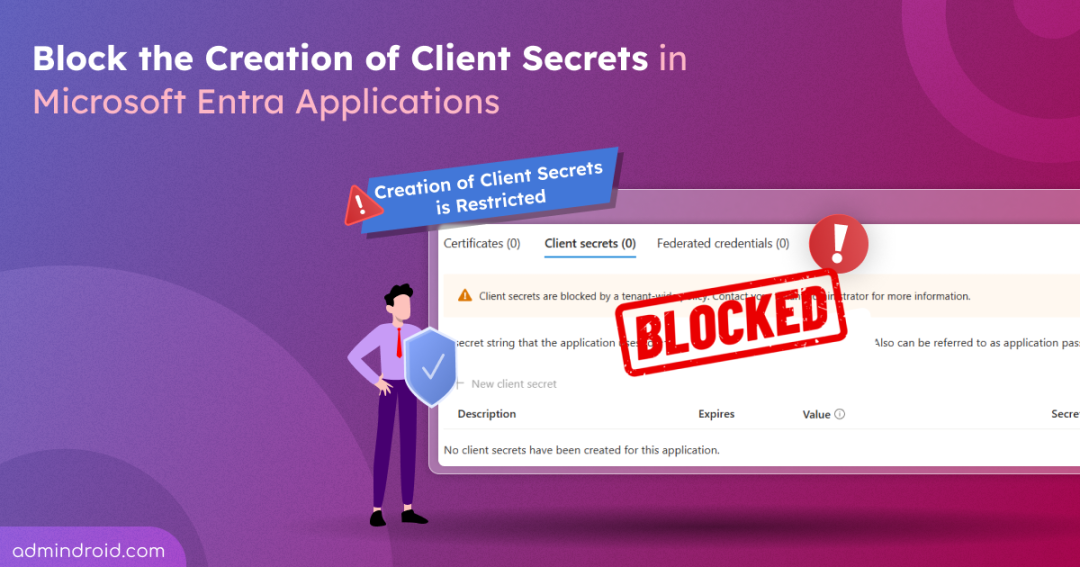
Client secrets might seem like a quick and easy way to authenticate applications, but they come with hidden risks. These secrets are often stored in plain text, hardcoded in scripts, or forgotten entirely, turning into silent security risks waiting to be exploited.
With attackers constantly scanning for exposed credentials, relying on client secrets is like locking your front door but leaving the key under the welcome mat.
To tackle this risk, Microsoft lets you block client secret creation in Entra applications. This enforces users to adopt stronger authentication methods and helps secure Microsoft Entra applications across your organization.
In this blog, let’s explore how to block the creation of client secrets in Microsoft Entra applications using app management policies and reduce the chance of a security breach.
Configure App Management Policy to Restrict Client Secrets Creation
App management policies in Microsoft Entra let you control how client secrets are created and managed for Azure-registered applications.
This helps enforce secure app-to-app authentication and reduces the risk of exposed credentials.
You can apply the app management policy at different levels, depending on your needs:
Prerequisites to Manage App Management Policy in Microsoft Entra
To configure application policies, you must have one of the following roles:
- Global Administrator
- Application Administrator
- Cloud Application Administrator
Update Tenant App Management Policy to Block Client Secret Creations
A default app management policy in Microsoft Entra allows you to block all applications in your organization from creating client secrets. This enforces stronger authentication methods and enhances overall security of your tenant.
By default, the tenant-wide app management policy is disabled. You can enable it to block secrets for all the applications in your tenant.
Follow the steps below to update the default tenant-wide app management policy:
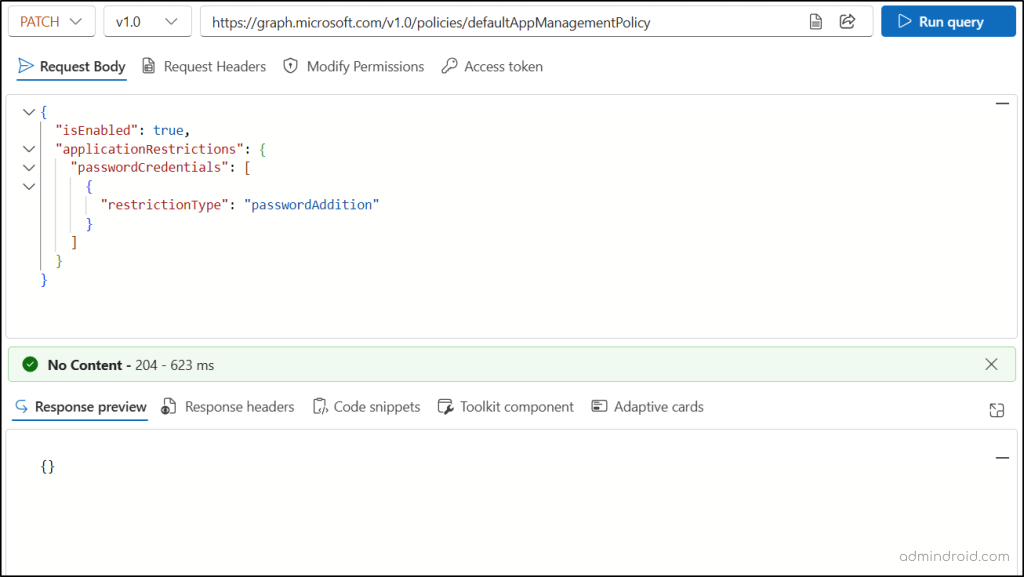
- Open and sign in to Microsoft Graph Explorer using your Microsoft 365 account.
- In the HTTP request bar, set the HTTP method to PATCH.
- Set the HTTP request URL to the following API.
https://graph.microsoft.com/v1.0/policies/defaultAppManagementPolicy - Go to the “Modify permissions” tab and click the Consent button near the Policy.ReadWrite.ApplicationConfiguration to grant the required permission to Graph Explorer.
- Enter the following JSON format in the Request Body and click Run query.
|
1 2 3 4 5 6 7 8 9 10 |
{ "isEnabled": true, "applicationRestrictions": { "passwordCredentials": [ { "restrictionType": "passwordAddition" } ] } } |
This JSON format enables the default tenant-wide policy and blocks client secret creation for all applications in your Microsoft 365 tenant. You can also block client secrets using the Microsoft Entra admin center. This UI-based method lets you easily apply client secret restrictions to all applications or only selected ones.
If successful, this method returns a “No Content – 204” response code. It doesn’t return anything in the Response preview.
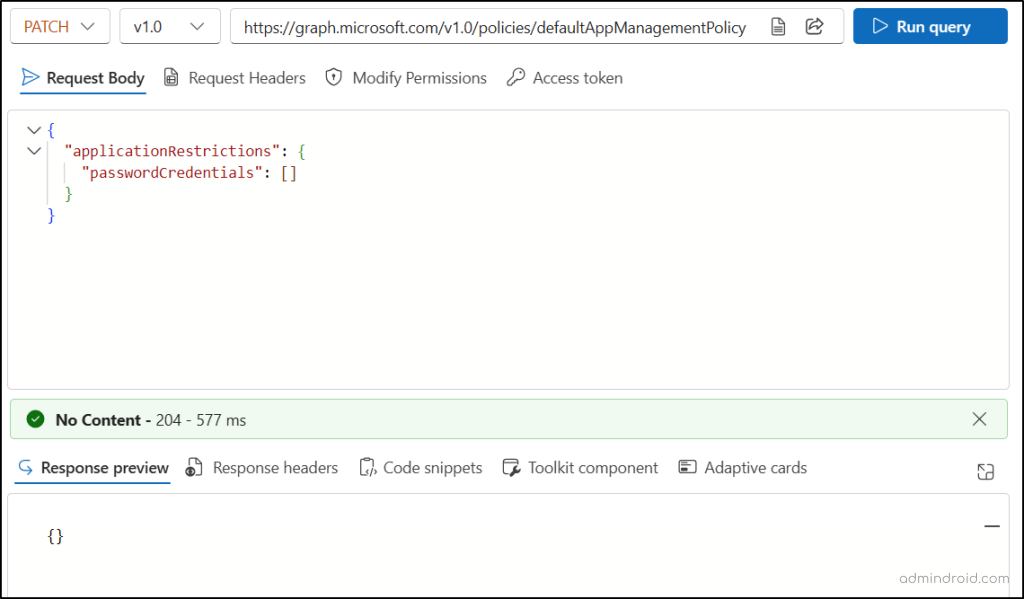
If the block on client secret creation is no longer needed in your organization, you can remove the restriction using the Graph API.
- Set the HTTP request method to PATCH.
- Enter the following URL in the HTTP request bar.
https://graph.microsoft.com/v1.0/policies/defaultAppManagementPolicy
- Enter the following JSON to the Request Body and click Run Query.
|
1 2 3 4 5 |
{ "applicationRestrictions": { "passwordCredentials": [] } } |
If successful, this method returns a “No Content – 204” response code.
Set Up Custom App Management Policies to Restrict Client Secrets Creation
Each application in your organization has different roles, risks, and requirements. While some may work fine with basic settings, others, especially those handling sensitive data, need stricter controls. That’s where Microsoft Entra’s custom app management policies come in. This lets you fine-tune restrictions for each app, giving you the flexibility to secure what matters most, without overcomplicating the rest.
Note: When both the tenant default policy and an app management policy define the same restriction, the app management policy takes precedence.
To control client secret creation at the application level, you can use the following steps:
1. Create a Custom App Management Policy in Microsoft Entra
To prevent users from creating client secrets in a specific application, you should first create a policy that restricts password (client secret) creation and then assign that policy to the application.
Follow the steps below to create a custom app management policy:
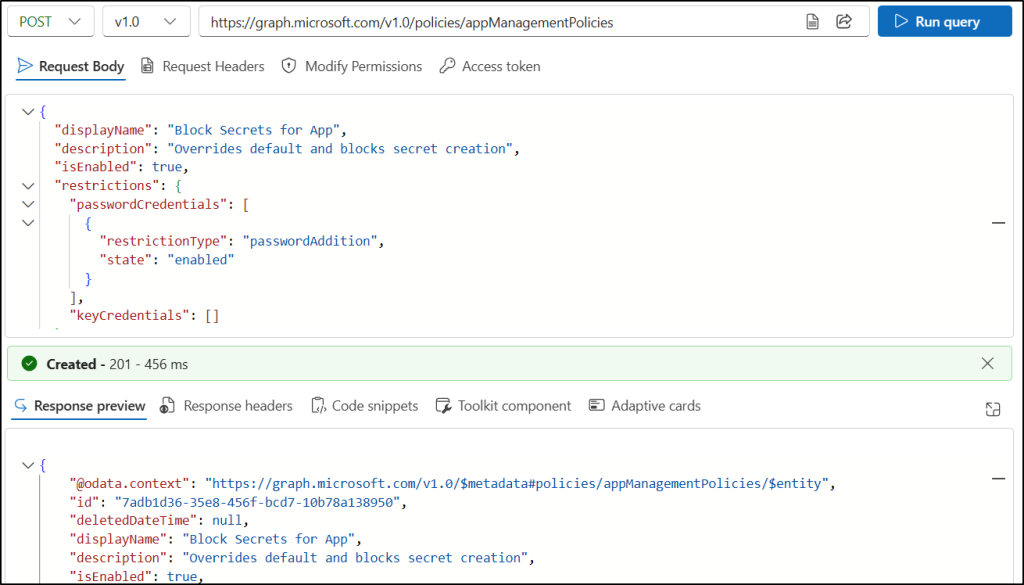
- Sign in to Microsoft Graph Explorer using your Microsoft 365 account.
- In the HTTP request bar, set the HTTP method to POST.
- Set the HTTP request URL to the following API.
https://graph.microsoft.com/v1.0/policies/appManagementPolicies
- Go to the “Modify permissions” tab and click the Consent button near the Policy.ReadWrite.ApplicationConfiguration to grant the required permission to Graph Explorer.
- Enter the following JSON format in the Request Body and click Run query.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
{ "displayName": "Block Secrets for App", "description": "Overrides default and blocks secret creation", "isEnabled": true, "restrictions": { "passwordCredentials": [ { "restrictionType": "passwordAddition", "state": "enabled" } ], "keyCredentials": [] } } |
If successful, this method returns a “Created – 201” response, confirming that the app management policy was created.
Save the policy ID (id) from the Response preview. This will be used for all the steps below.
2. Assign the Custom App Management Policy to an Application
Follow the steps below to assign an app management policy to a specific Microsoft Entra application.
- Sign in to Microsoft Graph Explorer using your Microsoft 365 account.
- Set the HTTP method to POST in the request bar.
- Enter the following API in the HTTP request URL.
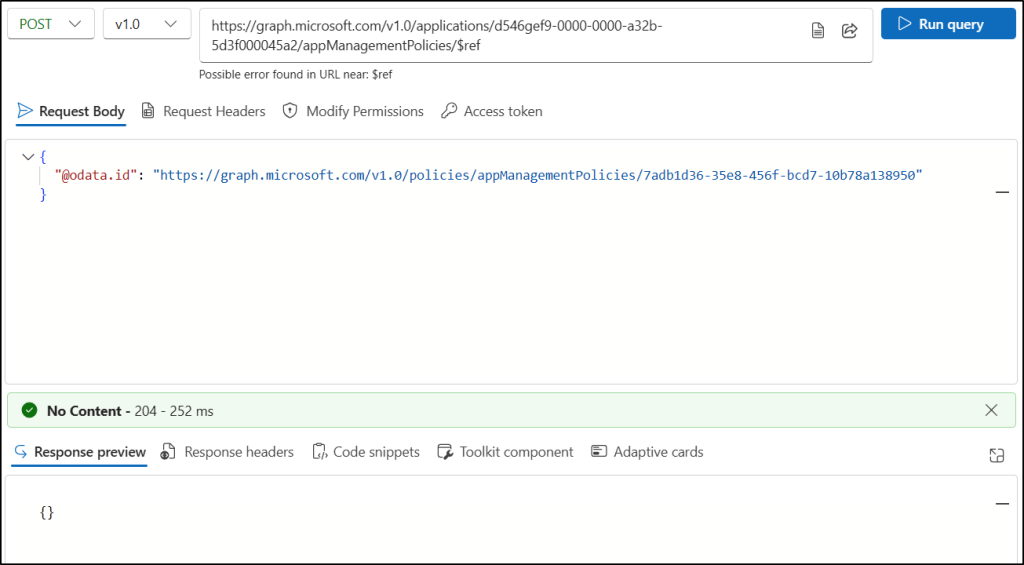
https://graph.microsoft.com/v1.0/applications/{app-id}/appManagementPolicies/$ref
Replace {app-id} with the object ID of the application to which you want to apply the policy. - Go to the “Modify permissions” tab and click the Consent button near the Policy.ReadWrite.ApplicationConfiguration and Application.ReadWrite.All permissions.
- Enter the following JSON format in the Request Body and click Run query.
|
1 2 3 |
{ "@odata.id": "https://graph.microsoft.com/v1.0/policies/appManagementPolicies/{policy-id}" } |
Replace {policy-id} with the “id” of the custom app management policy you created.
If successful, this method returns a No Content – 204 response code. It doesn’t return anything in the Response preview.
Note: Only one custom app management policy can be assigned to an application at a time.
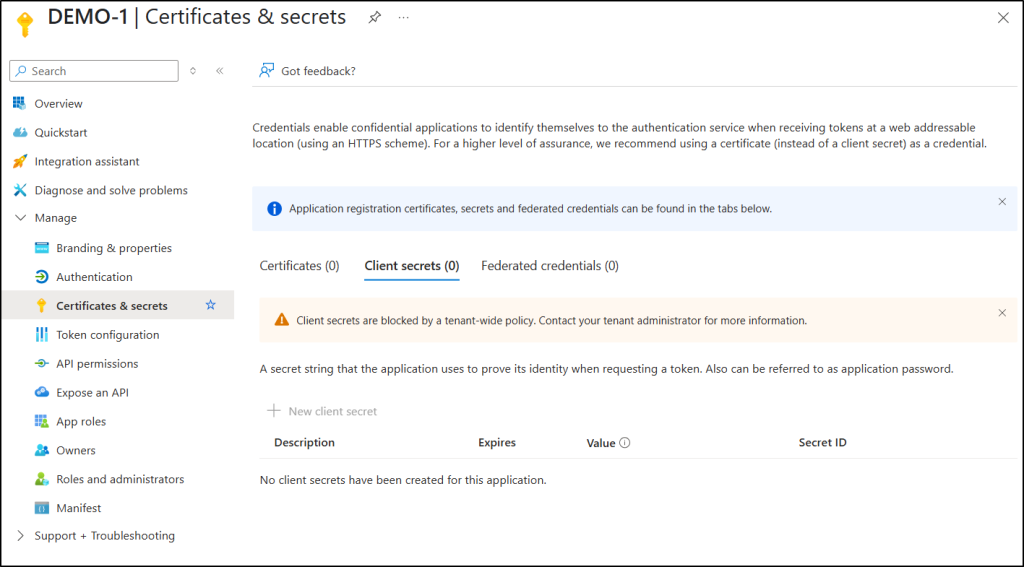
Now, when users attempt to create a client secret for the specific application, the following warning is displayed on the page:
Client secrets are blocked by a tenant-wide policy. Contact your administrator for more information.
3. Remove App Management Policy from Entra Application
You may need to remove the custom app management policy from an application when requirements change, or it no longer needs strict security controls. In this case, you can unassign the custom policy, allowing the application to follow the tenant-wide default policy.
Follow the steps below to remove the custom app management policy:
- Open and sign in to Microsoft Graph Explorer using your Microsoft 365 account.
- In the HTTP request bar, set the HTTP method to DELETE.
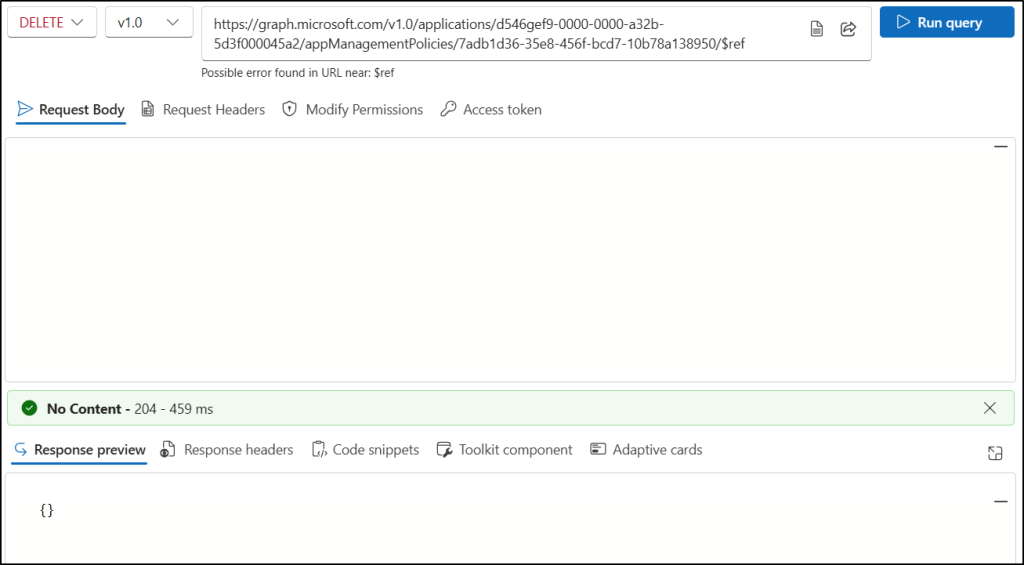
- Set the HTTP request URL to the following API.
https://graph.microsoft.com/v1.0/applications/{app-id}/appManagementPolicies/{policy-id}/$ref
Replace {app-id} and {policy-id} with the IDs of the application and the app management policy. - Go to the “Modify permissions” tab and click the Consent button near the Policy.ReadWrite.ApplicationConfiguration permission.
- Click Run query.
If successful, it returns a No Content – 204 response code. It doesn’t return anything in the Response preview.
Restricting client secret creation in Entra applications strengthens security by reducing the use of weak authentication methods. To further improve your Microsoft 365 security posture, follow best practices such as tracking and rotating expired app credentials, managing user consent to applications, and removing unused app credentials regularly.
We hope this blog helps you to take control of client secret management in Microsoft Entra, helping you strengthen your application security and stay ahead of evolving identity threats. If you have any further questions or feedback, feel free to share them in the comments below. We’re happy to help!