On Day 29 of Cybersecurity awareness month, learn the importance of Continuous Access Evaluation in Microsoft Entra. Stay tuned for more blogs in the Cybersecurity blog series.
IT administrators continue to place high importance on the security of email and other tools needed to run their businesses. It is a usual event where admins need to disable a user from accessing their resources for one or the other reason. When such a user account is disabled, it is crucial to wait until they lose access to the resource. Instead, it has to take place straight away which is not possible with the traditional session controls setting in Entra ID Conditional Access policy. With CAE, it is possible to kill the access token lifetime and enforce immediate response to critical events.
“Time is what determines security. With enough time, nothing is unhackable”
– Aniekee Tochukwu Ezekiel
In accordance with the quote, when resources are shared carelessly, they are exploited over time. One hour’s access token refresh time is sufficient in this case.
In this blog, we’ll explore how to enable Continuous Access Evaluation in Microsoft Entra and walk through scenario-based explanations to illustrate its importance.
What is Continuous Access Evaluation?
Entra ID offers a variety of security features to ensure security in organizations. One such feature is Continuous Access Evaluation.
Continuous access evaluation is the mechanism of a two-way conversation between the token issuer (Azure AD) and the relying party (client app). Currently, CAE is available for Exchange, Teams, and SharePoint Online which are referred to as CAE-capable clients.
The need for CAE starts with the OAuth (Open Authorization) 2.0 access tokens that are used to authorize any API requests. When a user’s access is removed or a client IP address changes, CAE automatically blocks access to resources and applications in near real-time (up to 15 minutes may be expected).
Note: From Mid-September 2024, Microsoft 365 admin center will implement continuous access evaluation, enabling near real-time session termination and enforcing policy changes without waiting for token expiration.
What are Access Tokens?
Whenever an app/user requests access to Entra ID-supported applications, an access token with a lifetime of 1 hour is shared. The access token contains information on the user’s identity and permissions. Access token together with token refresh gives the user uninterrupted access that regenerates/ refreshes new tokens every 1 hour. This is where CAE comes into action. Let’s take a look at them in more detail.
Client-side Claim Challenge
Claim challenge is an authentication mechanism that informs clients to bypass the cache token even if they are not expired. Before CAE, clients would replay the access token from its cache as long as it hadn’t expired. With CAE, it indicates that the token was rejected and a new access token needs to be issued by Entra ID.
The latest version of the CAE-enabled clients – Outlook, Teams, Office and OneDrive (on Web, Win32, iOS, Android, and macOS) supports the claim challenge except for Office on the Web which is not supported.
How to Enable Continuous Access Evalution?
Continuous access evaluation is enabled by default for all new tenants, but if you’re migrating from previous settings or have custom configurations, here’s what you need to know:
For New Tenants:
- Automatic Enablement: New tenants who haven’t configured CAE settings before will find CAE automatically enabled. The old CAE settings interface is hidden, as these customers would not have interacted with it prior to general availability.
For Existing Customers:
- All Users Enabled: If you previously enabled continuous access evaluation for all users, you don’t need to take any action. The old CAE settings will be greyed out, and Continuous Access Evaluation will be automatically enabled in your Conditional Access policies.
- Some Users Enabled: If you configured CAE for specific users only, you will need to migrate your settings. The old CAE settings will be greyed out. Click Migrate to launch the new Conditional Access policy wizard, which will include all users but exclude the users and groups copied from the old CAE settings. The new Customize continuous access evaluation Session control will be set to Disabled.
- Preview Disabled: For tenants that disabled the preview feature previously, the old CAE settings will also be greyed out. Clicking Migrate will launch the Conditional Access policy wizard, which will include all users and set the new Customize continuous access evaluation Session control to Disabled.
License Requirement for Continuous Access Evaluation
Since continuous access evaluation is configured using Conditional Access, a Microsoft Entra ID Premium (P1 or P2) license is required for doing any customizations.
Why CAE is Important?
CAE not only increases security but also reduces the time of losing access to a resource when critical events occur. As mentioned above, access tokens with a 1-hour lifetime can be questionable for the following scenario.
- Entra ID takes one long hour to lock the user’s account blocked by the administrator using Conditional Access policies. The user may download the confidential data within this one hour of dismissal.
CAE saves this situation by building a two-way conversation between Entra ID and the application. That is, if the application detects any unusual activity, it signals Entra ID and vice versa. This in turn paves way for immediate actions on the user whenever any changes happen to their account. CAE is also useful in Microsoft Entra Private Access. By integrating with Conditional Access and leveraging Global Secure Access signaling, Entra Private Access supports crucial features like client IP restoration, which is vital for CA, CAE, Identity Protection, and Microsoft Entra ID sign-in logs.
Continuous access evaluation involves two types of scenarios: critical event evaluation and Conditional Access policy evaluation.
What are Some of the Critical Events in Microsoft Entra ID?
When any of the following critical events occur, CAE helps in real-time access token refresh that causes the users to be logged out.
- User account is deleted or disabled
- Password for a user is changed or reset
- Location changes for a user
- Multi-factor authentication is enabled for the user
- Administrator explicitly revokes all refresh tokens for a user
- High user risk detected by Entra ID Identity Protection
Scenario-Based Explanation for CA Policy Evaluation
The following step-by-step explanation provides a clear view of how CAE works.
- Create a new Conditional Access policy by navigating through Microsoft Entra admin center > Security > Conditional Access.
- Select specific users from the ‘Users’ to whom you want the policy applied to.
- Select ‘All cloud apps’ option from the ‘Cloud apps or actions’ blade.
- Add conditions to exclude only the selected location, so that users accessing from any other locations will be blocked.
- After granting the option to block access, turn on the policy right away.
User Experience with Continuous Access Evaluation
Now, when the user tries to access the resource from a different IP location, their access is blocked instantly and they receive the following error.
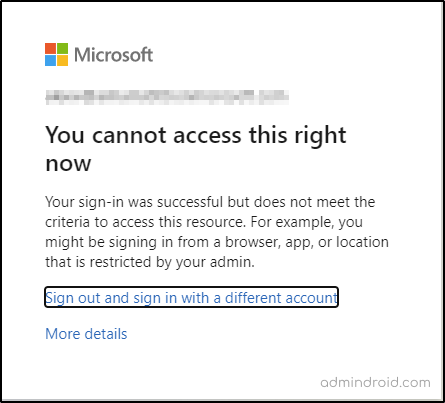
This proves that Continuous Access Evaluation is enabled for you.
Note: To better understand how CAE will function in different scenarios, What If tool in Azure AD, powered by Microsoft Graph, allows you to simulate Conditional Access policies. This gives you a clear view of how your policies will behave in real-world situations and their potential impact on security.
What Happens When Continuous Access Evaluation is Disabled?
As a premium Entra ID user, you can disable continuous access evaluation from the session blade for a Conditional Access policy.
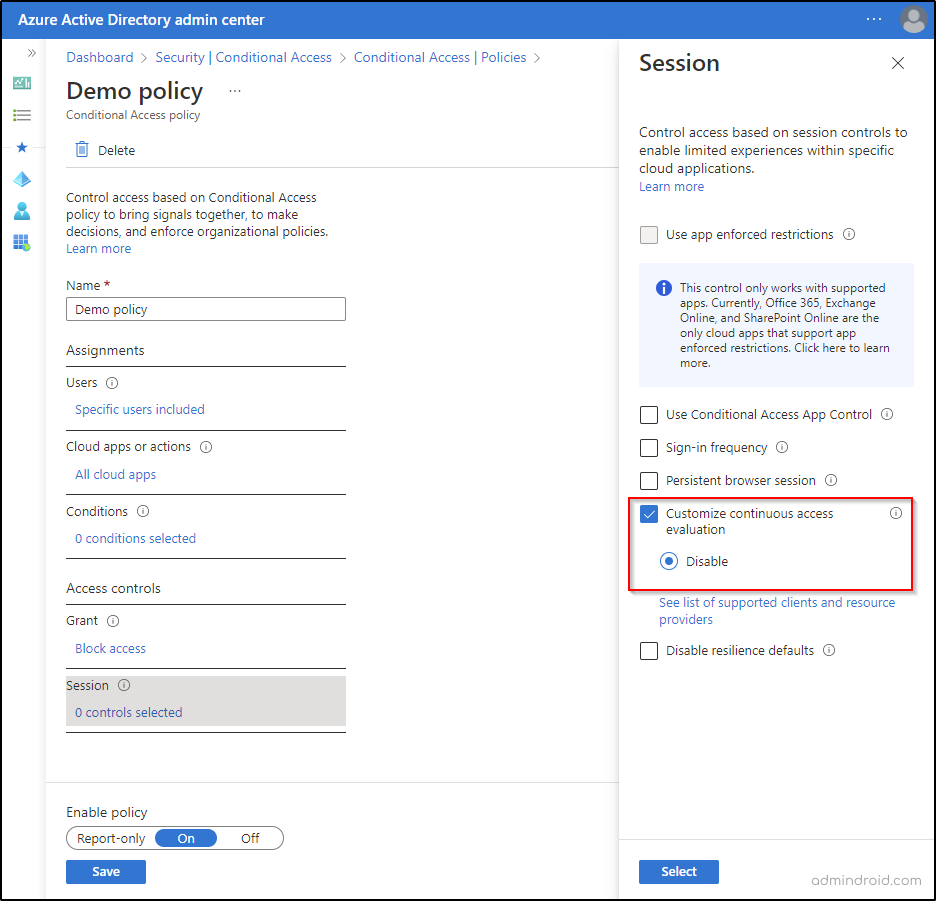
It is important to note that disabling continuous access evaluation works only when “All Cloud Apps” is selected and no condition has been chosen for a CA policy. When CAE is disabled, blocking access for an unusual event takes a long one-hour. This time is more than enough for a malicious user to steal all your confidential data.
Some Limitations of CAE to Make a Note of:
- CAE is not supported for all client apps and resource provider combinations.
- For location conditions, CAE supports only IP-based named locations insights. It does not support MFA-trusted IPs or country-based locations.
- Time taken to update changes made to group memberships and CA policies could take up to one day to be effective. This delay is from replication between the identity provider and the resource providers.
- The identity provider and the resource providers see differences in IP addresses if there are proxy implementations in your organization.
- CAE may not immediately revoke access to documents for policy change events if multiple users collaborate on them simultaneously.
- When you enable a user right after disabling them, it takes up to a 15-minute delay for SharePoint Online and a 35-40 minute delay for Exchange Online to recognize the account.
Though CAE possesses some limitations, Microsoft has provided remedies to overcome each limitation. You can check out the limitations and workarounds provided, and follow the steps to overcome them.
I hope this blog will guide you through the concepts of enabling Continuous Access Evaluation in Microsoft Entra. Thanks for reading. Feel free to reach us in the comments for any assistance.
Transform Your Office 365 User Management Landscape with AdminDroid
Continuous Access Evaluation in Microsoft Entra allows immediate termination of user access in response to critical events. Consequently, it becomes essential to monitor these user accounts closely. With AdminDroid, you can go beyond native capabilities and gain a deeper understanding of user activities, including detecting suspicious behavior and analyzing sign-in trends.
Therefore, simplify your user sign-in monitoring and take advantage of the AdminDroid Azure AD user reports!
The AdminDroid Azure AD auditing tool ensures comprehensive monitoring of user activities, minimizing the risk of overlooking critical events. It offers detailed records on various user categories such as
- Sign-in enabled and disabled users
- External and internal guest users
- Successful user logins,
- Failed user logins,
- User’s last and first logon time,
- User’s monthly login count summary
This level of visibility enables administrators to thoroughly analyze all events occurring within their organization, leaving no aspect unexplored.
In addition, the AdminDroid Azure AD reporting tool offers comprehensive visibility into the organization’s sign-ins, presenting clear and detailed information along with valuable insights. The free Azure AD reporting tool goes beyond expectations with over 120 reports that cover a wide range of information about your organization. These reports provide a detailed view of your groups, tracking any changes in group membership. They also give insights into your users, their licenses, login activities, and even password updates.
Don’t miss out on the opportunity to take your Entra ID management to the next level. Download and start using AdminDroid today!






