On Day 28 of Cybersecurity awareness month, learn strong security practices to protect priority accounts in Microsoft 365. Stay tuned for more blog posts in our M365 Cybersecurity blog series.
The importance of executive accounts within an organization’s structure is readily apparent. Therefore, it becomes essential to safeguard priority accounts from malicious users seeking vulnerabilities to exploit. These cybercriminals are not just after ordinary users; their focus lies on spear phishing that specifically targets high-priority accounts. Hackers breaching these accounts can access sensitive data like product development and financial information, threatening the organization’s security and integrity.
The best protection against cyber threats is a layered approach
In this guide, we will explore some best security practices for Microsoft priority accounts and how admins can use them to provide extra protection to these accounts. Let’s get started!
How to Protect Priority Accounts in Microsoft Defender for Office 365?
Microsoft 365 priority accounts are accounts that have access to high-priority information in your organization. They can be managers, infrastructure admins, and other C-suite executive accounts such as CEOs, CISOs, CFOs, build system accounts, infrastructure admins, etc.
In order to give special attention to these critical accounts, you just need to tag them as priority accounts. Microsoft introduced differentiated protection for priority accounts with app-specific features to monitor and manage them using powerful security capabilities like,
- Priority account protection
- Premium mail flow monitoring
By default, priority account protection is turned on in organizations with Microsoft Defender for Office 365 Plan 2. This means that when an account is tagged as a priority account, it will automatically receive priority account protection. Whereas with premium mail flow monitoring, you can maintain smooth email communication which is crucial for business success. You can set a threshold for email issues, get alerts when exceeded, and access priority account email reports in the modern EAC.
In addition to these, it is essential to implement stronger security measures for priority accounts to reduce the risk of compromise.
Security Measures for Protecting Priority Accounts in Microsoft 365
Organizations can safeguard their critical accounts with essential security features from Microsoft 365 and Microsoft Defender for Office 365. These measures include,
- Increase sign-in security for priority accounts
- Use strict preset security policies for priority accounts
- Apply user tags to priority accounts
- Monitor priority accounts with alerts, reports, and detections
- Train users about priority accounts
Unfortunately, these security measures got some license restrictions. Check them below!
| Priority accounts security recommendations | All Office 365 Enterprise plans | Microsoft 365 E3 | Microsoft 365 E5 |
| Increase sign-in security for priority accounts | ✅ | ✅ | ✅ |
| Use Strict preset security policies for priority accounts | ✅ | ✅ | ✅ |
| Apply user tags to priority accounts | ❌ | ❌ | ✅ |
| Monitor priority accounts with alerts, reports, and detections | ❌ | ❌ | ✅ |
| Train users about priority accounts | ✅ | ✅ | ✅ |
Now, let’s look at each of the security recommendations in detail.
1. Increase Sign-in Security for Priority Accounts
To protect priority accounts in Microsoft 365 and increase sign-in security, Microsoft recommends the following practices.
- Enable multi-factor authentication: Configure MFA in Microsoft 365 and require users to use more than just a password to sign in. Even if someone figures out the password, they also need to pass another check, like getting a text on their phone, to get in.
- Disable legacy authentication protocols: Legacy authentication doesn’t support MFA. According to Microsoft, “more than 97 percent of credential stuffing attacks use legacy authentication and more than 99 percent of password spray attacks use legacy authentication protocols”. As MFA is a common requirement to increase the security of priority accounts, Microsoft strongly recommends blocking legacy authentication.
If you can’t turn off legacy authentication protocols for all users, Exchange Online provides alternative options:
- Use Client Access Rules to control who can or can’t use Basic authentication and other legacy protocols like POP3, IMAP4, and authenticated SMTP.
- Disable POP3 and IMAP4 access for individual mailboxes. Additionally, you can disable authenticated SMTP at the organization level and enable it for specific mailboxes if needed.
IMPORTANT: Basic authentication is being phased out in Exchange Online for various services, such as EWS, Exchange ActiveSync, POP3, IMAP4, and remote PowerShell. Hence, it is advisable to ensure precise planning of your requirements before proceeding.
2. Use Strict Preset Security Policies for Priority Accounts
Microsoft Defender priority accounts need extra security measures to protect against malicious email attacks. To tackle this, you can set up strict preset security policies in Exchange Online Protection (EOP) and Defender for Office 365. If there’s a suspicion that an email might be spam, it is placed in quarantine rather than just moving them to the junk email folder. You can also avoid assigning licenses to priority accounts just for creating mailboxes, thereby reducing phishing risk. To ensure important alerts aren’t missed, set up alternate ways to receive notifications sent to priority accounts. This makes sure that their emails are handled with extra care.
3. Apply User Tags to Priority Accounts
Priority accounts in Microsoft Defender for Office 365 are supported as user tags by default. Tagging priority accounts helps you give special attention to them. These tags can be applied as filters in alerts and reports for easily identifying the threats posed on priority accounts. Admins have the ability to identify users who are at a higher risk of being targeted by attackers.
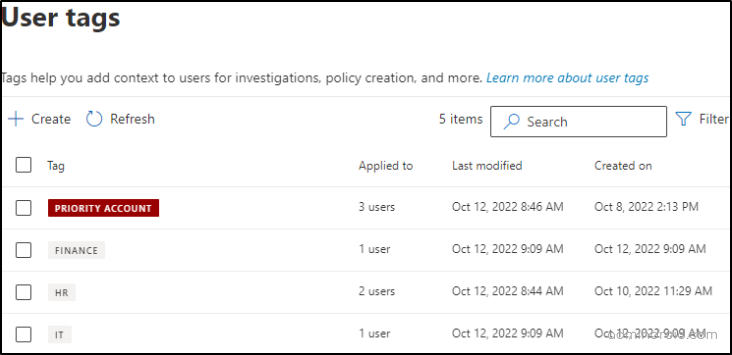
Note: You can monitor up to 250 priority accounts using these user tags in Microsoft Defender.
4. Monitor Priority Accounts with Alerts, Reports, and Detections
After applying priority account tags to important user accounts in Microsoft 365, you can filter them across the Microsoft 365 Defender portal and EOP such as,
- Alerts – Use user tags to filter alerts on the Alerts page in the Microsoft 365 Defender portal.
- Incidents – You can see all user tags for all correlated alerts on the Incidents page in the Microsoft 365 Defender portal.
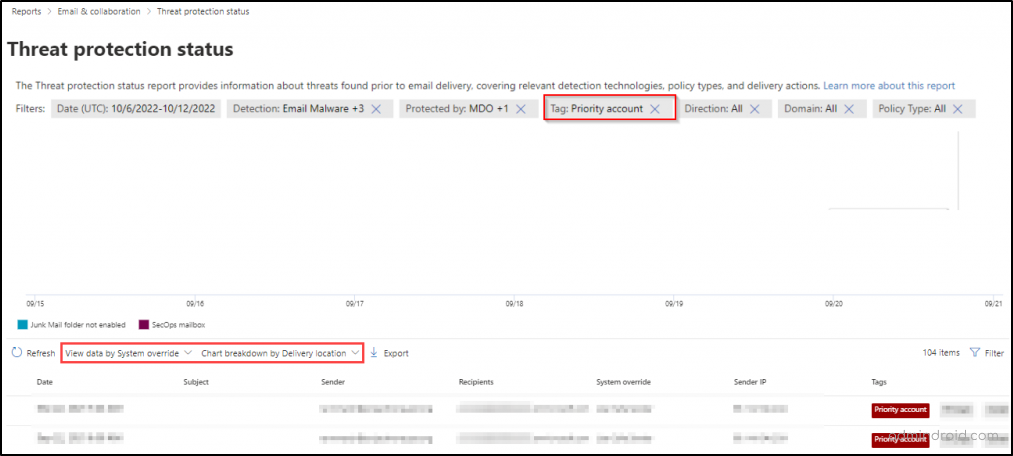
- Threat protection status – The Threat protection status report provides information about threats found prior to email delivery, covering relevant detection technologies, policy types, and delivery actions.
- Custom alert policies – Establish alert policies using user tags in the Microsoft 365 Defender portal.
- Campaign views – Using Campaign Views, you can filter priority accounts to gain a comprehensive overview of attacks targeting one or multiple organizations.
- Explorer – In Explorer, the ‘tags’ column in the email grid displays the priority accounts first as a result of tagging.
- Real-time detections – In Real-time detections (Defender for Office 365 Plan 1), user tags are visible in both the Email grid view and the Email details flyout.
- Email entity page – Filter emails based on applied user tags in Microsoft 365 E5, Defender for Office 365 Plan 1, and Plan 2.
- Top senders and recipients report – Assign this user tag to the top 20 message senders on the Email entity page in EOP or in the Defender for Office 365 for your organization.
- Compromised user report – User accounts marked as Suspicious or Restricted in Microsoft 365 organizations with Exchange Online mailboxes are included in the compromised user report.
- Quarantine – Quarantine policies store potentially harmful messages in Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations for priority accounts.
- Admin submissions and user reported messages – Utilize the Submissions page in the Microsoft 365 Defender portal to send email messages, URLs, and attachments to Microsoft for analysis
- Attack simulation – In the Attack simulation page, you can evaluate your security policies and conduct a harmless cyberattack simulation on your intended users.
- Email issues for priority accounts report – This report on the Message trace page provides details on undelivered and delayed messages for priority accounts.
This adds a highlighted visibility to email threats by quickly identifying incidents or detections that involve important accounts in your organization. One example of how priority accounts are supported in threat protection status reports is shown below.
5. Train Users About Priority Accounts
Priority accounts are often targeted by attackers because they are in positions of power. By educating users about security best practices, you can help reduce the risk of a successful attack, thereby ensuring the protection of priority accounts.
Here are some specific things you can do to train users with priority accounts:
- Teach them how to recognize phishing emails: Phishing emails are one of the most common ways that attackers gain access to user accounts. Train users to be suspicious of any email that asks for personal information, such as passwords or credit card numbers. They should also be wary of emails that come from unknown senders or that contain links or attachments. Reinforce this awareness through phishing attack simulation training, which helps users identify and respond to phishing attempts effectively.
- Educate them about the importance of strong passwords: Strong passwords are essential for protecting user accounts. Train users to create passwords that are at least 12 characters long and include a mix of upper & lowercase letters, numbers, and symbols. They should also avoid using easily guessed passwords, such as their name or birthday.
- Remind them to keep their devices up to date with the latest security patches: Software updates often include security patches that can help protect devices from known vulnerabilities. Train users to install updates as soon as they are available.
- Instruct them on how to report suspicious activity: If a user sees something suspicious, such as an unusual email or a login attempt from an unknown location, they should report it to their security team immediately.
I hope this blog has highlighted the importance of protecting Microsoft 365 admin accounts, C-suite executives, and other high-profile accounts. It also provides key security recommendations for safeguarding these critical assets. Thanks for reading! For further assistance, reach us through the comment section.






