Recently, Microsoft has been working on and rolling out many new features like adaptive MFAs, releasing a separate space for MFA registration and reset event reports, and a lot on the list. Now, they’re back to shed light on the existing Azure AD settings. Unlike others, the recently introduced Azure AD user tenant creation setting is both interesting as well as confusing! 😕 Apparently, this new Azure AD user tenant management setting has been generating a lot of buzz on social media since its release.
And the image below is just a sneak peek into what I’ve been witnessing recently.
Still, there is a lot! But what is this new configuration setting, and why so much dilemma over one such toggle button? What a mess, isn’t it? So, in this blog, let’s explore this new Azure AD setting in detail.
New Toggle for User Tenant Creation in Azure AD
Microsoft has allowed users(non-admins) to create new tenants, and the setting has been set to the default value of ‘True.’ Therefore, every Office 365 user can create an Azure AD tenant using the Azure portal.
Now, here is where MS introduced a new toggle to manage user tenant creation. Follow the below path to find the newly introduced ‘Tenant creation’ toggle button.
Microsoft Azure portal → Users (in the left pane) → User settings (under the ‘Manage’ tab) → Tenant creation.
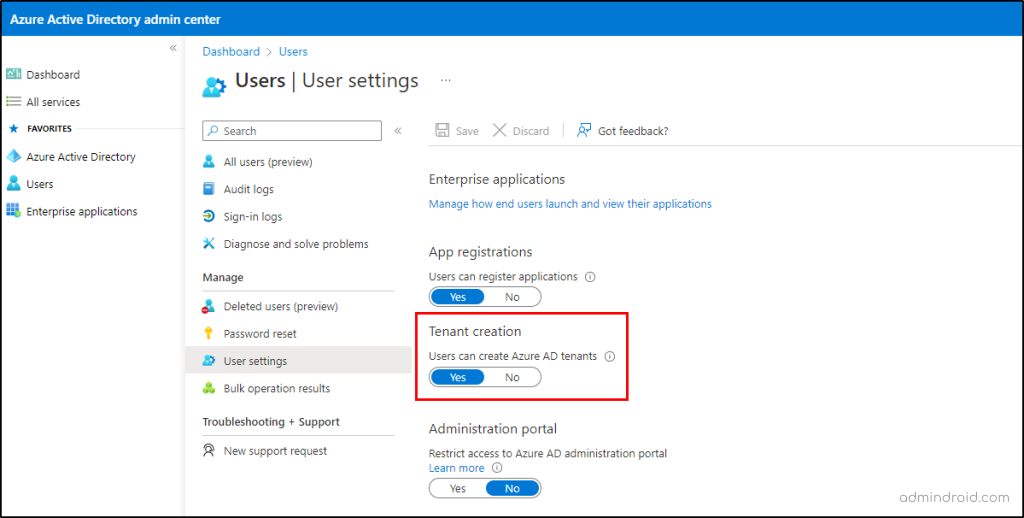
‘Yes’ – means that all users can create Azure AD tenants.
‘No’ – Only global administrators and tenant creator roles can create Azure AD tenants.
What is the Purpose of Creating New Tenants From Azure AD?
As one of the reasons for creating tenants within organizations is for testing purposes, we’ve got an alternative.
Rather than creating a new Azure AD tenant inside the work environment, you can educate your users to use the “Free Office 365 developer program” for testing purposes. This Microsoft 365 developer program comes with 25 E5 licensed users with pre-populated data, covering every requirement for testing purposes.
Therefore, it is better to try out the ‘developer program tenant’ rather than creating it within the organization.
Behind the Lens – User Tenant Creation:
If you’ve known about user tenant creation for so long, there is not much excitement. But if you’re new and unsure how to create a new tenant, follow the steps below.
Microsoft Azure portal → Azure Active Directory (in the left pane) → Manage tenants (in the Overview page) → + Create
Finally, following the path and completing the procedures will create a fresh Azure AD tenant. Then, what does this tenant have?
✅ A newly created Azure AD tenant will have the created user as a global admin but as an external user.
✅ It’ll be completely an empty tenant without any subscriptions.
✅ The newly created tenant does not inherit any settings and configurations from the existing tenant.
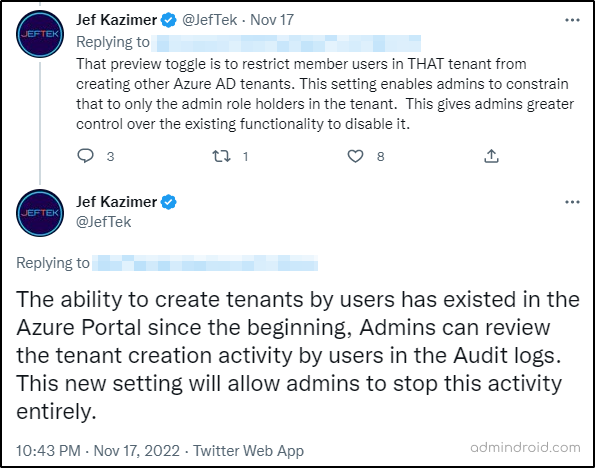
You might then wonder why the ‘Tenant Creation’ toggle bar has been added to Azure AD. So, here is the reason, previously, administrators had no power over user tenant creation, so now this configuration makes it easier for admins to have better control over it.
Here is a snippet of Microsoft’s Product Manager’s tweet on the following case:
Get Reports on User Tenant Creation in Azure AD:
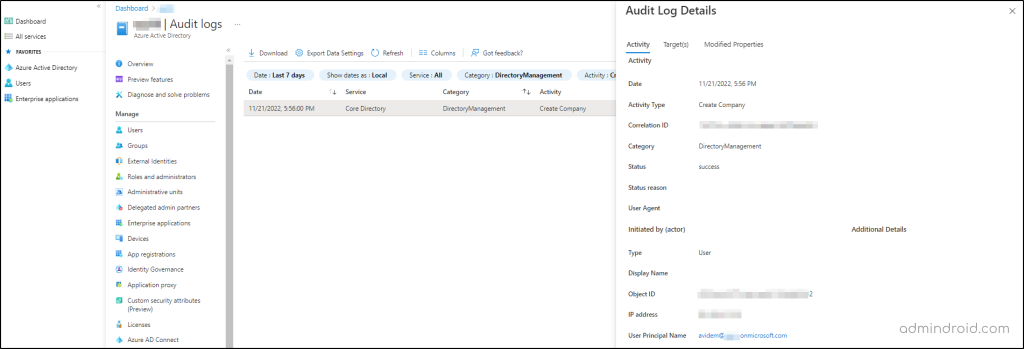
Don’t panic, if you can’t find whether any user has already created a tenant. Azure audit logs maintain a record of newly created tenants within your organization. Follow the below path and filter the columns as suggested.
Microsoft Azure → Azure Active Directory → Audit logs (under the ‘Monitoring’ tab)
Now, set the ‘Category’ as ‘DirectoryManagement’ and ‘Activity’ as ‘Created Company’
Here you can see the records of the tenants created, along with the date, tenant ID, and details of the user that created them.
Disable User Tenant Creation in Azure AD
🤔Quick que: Is it okay when organizations allow their users to create Azure tenants?
In my opinion, letting users create a new Azure AD tenant from your Office 365 environment is not recommended! 🚩
Creating Azure AD tenants does not impose a substantial impact on the organization, and also the risks associated with Azure AD tenants are so negligible. But, it’s always better to toggle the bar ‘Off’ and disable user tenant creation. Disabling this will prevent new threats from arising! Because we know, “An ounce of prevention is worth a pound of cure”.
Besides GUI, we have PowerShell backup as well! Use the following script to disable the user tenant creation in Azure AD. Before running the script, install the Microsoft Graph PowerShell module and proceed.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
Import-Module Microsoft.Graph.Identity.SignIns Connect-MgGraph -Scopes 'Policy.ReadWrite.Authorization' Select-MgProfile -Name beta $params = @{ DefaultUserRolePermissions = @{ AllowedToCreateTenants = $false } } Update-MgPolicyAuthorizationPolicy -AuthorizationPolicyId <AuthorizationPolicyID> -BodyParameter $params |
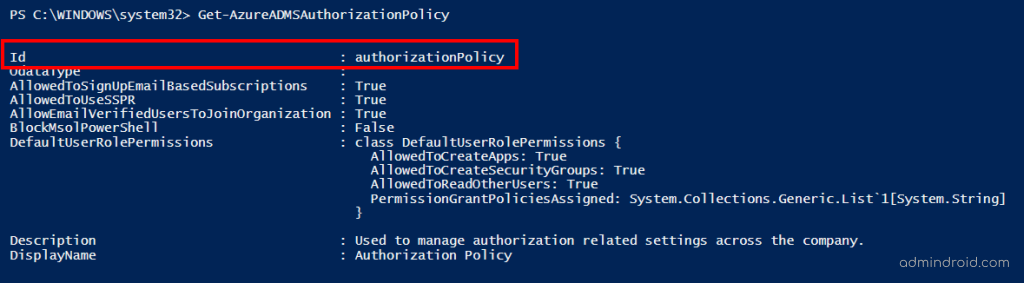
Use the cmdlet Get-AzureADMSAuthorizationPolicy to get the default authorization policy ID of your organization.
Firstly, why does this happen?
Why is so much chaos hovering around and disabling user tenant creation? First and foremost, no tenant should allow their users to access the Azure AD portal. Normally, non-admins can access the Azure portal without some restrictions.
Though they can’t modify/update any settings, they can view the user info, group info, device details, user privileges, etc., leaving this open to all Office 365 users can only result in multiple attacks. ❌ Hackers can gain all details through any unprivileged user in the organization without much effort.
Therefore, the best practice is to restrict user access to the Azure AD portal. ✅So, without further ado, admins should take the next step as suggested in the below blog and put the mission on protecting your Office 365 environment.
Restrict User Access to Azure AD to Prevent Data Exposure | AdminDroid Blog
That’s it! If you have any further loopholes and can’t find a way to fix them, we’ve got you! Check out the Microsoft 365 security hardening techniques comprising a high range of 31 security measures picked selectively on multiple bases. As we cannot completely eliminate the risks posed by our Office 365, it is always possible and easy to create a firewall that stops all threatening behaviors against your Office 365 organization.