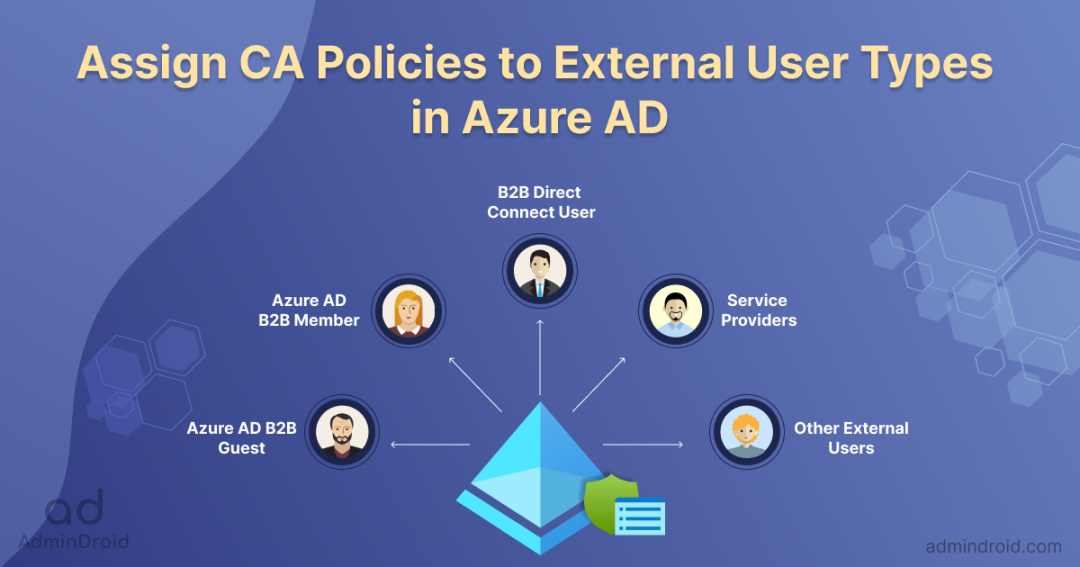
Previously, conditional access policies created in Azure AD were limited to external users as a whole. But that is not the case now. With the new preview feature, you can specify external user types instead of settling with the ‘All guest or external users‘ option. This amazing preview feature lets you apply conditional access policies to external user types in Azure AD, added through various collaboration methods. For a CA policy, the ‘Users or workload identities’ section under the ‘Assignments’ blade encompasses this new preview feature.
Specify External User Types in Conditional Access
The ‘All’ is expanded to ‘Select’ now! Here’s a comparison that shows the Azure AD conditional access page before and after the preview feature.
BEFORE:
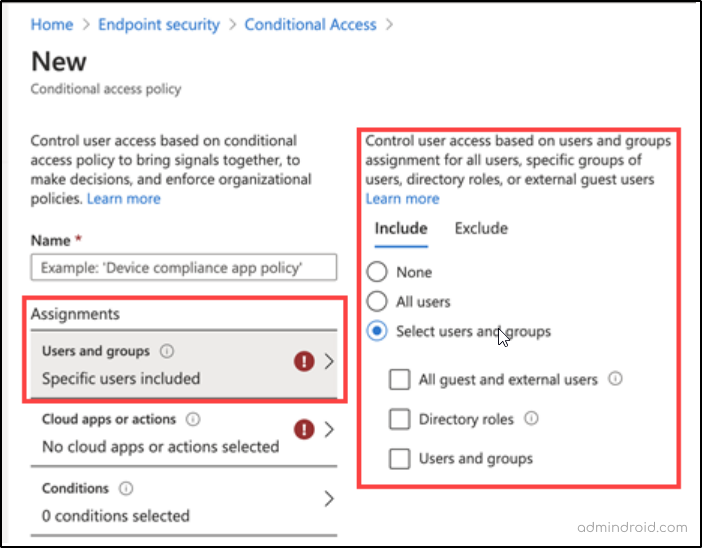
NOW:
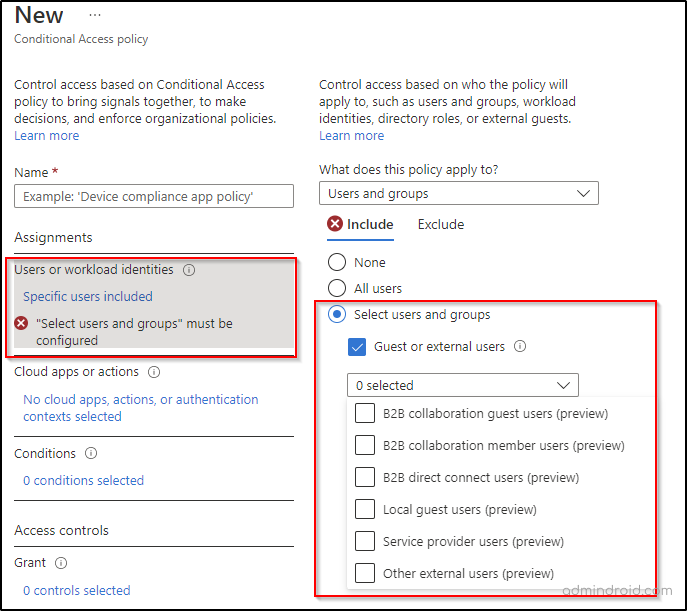
Thus, organizations can enforce multiple Conditional Access policies by either including or excluding specific external user types.
What are the Newly Added External User Types?
When you create a conditional access policy in Azure AD, you can apply it to the following types of external users.
- B2B collaboration guest users
- B2B collaboration member users
- B2B direct connect users
- Local guest users
- Service provider users
- Other external users
Let’s have a brief look at them.
B2B Collaboration Guest Users
- Has an external Azure AD account in your organization.
- Has guest-level permissions with UserType as ‘Guests’
- These are guest users who are added to the Azure AD directory using invitations or self-service sign up.
B2B Collaboration Member Users
To convert UserType from Guest to Member, Select the user from the list > Edit User Properties > Select ‘Member’ from the UserType dropdown.
- Has an external Azure AD account in your organization.
- Has member-level permissions with UserType as ‘Member’
- These users mostly belong to organizations that manage multiple tenants.
B2B Direct Connect Users
- Users who connect via B2B direct.
- Supported only for Microsoft Teams Connect Shared Channels as of now.
- Not present in the Azure AD directory.
Local Guest Users
So, who might be these local guest users? These users are designated with UserType ‘Guests’ at the time of creation by setting up internal credentials.
Service Provider Users
These users are those who serve as cloud service providers for your organization.
Other External Users
These are users that don’t fall into the above-mentioned categories. They don’t authenticate internally via Azure AD and don’t hold UserType of Member.
Control Access for External Azure AD Organizations
The new preview feature for external Azure AD organizations further allows the user to either choose all or specific external Azure AD organizations for the selected external user types.
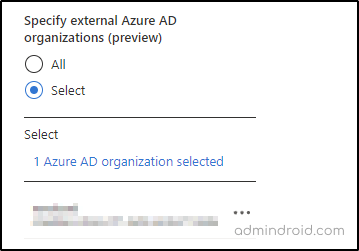
For applying the policy to a specific external Azure AD organization, you have to add them by entering their Tenant ID or domain name.
User Experience
To make the point clear, we will try out the preview feature with an example.
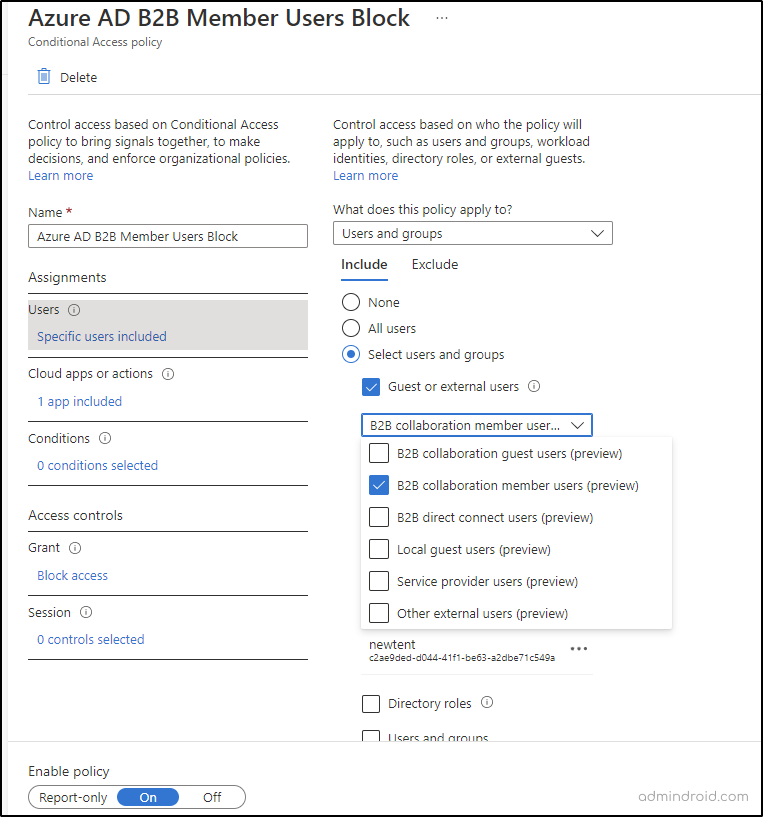
- First, let’s create a conditional access policy. I have named it ‘Azure AD B2B Member Users Block’ as my concern is to block access by B2B collaboration member users.
- Under the Assignments section, select only ‘B2B collaboration member users’
- For instance, I have included only Office apps for ‘Cloud apps or actions’ and the ‘Access controls’ is set to Block access.
- I have a user (Alex) from another tenant who is an external user with UserType ‘Member’.
- According to the policy I created, Alex’s access must be blocked and external users of any other type must be able to access the resource.
Now, I try sending an invitation for an Excel file from the home tenant to Alex. When he tries to access the resource, the following error appears.
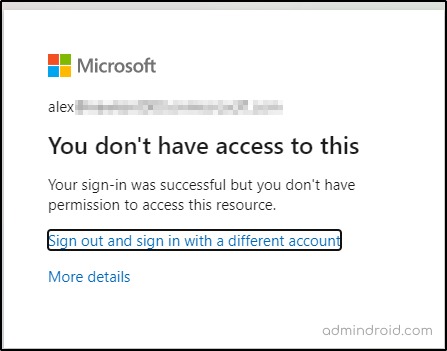
But, when the same invitation is sent to another user say, a B2B collaboration guest, they are prompted to access the resource immediately.
This is how you can utilize the new preview feature within the Azure AD conditional access policy.
I hope this blog will guide you through the concepts of applying conditional access control to external user types. Feel free to reach us in the comments for any assistance.